Hackers Hijacking Antivirus Updates to Deliver GuptiMiner

A cosmopolitan malware campaign has been compromising the update mechanism of eScan antivirus utility to distribute malicious backdoors and cryptocurrency mining utility.
The campaign, dubbed GuptiMiner, has been linked to a possibility actor with doable connections to the notorious Kimsuky community.

GuptiMiner leverages a person-in-the-center attack to use vulnerabilities within the update course of of the eScan antivirus, a fabricated from an Indian cybersecurity agency.
By hijacking this course of, the attackers luxuriate in been ready to distribute their malware to unsuspecting customers stealthily.
Avast’s investigation resulted in the discovery of the project, which was once promptly reported to eScan and India’s Pc Emergency Response Staff (CERT). On July 31, 2023, eScan confirmed that the vulnerability had been addressed and resolved.
GuptiMiner Operation
The GuptiMiner campaign is now not restricted to a single form of malware however positive aspects a range of tools designed to breach noteworthy corporate networks.
Two clear backdoors luxuriate in been identified, every with the doable to present attackers with distant rep admission to to contaminated systems.
Moreover, the campaign’s final payload involves deploying XMRig, a successfully-known cryptocurrency mining utility, which harnesses the processing vitality of contaminated machines to mine Monero (XMR).
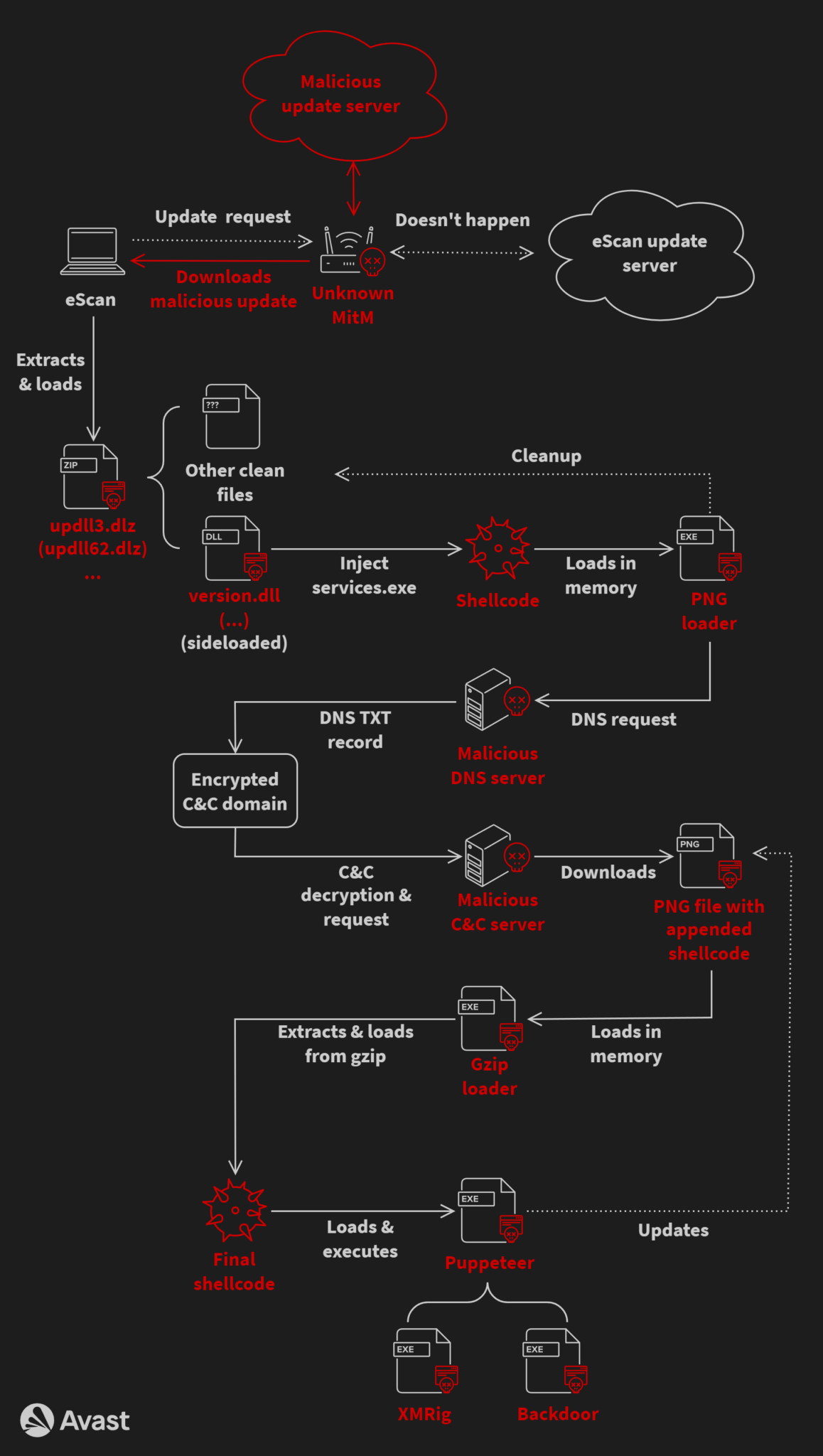
Since 2018, GuptiMiner has passed via indispensable evolution, with its developers repeatedly enhancing its capabilities. The malware displays a advanced an infection chain and employs superior ideas equivalent to:
- DNS requests to attacker-controlled servers
- Sideload malicious payloads
- Extracting executable code from seemingly benign pictures
- Utilizing a custom trusted root anchor certification authority to impress payloads
These sophisticated ideas now not handiest impress the attackers’ high stage of journey however additionally highlight the chronic possibility posed by such malware campaigns.
The GuptiMiner campaign represents a severe security possibility, in particular for noteworthy organizations that rely on antivirus strategies to shield their networks.
Hackers’ skill to make use of a trusted update course of as a supply mechanism for malware is a touching on development within the cybersecurity panorama.
In the GuptiMiner operation, the attackers aged superior ideas equivalent to DNS requests to the attacker’s DNS servers, sideloading, extracting payloads from pictures, and signing payloads with trusted root anchor certification authority.
Avast straight away mitigated the possibility upon discovery by disclosing the vulnerability to the affected occasions.
The swift response from eScan and the next resolution of the project has averted additional exploitation of the vulnerability.
Customers are told to be obvious their antivirus utility is as a lot as the moment and to dwell cautious of any irregular machine behavior that can also indicate a compromise.
Source credit : cybersecuritynews.com


