Next-Generation Malware Analysis With Sandboxing – Threat Analysis Guide in 2024
With the growing complexity and class of malware, inclined signature-primarily based completely detection applied sciences are insufficient. Subsequent-abilities malware diagnosis is a important cybersecurity step forward.
Subtle malware can employ polymorphic and metamorphic code, which modifies with every replication, making signature detection a not easy process. These malware traces can remain undetected by running in memory without writing to disk or simulating traditional network utter.
New methods for examining malware dangle behavioral diagnosis as another of code fingerprints. Machine finding out can adapt to recent dangers. Being in a lab is a fetch system to behold malware behavior and obtain and analyze instrument dynamically. This presents malware analysts an advantage.
Subsequent-abilities malware diagnosis with sandboxing identifies evolved malware methods, targets, and effects, making improvements to defenses and shaping cybersecurity coverage. As malware evolves, diagnosis methodologies and instruments must invent to be resilient to those ever-changing cybersecurity considerations.
Are you a Safety Analyst? Strive ANY.RUN Interactive Malware Sandbox for Free
More than 300,000 analysts utter ANY.RUN is a malware diagnosis sandbox worldwide. Join the neighborhood to behavior in-depth investigations into the head threats and salvage detailed experiences on their behavior..
Characteristic of Machine Studying in Malware Detection
ML programs can detect malware by examining files patterns without specific programming. They title out-of-the-fashioned occurrences and alert users.
Varied Kinds of Machine Studying for Figuring out Malware.
- The supervised finding out process involves teaching algorithms that distinguish aspects of malicious and benign instrument the utter of a labeled dataset.
- Unsupervised finding out algorithms can detect recent or unknown forms of malware by figuring out patterns and anomalies in files without outdated classification.
- Optimal decision-making is carried out thru reinforcement finding out, which adapts detection methods in precise-time primarily based completely on the effects of prior actions.
Machine Studying in Malware Detection: Examples
Used antivirus instrument continuously makes utter of supervised finding out to compare file signatures with a database of known malware signatures, an example of machine finding out in malware detection.
Behavioral Prognosis: Cylance and identical programs employ machine finding out to perceive program behavior and detect harmful actions, equivalent to the unlawful encryption of files that is characteristic of ransomware.
Zero-Day Threats the utter of Deep Studying: A fetch of machine finding out known as deep finding out objects can sift thru huge datasets searching for malware patterns which possess never been considered before, allowing them to uncover zero-day threats. Example: Any.Lunge, an interactive Sandbox for unknown malware diagnosis.
Analyzing Community Traffic: Any Lunge and identical instruments employ unsupervised finding out to assign tabs on network traffic, determining what’s conventional and what may well presumably per chance furthermore utter a breach.
Sandboxing in Malware Prognosis
An wanted cybersecurity technique in malware diagnosis is sandboxing. It involves running suspected files or code in a controlled, remoted environment to peek their behavior without compromising the major blueprint or network’s integrity.Â
Analysts may well presumably per chance furthermore utter this plot in a fetch environment to compare malware’s behaviors, equivalent to its propagation, verbal substitute methods, and blueprint alterations. Analyzing sandboxing in malware diagnosis in depth is introduced right here:
How Sandboxing Works
Sandboxing is a extremely efficient security attain that limits the scope of an application’s environment. By doing so, it helps to administration the appliance’s fetch proper of entry to to sources and the system it interacts with other programs.Â
Sandboxing primarily targets to isolate applications to mitigate the hazards of blueprint screw ups and the unfold of malware. In reveal, sandboxing creates a controlled environment for applications to journey in, which helps forestall unauthorized fetch proper of entry to to critical blueprint sources and serve the blueprint’s total security.
- Isolation: Valid and separate from the remainder of the blueprint, the sandbox is designed to simulate the system pause users’ operating programs work. Malware is journey on this sandbox to discontinuance it from harming the precise blueprint or network.
