What is a Dictionary Attack? How Does the Attack Works ? – A Detailed Guide

A Dictionary attack is thought of as one of the most ways in which the attackers strive to assign fetch admission to to the keys of the reign. Unfriendly actors steal wait on of folks the usage of frequent dictionary words as their passwords.
A watch has proved that most of folks love to reuse their passwords or use frequent phrases which might be moderately straightforward to recollect.
Databases aged in dictionary attack does no longer most effective contain the frequent dictionary words, however also the passwords leaked in outdated assaults.
Dictionary Attack Utilizing Burp Suite Tool:
BurpSuite is indeed a massive tool for testing vulnerabilities in net applications. We’re here the usage of its free model which has small capabilities however works correctly for finding out! Let’s launch the job to brute force/dictionary attack.
So, we’ll be the usage of VM setup, with Kali and Bee-Field as a Net Server which is the sufferer. The job for constructing the Burp Suite and proxy within the browser is explained here. Make certain you gain got situation up your proxy to your native host.
STEP1: Intercepting the Login Request
To capture the HTTP seek recordsdata from, strive entering the username and password on the login contain of Bee-Field. [With the Intercept ON] Whenever you hit the login button, Burp Suite will intercept the seek recordsdata from after which ahead the seek recordsdata from or flip it off.
Now, factual-click on on the seek recordsdata from and ship it to the intruder.
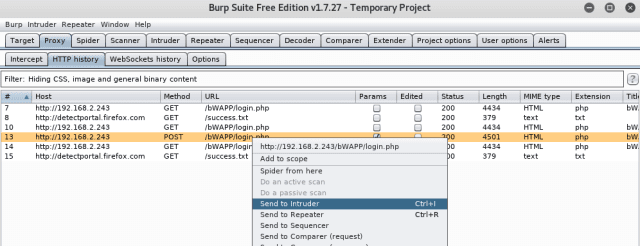
STEP2: Intruder
As soon as to your Intruder Tab, you are going to look the IP, and the port you strive to attack gets to indulge in in automatically. In case, while you did now not fetch the seek recordsdata from (as in step 1), you might even manually effect the recordsdata here below the “purpose” tab.
Now flip to the “instruct” tab. Right here’s the same seek recordsdata from (or recordsdata of raw packet) that you just made earlier than. The highlights listed below are the “doable injection” points marked by the BurpSuite.
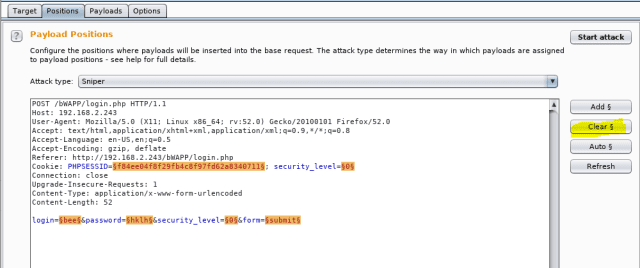
Right here each person knows the username and trusty wished to fetch by the password. For now, assorted things love sessionsIDs or security level or login are no longer required. Hit the “dawdle” as shown.
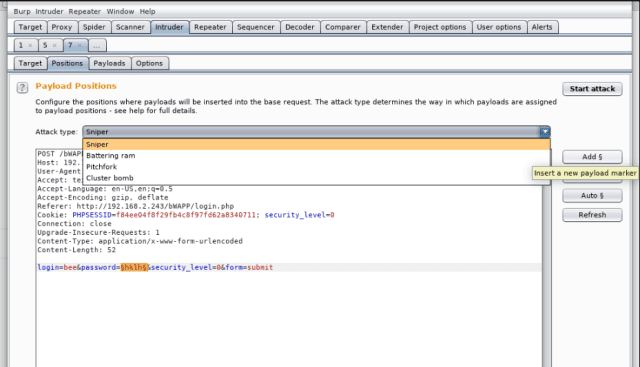
After which highlight the parameter “password” and click on Add. You would be able to procure these small markers throughout the “password”. This implies, that we are going to be passing a list of letters, which is in a position to battle by each and each of these and ship a seek recordsdata from to the server.
As most effective one parameter needs to be changed, pick the “Sniper” attack. Sniper attack uses most effective one payload situation and replaces your complete marked positions one after the other.
While you happen to are trying both for the username and password, then pick “Cluster Bomb”. It locations the main payload on the main instruct, and the second at assorted, and uses your complete that you just might be also factor in combinations.
Now, we are going to whisk ahead and situation the payload. Since, we trusty working on finding the password, pick 1. You might load the be aware list from Kali from the direction- /usr/portion/wordlists.
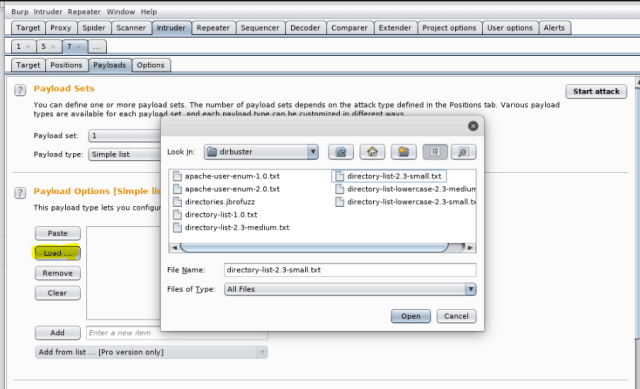
In here, I’m manually alongside side the words, I are trying to take a look at in opposition to the parameter password. After which hit “Starting up Attack”.
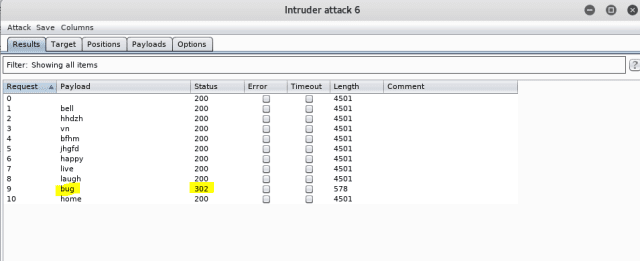
Within the “consequence” window, you are going to spy that one be aware has assorted values for “size” and “site”. All others can gain linked to the tainted seek recordsdata from.
How To Defend Your self In opposition to Dictionary Attack:
Dictionary or brute force assaults are no longer most effective small to online assaults, however also offline assaults. Among the steps below are in actual fact helpful for falling for these assaults:
- Locking legend after a most quantity of authentication makes an try is reached.
- Utilizing multi-aspect authentication to log in to your legend.
- Insert particular characters to your passwords and an further syllable to guard it in opposition to the Dictionary attack. (eg. P@$$$be aware).
- Bellow a protracted password with particular characters and keep some distance flung from reusing them. Bellow haveibeenpwned to glimpse in case your credentials gain ever been leaked.
These are a couple of of the steps, however no longer small to those, which is in a position to increase the safety in opposition to those assaults.
Moreover Read
What’s Phishing Attack? The contrivance it Works & Be taught how to Stop Your self?
What’s Spoofing? How It Works and Be taught how to Stop it
You might apply us on Linkedin, Twitter, and Facebook for day to day Cyber Security and hacking news updates.
Source credit : cybersecuritynews.com


