New Water Orthrus's Hacker Group Deploys Malware & Steals Credit Card Data

Pattern Micro researchers were monitoring a possibility actor identified as Water Orthrus since 2021, as they employed pay-per-install networks to distribute the CopperStealer malware.
The malware has undergone loads of adjustments and upgrades by the possibility actor to attend diversified illicit targets contend with:-
- Injecting community commercials
- Acquiring deepest recordsdata
- Stealing cryptocurrency
While as adverse to this, cybersecurity consultants suggest a seemingly affiliation between them and the previously reported “Scranos” possibility marketing campaign from 2019.
Credential Phishing Campaign
Analysts chanced on two unusual campaigns in March 2023, introducing malware called “CopperStealth” and “CopperPhish,” which allotment similarities with CopperStealer and are believed to be the work of the the same author, suggesting they are the unusual actions of Water Orthrus.
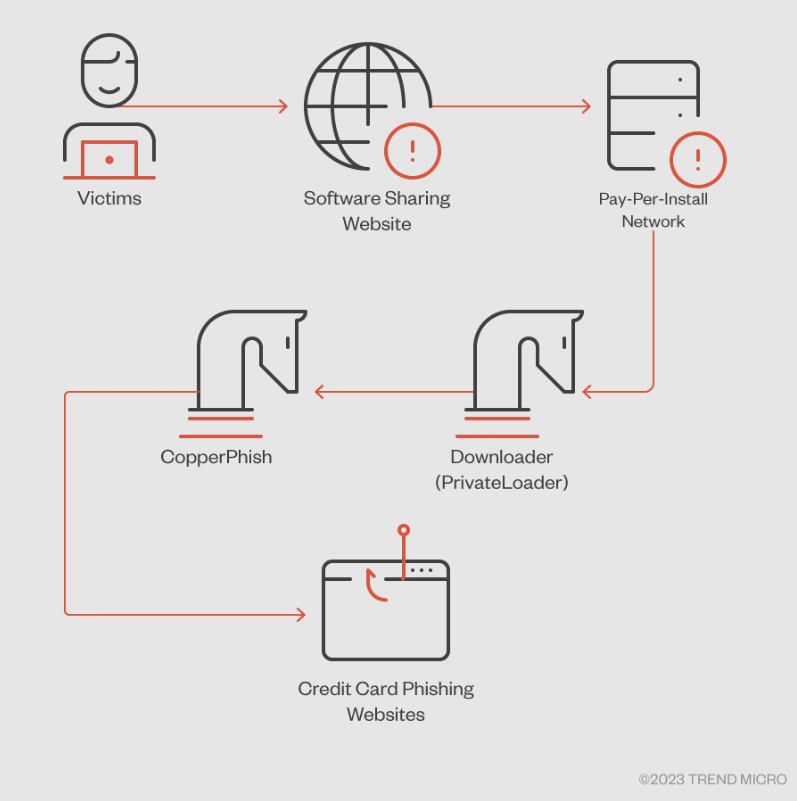
On March 8, 2023, the preliminary marketing campaign deployed CopperStealth thru installers equipped on a in model Chinese language arrangement-sharing web set, covering the malware as free arrangement and specializing in Chinese language users.
CopperStealth deploys a rootkit that injects payloads into explorer.exe and other machine processes, initiating a derive and execution of extra tasks.
Moreover, the rootkit prevents the execution of certain executables and drivers and blocks receive admission to to blocklisted registry keys.
The installer entails encoded URLs that, upon execution, decode and derive recordsdata from those URLs onto the compromised machine, with one in all the recordsdata being identified as the CopperStealth dropper.
CopperStealth incorporates the “HelloWorld” export characteristic, carried over from old versions of CopperStealer, and the dropper determines the machine architecture to retrieve the connected driver from its sources.
There is a file machine filter driver that’s registered with the rootkit and has surely professional handlers for IRP_MJ_CREATE, IRP_MJ_READ, and IRP_MJ_SHUTDOWN in the DriverEntry characteristic.
When the rootkit loads a peculiar route of as a driver, it searches for explicit byte sequences which may well perchance perchance be blacklisted, and if chanced on, the entry level of the motive force is modified to reach aid:-
- STATUS_ACCESS_DENIED
Right here below we have now talked about the total byte sequences and amongst them, one in all the byte sequences comes embedded with blocklisted drivers:-
- Beijing Huorong Network Technology Co., Ltd.
