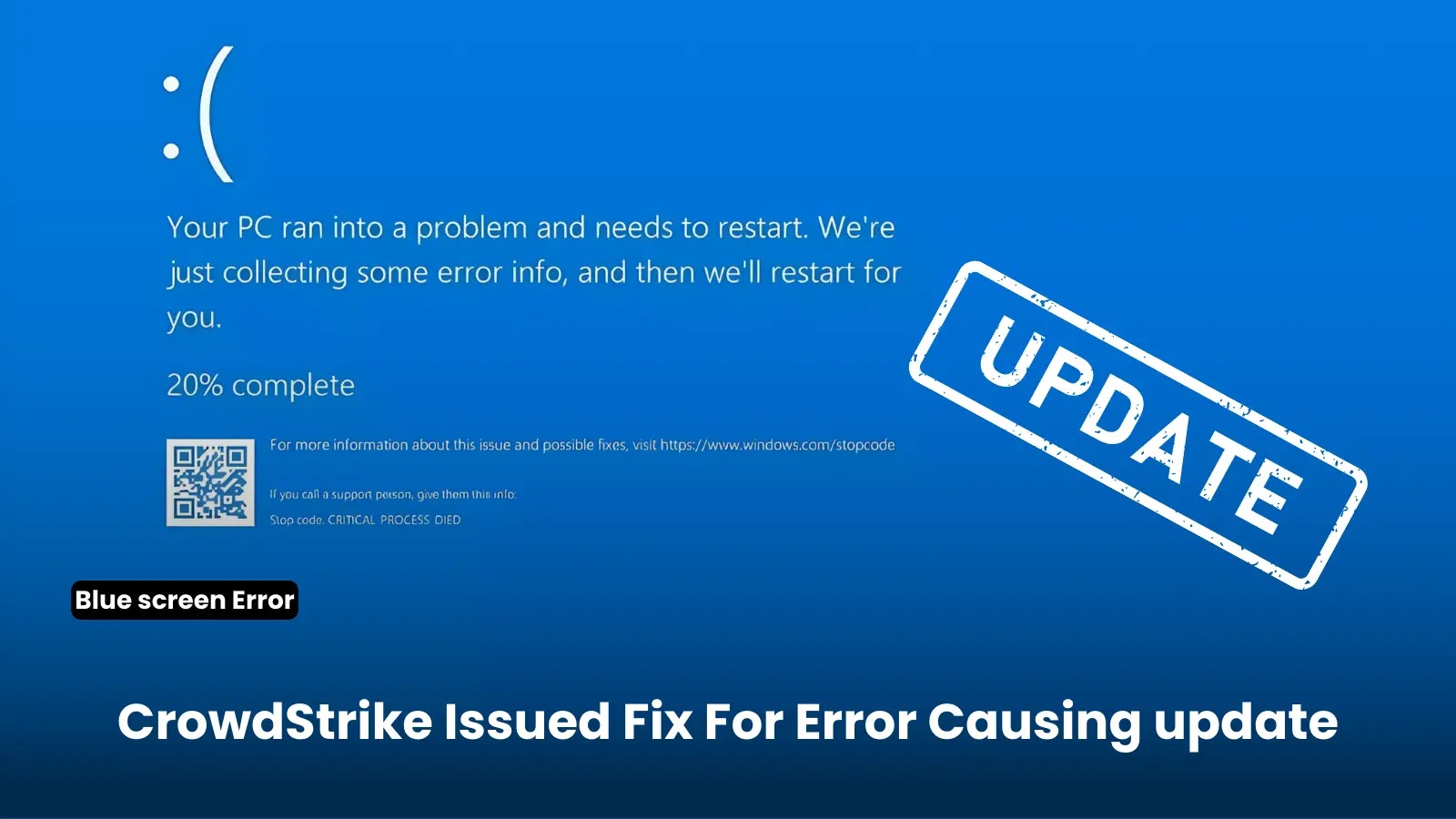
CrowdStrike Releases Fix for Updates Causing Windows to Enter BSOD Loop
CrowdStrike Releases Repair for Updates Inflicting Dwelling windows to Enter BSOD Loop
CrowdStrike has issued a repair for a problematic update that precipitated a huge collection of Dwelling windows programs to journey the Blue Display of Demise (BSOD), rendering them inoperable.
This scenario, which didn’t affect Mac or Linux hosts, changed into once now no longer a results of a security incident or cyberattack nevertheless stemmed from a defect in a single mumble update for Dwelling windows hosts.
Fixes Launched for CrowdStrike Update Error
The enviornment changed into once traced to the Falcon Sensor update, namely the channel file “C-00000291*.sys,” with a timestamp of 0409 UTC, which precipitated programs to shatter with a BSOD error.
CrowdStrike’s engineering group instant known and remoted the scenario, reverting the changes and deploying a repair. The updated channel file, now with “C-00000291*.sys” with the timestamp of 0527 UTC or later, must discontinue extra occurrences of the error.
Programs that cling now no longer been impacted attain now no longer require any motion, and folk introduced on-line after 0527 UTC will additionally now no longer be affected.
Affect and Mitigation Steps
The terrible update greatly impacted diverse sectors, collectively with banks, airlines, supermarkets, and television broadcasters, causing frequent disruption.
IT directors had been recommended to manually boot affected programs into Safe Mode or the Dwelling windows Recovery Atmosphere to delete the problematic driver file. This workaround, while efficient, frequently required physical access to the machines and would possibly perhaps well merely be sophisticated by disk encryption tools admire BitLocker.
For Person hosts, CrowdStrike equipped the following steps:
- Boot Dwelling windows into Safe Mode or the Dwelling windows Recovery Atmosphere.
- Navigate to the C:Dwelling windowsSystem32driversCrowdStrike itemizing.
- Hit upon and delete the file matching “C-00000291*.sys”.
- Boot the host in general.
Workaround for Public Cloud Environments
Option 1:
- âââââââDetach the working plot disk volume from the impacted digital server
- Form a snapshot or backup of the disk volume earlier than continuing extra as a precaution in opposition to unintended changes
- Join/mount the amount to to a unusual digital server
- Navigate to the %WINDIR%System32driversCrowdStrike itemizing
- Hit upon the file matching âC-00000291*.sysâ, and delete it.
- Detach the amount from the unusual digital server
- Reattach the fastened volume to the impacted digital server
Option 2:
- âââââââRoll aid to a snapshot earlier than 0409 UTC.
CrowdStrike has additionally equipped solutions for addressing AWS, Azure, and Bitlocker restoration concerns.
The incident underscores the risks associated with automatic updates for security utility and highlights the want for rigorous testing and staged rollout insurance policies.
Source credit : cybersecuritynews.com