DangerousPassword Attacks Targeting Windows, macOS, and Linux Software Developers

Python-essentially based entirely malware targets Windows, linux, and macOS and is presumed to be old fashioned by dangerous password attack groups, incessantly identified as Crypto mimics.
This group has been energetic since June 2019 and employs varied tactics to elevate malware to the sufferer’s machine.
JPCERT/CC released the newest article about attacks confirmed by the campaigns and shared their diagnosis narrative.
Focusing on Windows
For the reason that attack vector of this advertising campaign is unknown, the infection scamper together with the circulation after the execution of the malware is expounded to that of the Linkedin attack by this group.
In the foundation, the malware file builder.py of the Python module is dropped on the sufferer machine, which downloads additional malware as soon because it will get done by the client.
The malware downloads and runs additional MSI files externally using a Powershell script that’s dropped after the execution.
The malware communicates with the C2 server every minute and is to blame for the download and execution of additional malware.
Apart from, the secondary sample of the MSI file downloaded by the Powershell script encodes the client name, OS, direction of knowledge, etc. of the contaminated machine with BASE64 and sends it to the C2 server.
Also, it makes use of PythonHTTPBackdoor malware with straightforward instructions to develop the attack, which has a feature to detect the OS ambiance, and the instructions done are a minute bit numerous relying on the ambiance.
Linux and macOS:
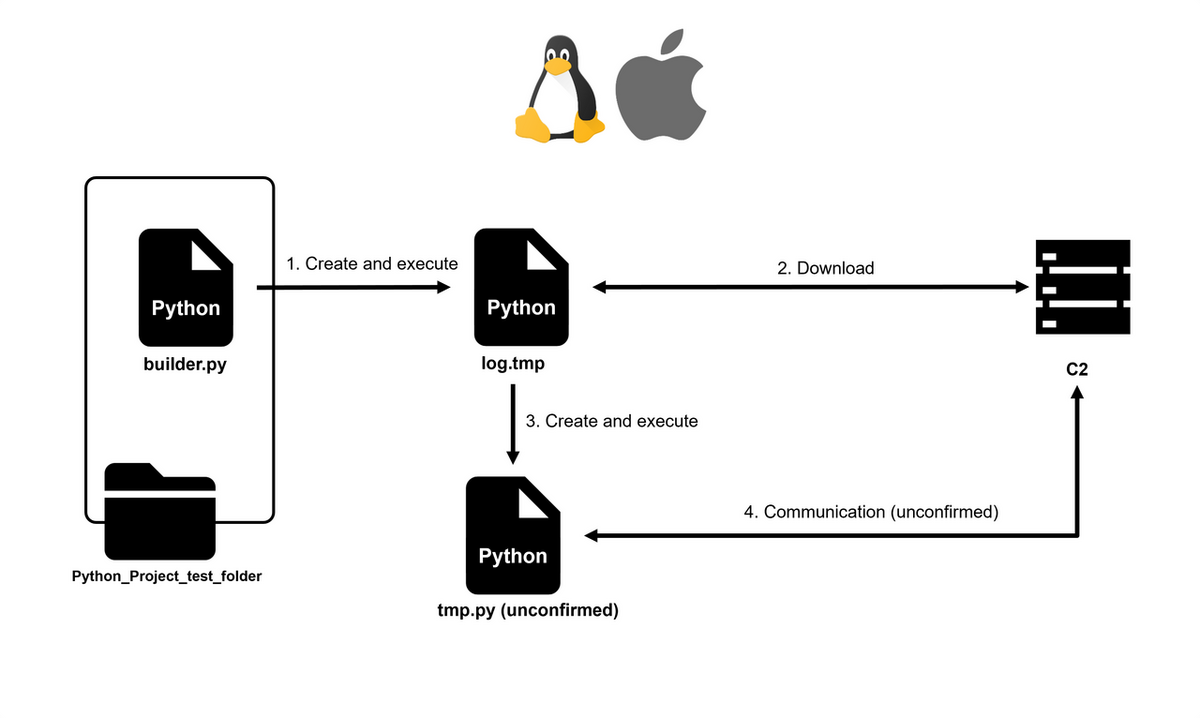
In macOS and Linux environments, the builder.py file is decoded and saved as a log. tmp, and done as a Python file.
The patron ID and OS ambiance knowledge are despatched to the C2 server every minute and decoded with BASE64, saving it as tmp.py.
PythonHTTPBackdoor has ROT13-encoded git-linked strings in the ask string and generated file name, proper admire a log. tmp, which indicates that Git is old fashioned. That you must possibly possibly presumably spy that it is miles focusing on developers.
As an illustration, the notify identity 501 is old fashioned to retrieve the community and direction of knowledge, and 502 is old fashioned to develop the instructions in Windows, Linux, and macOS machines.
In the same vogue, Mach-O malware JokerSPYand node.js malware are being old fashioned by this attack group to target the victims.
Indicator of compromise
118c1187c5b37ab9c4f9f39500d777c0a914c379d853439608157379dcb71772
35b4550050748c54faad1e5883c281f29c08e817cc193432e7b9b43124a7962a
575e852a1f24e84dacec9892042f2d2c1668bd836f9f5b03ed447f68caa7b612
e0891a1bfa5980171599dc5fe31d15be0a6c79cc08ab8dc9f09ceec7a029cbdf
2eea41eefdc11f9fb7607fc4ef90f76ef03b119eda8ee35ebff37b345f559e0e
474c8a5ba3614cca1c48f34df73bfad753a95a67998485696391499d9bdba430
1599f7365db421e4fe07a169309624e7e25d4f28cd1b101d340d54d66b6eb921
528ac7bdd56a6e7ff515c6e0936db66c987e731482845dcd64a96af0f42fc95a
56c6ab0083cf7edae7491e9c49b0cd9b4bb6b1fb61b5facf9ddb034ea69125f7
a7b0fa9c724e7837da97dc9c48ba76b22759e514afc305d43e87a69fa9089d4c
39bbc16028fd46bf4ddad49c21439504d3f6f42cccbd30945a2d2fdb4ce393a4
5fe1790667ee5085e73b054566d548eb4473c20cf962368dd53ba776e9642272
84bfc8c5bdba5b4eaa885af5e698382dd6baa0bf8da967c0716a0a6fce3e742a
67a0f25a20954a353021bbdfdd531f7cc99c305c25fb03079f7abbc60e8a8081
37850b6a422479e95e9fb856f3541a36cfd753070e2d10c7362f328231af5370
aa951c053baf011d08f3a60a10c1d09bbac32f332413db5b38b8737558a08dc1
6d3eff4e029db9d7b8dc076cfed5e2315fd54cb1ff9c6533954569f9e2397d4c
951039bf66cdf436c240ef206ef7356b1f6c8fffc6cbe55286ec2792bf7fe16c
d895075057e491b34b0f8c0392b44e43ade425d19eaaacea6ef8c5c9bd3487d8
6d3eff4e029db9d7b8dc076cfed5e2315fd54cb1ff9c6533954569f9e2397d4c
951039bf66cdf436c240ef206ef7356b1f6c8fffc6cbe55286ec2792bf7fe16c
aa951c053baf011d08f3a60a10c1d09bbac32f332413db5b38b8737558a08dc1
d895075057e491b34b0f8c0392b44e43ade425d19eaaacea6ef8c5c9bd3487d8
Source credit : cybersecuritynews.com