- Beijing Kingsoft Security Instrument Co., Ltd.
- Beijing Qihu Technology Co., Ltd.
- HuoRongBoRui (Beijing) Technology Co., Ltd.
- Qihoo 360 Instrument (Beijing) Co., Ltd.
The statistics module, cnzz, increases a counter in HKCUInstrumentMicrosoftcount_a0b1c2d3 upon execution, verifies web connection thru hxxp://www[.]msftconnecttest[.]com/connecttest.txt, obtains a particular machine ID, reports statistics to hxxp://cnzz_url&m=
CopperPhish begins with downloaders contend with PrivateLoader, distributed thru pay-per-install (PPI) networks by process of false derive links in commercials.
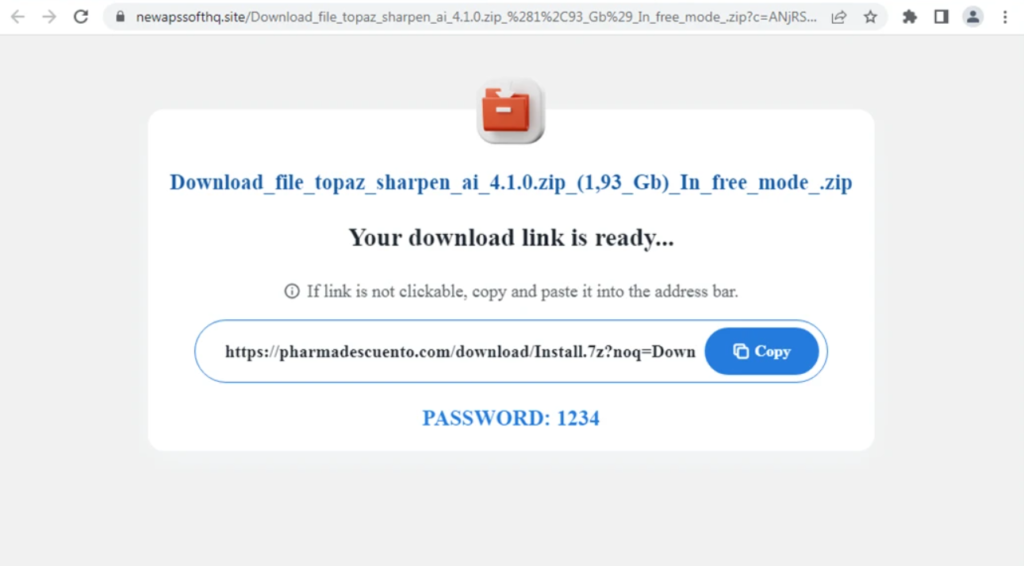
The find browser program employs an Web Explorer object and the SHDocVwCtl class to defend watch over its habits, extracting the charge from the sufferer’s “checkcode” input field and sending an exit message to the major payload thru the talked about pipes if the input is good.
Stealing CC recordsdata
The phishing webpage, that gains a Microsoft logo and QR code, lacks controls to gash or shut it, requiring victims to discontinuance both the browser route of and the major payload route of to prevent persistence, and a affirmation code serves as proof of fine recordsdata equipped by the sufferer.
