LeakyCLI: New Vulnerability Exposes Credentials In AWS, Azure & Google Cloud

More than one Cloud Provider companies cherish Google Cloud, AWS, and Azure had been came across with a brand new vulnerability that has been termed “LeakyCLI.”
Because the title suggests, the Expose line interfaces of Google Cloud (Gcloud CLI), AWS (AWSCLI), and Azure (Azure CLI) teach sensitive recordsdata in the accomplish of atmosphere variables.
This vulnerability modified into as soon as assigned with CVE-2023-36052, and the severity modified into as soon as given as 8.6 (High).
If this vulnerability is subjected to exploitation, chance actors can prevail in get right of entry to to diverse sensitive recordsdata comparable to credentials, usernames, passwords, and keys that can perhaps well later be historic to prevail in get right of entry to to any resource.
Exploitation might per chance well be done by plan of tools cherish GitHub actions.
LeakyCLI: Fresh Vulnerability
In line with the experiences shared with Cyber Security News, CLIs are tools supplied by Cloud Provider vendors for customers to retain watch over cloud companies and exercise documented Relaxation API requests to amass recordsdata about configuration or diversified disorders.
Free Live Webinar.for DIFR/SOC Teams: Securing the High 3 SME Cyber Assault Vectors - Register Here
In addition, these CLIs are also historic in CI/CD (True Integration and True Deployment) environments where the exercise of these documented Relaxation API requests can teach configuration recordsdata about the property alongside atmosphere variables.
In addition, all these disorders exist in a serverless atmosphere, comparable to Azure capabilities, Google Cloud capabilities, and AWS Lambda.
AWS CLI Leakage
In AWS, the lambda API requests cherish aws lambda get-feature-configuration and aws lambda get-feature might per chance well be historic to amass recordsdata about the atmosphere configuration and feature recordsdata.
On the opposite hand, the output given to the stdout contains the atmosphere variable recordsdata as effectively.

A few of the organizations store sensitive recordsdata comparable to AWS bucket title, passwords or any diversified keys in the atmosphere variables which are exposed when running these instructions on the AWS CLI.
GCloud CLI Leakage
Reminiscent of AWS CLI, GCloud CLI also affords certain instructions cherish gcloud capabilities deploy
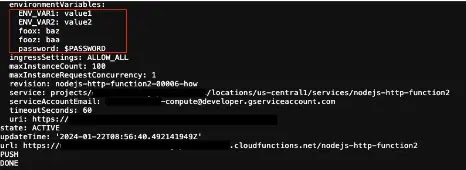
On the opposite hand, the responses given in the stdout teach outlined or predefined atmosphere variables.
In some low situations, the stdout also contains get logs which can perhaps well comprise pre-present atmosphere variables or sensitive recordsdata comparable to passwords in the cloud feature which are exposed.
Proof Of Theory
AWS
In present to expose this vulnerability’s existence and severity, researchers historic the under report to leak recordsdata by plan of GitHub actions, CircleCI and TravisCI
“aws lambda” AND (“update-feature-configuration” OR “update-feature-code” OR “post-version”) AND (course:.github/workflows OR course:.circleci OR course:.travis)
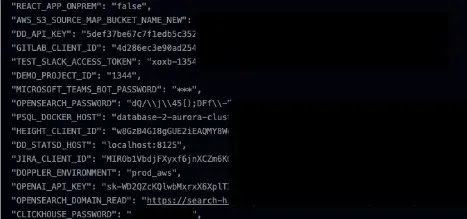
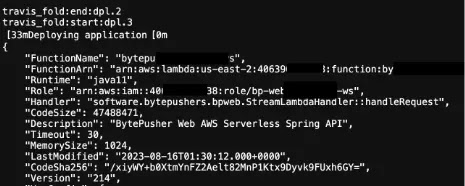
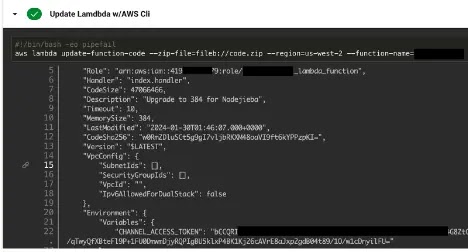
The final result of this report contained over 1000 hits which modified into as soon as narrowed all the perfect plan down to many dozens of initiatives by handbook and limited procedures.
A few of the ensuing repositories consisted of logs that leaked sensitive recordsdata cherish atmosphere variables, passwords and keys.
In diversified situations, diversified recordsdata cherish yarn ID’s or S3 bucket names were exposed which are no longer in point of fact appropriate as to be personal.
Nonetheless, there were also situations where the sensitive recordsdata ranged between yarn IDs (no longer personal) to passwords and keys (Non-public).
GCP
Researchers historic the under report to study Google Cloud CLI to try Github Actions, CircleCI, TravisCI and Cloudbuild.
The ensuing hits contributed to handiest 137 repositories nonetheless most of them consisted of several sensitive recordsdata comparable to mission names, provider accounts and atmosphere variables.
“gcloud capabilities deploy” AND (“–space-env-vars” OR “–update-env-vars” OR “–rob away-env-vars”) AND (course:.github/workflows OR course:.circleci OR course:.travis OR course:cloudbuild)
To assemble a temporary perception on how they were in a position to procure cloudbuild logs of personal repositories, researchers historic cloudbuild GitHub integration application which allowed them to appear these get logs interior GitHub.
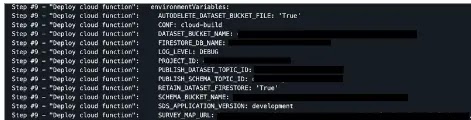
If chance actors get their hands on these cloudbuild logs and receive these sensitive recordsdata, they may be able to exercise them to escalate their privileges to diversified companies the exercise of the exposed atmosphere variables.
Mitigation
AWS
- Customers of AWS are suggested to agree to the under steps
- Earn no longer exercise atmosphere variables to store sensitive recordsdata
- Overview get logs to operate certain they don’t comprise sensitive recordsdata
- Restrict the get right of entry to and scope of the logs to specific exercise situations
GCP
For Google Cloud customers, the output from the CLI might per chance well be suppressed by the exercise of the –no-user-output-enabled flag. Furthermore, the exercise of the Secrets supervisor feature can be suggested for storing credentials.
For Azure customers, it’s suggested to upgrade your CLI versions to the latest as a system of mitigating this vulnerability.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP.
Source credit : cybersecuritynews.com


