How to Analyse Crypto Malware in ANY.RUN Sandbox ?
ANY.RUN, an interactive malware sandbox, has published a complete diagnosis of the growing possibility that crypto-malware poses in a time when it’s extra significant than ever to be pleased sturdy digital security.
This malicious plot, designed to covertly mine cryptocurrency utilizing infected devices’ processing energy, represents a massive shift within the cyber possibility panorama.
Let’s be pleased an intensive peep at crypto-malware, its loads of forms, and how its platform will even be leveraged to analyze and wrestle this insidious possibility.
ANY.RUN is a cloud-basically based mostly environment for analyzing Windows malware and Linux-basically based mostly samples. Malware analysts, SOC, DFIR teams can safely learn about threats, simulate various eventualities, and attain insights into malware behavior to toughen cybersecurity suggestions.
ANY.RUNÂ also allows researchers to take care of malware behavior, catch IOCs, and without declare arrangement malicious actions to TTPsâall in our interactive sandbox.
 The Possibility Intelligence Search for platform helps security researchers decide up linked possibility recordsdata from sandbox tasks of ANY.RUN.
What’s Cryptomining Malware?
Cryptomining malware, or cryptojacking, hijacks a aim’s computing resources to mine cryptocurrencies fancy Bitcoin. This malware performs complex mathematical calculations to verify cryptocurrency transactions, requiring significant CPU and incessantly GPU energy.
Unlike legitimate mining operations, the rewards of this illicit activity lunge to the attackers, leaving tool owners with degraded system performance and increased electrical energy payments.
Examples of Cryptomining Malware
The panorama of cryptomining malware is various, with loads of suggestions employed to contaminate aim computers. These differ from code embedded in web sites to classic e mail phishing attacks. As soon as in space, the malware operates within the background, making detection now now not easy.
High-profile examples of crypto-jacking consist of the Mirai botnet, which has been adapted for crypto-mining functions, showcasing the adaptability and persistence of cybercriminals in exploiting digital resources for monetary accomplish.
Cybersecurity consultants from ANY.RUN’s story neatly-known a upward push in utilizing crypto mining malware, with XMRig and DarkGate being two well-liked examples of this malicious plot’s repurposing by cyber criminals. Right here’s a being concerned pattern for digital security.
XMRig
XMRig, before all the pieces an originate-provide CPU mining plot intended for the cryptocurrency Monero (XMR), has been hijacked and embedded inside of the malware.
The altered model of XMRig is designed to stealthily alter its mining intensity consistent with the system’s CPU utilization. This crafty adaptation allows it to evade detection, as it avoids the long-established indicators of excessive handy resource consumption that will furthermore alert users to its presence.
DarkGate
Meanwhile, DarkGate, a multifaceted malware loader, has been found to enact crypto-mining payloads, including the compromised model of XMRig.
DarkGate is insidious attributable to its ability to function system-stage privileges on infected machines. It employs rootkit-fancy parts to withhold persistence, making it now now not easy to snatch away.
Tactics outdated by DarkGate to be sure its persevered operation consist of initiating from an LNK file within the Windows Startup folder, altering registry keys to urge in tandem with the LNK file, or utilizing a DLL file, varying with its configuration settings.
Examining Crypto Malware in ANY.RUN
ANY.RUN presents a reducing-edge resolution for analyzing crypto malware thru interactive malware sandboxes. This technology allows for the detailed examination of suspicious files, which unsolicited mail filters can robotically put up for diagnosis.
In a most trendy technical diagnosis, ANY.RUN efficiently acknowledged a crypto miner utilizing its developed detection capabilities, highlighting the effectiveness of its platform in combating the rising possibility of crypto-malware.
The detection used to be basically consistent with the miner’s network activity, which allowed ANY.RUN to bypass handbook investigation processes and straight proceed to catch Indicators of Compromise (IOCs).
The crypto miner, once activated, exhibited unmistakable indicators of malicious activity. Particularly, the system’s CPU utilization spiked to its most after startup, along with a massive amplify in RAM utilization.
