What Is Wireshark ? How to Use It For Network Sniffing?

Wireshark’s capabilities to analyze and visual display unit network traffic diagram it an indispensable tool for security experts, network administrators, and even outlandish members seeking to heed the continuous conversation between gadgets and programs.
The dependence on networks and the score is ever-increasing in this day’s interconnected world.

This growth has ended in a surge in doable assault vectors and security threats.
Community pentesting examines a computer network for flaws and openings that an attacker may well exploit.
A simulated network assault is performed to establish doable security vulnerabilities and assess their exploitability for unauthorized network or helpful resource fetch admission to.
It’s an mandatory tool for comprehending, retaining, and inserting forward networks within the favored period.
Furthermore, its trendy utility in penetration making an try out emphasizes the importance of spotting weaknesses and doable dangers to present protection to networked programs’ stability and security.
As an instance, Wireshark is seemingly one of many incident response instruments that may well establish doable security vulnerabilities comparable to unencrypted passwords and diversified gentle information transmitted in clear textual negate.
Desk of Boom material
What is Wireshark?
Wireshark Community Filtering
Who Created Wireshark?
Here’s a fleet timeline of the ancient past of Wireshark
How to download & Install Wireshark
Total Wireshark Uses
Conclusion
What is Wireshark?
Wireshark is a highly efficient, commence-supply network evaluation tool that permits customers to clutch and seek for network traffic. It’s miles a highly efficient tool enabling customers to clutch, analyze, and troubleshoot network traffic.
Wireshark enables seeing what’s going down on the network at a minute stage by inspecting the records packets flowing via the network interface. It has a person-friendly GUI with filters, colour coding, graphs, and diversified functions for traffic evaluation.
A lot of protocols are supported, including IP, TCP, UDP, HTTP, SSL/TLS, FTP, DNS, DHCP, and a range of more.
As a consequence, it is miles doable to analyze the traffic of diverse network applications and fabricate notify information about packets, comparable to header information, payload information, host conversations, top talkers, etc.
Wireshark can clutch information from network interfaces, including Ethernet, Wi-Fi, and Bluetooth. Users can peep the captured information at diverse ranges, from high-stage protocol summaries to detailed packet-stage analyses.
Wireshark Community Filtering
Wireshark affords several filtering and search functions that simplify locating and inspecting particular network events or issues.
There are several forms of filters:
- Capture filters: These filter incoming network traffic earlier than captures it. Capture filters are per the pcap filter syntax and shall be laid out within the clutch alternate suggestions dialog box or on the repeat line when starting up a clutch.
- Indicate filters: These are former to filter the captured network traffic that is displayed in most important window. Indicate filters are per Wireshark’s display filter syntax and shall be entered within the filter bar on the tip of the most important window.
- Protocol filters: These filter network traffic per the protocol being former. Protocol filters come in within the “Analyze” menu and can display most efficient traffic that makes declare of a notify protocol.
- Dialog filters: These filter network traffic per the conversation between two hosts. Dialog filters come in within the “Statistics” menu and display most efficient traffic between hosts.
