The Power of Threat Intelligence Platforms for Faster Threat Investigations Checklist
In cybersecurity, knowledge is what in a roundabout draw makes it ability to answer threats effectively and proactively. A number of the very best solutions to procure it is by the employ of threat intelligence platforms. By offering threat context and enrichment, they allow analysts to function told choices with self belief, allowing them to shift from reactive defense to proactive threat looking out.
What are Threat Intelligence Platforms?
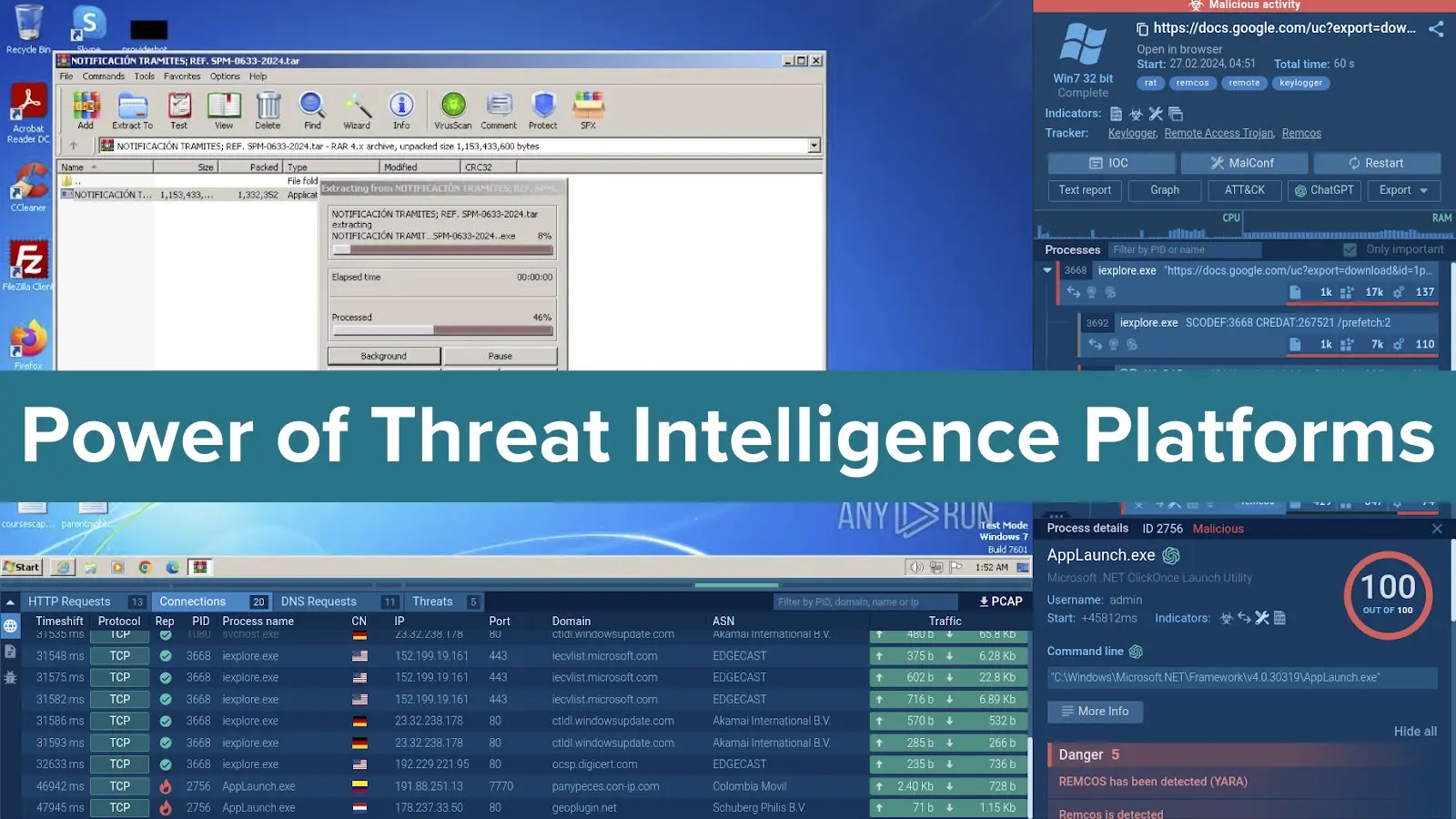
A threat intelligence platform (TIP) is a searchable hub of threat intelligence offering precise-time updates on new and existing malware, vulnerabilities, and attacker tactics, received via security researchers and substitute collaborations. This knowledge comes from varied sources, including threat intelligence feeds, start-offer intelligence (OSINT), sandboxes, and masses others.
The facts available on TIPs encompasses community indicators (IP addresses, arena names, URLs) and malware knowledge (file hashes and names, domains, tactics, tactics, and procedures).
For threat intelligence platforms (TIPs) that leverage malware evaluation sandboxes knowledge, the searchable ingredients lengthen beyond standard indicators of compromise (IOCs) to embody detailed system knowledge similar to repeat strains, registry say, and operating processes.
Are trying Threat Intelligence Lookup from the ANY.RUN sandbox
Bigger than 400,000 analysts employ ANY.RUN is a malware evaluation sandbox worldwide. Be a part of the community to conduct in-depth investigations into the cease threats and procure detailed reports on their behavior..