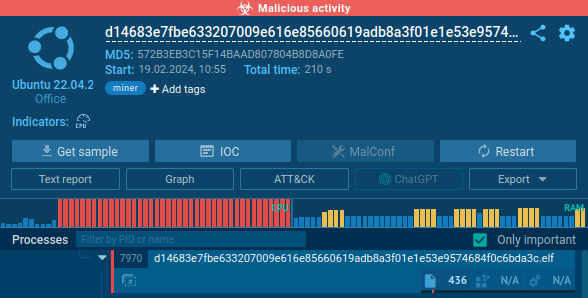
Such phenomenal behavior signifies a system being compromised, in particular when paired with the miner’s excessive network activity.
In an overwhelming existing of network exploitation, the miner sent almost 300,000 DNS requests to generate domains in lower than four minutes. This stage of network activity is extremely uncommon and a long way exceeds the bounds of legitimate plot operations, additional confirming the malicious nature of the entity.
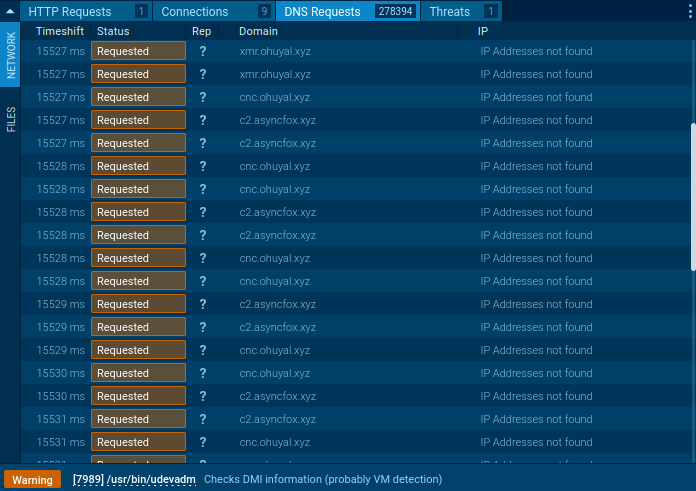
ANY.RUN’s thorough diagnosis established the existence of a crypto miner and made it seemingly to catch important IOCs hasty. These indicators are significant for configuring Security Knowledge and Occasion Management (SIEM) and Web Utility Firewall (WAF) programs to present protection to in disagreement possibility.
ANY.RUN’s ability to detect and analyze crypto malware with such precision underscores the importance of developed cybersecurity suggestions in as of late’s digital panorama.
As crypto malware continues to conform, platforms fancy ANY.RUN are important for figuring out and mitigating these restful but significant threats, safeguarding digital resources and affirming system integrity.
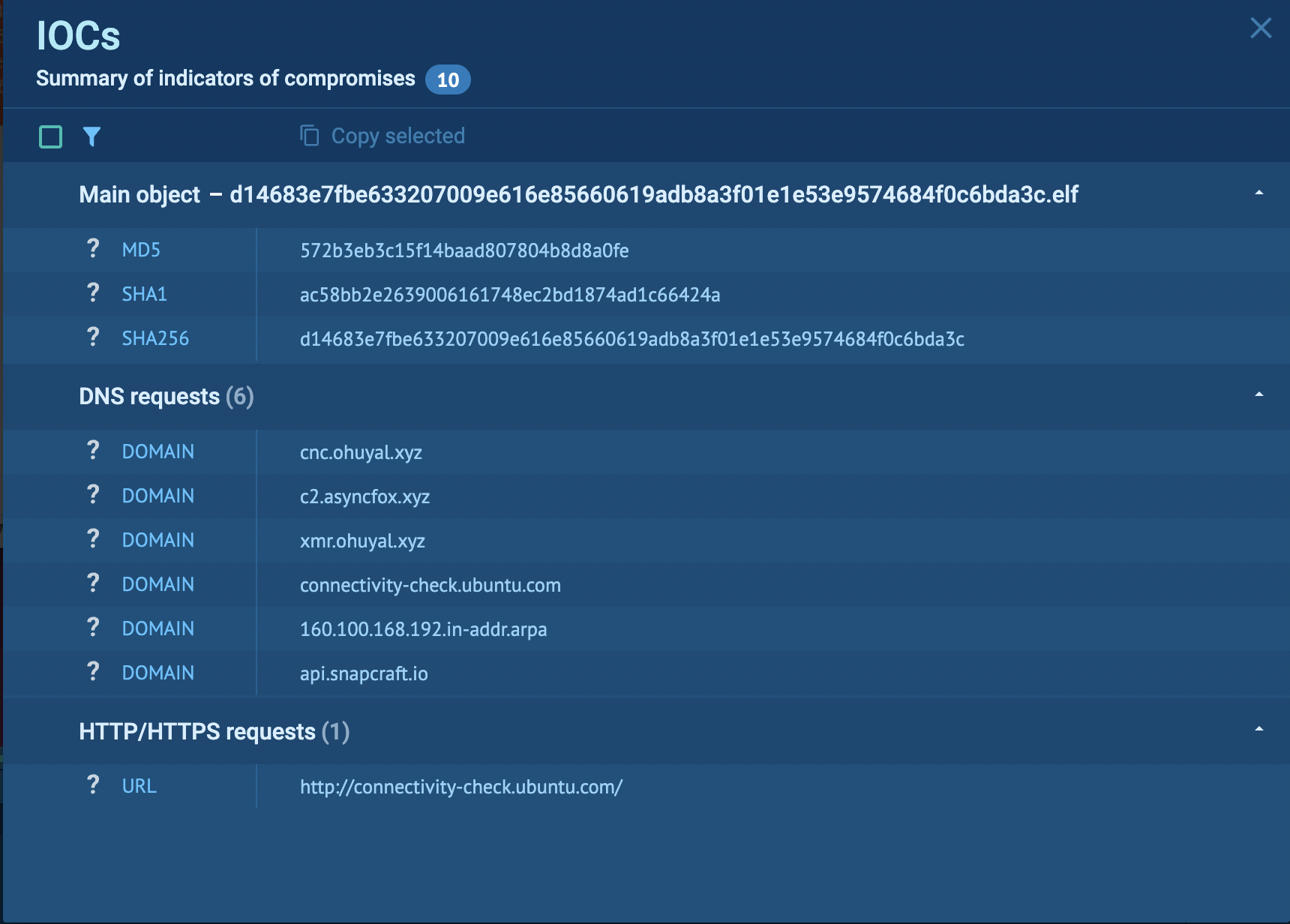
Customers can manually analyze these files or send samples straight by skill of API. By analyzing sandbox experiences, users can catch Indicators of Compromise (IOCs) and configure their security programs to fend off crypto malware attacks effectively.
Prevention
To safeguard against crypto-malware, ANY.RUN recommends a aggregate of vigilance and adherence to cybersecurity only practices. This involves exercising caution when downloading plot and visiting web sites, conserving programs updated, and utilizing legitimate antivirus suggestions.
