What is OAuth 2.0 ? How it Works ? A Detailed Explanation of Authorization Framework

OAuth 2.0 is the trade-customary protocol for authorization. OAuth 2.0 supersedes the work performed on the authentic OAuth protocol created in 2006.
The OAuth 2.0 authorization framework permits a Third-occasion application to get slight get admission to to an HTTP provider, both on behalf of a resource owner by orchestrating an approval interplay between the resource owner and the HTTP provider, or by allowing the third-occasion application to get get admission to by itself behalf.
OAuth 2.0 Earlier Practices
1. Straightforward Login: Hold-primarily based entirely mostly Authentication
Disadvantages-
- Making sure security of each and every login activity
- Affirming the categories , hashing algorithms , cookies , session variables etc.
2. Single-Ticket-On : SAML (Security Assertion Markup Language)
Security Assertion Markup Language is an open customary for exchanging authentication and authorization recordsdata between parties, in instruct, between an identification supplier and a provider supplier. SAML is an XML-primarily based entirely mostly markup language for security assertions.
3. Delegated Authorisation
Allowing a range of sites to get admission to a resource owner’s recordsdata saved in some a range of web situation without giving the Password.
Earlier Alternate choices for Delegated Authorization
1. Suppose
That is an instance whereby Suppose wanted to resolve the risk of delegated authorization and incorporated a manner with which a individual might perchance perchance let Suppose get admission to some piece of his/her recordsdata from his most modern mail ID by entering their mail ID and Password for the identical.

2. Facebook
That is an instance whereby Facebook wanted to resolve the risk of delegated authorization and incorporated a manner with which a individual might perchance perchance let Facebook get admission to some piece of his/her recordsdata from his most modern mail ID by entering their mail ID and Password for the identical.

