New Rilide Malware Attacking Enterprise Employees to Steal Credentials
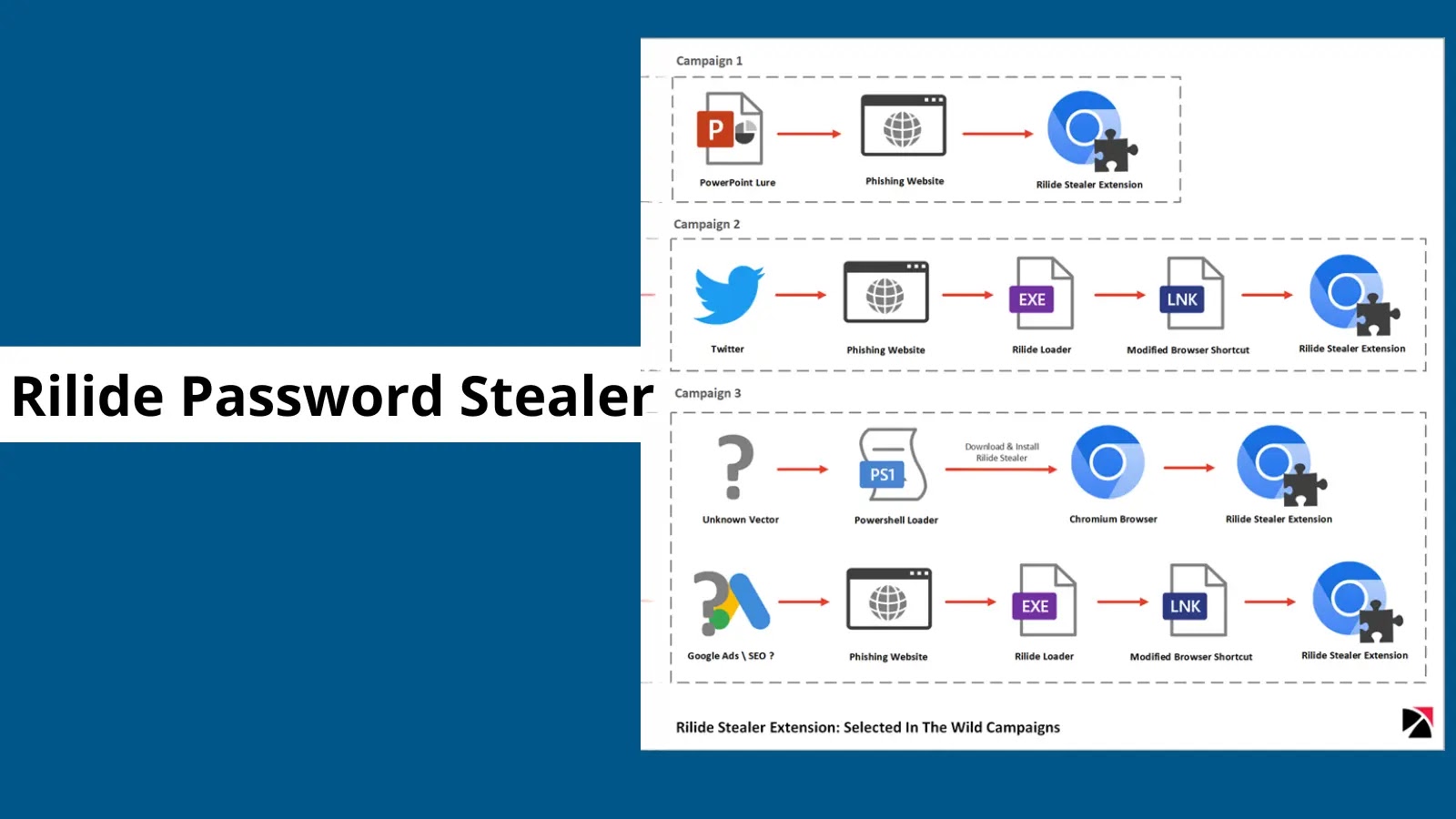
As per reports, a brand level-headed model of the Rilide stealer is identified to be stealing credentials from mission workers and crypto wallets. This level-headed model is able to bypassing the level-headed Chromium browser manifest v3.
Rilide is a malicious browser extension that turn out to be once discovered in April 2023 by Trustwave SpiderLabs. The at the 2d discovered model is no longer suffering from the Google Chrome Extensions manifest V3, which restricts in-line Javascript code execution.
Apart from, the Rilide malware extension targets banking accounts in Australia and the UK. It also captures screenshots at smartly-liked intervals and exfiltrates the stolen data into a Telegram channel.
Rilide Malware Setal Credentials
The level-headed Rilide model is able to doing a large range of actions relish enabling or disabling other browser extensions, retrieving browser history and cookies, stealing login credentials, on-demand screenshots, and malicious script injection for stealing money from cryptocurrency exchanges.
Furthermore, this newest model is added with code obfuscation and imitated as a Palo Alto GlobalProtect VPN extension on Chrome Web Store which is configured to focus on with the C2 domain edd2ed2[.]online.
Furthermore, the Rilide extension is now outfitted with a CursedChrome tool integration, allowing threat actors to browse the derive authenticated because the victim who has set up in this extension.
Furthermore, threat actors conducted Twitter campaigns utilizing Unsuitable P2E (Play to Secure) wherein avid gamers can derive NFTs (Non-Fungible Tokens) and sell them for staunch money. Users are requested to share their Twitter type out and SOL wallets to build rewards.
Likelihood actors created dedicated discord servers and dedicated web sites for this campaign. These video games are feeble to fall the Rilide and Redline stealer onto victims. Several scripts were discovered to be in vogue all throughout the investigation.
On the replacement hand, a entire file has been printed by Trustwave SpiderLabs, which offers detailed files on the attack vector, source code, and stealing suggestions of the Rilide extension.
A listing of indicators of compromise has also been launched by Trustwave, that is also feeble by security personnel to present protection to against threat actors.
Source credit : cybersecuritynews.com