Monitoring for uncommon spikes in CPU utilization could furthermore also function an early warning signal of an infection, enabling users to snatch swift motion to mitigate seemingly afflict.
Forestall Crypto-Malware Assaults
EDR system configuration: EDR can warn you of uncommon CPU/GPU and reminiscence utilization by non-traditional functions.
Also out for arresting direction of executions, in particular those connecting to acknowledged crypto mining pool addresses.
Originate use of the Possibility Intelligence search for. Employ true-time possibility recordsdata to update TIP and SIEM programs with crypto-malware indications (IPs, domains, and file hashes).
Space up e mail filters. Block executable, script, and macro-filled e mail attachments. Ship questionable files for handbook assessment robotically.
Analyze samples with Interactive Malware Sandboxes fancy ANY.RUN. Automatically send suspected unsolicited mail filter-detected files to ANY.RUN for complete diagnosis by API or fee. Analyze sandbox experiences for IOCs and security system configuration.
Who is ANY.RUN?
Because the digital world continues to conform, the specter of crypto-malware looms increased, making the insights and tools supplied by ANY.RUN is extra important than ever.
By approach to their complete diagnosis and innovative sandbox technology, ANY.RUN empowers users to take care of and protect against crypto-malware’s restful but significant possibility.
For additional recordsdata on ANY.RUN’s diagnosis of crypto-malware and how their platform can support in combating this possibility, it’s seemingly you’ll perchance furthermore derive derive entry to to ANY.RUN sandbox platform free of fee.
If youâre from the SOC and DFIR teams to study incidents and streamline possibility diagnosis. Strive all parts of ANY.RUN at zero model for 14 days with a free trial.
Source credit : cybersecuritynews.com






