What is DevSecOps? Benefits of Automated DevOps Security
What’s DevSecOps? Advantages of Automatic DevOps Security
DevSecOps is a technique that integrates security as a shared responsibility in each place in everything of the information technology lifecycle.
This capacity takes into legend culture, automation, and platform architecture. The DevOps methodology, which emphasizes collaboration between machine developers and IT operations, has evolved into this new capacity.
In distinction to the venerable approach of along with security controls and concerns after the DevOps course of, the DevSecOps methodology includes security concerns and controls from the very starting of the course of.
Desk of Contents:
FAQ
What’s DevSecOps?
Why is that this crucial?
Constructed-in DevOps Security
Automatic DevOps Security
FAQ
1.What’s the fundamental income of computerized enablement in DevSecOps?
The supreme income of computerized DevSecOps enabling is improved machine pattern lifecycle security. Automation in DevSecOps facilitates continuous and early security prepare integration, casting off slack-stage vulnerabilities and dear post-deployment corrections.
This improves machine security and streamlines the pattern course of, incorporating security checks and compliance with out slowing down DevOps.
Automating security processes helps corporations spy and fix security vulnerabilities faster, organising a proactive security culture that matches standard machine pattern.
2.What’s a fundamental plan of security in DevSecOps?
Security in DevSecOps aims to seamlessly integrate security practices into the course of, making security a standard and continuous ingredient of machine pattern and deployment.
As a change of hanging security closing, this integration identifies and mitigates threats early and consistently. DevSecOps aims to unify pattern, operations, and security teams by organising a culture and environment where constructing, attempting out, and deploying machine can happen posthaste, again and again, and safely.
This plan improves application security, decreases security incidents, and encourages proactive security.
3. What are the three aims of security in DevSecOps?
The three fundamental aims of security in DevSecOps are:
- Early and Continuous Integration of Security
- Collaboration and Shared Responsibility
- Automation of Security Processes
What’s DevSecOps?
A term coined from the three words “pattern,” “security,” and “ops,” “DevSecOps” refers to a form of pondering and doing machine pattern that makes security an integral piece of each and every step of the course of.
By incorporating an early emphasis on security, this capacity builds upon the suggestions of DevOps, which promote cooperation and integration between IT operations teams and machine developers.
DevOps is great bigger than steady the functional operations and pattern teams.
To accumulate primarily the most out of the responsiveness and added agility of the DevOps capacity, teams must additionally integrate IT security in each place in the lifecycle of the applying.Â
Why is that this crucial?
Within the brand new past, security tended to be isolated to steady one insist workforce that used to be active at the final stages of the app pattern. Right thru this time, the delegation of security teams at the cease of the course of used to be less of a anguish, since the cycles of pattern lasted for lots longer.Â
On the opposite hand, those days are now prolonged long gone. Smartly-liked enterprises use efficient DevOps to be obvious more frequent and rapid pattern cycles. Antiquated or outdated safety features can serve to derail even the utmost influential DevOps initiatives.
DevSecOps requires pondering the security of the applying and the infrastructure from the very start of the project. It will additionally require that some kinds of security gates be computerized to forestall the workflow of the DevOps from experiencing slowdowns. Utilizing the suitable tools to integrate security repeatedly is a crucial. Such tools as an built-in pattern environment (IDE), entire with lowering-edge security parts, could aid in doing steady that.Â
On the opposite hand, any truly efficient DevOps integration takes great bigger than steady standard tools. It additionally requires that the organization launch cultural changes via DevOps integration to be obvious that the work done by security teams is done promptly.Â
Constructed-in DevOps Security
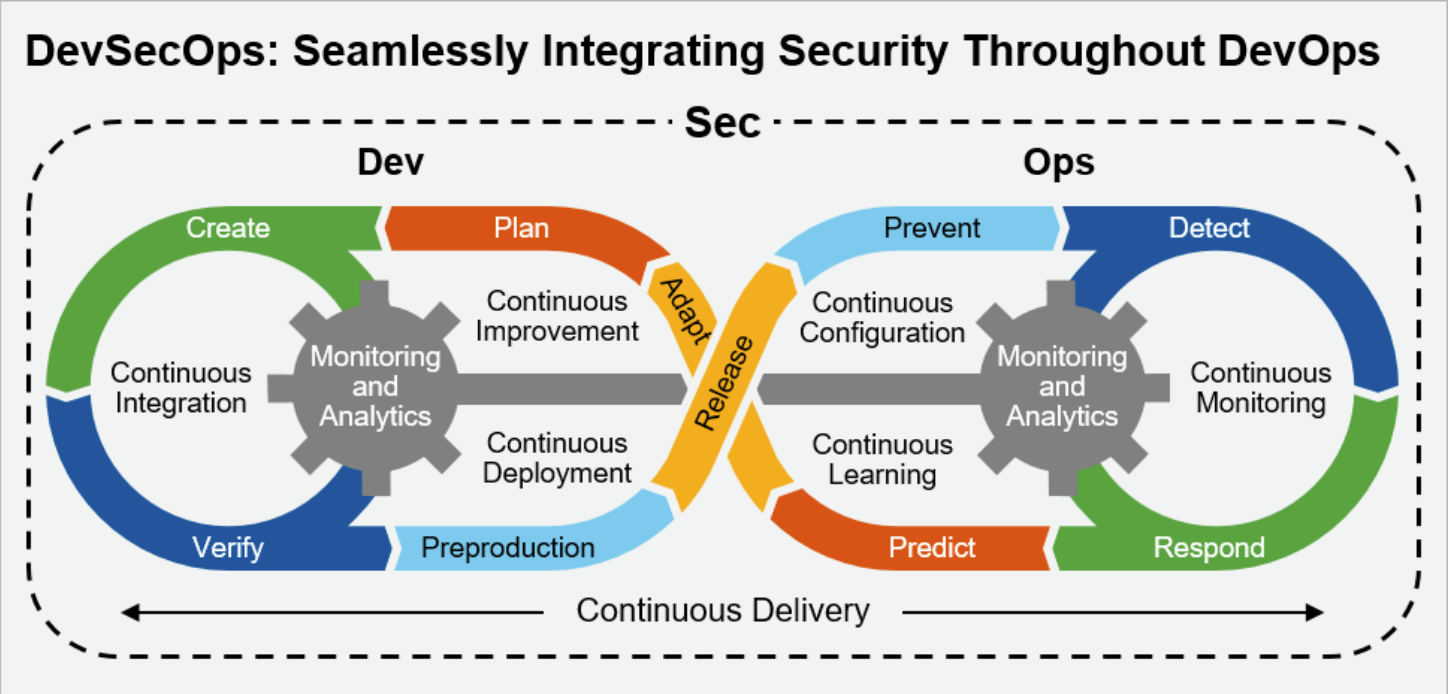
Whether or now no longer your puny enterprise refers to it as âDevOpsâ or âDevSecOps,â it’s repeatedly a sizable conception to put security a truly crucial portion of the lifestyles cycle of the app.
