WordPress Plugin Flaw Exposes 10k+ Websites to Cyber Attacks
.webp)
A severe vulnerability in the WP Datepicker WordPress plugin was as soon as identified, affecting over 10,000 active installations.
This Arbitrary Alternate options Change vulnerability (CVE-2024-3895) has been assigned a CVSS obtain of 8.8, indicating a excessive severity level.
CVE-2024-3895: Arbitrary Alternate options Change Vulnerability in WP Datepicker Plugin
This vulnerability will be exploited by authenticated attackers with subscriber-level score entry to and above to interchange arbitrary options, which is in a location to be with out affirm leveraged for privilege escalation.
Such an attack may per chance per chance additionally permit threat actors to build administrator accounts, posing a important anxiousness to affected web sites.
The vulnerability was as soon as display masks in the WP Datepicker plugin, a broadly previous tool for managing date and time inputs in WordPress kinds. The flaw, which existed in variations 2.1.0 and earlier, has been fully addressed in model 2.1.1.
The source code has been reformatted for better readability, causing the line numbers to be various:
function wpdp_add_new_datepicker_ajax(){ global $wpdp_premium_link, $wpdp_dir, $wpdp_url, $wpdp_pro, $wpdp_data, $wpdp_options, $wpdp_styles, $wpdp_gen_file; if(isset($_POST['wpdp_add_new_datepicker']) || isset($_POST['wpdp_get_selected_datepicker']) || isset($_POST['wpdp_form_data'])){ if ( ! isset( $_POST['wpdp_nonce_action_field'] ) || ! wp_verify_nonce( $_POST['wpdp_nonce_action_field'], 'wpdp_nonce_action' ) ) { print __('Sorry, your nonce did not verify.', 'wp-datepicker'); exit; Bounty Program:
The researcher who found and responsibly reported this vulnerability throughout the Wordfence Worm Bounty Program, Lucio Sá, was as soon as awarded a bounty of $493.00 for their discovery at some level of the Worm Bounty Program Extravaganza.
Wordfence is operating a Worm Bounty Extravaganza, offering increased bounty charges for vulnerabilities submitted through Could per chance per chance also 27th, 2024.
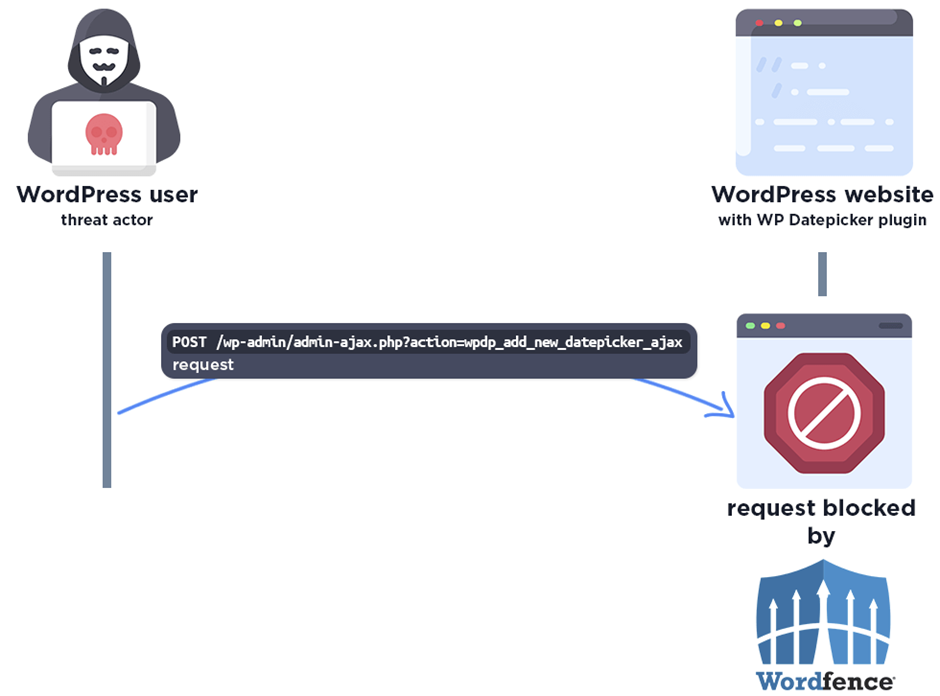
To present protection to against exploits targeting this vulnerability, WordPress users are strongly encouraged to verify that their sites are up to the moment to the latest patched model of WP Datepicker (2.1.1 or better).
In April, Wordfence Top charge, Wordfence Care, and Wordfence Response users obtained a firewall rule to give protection to against exploits targeting this vulnerability.
Source credit : cybersecuritynews.com


