Top 15 Best Security Incident Response Tools In 2024
Introduction :
Incident response Instruments or incident management machine are significant security solutions to present protection to agencies and enterprises from cyber attacks.
Our reliance on the online is rising, and so make a threat to agencies, no topic increased investments and abilities in cyber security. Extra records breaches and cyberattacks exist on organizations, governments, and folk than ever earlier than.
New technologies love Machine Learning, Man made Intelligence, and 5G, apart from to greater coordination between hacker groups and train actors, have made threats riskier.
The faster your group detects and responds to an unauthorized accumulate admission to or IoT security incident, the much less seemingly it is to have a negative influence on the records, buyer belief, status, and profitability.
What’s an Incident Response?
Incident response refers to an organizationâs strategy for responding to and managing a cyberattack.
A cyberattack or security violation also can result in chaos, copyright claims, a drain on overall organizational sources and time, and a decline in impress ticket.
An incident response aims to mitigate hurt and speedily return to normalcy.
A well-outlined incident response realizing can limit assault hurt and put cash and time after a cyber assault.
Why Incident Response Instruments are Vital?
Incident response manages the repercussions of an IoT security breach or failure.
It is important to have a response draw in location earlier than an incident happens in say to diminish the amount of hurt the occasion causes and put the group cash and time all the scheme by the restoration route of.
Incident response Instruments helps an group to detect, analyze, manage, and reply to a cyberattack. It helps to diminish the hurt and enact speedy restoration as rapid as seemingly.
Organizations on the overall exercise several simplest incident response tools to detect and mitigate cyberattacks.
Right here we have listed a few of basically the most vital cyber incident response machine widely historical with basically the most sophisticated substances.
As you realize, the investigation is constantly required to safeguard your future; you’d wish to discover about and prepare for the assault.
Safety Incident Response machine has to be accessible for every group to establish and address exploits, malware, cyberattacks, and diverse external security threats.
These Incident Response Instruments on the overall work with diverse vulnerable security solutions, love firewalls and antivirus, to analyze the attacks earlier than it happens.
To enact this correctly, these tools derive the records from the logs, identity system, endpoints, and so forth.
it furthermore notices suspicious activities within the system.
If we exercise these simplest Incident Response Instruments it turns into straightforward for us to video display, unravel, and establish security disorders rapid.
It streamlines the route of and eliminates repetitive tasks manually.
Most standard tools have multiple capacities to dam and detect the threat and even alert the safety groups to overview extra disorders.
Safety phrases fluctuate for diverse areas and fully rely on the organizationâs wants.
In this case, pleases make a choice out the preferrred tool is constantly now not easy, and it furthermore has to give you with the suitable resolution.
What’s within the Incident Response Instruments Article?
- Introduction
- Why Incident Response machine are Vital?
- What’s an Incident Response?
- Incident Response Phases
- What’s an Incident Response Gadget?
- Why enact we exercise Incident Response Gadget?
- Desk of Contents
- Incident Response Instruments Components
- Demo Video
- Professionals & Cos
- IR Gadget Users
- Designate for every Gadget
- Conclusion
Incident Response Phases
The incident response methods are essentially essentially based on six significant steps: preparation, identification, containment, eradication, restoration, and lesson.
| Incident Response Phases | Answer |
| Preparation | This also can require determining the right kind individuals of the response team and the stimulates for internal accomplice signals. |
| Identification | That is the route of of finding threats and responding effectively and rapid. |
| Containment | After determining what to enact, the third step is to limit the hurt and quit it from spreading. |
| Eradication | This step entails removing the threat and restoring internal programs as precisely as seemingly to their initial train. |
| Recovery | Safety experts must guarantee that all compromised programs are no longer abominable and might even be put abet on-line. |
| Lesson | One of basically the most vital and on the overall forgotten steps. The incident response team and its companions occasion to discuss about toughen their work within the long term. |
In todayâs technology-pushed society, organizations face rising security risks that turned into unavoidable.
Subsequently, the incident response team wants tough incident response tools to overcome and manage security incidents.
So letâs first realize what an incident response tool is and dive deep into the tools.
Why enact we exercise Incident Response Gadget?

Even though agencies have hundreds of security practices in location, the human ingredient is composed basically the most vital.
Per the annual Verizon Details Breach Investigations Tale, over 85% of all breaches are prompted by phishing attacks.
IT security mavens must be ready for the worst since 13% of breaches prompted by of us fill ransomware, and 10% of ransomware attacks payment organizations an average of $1 million.