Some Examples of Filters in Wireshark Consist of:
| ip.addr == 192.168.1.1 | This filter will display most efficient network traffic nice looking IP address 192.168.1.1 |
| TCP.port == 80 | This filter will display most efficient network traffic that makes declare of the TCP port 80, usually former for HTTP traffic. |
| udp | This filter will display most efficient network traffic that makes declare of the UDP protocol. |
| http.quiz.contrivance == “GET” | This filter will display most efficient HTTP traffic that makes declare of the GET contrivance. |
| ip.src == 192.168.1.1 && ip.dst == 192.168.1.2 | This filter will display most efficient network traffic between the IP addresses 192.168.1.1 and 192.168.1.2. |

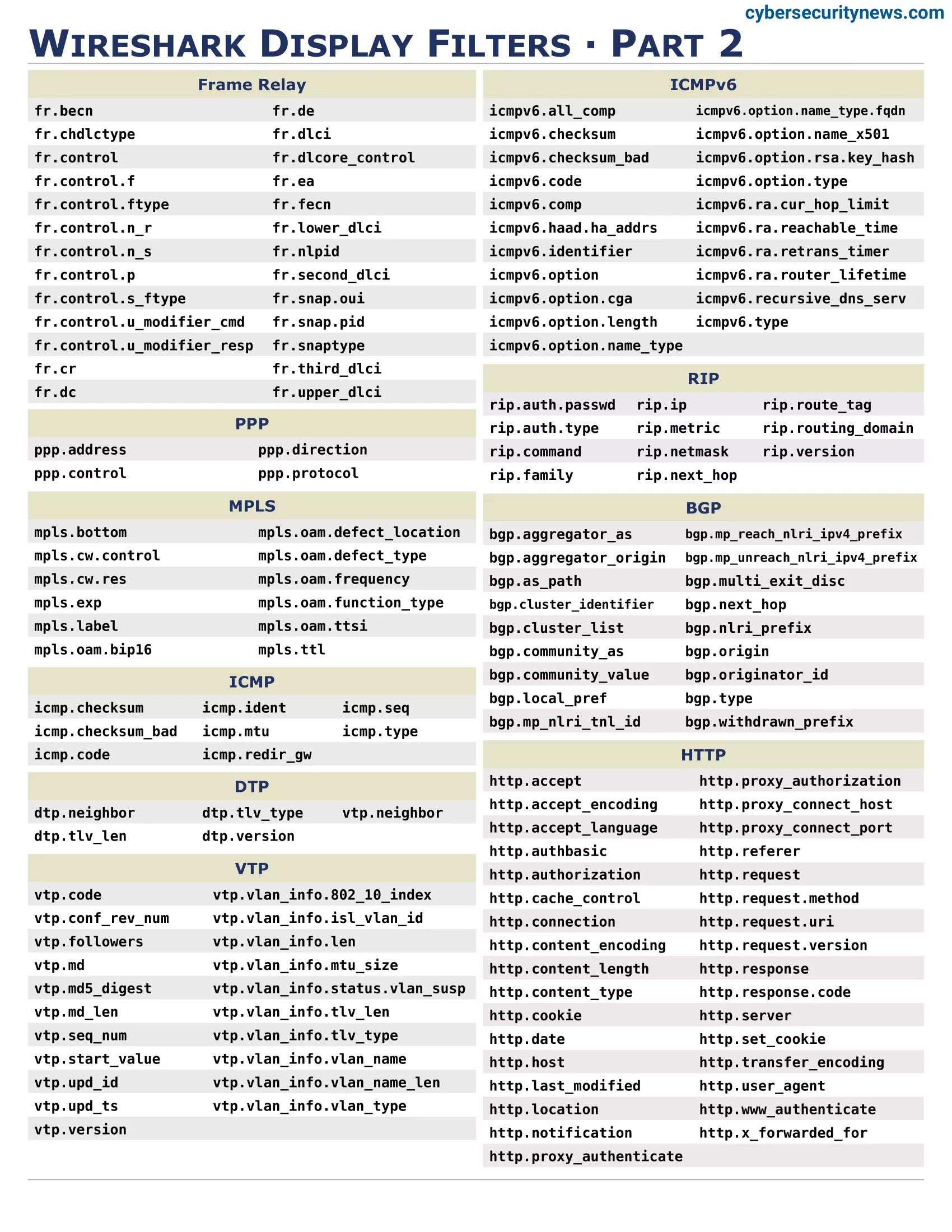
Who Created Wireshark?
Wireshark was created in 1998 by Gerald Combs. Combs was a computer science graduate pupil on the University of Missouri-Kansas Metropolis. He was engaged on a challenge to non-public a network analyzer tool to support him resolve network issues.
It was to delivery with named Ethereal but was renamed Wireshark in 2006 ensuing from trademark issues. It’s accessible for diverse platforms, including Windows, macOS, and Linux.
Wireshark is written within the C, C++, and Lua programming languages and launched below the GNU Fashioned Public License. The utility is continuously updated with unique functions, bug fixes, and security updates.
The community contains programmers, contributors, and customers who collaborate to present a clutch to and defend the utility most modern with the most most modern network protocols and applied sciences.
Versions 4.0.4 and 3.6.12, made accessible on March 2, 2023, are Wireshark’s most most modern procure versions as of April 2023.
