New Wi-Fi MITM Attack That Can Evade WPA3 Security Mechanisms

The sizzling discovery of a significant vulnerability within the NPU chipset by Tsinghua University and George Mason University researchers enables attackers to snoop on data transmitted over 89% of staunch-world Wi-Fi networks by exploiting it.
Hardware acceleration, such as the usage of NPU chipsets in Wi-Fi networks, improves data transmission charge and reduces latency nonetheless moreover introduces security considerations this potential that of the say transmission of wi-fi frames by Obtain admission to Level (AP) routers.
Wi-Fi MITM Assault Model
The one real within the near past chanced on flaw within the NPU’s wi-fi body forwarding plan enables attackers to originate Man-in-the-Heart (MITM) attacks on Wi-Fi networks without requiring rogue APs.
The assault, able to bypassing hyperlink-layer security mechanisms such as WPA3 and intercepting plaintext site visitors, has been detailed in a analysis paper well-liked by the 2023 IEEE Symposium on Security and Privacy.
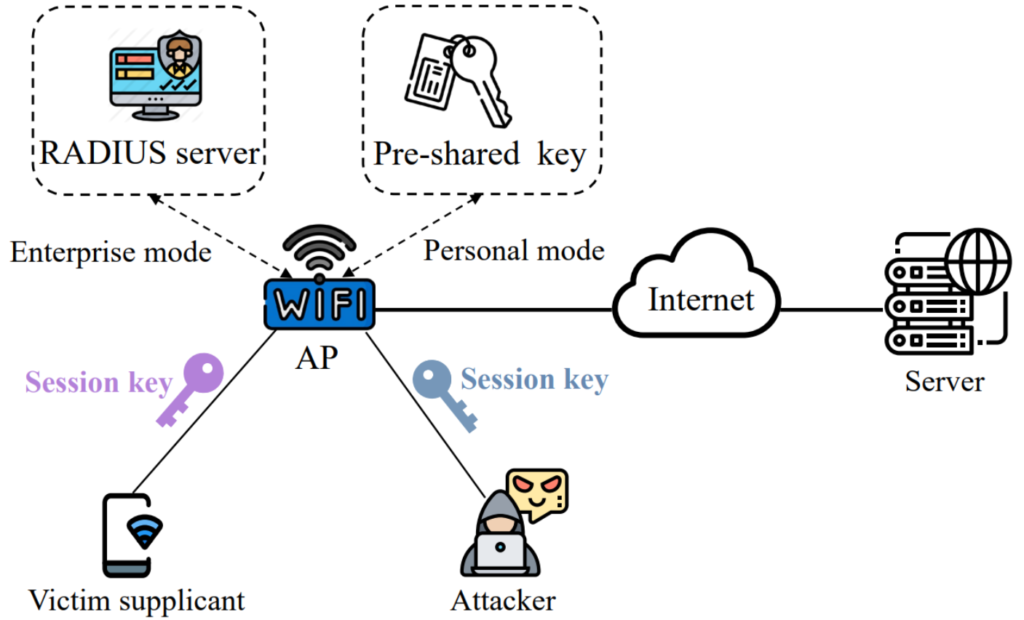
An attacker is connected to a Wi-Fi network at this point so that the attacker has get entry to to the Internet in list to assault the victim.
After passing cellular phone authentication, have faith in accessing the Wi-Fi network of a cafeteria secured with WPA2 or WPA3, where each session to the AP router is safe by the Pairwise Transient Key (PTK) session key.
Experts chanced on that the victim supplicant’s site visitors in plaintext would possibly also be intercepted without misfortune by evading the safety mechanisms like WPA2 and WPA3.
Attackers Spoofing IP
Here the attacker spoofs the availability IP tackle by impersonating the AP after which sends an ICMP redirect message (kind=5) to the victim.
To prioritize performance, the NPU in AP routers like Qualcomm IPQ5018 and HiSilicon Gigahome Quad-core will without lengthen transmit the received fake ICMP redirect messages to the victim seeker.
When the victim supplicant receives the message, it is deceived into updating its routing cache and substituting the next hop with the attacker’s IP tackle, inflicting subsequent IP packets supposed for the server to be directed to the attacker at the IP layer, enabling packet forwarding by the attacker.
Silently and without the usage of any rogue AP, the attacker effectively performs a MITM assault, enabling the interception and modification of the victim supplicant’s site visitors.
The vulnerability stopping AP devices from blockading solid ICMP redirect messages has been confirmed by Qualcomm and Hisilicon, with Qualcomm assigning CVE-2022-25667 to this particular disaster.
Security analysts conducting a huge-scale empirical study about on mainstream AP routers and staunch-world Wi-Fi networks chanced on that the vulnerability in embedded NPUs impacts regarding all mainstream AP routers.
Out of the 55 prone AP routers examined from 10 neatly-known AP distributors, the consultants chanced on that over 89% of the 122 staunch-world Wi-Fi networks examined had been uncovered to already known attacks.
Whereas as a mitigatory recommendation, consultants maintain affirmed that to improve security, APs would possibly well mute throttle crafted ICMP redirects, and supplicants would possibly well mute verify received ICMP messages.
Source credit : cybersecuritynews.com