For this motive, organizations must composed invest in incident response machine.Â
The incident response tools are significant because they merit agencies detect and reply to cyberattacks, manipulates, malware, and diverse security threats internal and outside the group in an inexpensive timeframe.
Most of todayâs incident response machine has several substances, including the skill to automatically detect and block threats whereas notifying the correct security groups to overview the recount.
Incident response tools is at chance of be historical in assorted methods depending on the group’s wants.
This might involve monitoring the system and particular person nodes, networks, assets, users, and so forth.
Many organizations salvage it onerous to establish the preferrred incident response machine.
To enable you to salvage the suitable resolution, right here is a listing of incident response tools to enable you to understand, prevent, and care for diverse security threats and attacks to your IoT security tools system.
How enact We Choose the Simplest Incident Response Instruments?
We analyzed the industry with the requirement to present protection to digital assets and mentioned the respective industries’ wants with the experts essentially essentially based on the following Components.
How effectively are the incident response machine performing for the following operations?
- Preparation & Identification
- Containment & Eradication
- Recovery and restoration
- Event False particular Assessments
- Identification of incidents
- Containment and quarantine of attackers and incident exercise
- Recovery from incidents, including restoration of programs
- Components, Bustle, User friendly
- Actions in all the issues of incident response
Incident Response Market
| By Safety Form | Web Safety Utility Safety Endpoint security Community Safety Cloud Safety |
| By Deployment Mode | Cloud On-premises |
| By Group Kinds | Small Enterprises Medium Enterprises Colossal Enterprises |
Desk of contents
Simplest Cyber Incident Response Instruments List
| Incident Response Instruments | Key Components |
|---|---|
| 1.- ManageEngine Log360 | 1. It examines on-premises programs and cloud platforms 2. Logs are consolidated and kept. 3. Utilize User and Entity Behaviour Analytics (UEBA) to defend song of customary events. 4. The ManageEngine package has diverse security substances love records integrity tracking and a threat intelligence 5. feed that makes threat hunting faster. |
| 2. SolarWinds | 1. User Dispute Monitoring. 2. File Integrity Monitoring. 3. Community Safety Monitoring. 4. Microsoft IIS Log Analysis. 5. Firewall Safety Management. 6. Community Safety Instruments. 7. Chortle IDS Log Analysis. 8. IT DISA STIG Compliance. |
| 3. CrowdStrike Falcon Insight XDR | 1. Unparalleled protection 2. Bustle investigations 3. Likelihood intel integration 4. 24/7 managed threat hunting 5. Continuous uncooked events capture 6. proactive threat hunting |
| 4. IBM QRadar | 1. Ideal filtering to construct the desired outcomes 2. Ideal threat-hunting capabilities 3. Netflow diagnosis 4. Functionality to analyze substantial portions of records rapid 5. Establish hidden threads 6. Analytics of user conduct |
| 5. Splunk | 1. Ask-essentially essentially based historical and contemporary diagnosis. 2. AI-powered threat detection. 3. It indubitably works with Home windows, Linux, and macOS. 4.Components for security and compliance 5.Integration with a preference of diverse records sources |
| 6. AlienVault | 1. Smartly suited with Linux and Home windows 2. Monitoring of conduct 3. Detection of intrusions 4.Analysis and alter of logs 5.The skill to address compliance |
| 7. LogRhythm | 1. It has a response playbook 2. Automatic tidy responses 3. Abet-quit for Elasticsearch that is delivery source. 4.Higher integration of threat records 5.Checking the steadiness of recordsdata |
| 8. Varonis | 1. Investigating seemingly incidents⯠2. Containment, eradication, and recovery⯠3. Recommendation on detections, procedures, and cyber resilience 4. Deep forensics diagnosis |
| 9. OpenVAS | 1. An Developed Process Wizard is furthermore integrated within the OpenVAS web interface. 2. It entails several default scan configurations and enables users to construct customized configurations. 3.Reporting and suggestions for fixing problems 4.At the side of security tools to diverse ones |
| 10. Rapid7 InsightlDR | 1. Endpoint Detection and Response (EDR) 2. Community Traffic Analysis (NTA) 3. User and Entity Behavior Analytics (UEBA) 4. Cloud and Integrations. 5. Safety Details and Event Management (SIEM) 6. Embedded Likelihood Intelligence. 7. MITRE ATT&CK Alignment. 8. Deception Technology. |
| 11. Chortle | 1. Adjustments and extensions are seemingly. 2. Personalized tests and plugins are supported 3.Launch source and versatile 4. inline and passive |
| 12. Suricata | 1. It helps JSON output 2. It helps Lua scripting 3. Support for pcap (packet capture) 4. This tool permits multiple integrations. |
| 13. Nagios | 1. It’s straightforward to establish community disorders and provide security and scalability. 2. It furthermore helps with retaining song of logs and databases. 3. It has an effortless-to-exercise and informative web interface that makes it straightforward to video display a community. |
| 14. Sumo Good judgment | 1. Song & troubleshoot 2. Mix proper-time threat intelligence 3. Song & troubleshoot 4. integrated logs, metrics, and traces 5. Speedily detect applications & Incidents |
| 15. Dynatrace | 1. Chunky stack availability and performance monitoring 2. Easy monitoring with no configuration 3. Automatic Incident Management4. 4. AWS Monitoring 5. Azure Monitoring 6. Kubernetes Monitoring |
Top 10 Simplest Incident Response Instruments
- ManageEngine
- SolarWinds
- CrowdStrike Falcon Insight XDR
- IBM QRadar
- Splunk
- AlienVault
- LogRhythm
- Varonis
- OpenVAS
- Rapid7 InsightlDR
- Chortle
- Suricata
- Nagios
- Sumo Good judgment
- Dynatrace
1. ManageEngine

Which you might perhaps presumably fight threats on-premises, within the cloud, or in a hybrid atmosphere with the advantage of Log360, a security analytics resolution.