Furthermore, Tool has a building delivery called Wireshark-git that contains the most most modern enhancements and bug fixes.
Version 3.6.12 is the supreme delivery branch with support for 32-bit Windows. Due to the this truth, updates will no longer be accessible for that platform after Would possibly maybe well well also honest 22, 2024.
Here’s a Transient Timeline of the Historical past of Wireshark:
- 1998: Gerald Combs creates the most important model of Wireshark below Ethereal.
- 1999: Ethereal is launched as commence-supply utility below the GPL.
- 2006: Ethereal is renamed to Wireshark ensuing from trademark issues.
- 2008: Wireshark 1.0 has a unique person interface and support for more protocols.
- 2010: Wireshark 1.4 is launched with improved efficiency and support for wireless protocols.
- 2013: Wireshark 1.10 is launched with a unique, more customizable person interface.
- 2015: Wireshark 2.0 is launched with a unique packet decoding engine and support for unique protocols.
- 2019: Wireshark 3.0 has a unique person interface and support for more protocols.
- 2020: Wireshark 3.3.0 Released – Up to this level Futures, New Protocol & Up to this level Capture File Enhance
- 2021: Wireshark 3.6 is launched with improved support for 5G and diversified unique applied sciences—supreme delivery to support 32-bit Windows.
- 2022: Wireshark 4.0 is launched with adjustments in quite a lot of filters and added many unique protocols support.
- 2023: Wireshark 4.0.4 and 3.6.12 is launched with multiple adjustments.
Total Wireshark Uses
Packet Analysis: Wireshark lets pentesters clutch, dissect, and analyze packets in trusty time or from saved files. This helps realize network protocols, establish vulnerabilities, and visual display unit network behavior.
- Community Discovery: Penetration testers can declare the tool to establish network gadgets, services, and topology, helping them blueprint the assault ground and opinion their penetration assessments.
- Protocol Analysis: Wireshark is geared up with decoders for a wide series of protocols, which permits pentesters to analyze diverse network conversation patterns and detect anomalies or suspicious activity.
- Sniffing Sensitive Knowledge: it will support pentesters establish gentle information transmitted over the network, comparable to passwords, session tokens, or confidential paperwork, which is in all chance at chance of interception and exploitation.
- Reconnaissance: Itcan be former for passive reconnaissance, gathering information about centered programs and networks with out actively probing or taking part with the map.
- Forensic Analysis: Within the match of a security breach, it will support security experts analyze network traffic, establish indicators of compromise (IOCs), and realize the systems and instruments former by attackers.
- Community troubleshooting: it will diagnose network issues by capturing and inspecting traffic. It may well support establish network congestion, packet loss, and misconfigured network gadgets.
- Community security: it will detect and analyze malware, viruses, and network assaults. It’ll also visual display unit network traffic for suspicious activity and establish security vulnerabilities.
- Application evaluation: Wireshark can analyze the behavior of applications that declare network protocols. This may well support establish efficiency issues and bugs within the utility.
- Protocol building: it will even be former to non-public and check unique network protocols. It’ll clutch and decode network traffic to support builders realize how protocols are former within the trusty world.
- Diagnosing bandwidth issues – it will support you build if there are any bandwidth hogs on your network by showing you a graphical peep of network traffic.
How Wireshark Improves Community Security
Wireshark is an commence-supply packet analyzer that network experts broadly declare for troubleshooting, evaluation, and network security.
It may well support give a clutch to network security by capturing and inspecting network traffic in different systems.
1. Figuring out Irregular Community Visitors
Wireshark can establish outlandish patterns or spikes in traffic that may well repeat malicious activity by continuously monitoring network traffic.
As an illustration, a sudden diagram bigger in traffic to a selected IP address may well repeat a distributed denial-of-carrier (DDoS) assault. Community administrators can rob acceptable measures to mitigate doable threats by figuring out these anomalies.
2. Detecting Intrusions and Vulnerabilities
Wireshark can detect intrusions and vulnerabilities within the network by inspecting packet information.
As an illustration, making an try for particular packet signatures associated with these exploits can support in figuring out attempts to declare identified vulnerabilities, comparable to Heartbleed or EternalBlue.
