Hackers Use Abandoned WordPress Plugins to Backdoor Websites

Threat actors possess stumbled on a original formula to insert malicious code into web sites. They are at this time the exercise of Eval PHP, an deserted WordPress plugin.
Mostly, web dispute backdoors are programmed in PHP, the foundational language of the novel web. Most completely different well-liked CMS platforms, including Joomla, Magento, and WordPress (which create up over 40% of the internet), are in accordance with PHP.
PHP is a extremely universal language so attackers can abuse it. Backdoors are one in every of essentially the most widely old (and misused) by attackers.
Over the previous few weeks, PHP code injections had been stumbled on. These assaults send a previously identified payload that permits the attackers to stay code on the contaminated web dispute remotely.
The ‘wp_posts’ desk within the databases of the targeted web sites is where the malicious code is launched. Which means that, it avoids identical old web dispute security procedures fancy file integrity monitoring, server-facet scanning, and heaps others., making it more advanced to detect.

The threat actors set up Eval PHP the exercise of a compromised or newly generated administrator account to manufacture this. This allows them to make exercise of [evalphp] shortcodes to introduce PHP code into the positioning’s pages and posts.
The backdoor (3e9c0ca6bbe9.php) is dropped into the positioning root as soon as the code has carried out running. Relying on the assault, the backdoor’s title would possibly seemingly well also commerce.
Misusing a Respected Plugin
Researchers identified that attackers breach web sites by injecting covert backdoors the exercise of Eval PHP, an outdated legit WordPress plugin.
Eval PHP enables attach administrators to insert PHP code into posts and pages of WordPress web sites, which is as a consequence of this truth completed when the page is loaded within the browser.
The plugin was as soon as last updated a decade ago and is on the total thought of outdated, even supposing it’s still accessible thru the WordPress plugin repository.
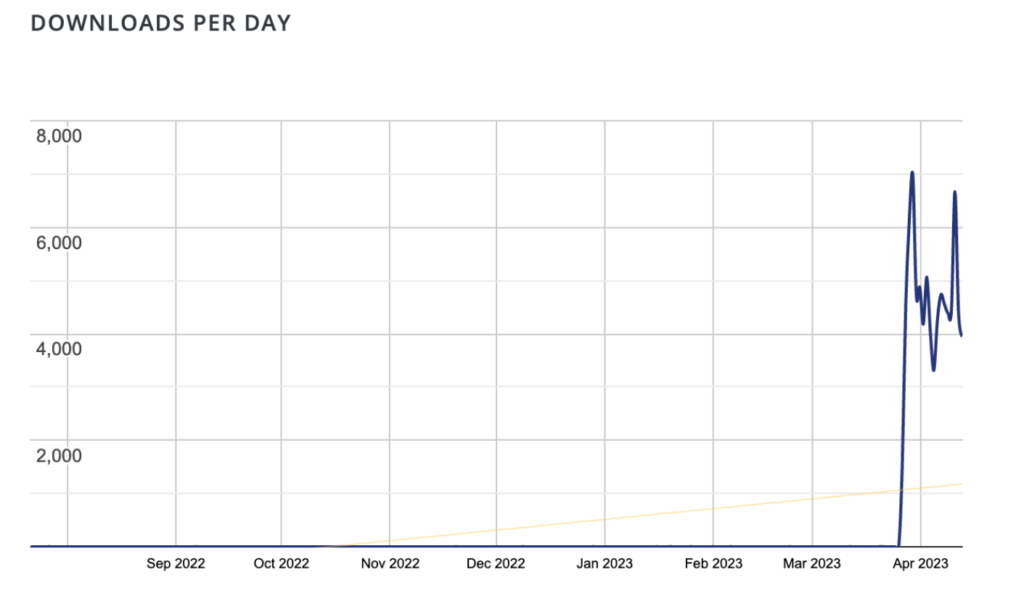
“For the ten years main up to the discontinue of March 2023, this plugin no longer frequently ever had one internet a day.” However spherical March 29, 2023, we saw day-to-day downloads spike to 7,000. After that, now we possess got considered 3k-5k downloads day-after-day, with over 100,000 downloads whole”, says Sucuri.
Particularly, the critical advantage of this kind over veteran backdoor injections is the power to re-infect cleaned sites with Eval PHP whereas keeping the purpose of breach largely secret.
The next three IP addresses are the source of malicious requests:
- 91.193.43.151
- seventy 9.137.206.177
- 212.113.119.6
Researchers convey the backdoor sends recordsdata thru cookies and GET requests without visible parameters for C2 communication in place of residing of the exercise of POST requests to steer obvious of detection.
“The vogue the Eval PHP plugin works,, it’s enough to avoid losing a page as a draft to stay the PHP code all over the [evalphp] shortcodes.
“Though the injection in attach aside a question to does drop a frail backdoor into the file structure, the aggregate of a legit plugin and a backdoor dropper in a WordPress put up permits them to reinfect the web dispute and finish hidden without scrape—all they ought to create is say over with a “benign” web dispute,” researchers point out.
Must you entry the EvalPHP page within the legit plugin repository, WordPress shows the following warning:
“This plugin hasn’t been tested withthe latestt three main releases of WordPress. It would possibly seemingly well also no longer be maintained or supported and would possibly seemingly well also possess compatibility components when old with more moderen variations of WordPress.”
Researchers convey this would possibly occasionally no longer be ample for plugins inclined to misuse. Such plugins ought to be totally eradicated from the list, especially within the occasion that they haven’t got any updates in additional than ten years and possess a really minute desire of precise users.
Source credit : cybersecuritynews.com