Compliance mandates love PCI DSS, HIPAA, GDPR, and others might even be more without problems met with its support.
In say to safeguard your sensitive records, you are going to be ready to personalize the resolution to fit your particular wants.
Every side of your community, including Active List, workstations, file servers, databases, Microsoft 365, cloud services, and more, might even be tracked and audited the utilization of Log360.
By combining logs from several devices, Log360 is prepared to establish sophisticated assault patterns and APTs.
Alongside with the resolution, you accumulate behavioral analytics powered by machine finding out.
These analytics also can build abnormalities in user and entity conduct and effect them a chance receive.
Bigger than a thousand pre-made experiences with concrete ideas are supplied by the safety analytics.
Discovering the source of a security recount is seemingly with the advantage of log forensics.
Which you might perhaps presumably automate the remediation response with tidy processes and integrations with predominant ticketing tools the utilization of the constructed-in incident management system.
The resolution is offered both on-premises and within the cloud, below the title Log360 Cloud.
One SIEM product that might sift by all those logs and web insights about performance and security is ManageEngine Log360.
Each user fable and instrument might even be profiled with the advantage of User and Entity Behaviour Analytics (UEBA), which files customary events.
This strategy is extremely effective in figuring out someone attempting to supply unauthorized accumulate admission to, steal records, or take over accounts.
The log management ingredient ManageEngine connects with bigger than 700 apps to accumulate exercise records and collects Home windows Occasions and Syslog messages.
Log records from Salesforce, Azure, and AWS can furthermore be retrieved via the program.
All of those logs are consolidated, formatted in retaining with industry requirements, searched, after which filed.
To guarantee compliance with regulations a lot like PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA, these logs might even be priceless.
With its emphasis on security and diagnosis of diverse logs, this incident response tool is amongst the preferrred.
As well to to finding the log server, it notifies the suggestions of the uncommon occurrence.
Unauthorized accumulate admission to to the firm’s IT system is rapid and without problems caught by it.
Some key sectors that supply significant services embrace web servers, databases, DHCP servers, e mail services, and so forth.
This program complies with records security requirements a lot like HIPPA, DSS, PCI, ISO 27001, and others; it is compatible with both Home windows and Linux computer programs.
Components
- Automatic Active List management, delegation, and substantial user management.
- Single endpoint for patching, machine liberate, some distance away alter, and cellular instrument management.
- A community monitoring tool enables you video display velocity, faults, and proper-time exercise.
- Monitoring utility performance at some stage in programs and infrastructures.
- Cloud monitoring covers web sites, servers, apps, and community devices.
Demo Video
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| Customize tools | Self-service alternatives and records bases for purchasers must composed be strengthened. |
| Most mighty interface | Adjusting settings whereas on the dart is now not straightforward, so the interface and user trip must be enhanced. |
| Completely ticketing system | Interface difficulties reported |
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Unbiased Gadget Vendors
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
2. SolarWinds

In terms of managing and reporting on logs, that is yet one other high incident response tool.
A response to incidents might even be supplied in proper-time. With SolarWinds, groups can suddenly assess and establish threats, after which video display and address them.
With this utility, the user also can without problems visualize uncommon exercise and establish it.
Furthermore, it affords a dashboard that affords records about every hazard, allowing engineers to without problems establish the recount.
