Bug in Honda, Nissan, Toyota Cars App Let Hackers Unlock & Start The Car Remotely

A significant vulnerability uncovered in Honda, Nissan, Infiniti, and Acura vehicle apps lets hackers and laws enforcement agencies liberate the vehicle remotely and commence the vehicle with a laptop from anyplace within the field.
The significant worm exists in SiriusXM, a connected vehicle platform that provides services to services to Acura, BMW, Honda, Hyundai, Infiniti, Jaguar, Land Rover, Lexus, Nissan, Subaru, and Toyota.
For the length of routine be taught, Sam Curry, a Web utility security researcher, and his crew found a significant vulnerability within the connected vehicle’s faraway administration provider that has enrolled with SiriusXM mobile apps.
The be taught has no longer splendid highlighted how one vulnerability could maybe have a bodily originate on a large different of vehicles but additionally how great non-public recordsdata could maybe be retrieved from a vehicle.
Investigation Towards Discovering the Malicious program
A Domain “http://telematics(.)secure” used to be found on this be taught and is connected with enrolling vehicles within the SiriusXM faraway administration performance.
Extra diagnosis of this enviornment finds that quite a variety of references are pointed to the Nissan Automobile Linked App.
Later switch ahead to log in to the app and peep the HTTPS net site traffic from one in every of the Nissan vehicle owners.
For the length of the scan, researchers found that there used to be one HTTP question, particularly, that used to be attention-grabbing: the “exchangeToken” endpoint would return an authorization bearer reckoning on the provided “customerId”.

Within the above HTTPS question, a VIN” parameter used to be removed and silent works, in a single more hand, the question will get failed if utterly different issues “nissancust” prefix and “Cv-Tsp” header will be modified.
Pull the Customer Files Out
“Extra diagnosis of one in every of the HTTP responses researchers observed the following format of a VIN quantity: vin:5FNRL6H82NB044273, This VIN format looked eerily identical to the “nissancust” prefix from the earlier HTTP question. What if we tried sending the VIN prefixed ID because the customerId?” The researcher talked about in his tweet.
Thru passing the VPN prefixed ID as a customerID, researchers fetch a bearer Toke return along with “200 OK” response of the following:
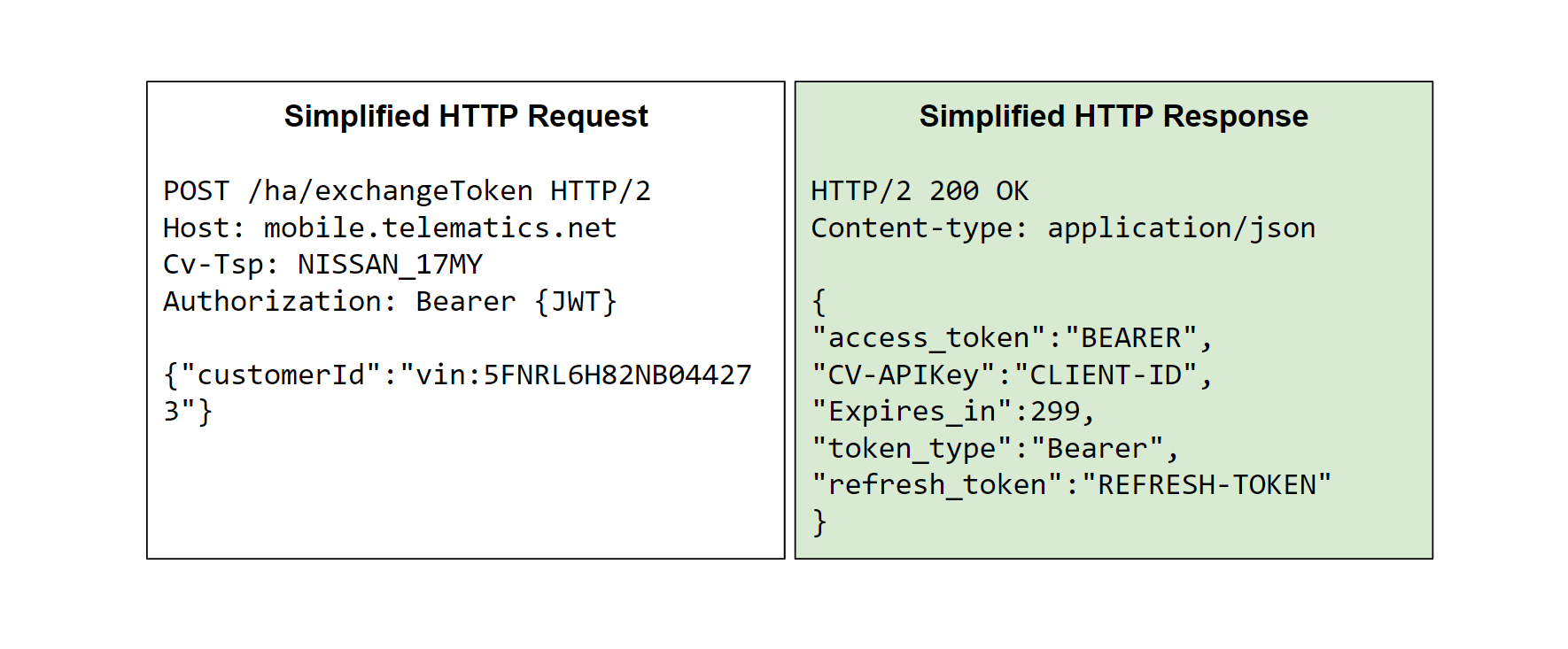
“This used to be thrilling, we have been generating some token and it used to be indexing the arbitrary VIN because the identifier. To verify that this wasn’t connected to our session JWT, we fully dropped the Authorization parameter and it silent labored!”
To catch the user profile, researchers try to make divulge of the Authorization bearer in an HTTP question, in response, they’ve successfully retrieved the sufferer’s name, cell phone quantity, address, and vehicle information.

By splendid having the VIN quantity, any attackers can catch the customer information with the inspire of a python script and a continuous escalation lead researchers to search out the HTTP question to bustle vehicle instructions.
Finally, at this point, attackers will access customer recordsdata and bustle vehicle instructions to liberate the vehicle and commence the vehicle remotely.
Researchers have successfully tested this worm on Honda, Infiniti, and Acura vehicles besides to Nissan vehicles and reported the subject to SiriusXM who fastened it at this time.
Source credit : cybersecuritynews.com


