EtherHiding: A Novel Technique to Hide Malicious Code Using Binance's Smart Chain

Threat actors own employed a recent technique to distribute malicious code named “EtherHiding,” which abuses Binance’s Ravishing Chain (BSC) contracts to host ingredients of a malicious code chain to cowl them interior the blockchain.
To inject malicious JavaScript codes into the blockchain systems, possibility actors used compromised WordPress websites redirected to Cloudflare Employee hosts to manufacture evasive distribution.
“Within the assault drift, a build is defaced with a truly believable overlay tense a browser replace sooner than the build also will be accessed. The spurious “replace” appears to be like to be vicious infostealer malware admire RedLine, Amadey, or Lumma.”, reads the submit by Guardio Labs.
Why API Safety Must be Your Top Precedence
API security isn’t appropriate a precedence; it’s the lifeline of companies and organizations. But, this interconnectivity brings with it an array of vulnerabilities that are normally hid beneath the ground.
EtherHiding Malware
This contemporary technique has also been termed “ClearFake,” which distributes malicious codes by strategy of compromised websites by showing spurious browser replace overlays.
In step with the experiences shared with Cyber Safety Data, it used to be confirmed that possibility actors had been focusing on inclined WordPress websites to inject two malicious scripts into the salvage pages.
These malicious scripts load the Binance Ravishing Chain (BSC) JS library, which fetches varied malicious scripts from the blockchain that are injected into the build. Furthermore, this code also triggers the download of the third-stage payload from the attacker-controlled server (C2).
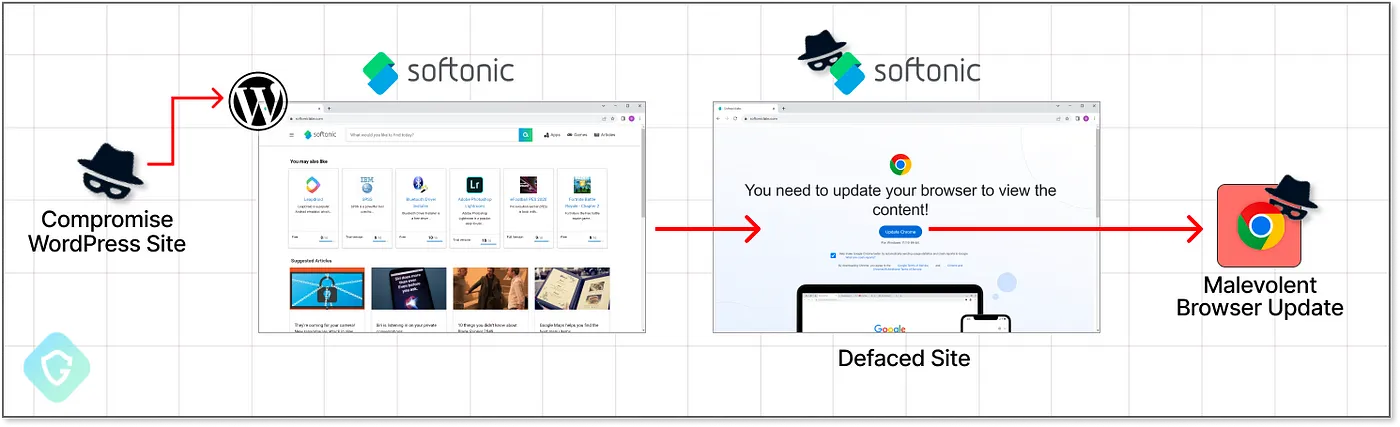
The spurious browser replace overlays are brought on for Google Chrome, Microsoft Edge, or Mozilla Firefox browser users. When the victims click the “replace” button, they are directed to download a malicious executable from Dropbox or varied reliable websites.
Blockchain technology, while being a ambitious map, might perchance also be exploited in diversified ways, equivalent to in the spread of malware or in the exfiltration of stolen records and data. These malicious actions also will be advanced to trace and shut down the utilization of aged law enforcement techniques.
A total document about ClearFake has been printed by Guardio Labs, providing detailed records about the distribution technique, exploitation techniques, explanation for Binance utilization, and varied records.
Indicators of Compromises (IOCs)
| Connected BSC Addresses/Contracts: ———————————– 0xfc1fE66FB63c542A3e4D45305DaB196E5EcA222A 0x7f36D9292e7c70A204faCC2d255475A861487c60 3ed Stage IP Addresses: Third Stage Attacker Managed Domains: Compromised WordPress Web sites (Detected Closing 14 Days): Malware Hashes (samples): Malware Filename samples (Repeat UNICODE abuse in filenames): |
Source credit : cybersecuritynews.com


