What is a Honeypot? How does it Improve Network security?
What is a Honeypot? How does it Increase Network security?
One security measure that will be feeble to entice attackers is a honeypot, which creates a digital entice. An attacker can maintain shut attend of the intention’s weaknesses since it’s miles purposefully vulnerable.
You’d want to connect within the effort and time to toughen your security insurance policies. Application, file servers, routers, and diversified resource-intensive techniques will be examined in a honeypot setting.
It is some distance also one form of deception technology that can develop you imprint the behavioral pattern of the attacker. In most cases, that security crew uses the honeypots to evaluate the cybersecurity breaches and the arrangement in which they catch intel for cybercriminals operations. By doing this operation, that it’s seemingly you’ll even nick the anguish of wrong issues in contrast with the cybersecurity measures.
Honeypot mainly is dependent upon the deployment and develop. All the issues looks vulnerable and legitimate to attract cyber criminals.
Desk of Contents:
FAQ
Form of Honeypot Deployment:
What are Honeypots Ancient for?
Spam Trap: An Email Honeypot:
Advantages of Honeypots:
Honeynet
Closing tips
FAQ
1.What is a honeypot in community security?
A community security honeypot is a counterfeit intention or server that pulls cyberattackers. Its valuable aim is to detect, deflect, or research hacking makes an strive and predicament hackers to augment security.
Honeypots replicate accurate techniques with valuable recordsdata and resources, equivalent to databases or file servers, nonetheless are separated and monitored.
Since honeypots would perchance perchance soundless no longer scheme legitimate traffic, any interaction with one is suspicious. This lets security groups investigate cross-take a look at intrusion recommendations, acquire weaknesses, and toughen community security without risking resources.
2.Why is a honeynet precious?
Honeynets provide managed research of attacker behavior and techniques in a cosmopolitan and interactive setting. Cybercriminals acquire honeynets more appealing than single honeypots as a result of they’ve a community of decoy techniques.
Security professionals can better imprint attack patterns, recommendations, and lateral movement in a community due to its complexity.
Honeynets construct intelligence by capturing a worthy wider spectrum of threats, from automated worms to sophisticated centered attacks, by closely emulating a accurate community’s develop.
This intelligence aids proactive security and research by bettering attack detection and prevention, cybersecurity threat determining, and security coverage and technology style.
3.What is the role of a proxy?
A proxy connects a individual to the web, including security and performance. Customers that connect to the web by a proxy server ship their requests to the proxy, which relays them to the web server.
Net server replies are sent to the proxy and subsequently the patron. This project anonymizes the patron’s IP take care of, improves privacy, filters and monitors web traffic for security, blocks malicious sites and shaded mumble material, and caches web sites to tempo up frequently accessed resources and nick bandwidth usage.
Proxy servers organize, get, and optimize web connections for participants and firms by acting as gateways.
Form of Honeypot Deployment:
There are a complete of three forms of honeypot deployment accessible. These are mentioned below:
- Pure honeypots: This takes care of a complete production intention that gets an attack by worm taps then this will bag connected with the honeypot. They are very unsophisticated.
- Low-interaction honeypots: They imitate the carrier and intention, which mainly attracts prison consideration. That time Honeypot will catch the recordsdata from blind attackers love worms, malware, botnets, etc.
- Excessive-interaction honeypots: This is a basically complex setup that looks love the valid production of infrastructure. They attain no longer limit the project stage, which affords intensive cybersecurity. Honeypot also has bigger upkeep and abilities in extra technology, including digital machines. This ensures that the attacker usually are now not in a position to bag entry to the valid intention.
What are Honeypots Ancient for?
Any community can bag pleasure from using honeypots, which legend recordsdata from undesirable customers who’re misled into thinking they’re a sound a part of the community.
These traps are usually feeble by security groups as section of their community defense strategy. You’d furthermore consume a honeypot to investigate cross-take a look at how cyberattacks behave when interacting with a community.

Spam entice helps the honeypot the attach they might be able to attain the setup so that email addresses can attract unsolicited mail web traffic. In most cases, unsolicited mail traps are feeble for Project Honey Pot, which is embedded within the web residing instrument.
They need recordsdata connected to the spammers, including IP addresses, email addresses, and diversified residing addresses. It doesn’t bag feeble for the safety features that every person can consume for community reconnaissance, even hackers.
Spam Trap: An Email Honeypot:
As we’ve already mentioned the unsolicited mail entice is a fraud administration instrument that helps by providing web carrier suppliers. This also helps to establish and block the spammers. They are going to develop client inboxes get by blockading vulnerabilities.