- Execution and Monitoring: The blueprint retains observe of the malware’s actions, equivalent to modifications to files and registry entries, network traffic, and attempts to utter security holes once it has been operated in the sandbox.
- Examination: The execution logs are examined to study in regards to the malware’s traits, payload, most likely effects, and propagation mechanism.
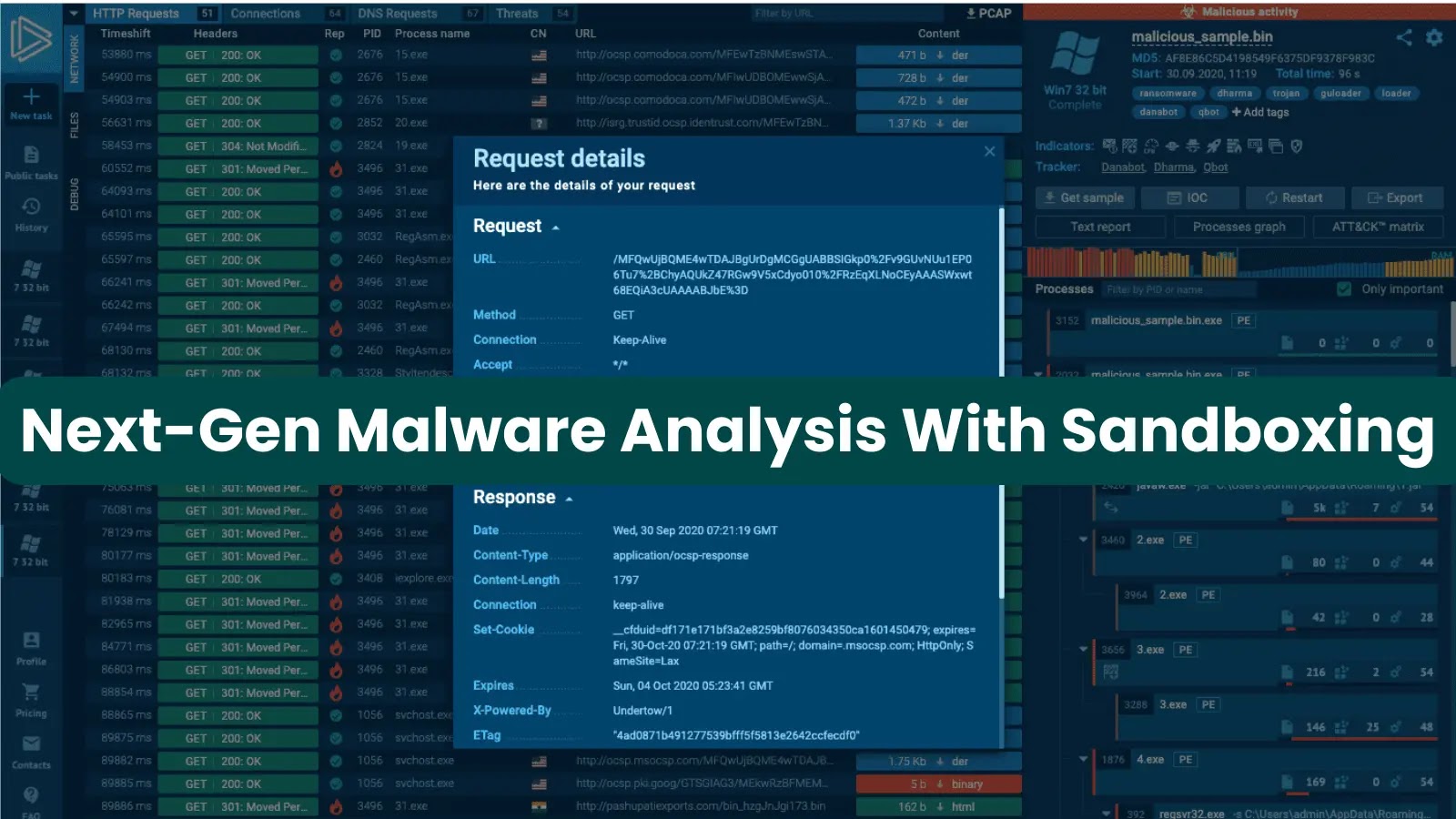
ANY.RUN, An Interactive Malware Prognosis Sandbox
ANY.RUN is a popular interactive sandboxing provider extinct by Over 300,000 users in malware diagnosis to detect and analyze malicious files., and it’s widely idea to be as one of the most particular instruments on this location because of its particular person-pleasant interface and extremely efficient aspects of the next:
- Interactive Prognosis
- Innovative cloud-primarily based completely sandbox with fat interactive fetch proper of entry to
- Computerized interactivity (ML)
- Visible Illustration
- Integration & Customization
- Integration Capabilities
- Track behavior and actions in precise-time
You may study more about how to make utter of ANY.RUN right here.