Disorders with Earlier Alternate choices
In the proven cases, a individual will want to correct believe Suppose or Facebook and consider that they retain his/her mail ID and password gain and additionally that they do not get admission to any a range of recordsdata excluding what they requested for.
These gather been afraid and frightful ways to implement delegated authorization and left the person’s credentials to boot to his/her tale at peril repeatedly.
Alternate choices for Delegated Authorization As of late
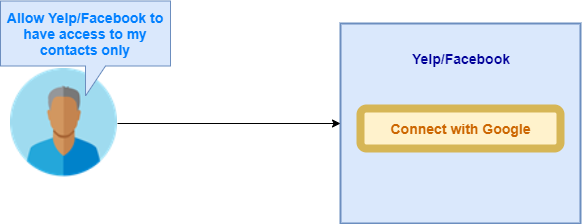
In the given instance, the person is asking Google to enable Suppose/Facebook to get admission to most efficient his contacts utilizing Google APIs.
Right here, after authenticating the person, Google API will grant get admission to of the person’s contacts to Suppose/Facebook.
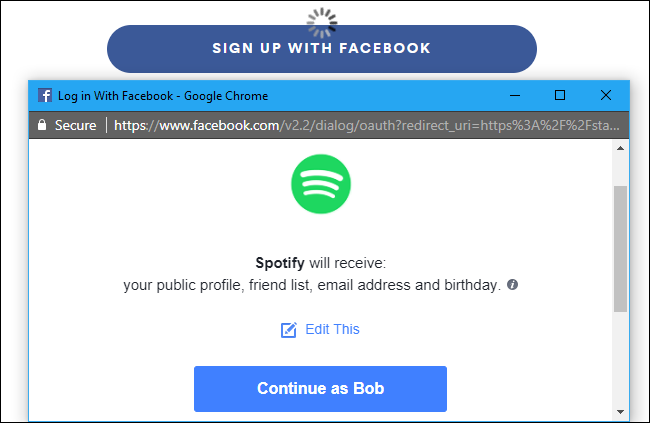
A Proper Life Instance
The following are precise-lifestyles examples that involve a gain implementation of delegated authorization.
Right here, Spotify desires to get admission to one of the indispensable indispensable person’s Facebook recordsdata.
OAuth 2.0 Terminology
Taking an instance of a individual searching to login into LinkedIn utilizing Gmail(Google) API and credentials-
- Resource Proprietor: The individual that is interacting with the applying (the individual owns the suggestions the applying desires to get to)
- Client: The application with which the person is interacting straight (LinkedIn)
- Authorization Server: The server which is conventional to Authorize the demand despatched by the client for the person’s recordsdata (Gmail)
- Resource Server: The API or the design that really holds the client’s recordsdata (Gmail API )
- Authorization Grant: The entity that proves that permission is granted to the client by the Authorization Server
- Redirect URI: After the Authorization Grant is given by the Authorization Server , it is despatched to the client , to the callback handle supplied by the client, this callback is frequently identified as Redirect URI
- Obtain admission to Token: It is miles the important thing conventional by the client to get admission to the sources it has been granted get admission to to , at the Resource Server
Channels
There are two sorts of channels whereby the total course of occurs.
- Entrance Channel: It is miles the initial (no longer so gain) channel between the person’s browser aspect client and the Authorisation Server.
- Support Channel: It is miles the highly gain channel between the Client’s Server and the Authorization Server and the Client’s Server and the Resource Server.
Client Kinds
OAuth defines two client forms, in preserving with their potential to authenticate securely with the authorization server (i.e., the potential to defend the confidentiality of their client credentials):
Confidential: Potentialities able to affirming the confidentiality of their credentials (e.g., the client implemented on a gain server with restricted get admission to to the client credentials), or able to gain client authentication utilizing a range of plot.
Public: Potentialities incapable of affirming the confidentiality of their credentials (e.g., clients executing on the design conventional by the resource owner, much like an installed native application or a web browser-primarily based entirely mostly application), and incapable of gain client authentication through any a range of plot.
Protocol Endpoints
The authorization course of utilizes two authorization server endpoints (HTTP sources):
Authorization endpoint — conventional by the client to get authorization from the resource owner through individual-agent redirection.
Token endpoint — conventional by the client to trade an authorization grant for an get admission to token, in most cases with client authentication.
Besides to one client endpoint:
Redirection endpoint — conventional by the authorization server to come help responses containing authorization credentials to the client through the resource owner individual-agent.
Straightforward Illustration of OAuth 2.0 in Action
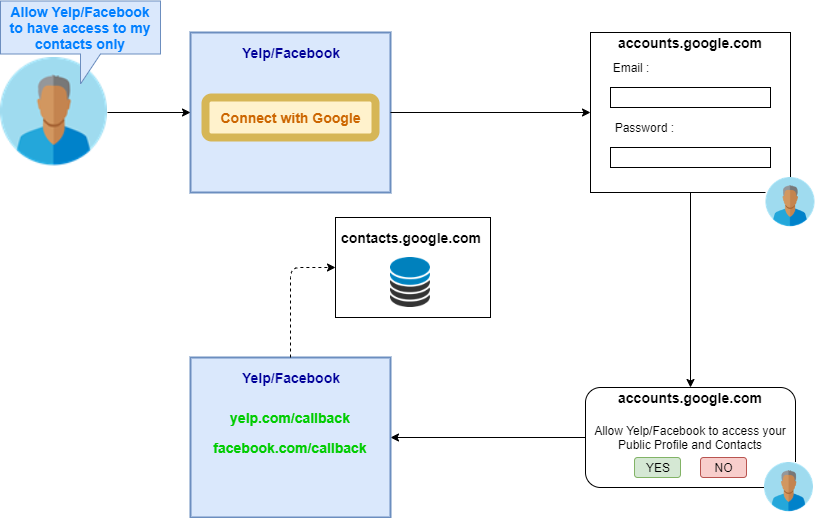
Steps:
- Suppose/Facebook desires to get admission to the person’s Gmail contacts, so that they provide the possibility to place so utilizing Google’s API
- As soon because the person clicks on Join with Google, he’s redirected to a google endpoint the place he’s requested to enter his gmail credentials (Authentication)
- When the Authentication is price it, the person is requested whether he desires to enable Suppose/Facebook to get admission to his recordsdata or no longer
- If the person clicks on Sure, he’s redirected help to Suppose/Facebook, and Suppose/Facebook is given get admission to to his contacts.
- If the person clicks on No, the get admission to demand is terminated.
We can scrutinize that the formula whereby Suppose/Facebook accesses Gmail contacts has dotted lines, which implies that it takes station during the Support Channel.
The solid lines dispute the Entrance Channel.
OAuth 2.0 Authorisation Grant
An Authorisation Grant is a credential representing the resource owner’s authorization (to get admission to its gain sources) conventional by the client to get an get admission to token.
It has the next forms:
1. Authorisation Code
