Hackers Attacking Hotel Owners & Employees as Potential Guests

Since closing summer, hotel owners and workers trust grappled with a surge in malicious e-mails disguised as typical correspondence from outdated or seemingly company.
These e-mails, many times performing as typical messages sent to the hotel’s public e-mail take care of or as pressing requests from Booking.com, goal to take workers’ login credentials or infect hotel programs with malware.
=The attackers’ tactics trust developed, making it more and more durable for hotel workers to name and thwart these threats.
In step with the experiences from Kaspersky, when concentrated on resorts, cybercriminals exploit the alternate’s inherent buyer carrier point of curiosity.
Lodge workers, alive to to gain to the bottom of conflicts and fulfill requests to preserve up their establishment’s repute, many times fall prey to those assaults.
The attackers craft e-mails that mimic real buyer inquiries or complaints, prompting workers to employ hyperlinks or initiating attachments that trust malware.
This potential termed a “buyer point of curiosity assault,” leverages the hotel’s commitment to buyer pleasure to breach its defenses.
E-mail Content: Complaints and Inquiries
The malicious e-mails on the whole apply two issues: complaints or inquiries.
In criticism-basically based totally e-mails, attackers pose as dissatisfied company, citing unethical workers behavior, double-charged bank cards, or downhearted lodging stipulations.
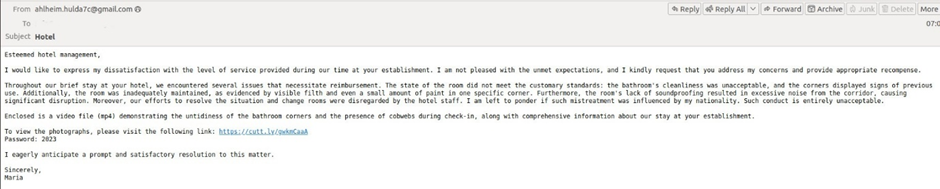
They many times include supposed evidence take care of videos, images, or bank statements to lend credibility to their claims.
In inquiry-basically based totally e-mails, attackers pose as seemingly company hunting for info about hotel products and companies and pricing.
These inquiries quilt varied topics, from room facilities to sustainable vitality sources, making them appear legitimate.
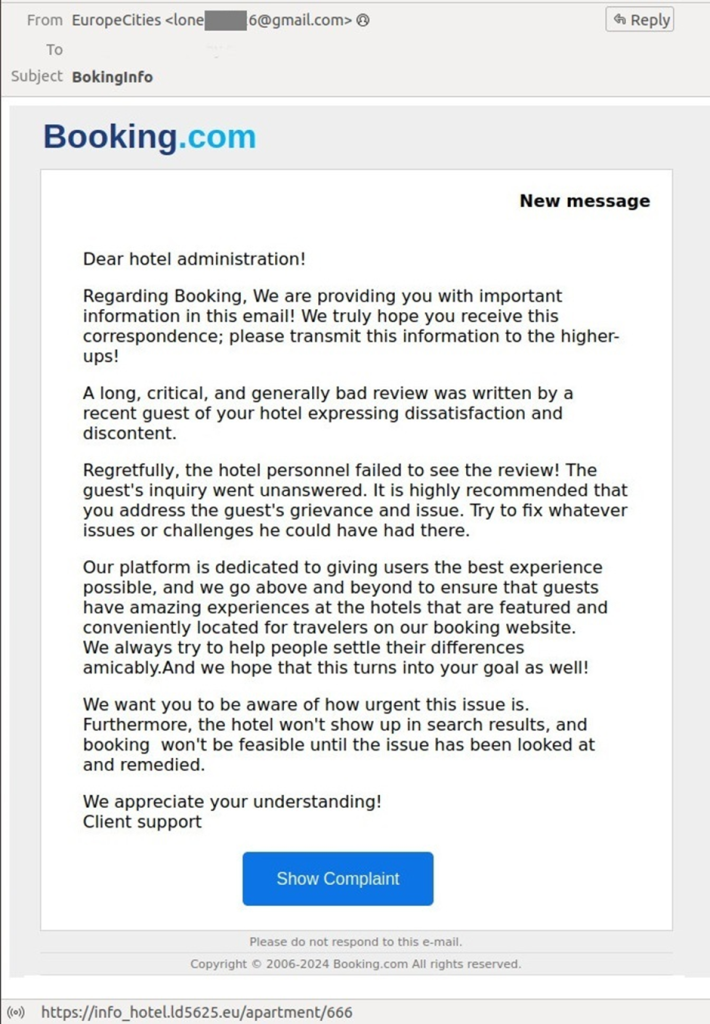
In some cases, attackers make employ of a more sophisticated potential, participating in multi-stage correspondence with hotel workers.
Within the origin, they ship innocuous messages about lodging stipulations, step by step constructing belief.