Which you might perhaps automate threat response with SolarWinds’s characteristic, which helps you to video display USB drives.
Node management alternatives and log filtering are furthermore accessible.
Components
- SolarWinds’ fat community tracking capabilities enable you video display and alter community performance in proper time.
- It helps hundreds of devices and producers, making community installations straightforward to address.
- SolarWinds signals and experiences essentially essentially based to your restrictions and criteria. Fixing disorders earlier than they happen.
- Small and substantial enterprises can add monitoring functions as their community grows since it’s versatile.
- The SolarWinds interface is straightforward and its dashboards conceal significant community records.
Demo Video
That is simplest for all sorts of industry and works with Linux and Home windows.
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| Easy to Configure | New SEM Gadget |
| Active and fast Response | Pre-finding out required to make exercise of the tool |
| Easy and sensible licensing | Leisurely loading route of identified |
Users
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
3. CrowdStrike Falcon Insight XDR

Global enterprise networks and assets are protected by CrowdStrike’s Falcon Insight XDR, an incident detection and response platform.
To greater shield against cyber assaults, it expedites security activities by offering comprehensive threat visibility.
CrowdStrike handles detection and response with enhanced capabilities to enable enterprise-extensive investigations and harmful-domain detections.
By bringing together the overall devices that are connecting to the community, the Falcon Incident response tool creates a more effective cybersecurity ecosystem and affords a centralized location for diagnosis.
As well to to offering third-occasion integrations at some stage in serious security areas, the IR program presents Deep native telemetry.
Components
- Falcon Insight XDR’s sophisticated EDR substances detect and quit threats at some stage in all endpoints in proper time.
- Home windows, macOS, Linux, and diverse operating programs and devices are protected and monitored.
- Behavioral analytics and machine finding out detect and quit instrument threats and suspicious conduct.
- Combining threat intelligence records helps detect and quit new and established threats.
- Enables fast security responses including containment, isolation, and remediation.
Falcon Insight XDRVideo Demo:
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
4. IBM QRadar
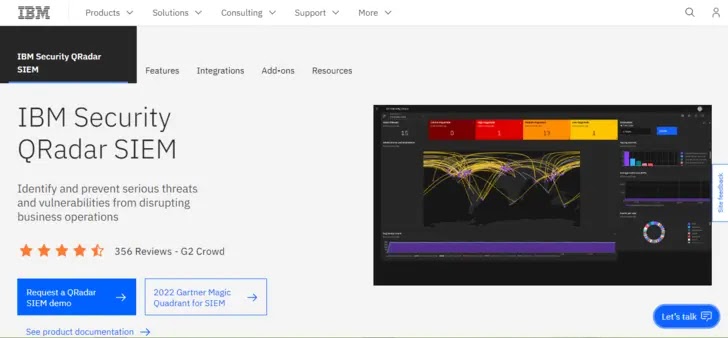
The incident detection and response platform Falcon Insight XDR, developed by CrowdStrike, safeguards the networks and assets of world enterprises.
By giving fat visibility into threats, it hastens security operations, making them more effective within the fight against cyberattacks.
To facilitate enterprise-extensive investigations and harmful-domain detections, CrowdStrike manages detection and response with increased capabilities.
The Falcon Incident response resolution improves cybersecurity ecosystems and affords a centralized build for diagnosis by bringing together the overall devices that are connecting to the community.
As well to to offering Deep native telemetry, the IR program affords third-occasion connectors at some stage in significant security areas.
Components
- Assessments log records from many sources for security threats and uncommon exercise.
- Helps SIEM establish risks by connecting community events.
- combines behavioral diagnosis and anomaly detection to expose suspicious conduct and security flaws.
- Precise-time monitoring and automatic reaction abet incident response.
- combined threat records sources make finding identified and new threats less complicated.
Demo Video
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| QRadar presents you a fat deem of whatâs going on. It helps accumulate a unified deem of the records transfers, activities, and logs in SaaS (machine-as-a-service), IaaS (infrastructure-as-a-service), and on-premises environments. | When QRadar finds something, it makes something it calls an âoff ense.â So, it has a straightforward system for selling tickets. |
| It actively appears to be for security vulnerabilities in Community devices and applications. | You appropriate wish to pay shut consideration to what number of events happen per 2nd because thatâs where the payment turns into a mountainous recount. |
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Unbiased Gadget Vendors
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
5. Splunk

For comprehensive community management, Splunk is an all-inclusive incident response resolution.
Safety monitoring and prevention enabled by man made intelligence is on the center of Splunk’s incident response.