The authorization code is got by utilizing an authorization server as an intermediary between the client and the resource owner.
In station of inquiring for authorization straight from the resource owner, the client directs the resource owner to an authorization server through its individual agent, which in flip directs the resource owner help to the client with the authorization code.
Earlier than directing the resource owner help to the client with the authorization code, the authorization server authenticates the resource owner and obtains authorization.
For the reason that resource owner most efficient authenticates with the authorization server, the resource owner’s credentials are by no plot shared with the client.
2. Implicit
The implicit grant is a simplified authorization code drift optimized for clients implemented in a browser utilizing a scripting language much like JavaScript.
In the implicit drift, as but one more of issuing the client an authorization code, the client is issued an get admission to token straight.
When issuing an get admission to token all around the implicit grant drift, the authorization server would no longer authenticate the client. In some cases, the client identification will be verified during the redirection URI conventional to hiss the get admission to token to the client.
3. Resource Proprietor Password Credentials
The resource owner password credentials (i.e., username and password) will be conventional straight as an authorization grant to get an get admission to token. The credentials might perchance perchance simply calm most efficient be conventional when there might perchance be a excessive degree of believe between the resource owner and the client, and when a range of authorization grant forms must no longer accessible.
4. Client Credentials
The patron credentials (or a range of sorts of client authentication) can be conventional as an authorization grant when the authorization scope is slight to the gain sources below the control of the client, or to gain sources beforehand arranged with the authorization server.
Client credentials are conventional as an authorization grant in most cases when the client is performing by itself behalf (the client is additionally the resource owner) or is inquiring for get admission to to gain sources in preserving with an authorization beforehand arranged with the authorization server.
OAuth 2.0 Obtain admission to and Refresh Tokens
Obtain admission to tokens are credentials conventional to get admission to gain sources. An get admission to token is a string representing an authorization issued to the client.
The string is in overall opaque to the client. Tokens dispute instruct scopes and periods of get admission to, granted by the resource owner, and enforced by the resource server and authorization server.
Refresh tokens are credentials conventional to get get admission to tokens. Refresh tokens are issued to the client by the authorization server and are conventional to get a brand unique get admission to token when the present get admission to token becomes invalid or expires, or to get extra get admission to tokens with an identical or narrower scope (get admission to tokens might perchance perchance simply gather a shorter lifetime and fewer permissions than authorized by the resource owner).
Issuing a refresh token is non-obligatory at the discretion of the authorization server. If the authorization server disorders a refresh token, it is incorporated when issuing an get admission to token.
A refresh token is a string representing the authorization granted to the client by the resource owner. The string is in overall opaque to the client.
The token denotes an identifier conventional to retrieve the authorization recordsdata. Now not like get admission to tokens, refresh tokens are supposed to be used most efficient with authorization servers and are by no plot despatched to resource servers.
Acquiring Authorisation Instance: Authorisation Code Grant

Steps:
- Suppose/Facebook desires to get admission to the person’s gmail contacts, so that they provide an plot to place so utilizing Google’s API.
- As soon because the person clicks on Join with Google , he’s redirected to an Authorisation Server the place he’s requested to enter his gmail credentials (Authentication). This demand additionally contains the Redirect URI , Response Style and Scope of the demand.
- When the Authentication is price it, the person is requested whether he desires to enable Suppose/Facebook to get admission to his recordsdata or no longer.
- If the person clicks on Sure , he’s redirected help to Suppose’s/Facebook’s Redirect URI, alongside with an Authorisation Code.
- If the person clicks on No , the get admission to demand is terminated.
- Suppose’s/Facebook’s Server then exchanges the Authorisation Code with the Authorisation Server, and in response, is given an Obtain admission to Token by the Authorisation Server.
- Suppose’s/Facebook’s Server then sends the suggestions get admission to demand to the Resource Server alongside with the Obtain admission to Token, and in response, is given get admission to to the suggestions in scope.
Summary Protocol High-tail alongside with the recede — OAuth 2.0

Refreshing an Expired Obtain admission to Token

Source credit : cybersecuritynews.com


