“Mobile NotPetya”!! Surge in Zero-click Vulnerabilities, Conditions Favour
.webp)
The cybersecurity community is sounding the fright regarding the rising probability of a “cellular NotPetya” match – a self-propagating cellular malware outbreak that would additionally beget devastating consequences.
All over the final yr, the alarming blueprint better within the invention and exploitation of zero-click vulnerabilities in cellular operating methods drives this grief.

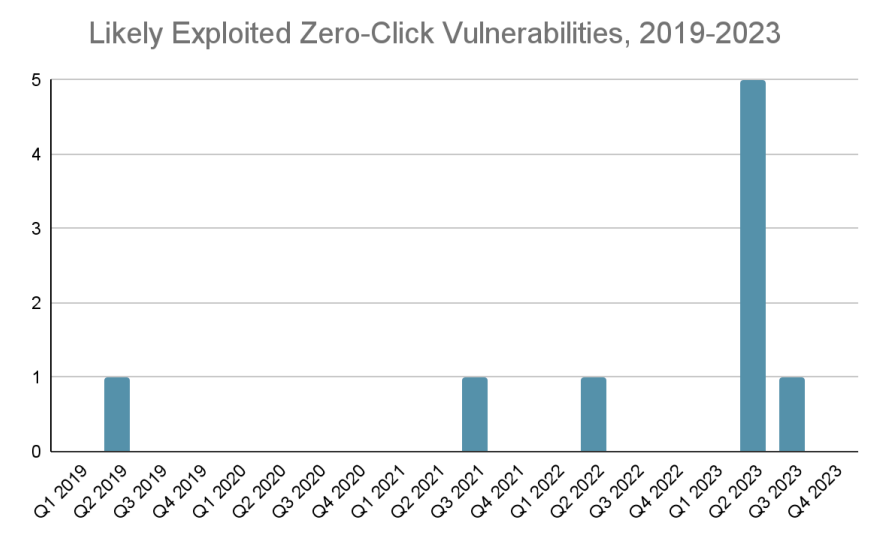
In 2023 by myself, more zero-click vulnerabilities were disclosed than mixed within the prior four years.
Experts warn that the stipulations are ripe for a cellular malware match on the dimensions of the 2017 NotPetya ransomware assault, which prompted over $10 billion in damages worldwide.
The Upward thrust of Zero-click Exploits
The severe ingredient for a “cellular NotPetya” is malware’s means to unfold autonomously through zero-click vulnerabilities without requiring particular person interaction.
All over the final few years, there has been a troubling surge within the invention and exploitation of such vulnerabilities:
- In May well additionally merely 2019, a WhatsApp zero-click vulnerability (CVE-2019-3568) allowed attackers to ship Pegasus spyware and adware to victims through malicious RTCP packets.
- In December 2020, Citizen Lab reported on the “KISMET” zero-click exploit, which abused iOS 13.5’s messaging parts to infect gadgets with Pegasus.
- In September 2021, Citizen Lab disclosed the “FORCEDENTRY” zero-click exploit, which focused a vulnerability (CVE-2021-30860) in Apple’s scream rendering library.
- In April 2023, Apple patched a nil-click vulnerability (CVE-2023-28205) in iOS that would additionally had been actively exploited.
- In June 2023, Kaspersky disclosed the “Operation Triangulation” campaign, which exploited six zero-day vulnerabilities, including one which might additionally write to unknown hardware registers.
The sequence of disclosed zero-click exploits has skyrocketed, from correct form 3 in 2019-2022 to 6 within the first two quarters of 2023 by myself.
Experts warn that this pattern will proceed as spyware and adware companies and various probability actors dedicate sources to discovering and exploiting these vulnerabilities.
Recorded Future no longer too prolonged ago released an article highlighting the surge in zero-click vulnerabilities within the Cell NotPetya malware.
The article additionally discusses the favorable stipulations for such vulnerabilities to be exploited.
Conditions Ripe for a “Cell NotPetya”
The important thing parts for a devastating cellular malware outbreak are all in situation:
- Zero-click exploits: Spyware companies’ ongoing pattern of zero-click vulnerabilities permits malware to unfold autonomously.
- Independent unfold: Cell malware could additionally abuse contact lists and Bluetooth to propagate to current victims.
- Monoculture panorama: Android and iOS dominate the cellular OS market, which manner a single vulnerability could additionally beget an outsized affect.
- Lack of effective mitigations: Measures love Apple’s Lockdown Mode are no longer going to be widely adopted, and tech companies earn no longer beget any particular public plans to end a cellular malware outbreak.
- Heightened motivations: Geopolitical tensions and the sophistication of cybercriminal groups blueprint better the probability of a cellular malware assault being deployed intentionally or accidentally.
Experts believe telecommunications companies and machine manufacturers could additionally beget some tools to end a cellular NotPetya in its tracks, equivalent to:
- Filtering messages essentially essentially based on header data that is constant throughout malicious messages
- Blocking off messages originating from geographic clusters of infected gadgets
Alternatively, these measures beget no longer been examined at scale and can simplest be utilized as soon as a plague is underway, limiting their effectiveness.
The cybersecurity community is sounding the fright – the stipulations are ripe for a devastating “cellular NotPetya” match.
The probability of an very fair correct-scale cellular malware outbreak is rising with the surge in zero-click vulnerabilities and the lack of particular mitigation methods.
Tech companies, governments, and the safety community must urgently deal with this rising probability earlier than it’s too slack.
Source credit : cybersecuritynews.com


