Apple ID “push bombing” Attack Targeting Apple Users to Steal passwords
.jpg)
Apple customers are falling prey to a cosmopolitan phishing campaign designed to hijack their Apple IDs through what’s in most cases known as a “push bombing” or “MFA fatigue” assault.
This kind exploits the multi-ingredient authentication (MFA) device, bombarding customers with incessant notifications to approve password changes or logins, finally aiming to steal passwords and produce unauthorized assemble admission to to non-public files and devices.
The Mechanics of the Assault
Entrepreneur Parth Patel no longer too long ago grew to become a target of this phishing device, experiencing firsthand the relentless flood of device notifications across all his Apple devices, urging him to approve a password reset.
This deluge of prompts is no longer correct tense but strategically designed to wear down the victim’s resistance or get them off guard, leading to an accidental approval of the malicious quiz.
Adding a layer of sophistication to the assault, phishers observe up with phone calls masquerading as Apple Toughen, the use of caller ID spoofing to existing Apple’s official customer assist quantity.
In Patel’s case, the caller supplied correct non-public files, other than his proper name, sourced from a of us-search online page material known for inaccurately itemizing non-public small print.
This tactic lends credibility to the phishing strive and objectives to manipulate victims into offering a one-time password despatched to their tool, enabling attackers to reset the Apple ID password and lock out the person.
Krebs on Safety, a illustrious security weblog, no longer too long ago reported a chain of attacks concentrated on Apple customers, in most cases known as “MFA Bombing.”
The Role of the Cell phone Number
The expertise shared by Chris, a cryptocurrency hedge fund proprietor, underscores the serious device of the phone quantity associated with the Apple memoir in these attacks.
Despite changing his passwords and even shopping a brand fresh iPhone, Chris continued to receive the identical device indicators, suggesting that the attackers exploit a vulnerability linked to the phone quantity on file for the Apple memoir.
Cybersecurity fanatic Orbs no longer too long ago tweeted relating to the surge of “Push Bombing” attacks being focused in direction of Apple customers by hackers and scammers.
A Chronic Threat
Safety industry broken-down Ken furthermore got these unsolicited device indicators, which no longer most effective disrupted his peace but furthermore raised concerns relating to the aptitude for accidental approval of malicious requests.
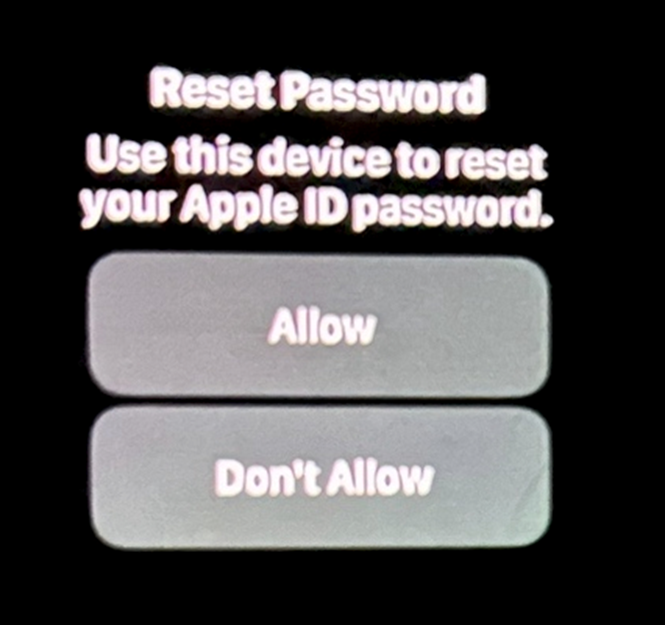
Despite taking preventive measures urged by Apple, comparable to enabling a recovery key for his memoir, Ken stumbled on that the indicators continued, indicating a extra profound field within Apple’s device that enables these password reset prompts to bypass security enhancements.
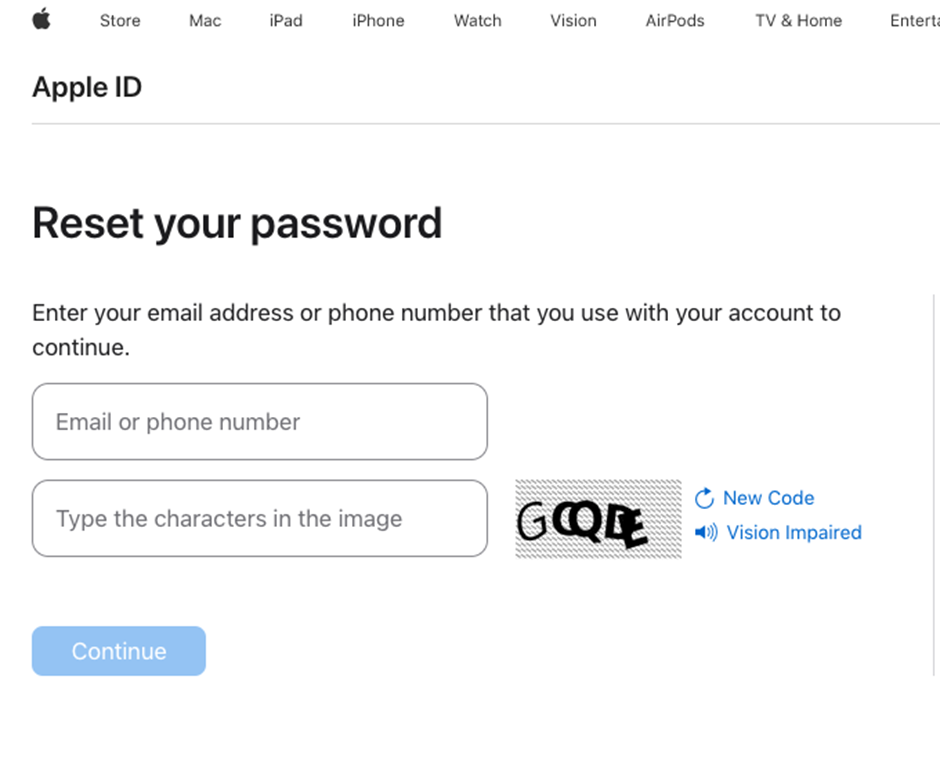
Apple’s Response and the Need for Enhanced Safety Measures
Apple has no longer publicly addressed this bellow phishing campaign or the apparent vulnerability in its device that enables for such “push bombing” attacks.
This field echoes past incidents whereby Apple needed to implement stricter rate limiting to curb an analogous exploits, suggesting that the tech big needs to reassess and provides a take to its authentication and notification systems in opposition to evolving phishing tactics.
The upward thrust of “push bombing” attacks concentrated on Apple customers highlights a rising express in digital security, where even sturdy multi-ingredient authentication systems might perchance perchance perchance also furthermore be exploited by determined attackers.
This campaign underscores the importance of vigilance amongst customers and the necessity for tech corporations to constantly evolve their security features to supply protection to in opposition to refined phishing tactics.
Because the digital landscape becomes an increasing number of fraught with threats, customers and tech giants must protect one step forward to safeguard non-public files and digital lives.
This document draws consideration to a chief and emerging possibility in digital security, urging both customers and corporations to reassess and provides a take to their defenses in opposition to refined phishing attacks.
Contend with updated on Cybersecurity files, Whitepapers, and Infographics. Apply us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