Threats, suspicious activities, and policy violations are constantly monitored by this methodology.
The safety services offered by Splunk, which video display the community in proper-time and actively search by log records, are largely pushed by man made intelligence and machine finding out.
Which you might perhaps presumably define how immoral a recount will seemingly be by taking a have a look on the events, grouping them, after which giving them a threat receive.
Whereas diverse signature-essentially essentially based programs fail to detect assaults essentially essentially based on their payload signatures, LogRhythm is prepared to decipher behavioral patterns.
Effective, predictive, and actionable AI and machine finding out technologies essentially make exercise of this.
As well to to enhancing security, it allowed users to personalize several substances of the system, a lot like statistical diagnosis, investigations, incident opinions, classification, dashboards, and so forth.
Which you might perhaps exercise it for SaaS deployments, and it works for both mountainous and tiny companies.
Extra abet from the public sector, healthcare suppliers, and financial institutions is at chance of be added as a outcomes of its scalability.
Splunk is huge at managing signals, can suddenly establish the chance receive, and responds effectively.
Components
- Logs, metrics, and machine-generated records are composed and indexed.
- Enables proper-time search and diagnosis of big records sets.
- Compares records from hundreds of sources and creates dashboards for clarity.
- uses machine finding out and AI to salvage patterns, anomalies, and predictions.
- Log diagnosis and monitoring merit with security, threat detection, and compliance.
Demo Video
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| It contains hundreds of extensions and plugins | The ticket of records is mostly increased for larger volumes of records. |
| It substances a magnificent dashboard with charting and search tools. | Continuously attempting to change it with delivery alternative machine |
| It generates analytical experiences the utilization of visual graphs and communal tables and charts. |
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Unbiased Gadget Vendors
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
6. AlienVault

One of basically the most all-encompassing incident response tools for threat detection is AlienVault.
Compliance management furthermore advantages vastly from AlientVault’s high-notch security monitoring capabilities.
It’s able to performing any accept as true with of cloud-connected cleanup.
It has a plethora of security substances apart from, such because the skill to establish, salvage assets, assess vulnerabilities, defend song of inventories, correlate events, take a look at for compliance, ship e mail signals, and more.
Because it employs the USM tool, which depends on tiny sensors, AlientVault is sensible, straightforward, and uncomplicated to set up.
This characteristic is simply like an endpoint agent in that it is going to establish threats as they happen.
Any company also can establish the threat with its versatile realizing. Every little thing is at chance of be monitored the utilization of appropriate one on-line portal.
With AlienVault, agencies of all sizes can take excellent thing about proper-time threat detection, incident response, and compliance managementâall in a single all-inclusive security resolution.
Your community’s dispersed sensors and endpoints derive accurate records apart from to log records.
AT&T Cybersecurity, of which AlienVault is now a part, presents a plethora of extra security services and technologies that agencies can see into.
Components
- Combines asset discovery, vulnerability evaluation, threat detection, and incident response.
- Presents infrastructure visibility by automatically figuring out and cataloging community assets.
- Makes exercise of accurate scans to understand and prioritize vulnerabilities to diminish chance.
- Precise-time security threat detection and response the utilization of threat intelligence and correlation principles.
- Automates workflows and affords actionable insights to resolve incidents faster.
Demo Video:
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| It has a unified security platform | If the programs historical by harmful-border companions are unreliable, it is going to even be rather straightforward to originate attacks against their databases. |
| Limitless threat intelligence | This might compromise the systemâs skill to search for threats. |
| Just a few deployment alternatives |
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Unbiased Gadget Vendors
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
7. LogRhythm

This works with AI’s log correlation and enables all sorts of greater characteristics.
With the utilization of AI and web converse traffic diagnosis, it is going to potentially be historical for behavioral diagnosis.
Home windows and Linux are amongst the platforms that LogRhythm is compatible with.
It indubitably works well with disjointed workflows and has highly adaptable records storage capabilities.
No topic the inability of structure within the records, it affords a further layer for threat detection.
There’s a dearth of properly organized records, glorious transparency, and automation, amongst diverse issues.
That is compatible with Home windows and diverse community sites, making it preferrred for both tiny and substantial enterprises.
Diversified logs and objects can exercise this.
Speedily reply to security problems and produce extra security records to toughen the community with LogRhythm’s incident response resolution, which combines search analytics and machine finding out.
Of us outlandish with the delivery-source search tool Elasticsearch also can salvage it now not easy to fill exercise the platform’s backend.