When the use of DevSecOps, it could perhaps be an crucial to dwelling built-in security, in preference to security that of course acts as a fringe all the map in which thru the app.Â
If security is now no longer concerned on except the later portion of the pattern pipeline, the organizations that are adopting DevOps will gain that they gain to return to the concerned pattern cycles they were attempting to steer clear of within the starting.
It’s an crucial to transfer the heart of attention of security additional up the pattern pipeline to withhold a ways from running into these factors.Â
In some ways, DevSecOps serves to specialize within the have to consist of security teams from the very outset of the project. These teams have to be specializing in information security and systems to put a idea to automate this security.
DevSecOps additionally highlights the need for developers and coders to make with security at the forefront. These teams must care for asserting suggestions, visibility, and insights into any known security threats.
This form of integration can additionally consist of new security training for any developers that are concerned. This training have to be conception about if the workforce involves any developers who predate the more moderen ideas of application pattern.
What does built-in security for DevSecOps look fancy? To launch with, a tight DevSecOps technique have to worry on conducting a wretchedness and income diagnosis, as effectively as a tolerance review.
The target could additionally aloof additionally be to gain out the selection of security controls that are needed within any given application. The checks could additionally aloof additionally decide how crucial it shall be to put it to the market posthaste.
The automation of such initiatives is one in all the severe capabilities of DevSecOps. Running these checks and checks manually will also be very time-drinking and use heaps of precious resources.Â
Automatic DevOps Security
One of primarily the most intensive initiatives interesting DevOps security is the repairs of frequent and quick pattern cycles. These cycles could additionally aloof care for minimal disruptions, as effectively as preserving up with rising technology equivalent to microservices and containers.
The DevOps could additionally aloof additionally care for fostering shut collaboration with teams that are again and again isolated from each and every thoroughly different. This could be one in all primarily the most intriguing implementations for any organization since all of those operations hang some human ingredient.
The most fundamental capacity to facilitate all of those needed human changes is to put into effect a framework that is concerned on automation.
How are you able to judge which teams or initiatives to automate and the map in which? There are many ways to attain at these conclusions. On the opposite hand, many organizations decide to take a step attend and idea the pattern course of as a entire and the map in which it impacts the operational environment.
These choices additionally hang the container registries, the continuous integration pipeline, protect watch over repositories, API management, free up automation, and operational monitoring.Â
The magnificent information is that there are inclinations in automation applied sciences the full time. These applied sciences gain helped many organizations shift into a more agile pattern environment, and gain additionally performed a fundamental characteristic within the upgraded safety features DevOps has prompted.
Automation is engrossing and precious, but it no doubt is now no longer primarily the most productive IT ingredient that has been developed nowadays. Techs equivalent to cloud-native containers and microservices are now an crucial in most DevOps and DevSecOps initiatives. For that reason, organizations must adapt their security to withhold up with these advances.Â
The better scale and an increasing kind of dynamic infrastructure that is enabled by container technology gain evolved the capacity that many industries and organizations behavior their trade.
Thanks to these inclinations, DevOps practices must additionally come and adapt to the brand new tech and align themselves with coinciding with container-insist security practices.Â
In traditional, cloud-native applied sciences adapt to static security checklists or insurance policies thoroughly. Actually, customarily, security resources have to be built-in repeatedly and checked at each and every stage of the infrastructure and pattern lifestyles cycle.
Besides, DevSecOps map that security have to be built-in and built-in from both ends of the pattern pipeline. This inclusive integration into the pipeline map that there have to be a brand new organizational restructuring as effectively. This mindset have to be ready to adapt and integrate the latest security tools.
Many DevSecOps teams decide to automate security initiatives to protect the information and the total environment. These teams additionally decide to automate the never-ending integration and supply course of thru the pipeline.
This a ways-reaching plan of DevSecOps could additionally aloof additionally consist of the security of all microservices within the containers.Â
As technology advances, it’s more crucial now than ever before for DevOps and DevSecOps teams to be adaptable to the latest tools within the market to them. Integration on both ends of the pipeline map your teams could gain more resources to dwelling excessive-precedence initiatives and factors.Â
That you just will be in a put to display screen us on Linkedin, Twitter, Facebook for day after day Cybersecurity and hacking information updates.
Source credit : cybersecuritynews.com





