400k Linux Servers Hacked to Mine Cryptocurrency
.webp)
A brand original file from cybersecurity researchers at ESET has uncovered a huge botnet created from over 400,000 compromised Linux servers being ragged for cryptocurrency theft and totally different illicit financial fabricate.
The botnet, operated by the chance community within the again of the Ebury malware, has been active since at the very least 2009 however has evolved considerably throughout the final decade.

Ebury’s Insidious Unfold
The Ebury gang employs a diversity of tactics to propagate the malware and blueprint bigger their botnet:
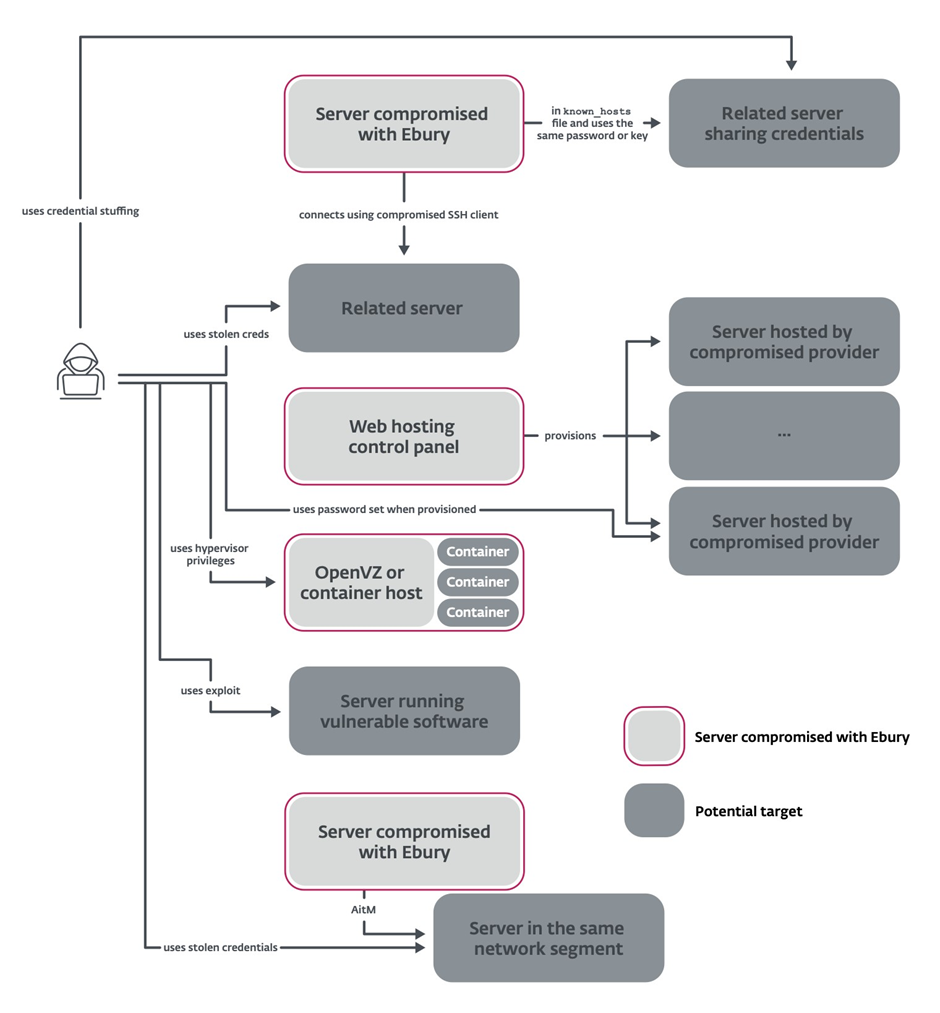
- Compromised Net hosting Services: Leveraging in finding entry to to internet hosting companies’ infrastructure to install Ebury on all hosted servers
- ARP Spoofing Attacks: Intercepting and redirecting SSH visitors interior info products and companies to take hold of credentials
- Over 200 Bitcoin/Ethereum Nodes Focused: Automatically stealing crypto wallets when victims log in
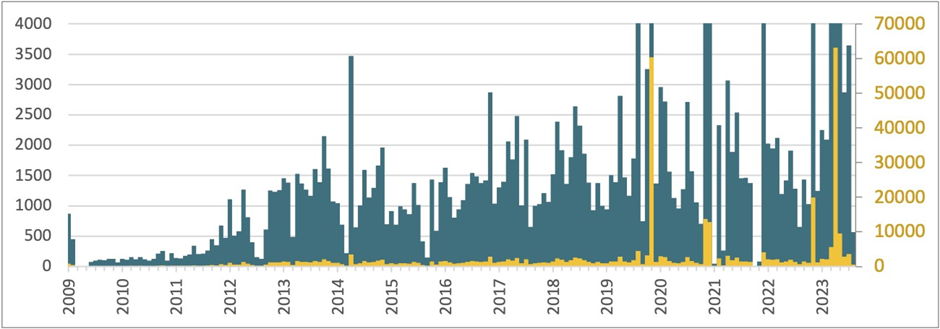
As illustrated below, the botnet has seen explosive boost, with over 100,000 servers unruffled contaminated as of gradual 2023.