In say to establish and prevent seemingly dangers, the hunt engine scours the logs for patterns, indicators of chance, causal relationships, and changes in conduct.
It’s seemingly to location up automated actions and web proper-time notifications from sophisticated continual threats the utilization of firewall principles.
Components
- Supplies SIEM log collection, correlation, and diagnosis.
- Logs from several sources are composed and normalized for centralized threat detection.
- Detects irregularities and security threats the utilization of behavioral diagnosis and machine finding out.
- Helps prevent security incidents with proper-time threat detection and response.
- Helps unravel incidents effectively by automating operations.
Demo Video
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| Log ingestion | Just a few tools with particular entry aspects |
| Utilizing the AI engineâs regulations, it rapid detects confrontational exercise. | Executing intensive web searches all the scheme by web converse traffic can make it seriously unstable. |
| Unifies SIEM, UEBA, and SOAR capabilities. | |
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Indipendent Gadget Vendors
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
8. Varonis
Infrastructure, records accumulate admission to, consumption, users, and so forth. are the principle areas of utility for this purposeful instrument.
Alerts, customizable experiences, actionable insights, flexibility, and diverse suspicious exercise substances are furthermore offered by Varonis.
Furthermore, it presents a detailed dashboard that enables users to see the safety phrases, which enhances their records and system visibility.
In cases where there is accumulate admission to to unstructured records, it presents the optimum resolution for e mail security programs.
If a user tries to join into the firm community without authorization or from an unauthorized IP address, it is going to rapid block them.
Enhanced records and alarms previous to any assault are supplied by this varnish, an incident response tool.
It reacts correctly and never shirks its job; it improves threat detection and affords LogRhythm.
Due to this, the route of turns into scheme more streamlined, allowing users to suddenly analyze seemingly dangers.
When combined with SIEM tools, the varonis incident response tool presents extra context, decreases notification lethargy, and yields basically the Most mighty insights.
the varonis In distinction to SIEM’s community-centric potential, DatAlert’s records-pushed threat detection capabilities provide extra context via its tough User Entity Behavior Analytics (UEBA) capabilities.
Organizations involved with compliance can make exercise of varonis DatAdvantage to diminish overall firm chance by recognizing overprivileged users and offering enhanced clear up alternatives.
Stable analytics with comprehensive records context are supplied by varonis by integration with SIEM tools, allowing the group to indubitably feel confident in its records security policy.
Safety groups can accumulate pleasure from varonis’s extra records source for infrastructure-connected analyses and alarms without burdening the SIEM with extra effort or frequency noise.
With SIEM and varonis, SOC groups also can overview disorders more rapid and produce an even bigger working out of basically the most vital sources to safeguard: specifics and digital correspondence.
Components
- Presents visibility, classification, and management for sensitive structured and unstructured records.
- Behavioral analytics detect and quit insider threats and uncommon records accumulate admission to.
- Monitors user conduct for security threats and unauthorized accumulate admission to.
- limits accumulate admission to, encrypts records, and displays it to categorise and safe private records.
- Presents intensive audit and compliance experiences.
Demo Video
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| Aids records security, accumulate admission to, and sensitive records management. | Advanced Intergaration |
| Details discovery & classification | Required ongoing monitoring and repairs for optimum operation. |
| Insider Likelihood Management Gadget |
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
Advantage
- With the advantage of Varonis signals and dashboards, investigations might even be conducted more rapid and effectively.
- Send a message to focused search outcomes
- Vital records is displayed at a seek, alongside with actionable insights and a number of of background.
9. OpenVAS

The Launch Vulnerability Assessment Gadget (OpenVAS) is a vulnerability scanner that is maintained and disbursed by Greenbone Networks.
With its Web interface and constructed-in tests, this vulnerability scanner is meant to be an all-in-one resolution that enables for high ranges of user customisation and makes developing and running vulnerability scans fast and uncomplicated.
Utilize the Linux-compatible OpenVAS to ascertain for security flaws.
The digital machine is pre-installed, or it is going to even be constructed from scratch the utilization of the code that is accessible below the GNU Total Public License (GPL).
Components
- Completely examines networks and programs for security flaws.
- Finds and maps community assets to cover the fat system.
- Adjustments vulnerability tests normally to address new threats and weaknesses.
- Web app screening and security hole detection are accessible.
- analyzes system setup for weaknesses and mistakes that might perhaps be historical against it.