Interactive Prognosis
ANY.RUN is a to hand sandbox instrument that detects, screens, and researches cyber threats in precise time. The procure interactive sandbox is a gargantuan instrument to pork up the rate of your diagnosis. Our workflow is designed to be particular person-pleasant, with an interface that is easy to navigate. We present detailed experiences to come up with the total files you will want.
With Any.Lunge, analysts possess the irregular potential to actively engage with malware in location of lawful receiving static experiences fancy in inclined sandboxes. With this functionality, that you would be capable to alter the sequence of actions and peep various outcomes reckoning on various eventualities.
You would be a part of Any.RUN With 300,000 users and study the system to compare malware right here.
Innovative cloud-primarily based completely sandbox with fat interactive fetch proper of entry to
Working a questionable file on a test machine will not guarantee security. It is miles a necessity to encompass a human analyst straight when examining malware or vulnerabilities (equivalent to APT).
As a replacement of reckoning on an absolutely automated sandbox, that that you would be capable to presumably furthermore utter a suite of online malware diagnosis instruments to undercover agent the study process and fetch modifications as required, lawful fancy that that you would be capable to presumably per chance on an genuine blueprint.
Computerized interactivity (ML)
Within the heart of the efficiency of initiatives, ANY.RUN may well presumably per chance furthermore now intelligently imitate human actions. Believe a fancy auto-clickerâthe latest addition utilizes machine finding out to title and prioritize buttons primarily based completely on their significance, continuously selecting selections that attain the mission. This encompasses ending setup kinds or overcoming captchas.Â
Visible Illustration
A visual depiction of process execution is accessible with ANY.RUN, simplifying the belief of not easy behaviors. Malicious programs and network connections would be without reveal detected the utter of this visible potential.
Integration & Customization
ANY.RUN seamlessly integrates with a form of cybersecurity instruments and platforms, making it a treasured asset in a legitimate security setup.
The legitimate and project versions present a form of customization alternate choices, including inner most environments, expanded configuration selections, and evolved analytical aspects.
Track behavior and actions in precise-time
ANY.RUN presents a comprehensive demand of testing, including creating recent processes, figuring out potentially suspicious or malicious files or URLs, monitoring registry utter, monitoring network requests, and more in precise time. This permits rapid conclusions to be drawn all the plan thru process execution, laying aside the wish to stay conscious for the closing document.
You may study about 8 ANY.RUN Parts you will want to clutch about.Â
ChatGPT-powered Malware Prognosis
ANY.RUN recently launched an evolved AI-powered malware diagnosis with the serve of ChatGPT, ANY.RUN’s newest addition presents another potential to assess the protection of files. This feature targets to pork up effectivity, streamline resource allocation, and enable you be conscious of critical aspects of your initiatives.Â
Expanded Recordsdata will serve as the major portion. A ChatGPT malware diagnosis reveal is included in every work, and its purpose is to make a selection if the sample is malevolent, suspicious, or pleasant.
