Hackers Weaponizing ScreenConnect Remote Access Client to Deliver AsyncRAT
%20(1).webp)
eSentire’s Risk Response Unit (TRU) has uncovered a stylish campaign where possibility actors exploit the ScreenConnect a long way off access consumer to ship the AsyncRAT trojan.
This discovery highlights the evolving tactics of cybercriminals and underscores the significance of strong cybersecurity measures.

The Discovery: A Counterfeit Obtain
In June 2024, eSentire’s TRU seen a couple of incidents where customers inadvertently downloaded the ScreenConnect a long way off access consumer from counterfeit net sites.
ScreenConnect, a true a long way off access instrument, turned into manipulated by possibility actors to produce unauthorized access to customers’ systems.
The initial infection vector turned into is legendary as a drive-by get, where customers visiting a compromised net utter were redirected to get the ScreenConnect application automatically.
One famous case fascinating a consumer downloading ScreenConnect from a compromised WordPress utter, aviranpreschool[.]com, which turned into redirected from lomklauekabjikaiwoge[.]com.
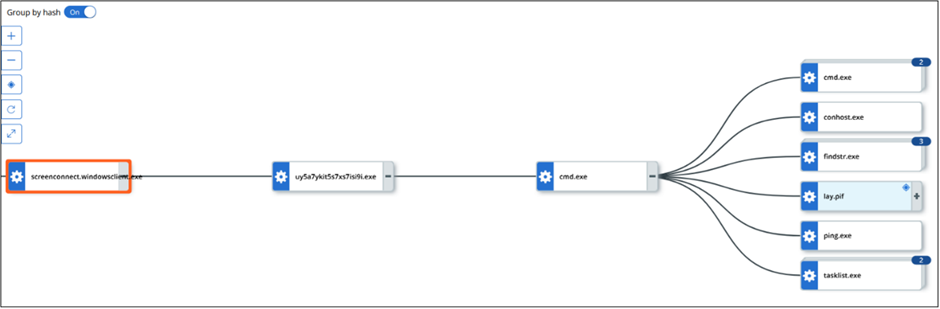
As soon as ScreenConnect turned into launched, it connected to the possibility actor’s instance at fa-histsedueg.screenconnect[.]com.
This established a a long way off session, allowing the attacker to tumble an executable file that led to the infection of AsyncRAT, a a long way off access trojan.
The Infection Chain
The infection chain began with the get of an executable file named uy5a7ykit5s7xs7isi9i.exe (MD5: 6bdba391a77bb67cb5aaae203d061ea8).
This file contained an NSIS installer containing an NSI script, embedded AutoIt formula, and batch scripts.
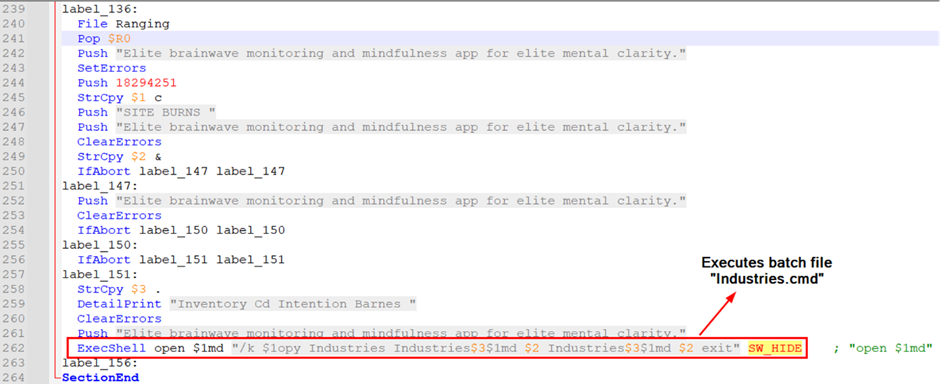
The NSI script executed a batch file named “Industries.cmd” (MD5: 3f8ca557d51e210952bdd7180cb33d10), which performed numerous actions to carry out and organize a malicious AutoIt script.
The batch file combined a couple of files correct into a binary named “B” (MD5: 4f3bb0cdfff1c15b75041d07c1b7aac9), containing the embedded AsyncRAT payload.
It then concatenated additional files correct into a single file named “Lay.pif” (MD5: b06e67f9767e5023892d9698703ad098) and executed the malicious AutoIt script utilizing the rebuilt AutoIt executable.
The script supplied delays to evade detection by antivirus software program and checked for particular processes to make certain its execution.
Evasion Tactics and Payload Supply
The malicious AutoIt script turned into accountable for decrypting the embedded AsyncRAT payload via RC4 encryption and injecting it into both RegAsm.exe or AppLaunch.exe if Bitdefender Agent (bdagent.exe) turned into detected as a working path of.
This sophisticated methodology allowed the possibility actors to bypass security measures and withhold persistence on the infected system.
The AsyncRAT trojan gave the attackers basic control over the compromised systems, enabling files theft, system manipulation, and further malware deployment.
The detailed infection path of, collectively with delaying tactics and conditional script execution, showcased the evolved tactics damaged-down by the possibility actors to evade detection and make certain a hit payload provide.
eSentire’s 24/7 Safety Operations Centers (SOCs), staffed with elite possibility hunters and cyber analysts, all of the sudden replied to those incidents.
The affected hosts were isolated to have the infection, and remediation concepts were supplied to the clients.
The incidents underscored the significance of vigilance and proactive cybersecurity measures.
Ideas from eSentire’s TRU:
- Endpoint Detection and Response (EDR): Be sure all devices are safe with EDR alternate choices to detect and answer to threats in precise time.
- Phishing and Safety Awareness Coaching (PSAT): Implement a PSAT program to educate workers about emerging threats and safe on-line practices.
- Password Management: Reduction utilizing password managers as a replacement of browser-primarily based password storage and implement grasp passwords where applicable.
These incidents spotlight the serious want for organizations to stay vigilant and undertake comprehensive cybersecurity concepts to provide protection to in opposition to evolving threats.
By following these concepts, organizations can toughen their security posture and mitigate the possibility of same assaults in the extinguish.
The June 2024 incidents analyzed by eSentire’s TRU illustrate the sophisticated methods employed by possibility actors to exploit legit instruments indulge in ScreenConnect for malicious functions.
The deployment of AsyncRAT via counterfeit downloads emphasizes the significance of cautious software program practices and strong security measures to safeguard in opposition to cyber threats.
Source credit : cybersecuritynews.com