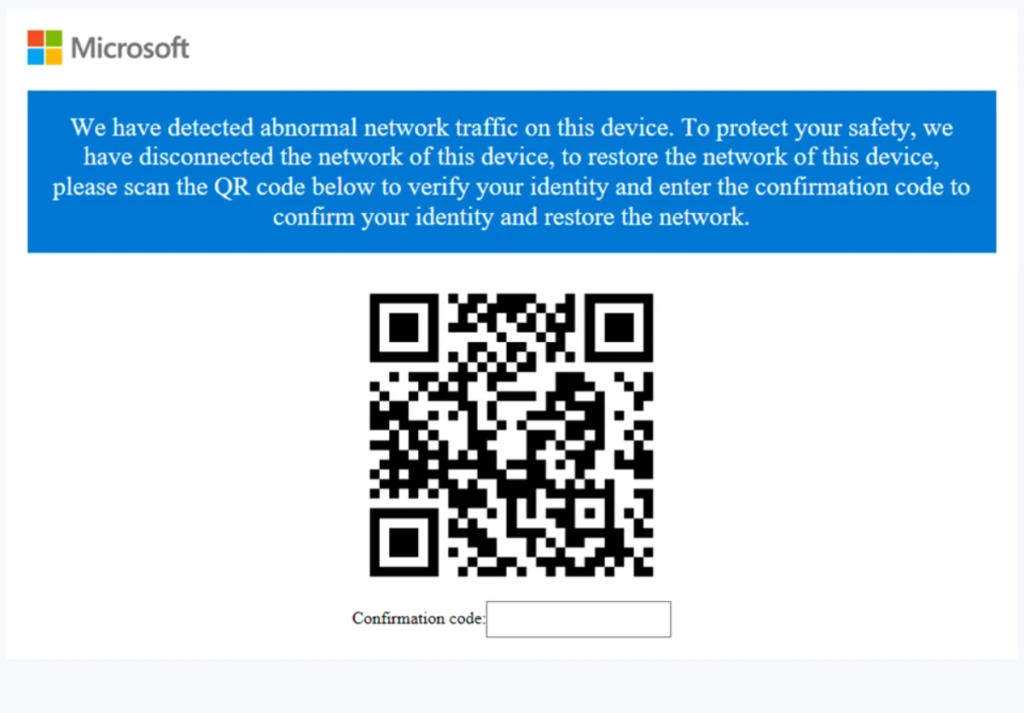
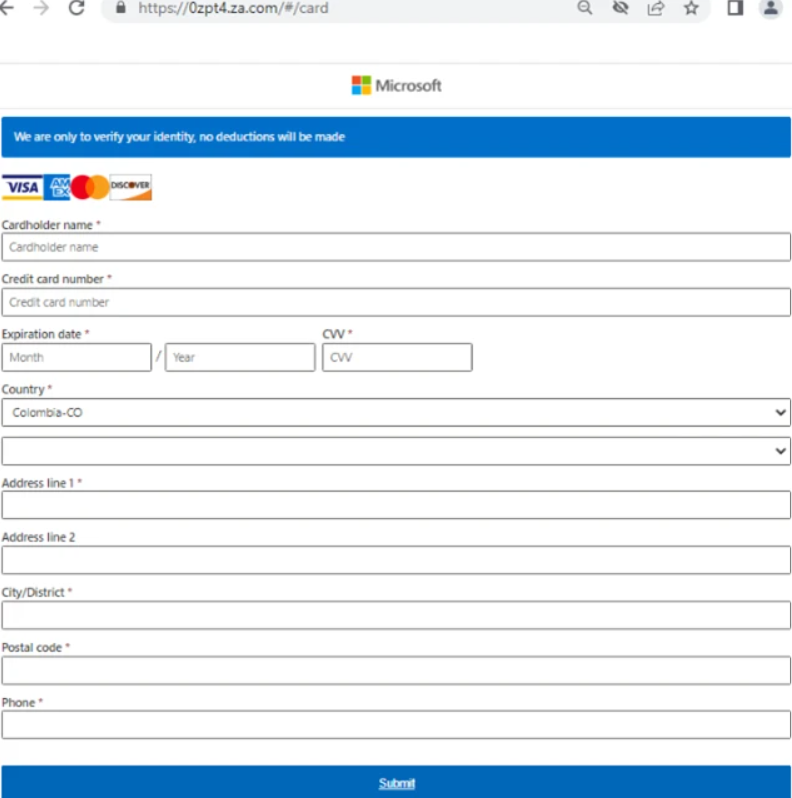
The phishing URL items the sufferer with a affirmation page, followed by a page requesting sensitive recordsdata comparable to bank card runt print contend with:-
- Bank card number
- Expiration date
- CVV code
CopperPhish is a global phishing marketing campaign concentrating on bank card recordsdata, suggesting that the possibility actor has just a few targets concurrently.
Besides this, the cybersecurity analysts additionally highlighted that Water Orthrus had shifted its focal level from deepest recordsdata and cryptocurrency to concentrating on bank card recordsdata.
Then again, proactive security features can safeguard organizational devices against such threats.
Source credit : cybersecuritynews.com

