Hackers Use Google AMP Pages to Bypass Enterprise Email Security Measures

A brand unusual phishing tactic used to be found that takes preferrred thing about Google Accelerated Cell Pages (AMP), which is basic to assign success in bypassing e-mail security infrastructure.
An originate-source HTML framework known as Google AMP is venerable to diagram web sites that are mobile and browser smartly matched. Google’s servers host AMP pages, the place aside inform material is streamlined and among the heavier media substances are pre-loaded for quicker beginning.
Threat actors have begun using Google AMP URLs as hyperlinks internal their phishing emails as share of a unusual system. These hyperlinks have a video display file of successfully contacting endeavor-level workers since they are hosted on depended on domains.
The reason of utilizing Google AMP URLs in phishing emails is to give up e-mail security abilities from flagging messages as faux or suspicious owing to Google’s popularity.
The AMP URLs cause a redirection to a faux phishing web place aside, and this extra step also adds an diagnosis-disrupting layer.
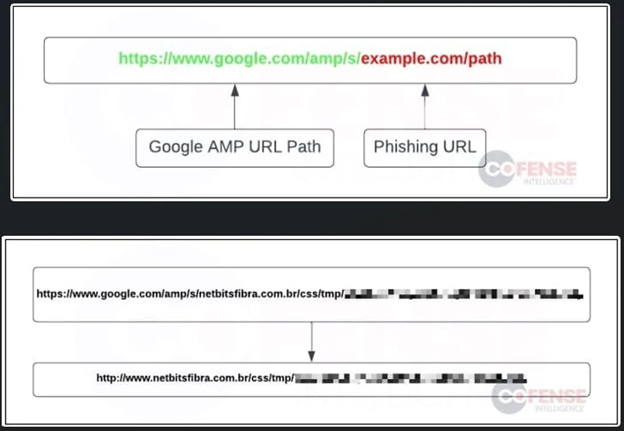
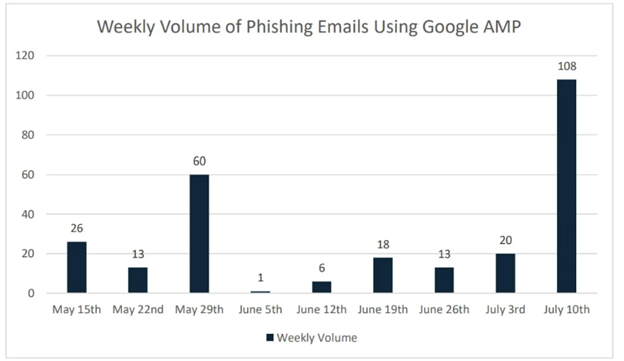
Seriously, the utilization of URLs in phishing attacks focusing on employee login credentials first surfaced in May maybe perhaps perhaps also merely 2023 and has persisted as of the time of this writing.
Per the Confense document, URLs are extremely efficient at reaching consumers in environments true by true e-mail gateways (SEGs).
“Out of the total Google AMP URLs we have now seen, approximately 77% were hosted on the area google.com and 23% were hosted on the area google.co.uk”, experiences Confense.
“The URL pathing is an efficient indicator for this phishing campaign, but it is complicated to outright block “google.com/amp/s/” as a result of the reliable uses.”
Noticed Programs Frail In The Campaigns
Relied on domains are continuously utilized across all phases of phishing makes an try, now now not merely the first Google area.
Lots of campaigns utilizing the Google AMP attain have seen URL redirection as a a part of the URL as smartly as an additional stage. Disrupt diagnosis positive elements a unusual layer as a results of this.

Image-primarily based entirely mostly phishing emails had been utilized. By substituting a frequent text body with an encoded HTML image that has a malicious embedded link and is clickable by the receiver, the menace actor can disrupt diagnosis.
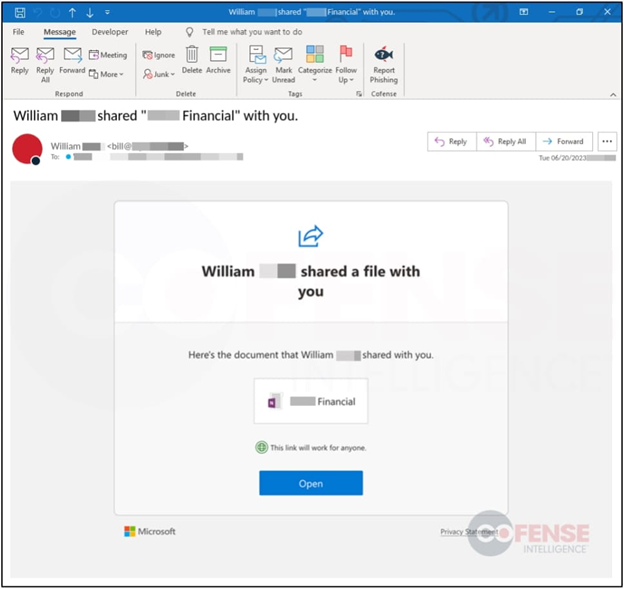
“The lures on the succor of those emails have a range of, but are primarily e-mail notifications, requests, reminders, shared files, or are finance connected,” Confense.
Cloudflare CAPTCHA is now now not sharp that it has surfaced because it has been a assuredly employed tactic in phishing attacks. Utilizing CAPTCHA companies disrupts computerized diagnosis and necessitates a manual examination of every phishing campaign.
Campaigns that apply this tactic have shown to be pretty elusive, and in addition they expend a range of TTPs that are known to bag around e-mail security infrastructure.
Source credit : cybersecuritynews.com