Community administrators can rob acceptable action to patch vulnerabilities and procure the network by detecting and inspecting these intrusions.
3. Inspecting Malware and Developed Power Threats (APTs)
Security analysts can declare Wireshark to dissect and analyze the conversation patterns of malware and APTs to heed these threats’ behavior larger and fetch efficient countermeasures.
Analysts can procure indicators of compromise (IOCs) and orderly up contaminated programs by having a seek for on the network traffic produced by malware.
4. Verifying Security Insurance policies and Controls
The tool can support network administrators check that security insurance policies and controls are accurately utilized and functioning as meant.
As an instance, it will even be former to visual display unit the effectiveness of firewalls, intrusion detection programs (IDS), and intrusion prevention programs (IPS) by inspecting packet information to substantiate that these security measures are blocking off or alerting malicious traffic as anticipated.
5. Troubleshooting Community Security Considerations
Wireshark can diagnose and troubleshoot network security issues, comparable to misconfigurations or efficiency issues linked to security instruments like VPNs or encryption.
By capturing and inspecting network traffic, administrators can pinpoint the root reason within the relief of the arena and implement the mandatory fixes to present a clutch to network security.
How to Download & Install Wireshark
Wireshark is supplied for Windows, Mac, and Linux and shall be easily installed via a repeat line or straight launching the utility.
1. Wireshark For Windows
- installer for Windows – Click on Wireshark for Windows
- Double-click the installer and be conscious the installation wizard.
- It may well ask to set up WinPcap, a packet clutch structure wants at some level of installation. Salvage the installation of WinPcap.
- As soon as installed, it will even be launched from the Birth menu.
2. Wireshark For Mac
- installer for Mac- Click on Wireshark for Mac
- Double-click the Wireshark disk image to mount it.
- Go the Wireshark app from the disk image to your Applications folder.
- Follow the installation assignment, comparable to agreeing to terms and licenses.
- You can well maybe now delivery it from your Applications folder or Launchpad.
Issue you’re operating Wireshark on macOS and beget upgraded to macOS 13 from an earlier model. If so, you can seemingly wish to commence and urge the “Uninstall ChmodBPF” equipment after which “Install ChmodBPF” to reset the ChmodBPF Birth Daemon.
3. Wireshark For Linux
- On Linux, it is miles supplied via the equipment manager. It’ll even be installed with:
- Ubuntu/Debian: sudo honest set up wireshark
- RHEL/CentOS: sudo yum set up wireshark
The above will set up it and all required dependencies.
- Wireshark can then be launched from the intention utility menu or urge the repeat “wireshark” in a terminal.
On some Linux distributions, it is miles in all chance mandatory to urge the tool with sudo or add the person to the it group to clutch packets.
That’s it! the tool is now installed, and inspecting network traffic shall be started.
Conclusion
For network security experts, Wireshark is a the truth is crucial tool because it affords in-depth perception into network traffic and assists in figuring out doable threats and vulnerabilities.
As a consequence, organizations can present a clutch to their network security posture and bigger defend their programs and records from cyberattacks by the declare of Wireshark’s capabilities.
it assists in locating security flaws like policy violations, brute power assaults, and DoS assaults in networks.
As successfully as, Wireshark affords network experts fetch admission to to the raw information flowing via their networks by inspecting individual packets.
Total, Wireshark is a really basic tool for network administrators and security experts to diagnose issues, fetch visibility, and affords a clutch to the protection posture of their network.
Learn Grasp in Wireshark Community Analysis – Wireshark Community Analysis Course Bundle
Also Learn:
- Crimson Team of workers vs Blue Team of workers Operations: How Does it Work?
- What is a Dictionary Assault? How Does the Assault Work?
- What is SYN Assault? How Does the Assault work?
- What is OAuth 2.0 ? How does it Works?
- What are Digital Certificates?
- What is Kerberos Authentication?
- What is Spoofing? How does It Works ?
- What is Magecart Assault?
- What is an Disagreeable Twin Assault?
- What is Crimson Teaming?
- What is IPsec? | How IPsec work?
- What is DLP?
Source credit : cybersecuritynews.com


