Linux Kernel Flaw Let Attackers Gain Full Root Access: PoC Published
.webp)
Security researchers hang uncovered a extreme vulnerability in the Linux kernel’s io_uring subsystem, which might perchance well allow attackers to originate full root gain admission to to affected systems.
The flaw, tracked as CVE-2024-0582, became realized to be seriously exploitable in Ubuntu distributions because of a prolong in patching despite the vulnerability being addressed in the real kernel unencumber in December 2023.
AI-Powered Protection for Business E mail Security
Trustifi’s Evolved possibility protection prevents the widest spectrum of sophisticated attacks sooner than they reach a user’s mailbox. Strive Trustifi Free Threat Scan with Sophisticated AI-Powered E mail Protection .
CVE-2024-0582: The Spend-After-Free Vulnerability
The vulnerability stems from a exhaust-after-free (UAF) situation in the io_uring interface, a characteristic launched in Linux kernel model 5.1 to beef up the efficiency of functions with excessive I/O operations.
Without reference to its advantages, io_uring has been a hotbed for security vulnerabilities, leading to its restriction or outright disablement in environments worship ChromeOS, Google’s production servers, and Android.
CVE-2024-0582 enables an attacker to originate read and write gain admission to to previously freed pages, offering a potent exploit veteran some distance beyond the favored-or-garden UAF exploit.
This vulnerability became display camouflage in Linux kernel variations from 6.4 up to, however now not together with, 6.7, affecting most foremost Ubuntu releases equivalent to Ubuntu 23.10 and Ubuntu 22.04 LTS.
Exodus Intelligence has now not too lengthy prior to now launched a describe on a flaw display camouflage in the Linux Kernel. The flaw enables an attacker to originate elevated privileges on a system by exploiting a vulnerability in the Futex subsystem.
Patch Timeline
- December 8, 2023: The vulnerability became patched in the real kernel unencumber 6.6.5.
- January 8, 2024: The Challenge Zero challenge detailing CVE-2024-0582 became made public.
- February 22, 2024: Ubuntu sooner or later patched the challenge in kernel model 6.5.0-21 for Ubuntu 22.04 LTS and Ubuntu 23.10.
CVE-2024-0582’s exploitability lies in its potential to allow recordsdata-handiest exploits, bypassing general exploit mitigations worship Assist an eye on-Circulation Integrity (CFI).
Attackers can manipulate recordsdata to escalate privileges without altering the code execution journey. This vulnerability became exploited the exhaust of an info-handiest design, enabling a non-privileged user to impress root privileges on affected systems.
In accordance to a fresh tweet by Cyber Advising, a memory leak vulnerability has been identified as CVE-2024-0582 in the Linux kernel’s io_uring functionality.
The io_uring Interface
io_uring provides a excessive-efficiency, asynchronous I/O API, reducing the overhead resulted in by blockading system calls and recordsdata transfers between user and kernel home. Nonetheless, its complexity has made it a scheme for vulnerability study.
The io_uring API contains three system calls:
- io_uring_setup()
- io_uring_register()
- io_uring_enter()
Exploitation Strategy
The exploitation design resulted in the UAF situation by manipulating io_uring’s offered buffer rings, explicitly the exhaust of the IOU_PBUF_RING_MMAP flag.
