QuickBlox Framework Security Flaws Exposes Millions of Users Sensitive Data

Most recent reviews from Team82 and Take a look at Level Research (CPR) crew command that there has been a important vulnerability in QuickBlox SDK (Machine Model Kit) and API (Utility Programming Interface) that is feeble for increasing chat and video functions.
Researchers are ready to rob over extra than one particular person accounts in dozens of functions that rely on the QuickBlox framework for increasing their functions.
These vulnerabilities had been reported to QuickBlox and fastened with the original safety structure.
QuickBlox Architecture
QuickBlox requires developers to earn a brand original QuickBlox fable which in flip creates a brand original utility with the QuickBlox Dashboard along with particular credentials for the utility, which accommodates an Utility ID, Authorization Key, Authorization Secret, and Myth Key.
These credentials are then feeble to ask and retrieve the QB token for this utility that is feeble for additional API requests.
Once the QB token is obtained by the original utility, it requires the actual person credentials and the utility session to earn the session extra licensed and authenticated.
As well to to this, every particular person of the utility requires the utility session to log in to the utility as per the QuickBlox documentation.
A complete lot of the functions that use QuickBlox real inserted the utility credentials into their functions, which is straightforward to extract by reverse engineering with tools relish Frida.
QuickBlox Vulnerabilities
Once these utility secret keys had been extracted, it was that you simply would possibly well well imagine for the analysis crew to extract extra than one recordsdata from endpoints, relish the entire list of users (/users.json), PII particular person recordsdata (/ID.json) which accommodates name, email, cell phone number, and so forth., and earn original users (/users.json).
An attacker with static settings recordsdata is in a position to taking on the overall particular person accounts and creating extra than one attacker-managed accounts.
Moreover, there had been loads of functions that did now no longer put in power appropriate safety measures of their functions.
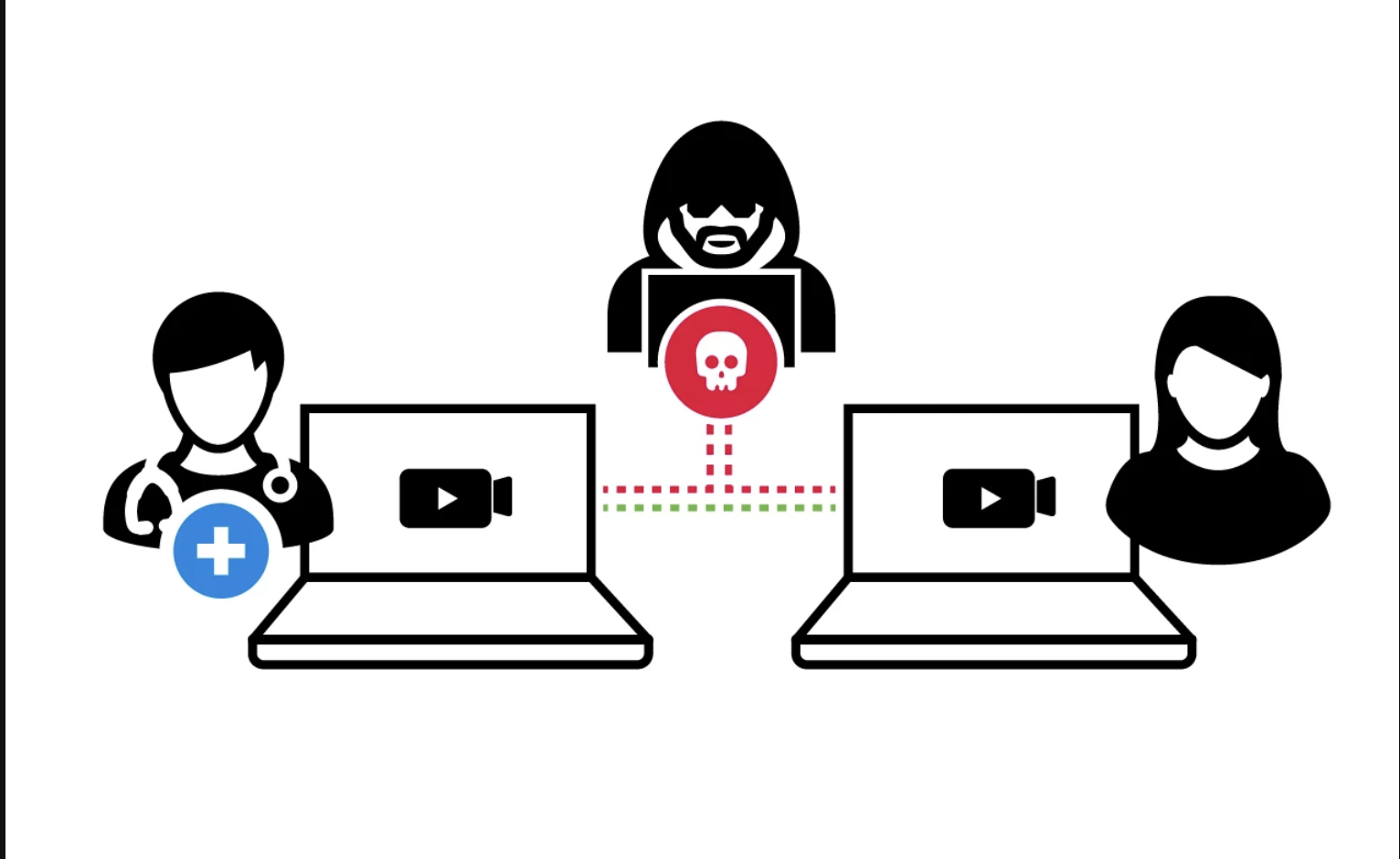
The most serious ones had been from the Telemedicine and Intercom / Verbal change industries.
Case Research and Affect
Two case analysis had been performed on a Telemedicine android utility and an Israeli-basically basically based Intercom utility that makes use of QuickBlox of their functions.
In the case of the Intercom, the researchers had been ready to extract recordsdata and behavior actions relish Wiretapping, opening the doors, controlling microphones, and much extra.
In Telemedicine’s case, the researchers would possibly well probably also extract serious and exquisite recordsdata relish patients’ medical records, chat histories, medical ancient past, medical doctors’ records, and so forth.
In worst conditions, risk actors exploiting this vulnerability can additionally impersonate an exact doctor.
A complete document was released by team82, which comprises detailed recordsdata on the exploitation and the suggestions feeble for exploitation.
Source credit : cybersecuritynews.com