Evolving Malware Arsenal
As properly as to primitive dispute mail and visitors redirection, ESET’s file unearths original malware households ragged to monetize the botnet via:
- Stealing financial info from transactional internet sites
- Cryptojacking to mine cryptocurrency on contaminated systems
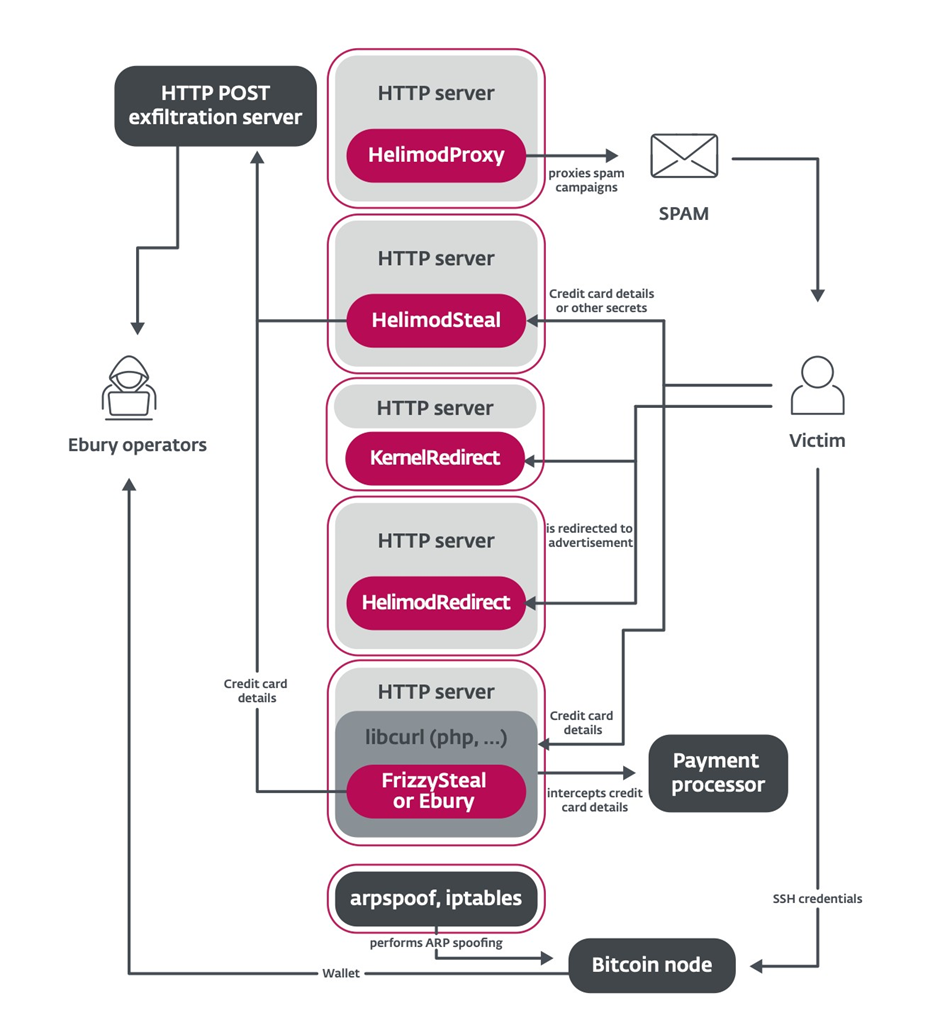
The Ebury household of malware has also been made higher.
The most modern colossal model change, 1.8, got right here out in gradual 2023.
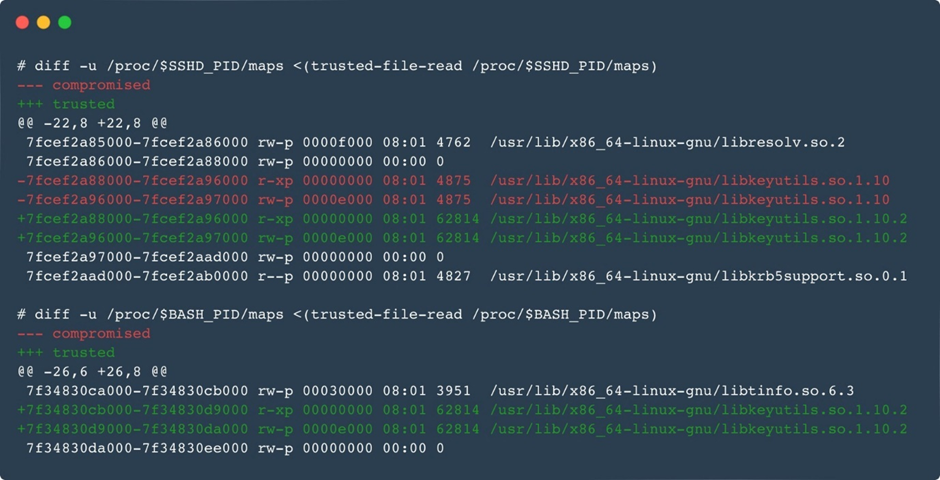
Many adjustments were made, including original systems to cowl info, a brand original domain technology algorithm (DGA), and better userland rootkits that Ebury uses to cowl from machine admins.
When the mode is on, the course of, file, port, and even the mapped memory are hidden.
ESET has released indicators of compromise and a detection script to abet organizations establish within the event that they’ve been impacted.
The fat file provides in-depth technical prognosis for safety groups.
As this potent botnet continues expanding, affirming patched systems and sturdy credential insurance policies is important to stopping compromise. The cybersecurity neighborhood must also remain vigilant against the evolving Ebury chance.
Source credit : cybersecuritynews.com