Demo Video:
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| Regular vulnerability take a look at updates and neighborhood fortify. | It’s complicated to set up, configure, and exercise |
| Enables scan policy customization. | That you’re going to be ready to trust false positives requiring manual verification. |
| Just a few OS fortify. |
Users
- Safety Analyst
- Incident Responder
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Unbiased Gadget Vendors
- Managed Safety Service suppliers
- Incident Response Service Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
10. Rapid7 InsightlDR

Amongst many diverse uses, this tough security system excels at monitoring authentication and offering endpoint visibility.
Details gathering, purchasing, and examining capabilities, phishing, malware, and so forth. are all dealt with by this SIEM platform.
Both internal and external users might even be readily identified if anything uncommon is going down.
It’s going to establish the user’s behavioral analytics thanks to its sophisticated deception methodology.
Furthermore, it affords extra discovery functions love as log management, file integrity monitoring, and more.
Companies of all sizes can accumulate pleasure from this tool’s proper-time threat detection capabilities, making it preferrred for any accept as true with of scan.
Within the tip, it presents you the suitable search outcomes, and you are going to be ready to make a accurate preference rapid.
Components
- It entails sophisticated SIEM tools for gathering, examining, and linking logs.
- User exercise Analytics (UBA) detects uncommon user exercise and insider risks the utilization of conduct analytics.
- This functionality enables you video display endpoints and quit threats.
- Gathers and normalizes log records from many sources for central diagnosis and threat detection.
- This characteristic shows contemporary community security threats and uncommon conduct.
Demo Video:
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| Endpoint Detection and Response (EDR) | Subscription records is much less |
| Cloud and Integrations | twelve months realizing is more costly than diverse distributors |
| MITRE ATT&CK Alignment | Costs fluctuate for local and world |
Users
- Safety Analyst
- Incident Responder
- SOC Analyst
- SOC Supervisor
- Unbiased Gadget Vendors
- Managed Safety Service suppliers
- Incident Response Service Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
11. Chortle

Chortle is an intrusion prevention system that is delivery-source and supplied by CISCO.
As an intrusion prevention system (IPS), it is going to also establish intrusions and quit attacks from going down by reacting to patterns in community web converse traffic. Chortle analyzes protocols and files packets essentially essentially based on IP/TCP addresses.
Furthermore, it is going to even be historical as a proper-time community prevention system, a packet logger, a community file logging instrument, and a packet sniffer, grand love tcpdump.
Components
- Searches proper-time community records for anomalies and risks.
- finds assault patterns and diverse undesirable exercise the utilization of acknowledged signatures.
- displays community protocols for uncommon or illegal exercise.
- Sends messages when principles and signatures match.
- Users can build and customise detecting principles for community security.
Demo Video:
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| It’s fast and uncomplicated to set up on networks. | The administrator must give you their accept as true with methods to log and teach. |
| Principles are straightforward to jot down. | Token ring is now not supported in Chortle |
| It has accurate fortify accessible on Chortle sites and its accept as true with listserv. | |
| It’s free for directors who need an inexpensive IDS. |
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Unbiased Gadget Vendors
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
12. Suricata

In say to answer to incidents, the Launch Details Safety Foundation (OSIF) created the Suricata tool.
Companies of all sizes take excellent thing about this free product. A mix intrusion detection system (IDS) and intrusion prevention system (IPS) (delivery-source) is what this detection engine is all about.
Implementing a signature language and a location of principles enables the system to establish and thwart seemingly dangers.
Any operating system can exercise Suricata, including Home windows, macOS, Unix, and Linux.
Components
- Just a few threads velocity up web converse traffic and performance.
- Signatures and principles establish community dangers and assault patterns.
- Precise-time community customary checks for uncommon exercise and security disorders.
- displays community records for abnormalities.
- Examines community records recordsdata for dangers or uncommon conduct.
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Safety Researcher
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| Excessive-velocity community intrusion detection and prevention is Suricata’s uniqueness. | Its absence of a graphical interface also can make management and monitoring complicated for some users. |
| Effectively processes community web converse traffic the utilization of multi-threading. | Savor any intrusion detection system, it wants tweaking and administration to diminish false positives. |
| Performs signature-essentially essentially based detection and behavioral diagnosis to detect emerging threats. | |
| Neighborhood contributions and modification are seemingly with this delivery-source tool. |
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
13. Nagios
In say to prevent records disruptions prompted by IT infrastructure difficulties, agencies might exercise Nagios, a tough monitoring incident response resolution.
With Nagios, the industry can leisure assured that its operational operations will reside unaffected by unforeseen shutdowns, thanks to its scalable and adaptable build.
There are a plethora of community services that might even be watched, including SMTP, HTTP, POP2, SNMP, NNTP, SSH FTP, and endless more.