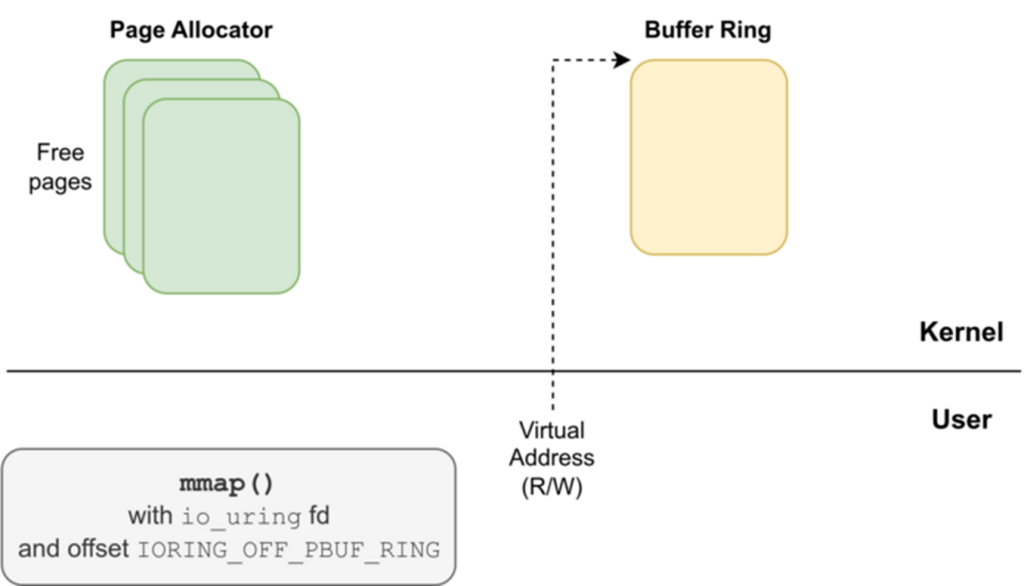
This allowed attackers to defend gain admission to to memory pages even after they had been freed and reallocated by the kernel for diversified functions, equivalent to file constructions (struct file).
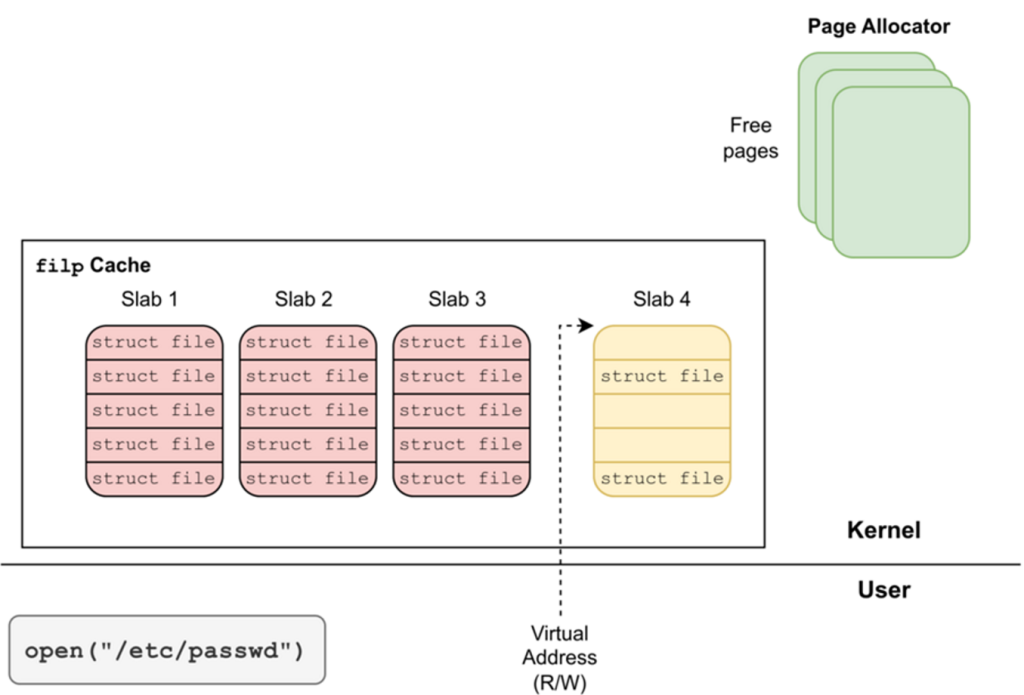
By forcing the allocation of file constructions on these managed pages, attackers might perchance well alter extreme fields, equivalent to f_mode, to originate writable gain admission to to read-handiest files, together with /and so on/passwd.
This successfully allowed the addition of a backdoor sage with root privileges.
The invention and exploitation of CVE-2024-0582 spotlight significant concerns regarding the safety of the io_uring subsystem and the timely patching vulnerabilities in broadly frail distributions worship Ubuntu.
The 2-month patch gap for Ubuntu kernels allowed attackers to profit from this vulnerability, underscoring the importance of immediate vulnerability response processes.
No longer sleep up to now on Cybersecurity news, Whitepapers, and Infographics. Notice us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


