Critical OAuth Framework Flaw Let Attackers Hijack Accounts & Steal Sensitive Data
OAuth is the stylish authentication mechanism most applications exhaust to ease off the signing by increasing a unhealthy-permit utility access delegation.
Nonetheless, most modern discoveries from Salt security direct a security flaw in the Expo framework, which is outdated in increasing excessive-quality native apps for platforms like iOS, Android, and internet platforms.
Serious OAuth Framework Flaw
CVE-2023-28131 – OAuth Flaw in Expo Platform impacts hundreds of Third-Celebration internet sites, apps
An attacker can exploit this vulnerability in the expo[.]io framework by sending a malicious hyperlink to a victim.
When the victim clicks on the hyperlink, the attacker can rob over the victim’s accounts and rob credentials on the utility or web page, which uses the “Expo AuthSession Redirect” Proxy for OAuth scurry.
Technical Diagnosis
The OAuth mechanism has two diversified flows implicit grant and explicit grant scurry.
- Implicit grant
- Explicit grant
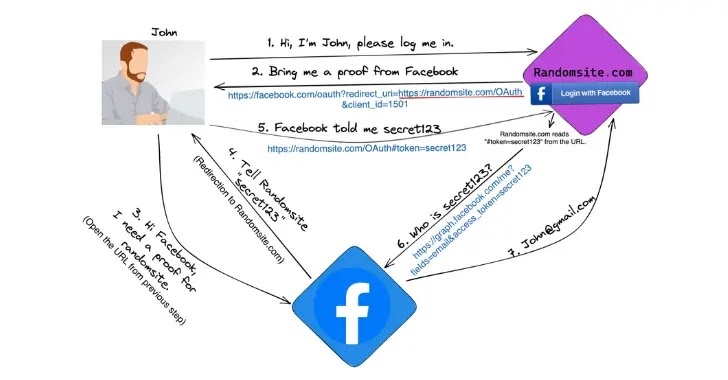
Within the implicit grant scurry, the utility that uses the OAuth model-in will depend on a token ID parameter from any of the OAuth suppliers like Fb, Google, and so forth.,
This token ID parameter is got when the actual person permits the online internet site to access his Fb or Google particular person profile.
When the actual person permits, a secret secret’s generated and despatched to the utility by utilizing URL.
The utility uses This secret key to retrieve particular person files from Fb or Google. The implicit grant form is outdated in single-page and native desktop applications.
The Expo Framework
The Expo framework is outdated in firms like flexport, Codecademy, Petal, Cameo, Insider, and so forth., with bigger than 650K developers worldwide.
Researchers at Salt security appreciate recreated the utility to attain the OAuth scurry in the Expo framework fully.
It became as soon as printed that the Expo framework had a scurry where the ReturnUrl parameter became as soon as inclined to exploitation by a threat actor.
Attack Methodology
The threat actor sends two links to the actual person.
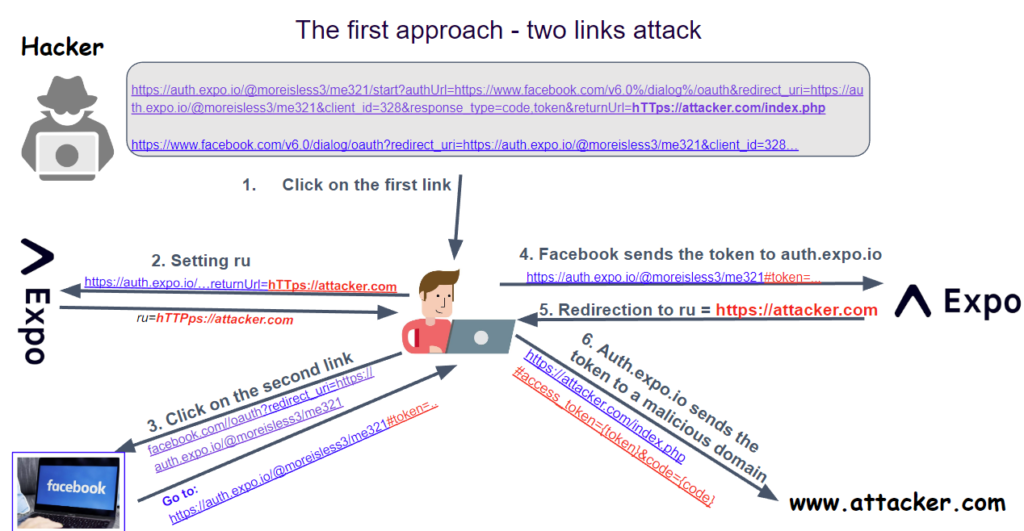
When the actual person clicks on the first hyperlink, the Expo framework sets the ReturnUrl to default the attacker’s worth, relate, [hTTps[:]//attacker.com]
After the actual person clicks on the 2d hyperlink, Fb redirects the actual person to the Expo.io web page and sends a token to the ReturnUrl.
Nonetheless, since a particular person will no longer click on two links concurrently at some point of a social engineering assault, a Javascript exploit is outdated, which reduces the time for the actual person to ogle the affirmation page from Fb.
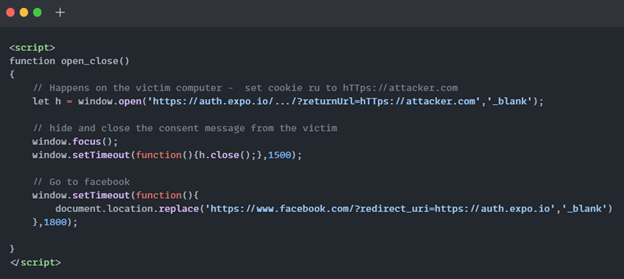
Salt Security publishes a full detailed diagnosis of the assault.
This ends in an myth takeover and credential stealing vulnerability in the Expo.io Framework.
Expo has suggested all of its customers update to the most fresh security patch released by them.
Source credit : cybersecuritynews.com