Also observable are the host’s useful resource metrics, including disk location, system log, and CPU load.
Diversified operating programs, including Linux and Microsoft Home windows, are compatible with it.
Components
- Monitors IT servers, apps, services, and networks in proper time.
- Sends configurable e mail, SMS, and diverse signals for pressing disorders.
- Dispensed monitoring lets it care for tiny and substantial environments.
- Makes exercise of performance graphs and experiences to analyze prior records and patterns.
- Its extensible plugin architecture enables users add tracking checks and customise the machine.
Demo Video
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| It helps to make services, servers, applications, and processes more accessible so that users can exercise them to video display the community. | The community throughput canât be tracked, and bandwidth and availability problems canât be tracked either. |
| It makes it straightforward to salvage protocol screw ups, community outages, and server outages so that they might even be mounted. | Within the free model, there are limited substances. |
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- MSP Services
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Managed Safety Service suppliers
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
14. Sumo Good judgment

That is an lustrous security platform that operates within the cloud and integrates with SIEM programs.
It performs high-notch diagnosis.
This platform affords a hybrid atmosphere apart from to diverse cloud services.
Which you might perhaps presumably toughen threat detection with this platform’s machine-finding out trip.
Furthermore, it detects and resolves security concerns as they occur.
The safety analytics is at chance of be centralized by the safety groups thanks to the unified records mannequin.
You won’t need any love new equipment or machine to make exercise of this.
The company can suddenly establish remoted threats with the advantage of proper-time security visibility.
By doing so, the safety system is location up and the infrastructure, apps, and so forth. are monitored.
Components
- affords cloud-essentially essentially based log management and analytics for proper-time machine records views.
- Will get and organizes logs and records from assorted programs.
- Has powerful analytics and visualization tools to establish records traits and insights.
- Presents log diagnosis for security, threat identification, and compliance.
- finds traits and outliers and predicts the long term the utilization of machine finding out.
Demo Video
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| Cloud-native SaaS analytics | To many alternatives make advanced Integration |
| Simplest Infrastructure Monitoring | Costly for Colossal Amounts of Details |
| Quite a bit of of native integrations |
Users
- Safety Analyst
- Incident Responder
- Safety Engineer
- SOC Analyst
- SOC Supervisor
- Cyber security researcher
- Managed Safety Service suppliers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
15. Dynatrace

Simplifying cloud complexity, this incident response machine is amongst the preferrred.
Furthermore, it presents scalability to the automated observability and hastens digital transformation.
In terms of Dynatrace, the massive infrastructure it depends on enables its users to innovate more rapid.
With limited effort, it is going to collaborate on the entirety.
This as a lot as this point machine package automates cloud operations, and heaps of considerable organizations belief it.
Furthermore, it presents an unparalleled on-line trip.
Components
- Monitors all apps, services, infrastructure, and user trip at some stage within the stack.
- AI and motive-and-enact diagnosis diagnose performance disorders in proper time.
- observes and reports proper-time app utilization.
- It presents performance-improvement advice essentially essentially based on AI-powered be taught.
- Monitors cloud-native and hybrid environments, offering you fat infrastructure alter.
Demo Video
| What’s Correct ? | What Could well Be Higher ? |
|---|---|
| Continuous, automated understand | Less interplay |
| Job-to-route of relationships | The payment is limited high |
| Intuitive infographics |
Users
- Safety Analyst
- Incident Responder
- Cyber security Analyst
- Likelihood Analyst
- SOC Analyst
- SOC Supervisor
- Managed Safety Service suppliers
- Incident Response Service Vendors
Industries
- Details Technology and Products and services
- Computer Gadget
- Details security
- Authorities Companies
- Financial services
- Healthcare industry
Designate
Which you might perhaps presumably accumulate a free trial and personalized demo from right here.
Conclusion
Cyber-attacks and threats are rising day-to-day, so we must defend song of the entirety so that our industry goes safe.
There are the above Incident Response Instruments that merit to video display the logs, detect many suspicious activities, defend records, and heaps of diverse issues
Also Read
Simplest UTM Gadget (Unified Likelihood Management Solutions)
Simplest Android Password Managers
Vulnerability Assessment and Penetration Testing (VAPT) Instruments
AWS Safety Instruments to Give protection to Your Atmosphere and Accounts
SMTP Test Instruments to Detect Server Components & To Test Email Safety
On-line Penetration Testing Instruments for Reconnaissance and Exploit Search
Simplest Developed Endpoint Safety Instruments
10 Simplest SysAdmin Instruments
Source credit : cybersecuritynews.com