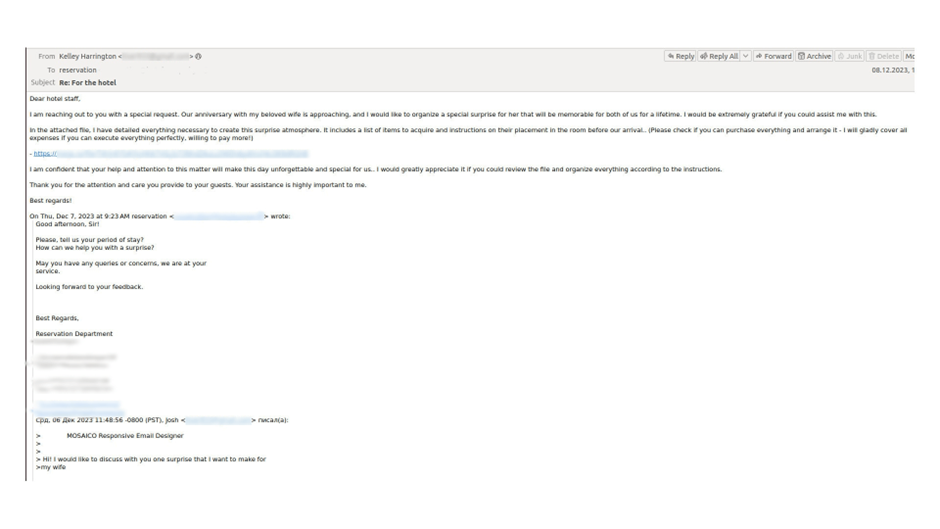
Shall we grunt, an attacker might well even pose as a seemingly buyer planning a shock for their accomplice.
After a few exchanges, they ship an e-mail with a hyperlink to a malicious file, claiming it contains detailed instructions for the shock.
This potential lulls the victim reliable into a unfounded sense of security before delivering the payload.
Pause Targets: Credential Theft and Malware Infection
The principle goal of these cybercriminals is to compose login credentials, which they can then employ in assorted scams or sell on the sad web.
Compromised hotel accounts on Booking.com might well possibly be exploited to bound-off purchasers out of charge info.
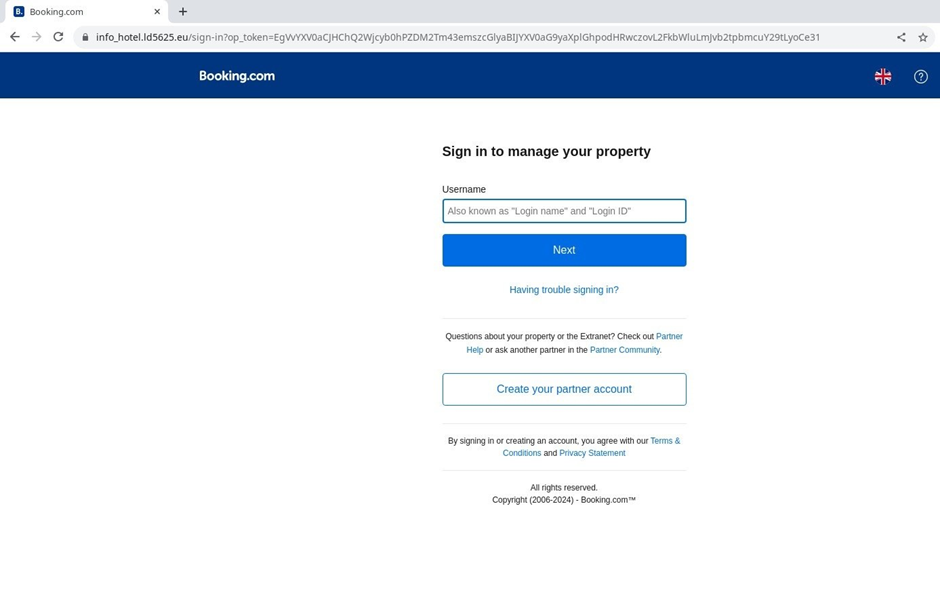
Attackers employ varied easy strategies to construct their goals, including phishing hyperlinks that mimic Booking.com login or corporate credential varieties.
They additionally make employ of malware, such as the XWorm backdoor and the RedLine stealer, to infect victims’ devices and take passwords.
The ideal technique to Defend In opposition to These Attacks
To present protection to in opposition to those sophisticated assaults, resorts might well even unruffled put in power plenty of key measures:
- Safety Awareness Coaching: Recent coaching sessions can equip workers to note and resist social engineering ways. Shall we grunt, workers might well even unruffled be trained to peek the sender’s e-mail take care of and be cautious of free e-mail products and companies weak by attackers.
- E-mail Gateway Protection: Imposing protection at the e-mail gateway stage can prevent phishing, malicious hyperlinks, and terrible attachments from reaching workers’ inboxes.
- Sturdy Safety Solutions: Placing in entire security alternate recommendations with anti-phishing expertise on all work devices can present an extra layer of protection.
- Defend Told: Retaining up-to-date with the most modern e-mail threats by legit sources might well well lend a hand resorts preserve sooner than cybercriminals’ evolving tactics.
By adopting these measures, resorts can significantly prick serve the risk of falling victim to those malicious e-mail campaigns and safeguard their operations and repute.
Source credit : cybersecuritynews.com