To demonstrate how a TIP might perchance maybe perchance additionally be old, imagine you receive an alert about an atypical URL. With a TIP, it is most likely you’ll perchance be in a space to speedily plod a search put a matter to to retrieve threat knowledge linked to this URL, similar to its threat stage, the malware linked to it and even its samples. This total research helps you to take dangle of told actions fancy extra investigation, escalation, or blocking off the threat.
Price of Threat Intelligence Platforms
1. Contextualizing Security Indicators for Truly helpful Prioritization
Threat Intelligence Platforms (TIPs) reinforce raw security signals by offering contextual knowledge. TIPs empower analysts to prioritize and focal point their efforts on potentially the indispensable disorders by enriching signals with malicious signatures and artifacts linked to threats. They’ll assess a threat’s severity and most likely affect consistent with its malicious activities and thus optimize their investigation time and resources.
2. Enabling Proactive Threat Hunting for Early Detection and Mitigation
Though-provoking from reactive to proactive security is main within the face of evolving cyber threats. TIPs empower analysts to cross beyond factual reacting to signals by offering tools for proactive threat looking out.
For occasion, TIPsâ superior search capabilities enable analysts to place a matter to various knowledge sources the employ of particular indicators, patterns, and behaviors to name most likely threats.
TIPs additionally like new knowledge about emerging threats, attacker tactics, tactics, and procedures (TTPs), and vulnerabilities, allowing analysts to pause sooner than most likely attacks and anticipate them.
3. Gaining Broader Threat Landscape Visibility for Truly helpful Security Decisions
To function told security choices, it is main to own a total figuring out of the evolving threat landscape. TIPs feature as a central hub, aggregating knowledge from varied sources. This provides analysts a holistic research of the threat landscape, allowing them to name connections and patterns between reputedly disparate events.
Developed Search with Threat Intelligence Lookup
Letâs now watch how TIPs operate and might perchance maybe perchance additionally be old in precise-world conditions. Threat Intelligence Lookup (TI Lookup) is a TIP that runs on the facts extracted from ANY.RUN sandboxâs intensive database of thousands and thousands of interactive malware evaluation sessions (projects). For that reason, it helps you to experience beyond standard key phrase searches and craft subtle queries the employ of over 30 fields, including registry paths and Suricata solutions. Listed below are these forms of:
1. Wildcards and Combined Requests
The MITRE ATT&CK framework provides a standardized language for describing attacker tactics, tactics, and procedures (TTPs). TI Lookup leverages the energy of MITRE ATT&CK by enabling you to appear particular tactics or combos of tactics within your threat intelligence knowledge.
Letâs submit the following ask: MITRE:”^T108″ AND ThreatName:”remcos”.
The platform provides a hundred assorted samples of Remcos, as effectively as linked events where MITRE tactics starting with “T108” had been old.
We can explore each and each of these samples in ingredient by going over to the ANY.RUN sandbox to analyze the community and registry say, watch the processes launched in some unspecified time in the future of the malware execution, as effectively as to procure precious IOCs and total threat reports.
| Are trying Threat Intelligence Lookup from the ANY.RUN sandbox. Obtain the first 50 requests without cost. |
2. Browsing for Explicit Registry Keys
TI Lookup permits you to appear particular registry keys, even these containing backslashes. Nonetheless, it’s essential to secure away the backslash character by doubling it within your put a matter to.
Example: RegistryKey:”HKEY_LOCAL_MACHINE\Application\Microsoft\Windows\CurrentVersion\Walk”
This ask searches for any instances of applications or processes configured to plod robotically at startup. The platform finds over 400 assorted events that meet the search standards.
3. Exploring File Hashes
TI Lookup provides total search capabilities the employ of assorted file hashes, including SHA256, SHA1, and MD5. This permits you to speedily name most likely threats consistent with recognized malicious file signatures.
Example: SHA-256:”7c2cf95543435f55cf814477874ba460fc6efc39438c15fb5bf49ffeb4142c2e”
This put a matter to searches for all instances where the file with the explicit SHA256 hash has been analyzed in some unspecified time in the future of the platform. The raze outcome reveals that this hash belongs to a file linked to the RisePro malware.
4. Focusing on Explicit Job Paths
Much like registry keys, it is most likely you’ll perchance be in a space to appear instances where a particular route of direction has been seen. Take into accout to double the backslash character within your put a matter to to secure away it.
Example: ImagePath:”C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe”
This put a matter to searches for instances where the C# compiler is being executed. The platform returns 13 projects, as effectively as events and recordsdata linked to the put a matter to.
5. Leveraging IP Addresses
Finally, it is most likely you’ll perchance be in a space to incorporate IP addresses into your search queries. This permits you to analyze particular endpoints or name most likely geographical trends linked to threats.
The put a matter to within the screenshot above searches for all incidents sharp the IP contend with in ask. The platform speedily identifies it as malicious, hyperlinks to the Asyncrat malware, and provides linked URLs, recordsdata, events, and projects.
Are trying ANY.RUN
You might perchance well explore superior search alternatives of Threat Intelligence Lookup take dangle of just correct thing about its energy to enhance your organizationâs cybersecurity posture. Interrogate a provider trial and secure 50 free requests to envision its capabilities.
Source credit : cybersecuritynews.com