This section is required to invent a comprehensive explanation of how the pause outcome was arrived at, what aspects of the code are hazardous, and the plan indicators were utilized to guarantee the final observe most likely diploma of readability.
An in-depth examination of the process, connection, and rule powered by man made intelligence potential that you can point of interest on specific aspects of the duty and the broader image. When that that you would be capable to presumably furthermore possess indicated the processes, principles, or other plot you are drawn to, a in point of fact just appropriate document will most likely be generated centered on these specific things.
You may study a brand recent AI-driven detection potential from ANY.RUN. Powered by OpenAIâs ChatGPT.
Sandboxing in Threat Intelligence
Figuring out the significance of sandboxing in risk intelligence, it becomes obvious that this plot performs a extremely important role in proactively figuring out, examining, and mitigating doable security threats. In the case of risk intelligence, sandboxing performs several important roles:
Malware Prognosis: Sandboxing presents a fetch environment to assign out and analyze malware. Utilizing an remoted environment, analysts can sparsely peek suspicious files or code, allowing them to scrupulously undercover agent their behavior, fetch insights into their mechanisms, and detect indicators of compromise (IOCs) without jeopardizing the protection of their programs.
Behavioral Prognosis: Not like static diagnosis, which appears to be on the code without running it, sandboxing is centered spherical finding out behavioral patterns.
This attain is treasured for gaining insight into the behavior of malware when it’s some distance carried out, including actions fancy network verbal substitute, file manipulation, and registry modifications. This belief is required for creating efficient countermeasures.
Computerized Threat Detection: Different slicing-edge sandboxing solutions can analyze and classify threats robotically. This automation is required for successfully managing the a immense series of doable threats that may well presumably per chance furthermore arise, in particular in immense or intricate environments.
Recordsdata derived from sandbox diagnosis, equivalent to IOCs, may well presumably per chance furthermore furthermore be shared with risk intelligence feeds. Organizations utter these feeds globally to pork up safety features and safeguard against identified threats.
Threat Intelligence: Figuring out zero-day threats is required in the enviornment of cybersecurity. Sandboxing is a extremely efficient instrument, equivalent to ANY.RUN aids in detecting these recent and previously unknown vulnerabilities or malware. Sandboxing instruments can detect and title malicious actions from queer sources by examining behavior in location of relying on established signatures.
Integration with Safety Systems: Sandboxing instruments continuously work alongside a form of security programs, equivalent to SIEM (Safety Recordsdata and Match Administration), firewalls, and endpoint protection platforms. This integration permits a more synchronized and forward-pondering security attain.
Bettering Incident Response: Treasured insights may well presumably per chance furthermore furthermore be received from sandboxing to pork up incident response actions greatly. Gaining a comprehensive belief of risk behavior allows for sooner and more environment pleasant implementation of containment and remediation methods.
Enhancing risk coverage: Feeds can provide treasured insights proper into a broader spectrum of doable dangers, encompassing industry-specific threats, emerging dangers, and targeted attacks on organizations of comparable scale.
Expediting mitigation: Feeds present treasured context for indicators produced by security programs, enabling security teams to distinguish between false positives and proper threats quickly.
Enhancing strategic decision-making: Feeds present treasured insights into security selections, including the identification of threats, the evaluation of security controls, and the evaluation of cyberattack impacts.
Now that you would be capable to amplify your SIEM and other security programs by integrating IOCs straight from ANY.RUN sandboxâs public initiatives. At the present, our Threat Intelligence Feed delivers:Â
- Malicious IPs
- Malicious URLs
- Malicious domainsÂ
Strive ANY.RUN free of payment
More than 300,000 analysts utter ANY.RUN, a malware diagnosis sandbox worldwide. Join the neighborhood to behavior in-depth investigations into the head threats and salvage detailed experiences on their behavior.
Strive all aspects of ANY.RUN at zero value for 14 days with a free trial.
Source credit : cybersecuritynews.com