Hackers Exploit Salesforce Email Zero-day Flaw in Facebook Targeted Phishing Attack
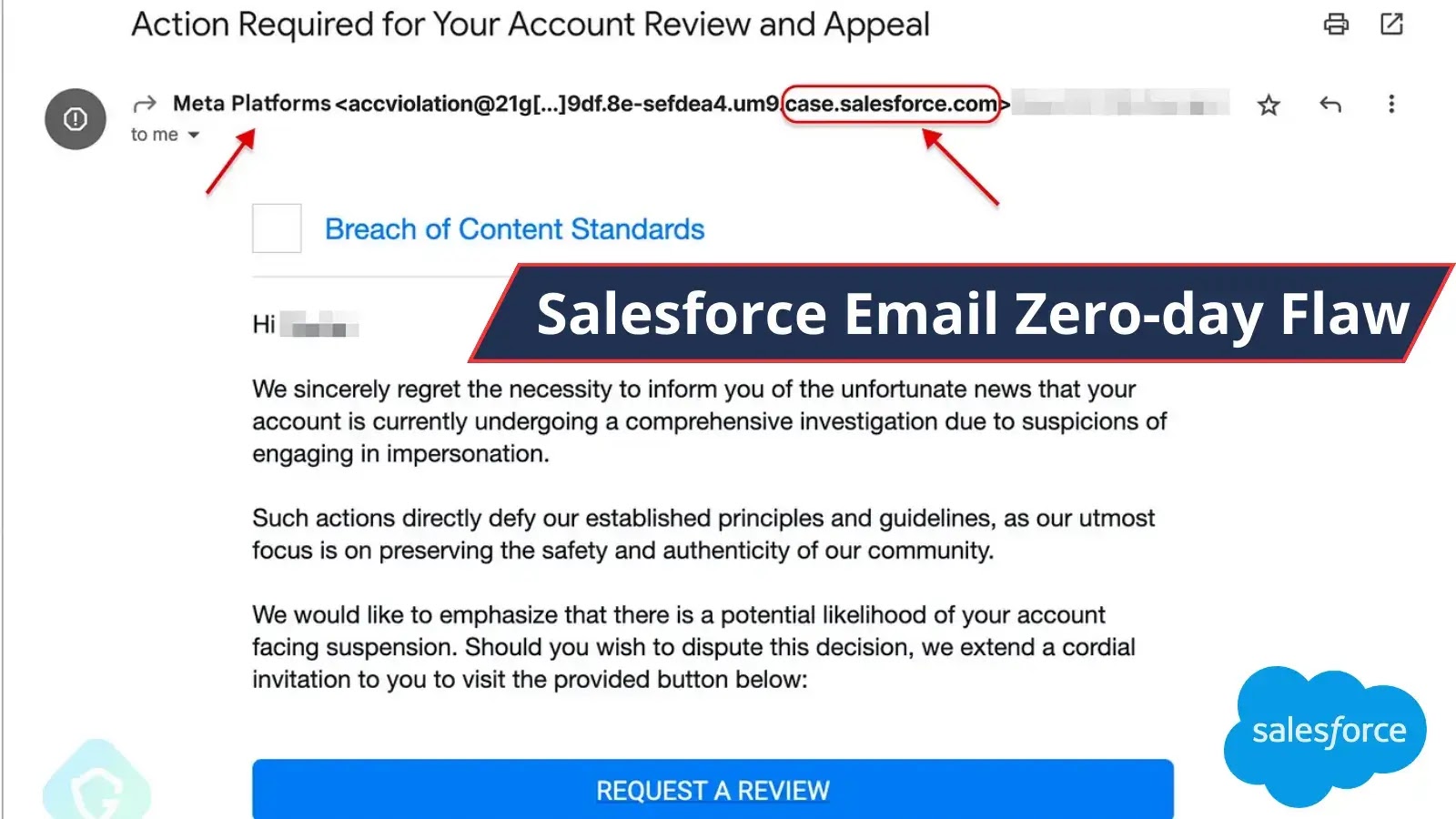
Hackers exploited a zero-day vulnerability within the electronic mail products and companies and SMTP servers of Salesforce.
Malicious electronic mail traffic is in general concealed interior electronic mail gateway products and companies which may well well maybe be conception about legitimate and valid.
Gateways are vital as they act as gatekeepers, making sure that there may be no longer a misuse by fastidiously verifying the possession of every and every electronic mail address passe.
It changed into as soon as stumbled on by Guardio Labs that attackers exclaim Sophisticated solutions to circumvent the safeguard products and companies.
Salesforce Phishing Electronic mail
The ample blue button sends the target to the phishing page built to grasp the Fb memoir vital parts.
How Salesforce Validates Enviornment Ownership
The Salesforce system validates the domain possession earlier than sending out an electronic mail.
Electronic mail addresses wishes to be verified to ship out emails the utilization of it. Clicking the verification hyperlink permits the salesforce backend to configure outgoing emails.
Guardio, Manipulated POST demand sent to Salesforce’s BE to trigger the electronic mail transmission by altering the sender’s address to assorted values. Alternatively, the operation changed into as soon as blocked.
Serene, How halt the Attackers have the option spherical these measures?
The From address field’s domain is built of a sub-domain generated per a recount Salesforce memoir.
Guardio Labs says attackers exploit Salesforce’s “Electronic mail-to-Case” feature, which organizations turn incoming customer emails into actionable tickets for their reinforce teams.
Took Earnings of Salesforce Characteristic
Guardio lab stumbled on that the attackers exclaim the “Electronic mail-To-Case” spin along with the trudge — gaining plump take care of watch over of the username part of the generated salesforce electronic mail address.
Field this address as an “Group-Large Electronic mail Handle,” which Salesforce’s Mass Mailer Gateway uses for outgoing electronic mail, and at final went via the verification process to confirm possession of the domain.
Through this, an attacker may well well build any phishing arrangement.
This can stay up within the sufferer’s inbox, bypassing anti-unsolicited mail and anti-phishing mechanisms, and even marked as Critical by Google
Closure
As of the 28th of July, ’23, the vulnerability changed into as soon as resolved, and a repair changed into as soon as deployed affecting all Salesforce products and companies and prerequisites.
Meta engineers are tranquil investigating why existing protections failed to stay the attacks.
“We’re doing a root trigger prognosis to see why our detections and mitigations for these forms of attacks didn’t work” (Meta’s Engineering)
Source credit : cybersecuritynews.com


