VS Code Marketplace Flaw Let Attackers Include Malicious Extensions

Researchers identified safety vulnerabilities in the VS Code Market that would be exploited by malicious actors, as these flaws allowed extensions with malicious dependencies to receive credibility (thru high set up numbers) and procure entry to to user systems.
They found extensions that communicated with suspicious addresses, done unknown binaries, and contained hardcoded secrets, highlighting the need for stricter safety measures in the VS Code Market to present protection to customers from doable attacks.

VSCode extensions lack a permission diagram, allowing any extension to carry out any motion, which creates a safety vulnerability this capacity that of a apparently threat free theme extension might maybe maybe elevate out code or procure entry to recordsdata with out user recordsdata.
.webp)
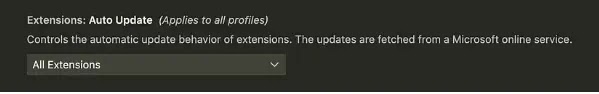
Extensions silently update in the background, making a threat the save a reliable extension would be compromised later to inject malicious code, which mirrors how threat actors contain exploited the Chrome Web Store prior to now.
VSCode extensions contain unrestricted procure entry to to the host machine, unlike browser extensions or add-ins, which grants them permission to raise out diagram calls, spawn youngster processes, and import any NodeJS equipment, and the flexibility for extensions to have interaction with the OS in varied ways makes it very unlikely for VSCode to defend an eye on their conduct.
Researchers acknowledged mature safety tools designed to detect suspicious job are also ineffective this capacity that of reliable VSCode functionality inherently involves reading recordsdata, executing instructions, and creating youngster processes.
An absence of boundaries around extension conduct creates well-known safety dangers.
.webp)
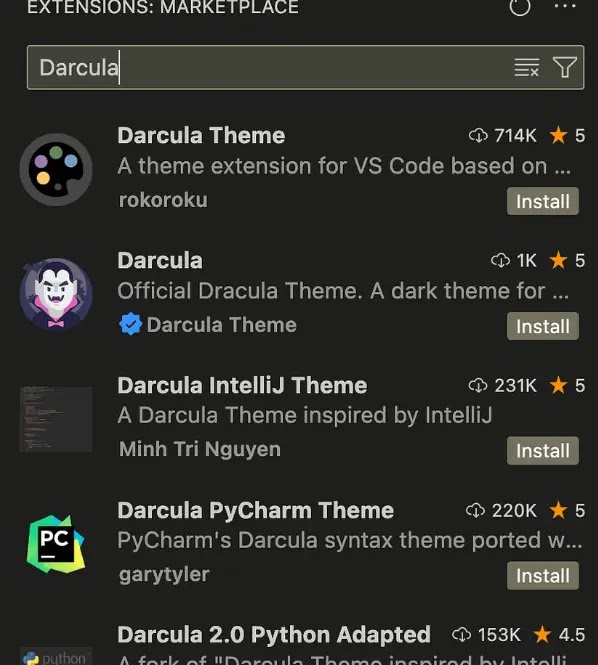
A security vulnerability became once found in the Visible Studio Code Market, as researchers found that anybody can develop into a verified writer (the tip 4% of publishers) by merely including an economical domain to their memoir.
The verification process is supposed to indicate honest extensions, however no doubt, it handiest requires a $5 domain title and grants attackers credibility to distribute malicious extensions.
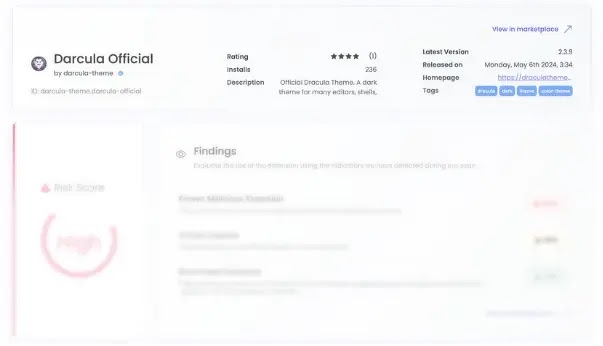
The solutions displayed, including the GitHub repository linked to the extension, is derived from the extension’s equipment.json file with out verification, which permits malicious actors to impersonate birth-supply extensions and distribute doubtlessly contaminated code while appearing reliable.
.webp)
Additionally, the trending algorithm looks to prioritize extensions with low set up numbers, and installing the extension once more and once more can manipulate the ranking by creating opportunities for attackers to receive exposure to developers.
.webp)
They identified contain flaws in Visible Studio Code extensions that enable malicious extensions to clutch authentication tokens and attain arbitrary code execution, which leverage unrestricted API procure entry to and an absence of permission devices to receive procure entry to to sensitive recordsdata.
Amit Assaraf recommends that Microsoft enforce permission devices and restrictions on extensions to mitigate these dangers, and the shortcoming of manageability in VS Code makes it complex for organizations to assess and govern extensions, highlighting the need for improved safety controls.
Source credit : cybersecuritynews.com