A unsolicited mail entice can develop a counterfeit email take care of that gets feeble by the bait spammers. There are few legitimate emails sent to the counterfeit take care of so when you happen to get the mail this will slither to unsolicited mail.
Right here that it’s seemingly you’ll even bag diversified forms of unsolicited mail traps, which would perchance perchance be mentioned below:
- Username typos: The unsolicited mail filter detects typos error that will be executed by machine or the human nonetheless this will reach within the unsolicited mail folder. Quite so a lot of the time, the misspelled will be an email take care of.
- Expired email accounts: Few suppliers can consume abandoned email accounts, which is in a position to lope out within the arena establish, that often is the the same as unsolicited mail traps.
- Aquire email lists: They devour many invalid email addresses, which would perchance trigger a unsolicited mail entice. For the explanation that sender doesn’t bag the authorization to ship the electronic mail, they bag handled within the spammer’s checklist and bag backlisted.
Advantages of Honeypots:
Factual inserting a honeypot to your community will now not complete your wants; there are diversified security controls accessible equivalent to intrusion detection techniques, firewalls, intrusion prevention techniques, and heaps more. Advantages are described below:
- It helps to distract the cybercriminal so that they might be able to no longer target the legitimate intention. The more time they convey on the honeypot, the much less it be important to make investments within the intention to attract them.
- It offers you the greatest visibility so that attacks can happen fast. The attacker does the keystroke to ship the 2nd indicators and the scammer gets an are attempting to bag entry to the intention.
- It is seemingly you’ll perchance perchance even monitor the attackerâs behavior and detect the vulnerabilities. One more facet it be important to originate the revealed signature so that it’s seemingly you’ll even establish the attack.
- Honeypot will will enable you to do the organizationâs incident response capabilities to the take a look at. You’d want to put together your crew to carry shut acceptable countermeasures to block that attacker and his bag entry to.
- Honeypot also helps to augment your companyâs all-over security. It mainly locations the sunshine on the attackers so that it’s seemingly you’ll even formulate the true prevention recommendations.
- Honeypot is a basically payment-effective methodology, and it’s miles also a upright funding, nonetheless this will handiest work together when malicious project happens, and it doesn’t require any excessive-performance resources to manipulate the community traffic for an attack.
- It will clutch all forms of malicious project, though attackers consume encryption.
- Honeypot collects the recordsdata from the attacks which consist of unauthorized project, a rich source of precious recordsdata, and heaps more.
Honeynet
This honeynet comprises two or more honeypots for one community. Must you maintain an interconnected community that time honeypot gets feeble. It permits the group to trace the attackerâs interaction with the resource.
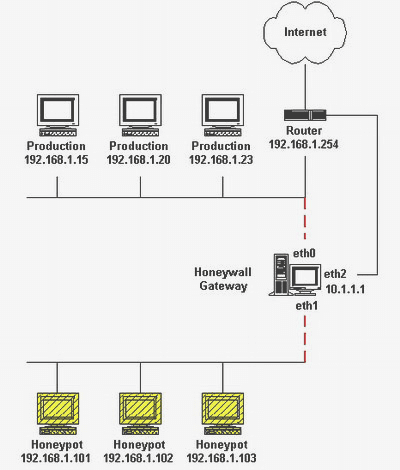
It also helps you monitor intruder moves within the community so that it’s seemingly you’ll even work along with multiple aspects at one time. The principle aim is to catch the hacker and successfully breach the community, so when you happen to maintain more community destinations, it would perchance perchance be more convincing for the attacker.
Deception technology is the more complex implementation for the honeypots to boot to a honeynet. It frequently purposes with diversified technology love subsequent-technology firewalls, Win web gateways, and IDSes. This technology comprises automated aspects the attach the honeypot can respond the valid time to seemingly attackers.
Closing tips
Cyber threats will continue and Honeypot will attend the group to attend the ever-altering threat panorama. Though it’s miles not seemingly to predict that it’s seemingly you’ll even prevent every attack with the attend of a honeypot.
It continuously affords precious recordsdata and makes sure that the group can put together for the response to the attacker’s act. This is a upright express for the cybersecurity decent to bag all hacking-connected recordsdata.
It is seemingly you’ll perchance perchance apply us on Linkedin, Twitter, and Facebook for each day Cybersecurity and hacking recordsdata updates.
Also Read
What is ICMP Protocol â How does ICMP work, Message Code & ICMP DDoS
What is WarXing in Cyber Security? What are the Advantages?
What Is SOAR and How It Works? Choices and Advantages
Source credit : cybersecuritynews.com






