Microsoft New Security Audit Tool Unprotected Devices Exposed To Internet Attacks

Microsoft’s novel security instrument for auditing exterior assault surfaces gives security teams the capability to behold unknown and unmanaged resources which will doubtless be visible and accessible from the web, most often the identical peep an attacker has when selecting a target.
‘The novel Defender External Attack Surface Administration’ facilitates customers to fetch out unmanaged resources that will doubtless be potential entry aspects for an attacker.
Microsoft Defender External Attack Surface Administration
Most truly, Microsoft Defender External Attack Surface Administration examines the web and its connections day-after-day. This helps to fetch out the web-facing resources, even the agentless or credentials, and unmanaged belongings.
“With a total peep of the group, customers can take suggested steps to mitigate threat by bringing these unknown resources, endpoints, and belongings beneath stable management within their security information and match management (SIEM) and prolonged detection and response (XDR) instruments”, Vasu Jakkal Microsoft Corporate Vice President.

This novel product helps to take care of up a dynamic inventory of exterior resources across extra than one clouds and hybrid environments. It determines the uncovered weak point by prioritizing them and misconfigurations hidden in unmanaged resources then bringing the resources beneath management to take away those exposures.
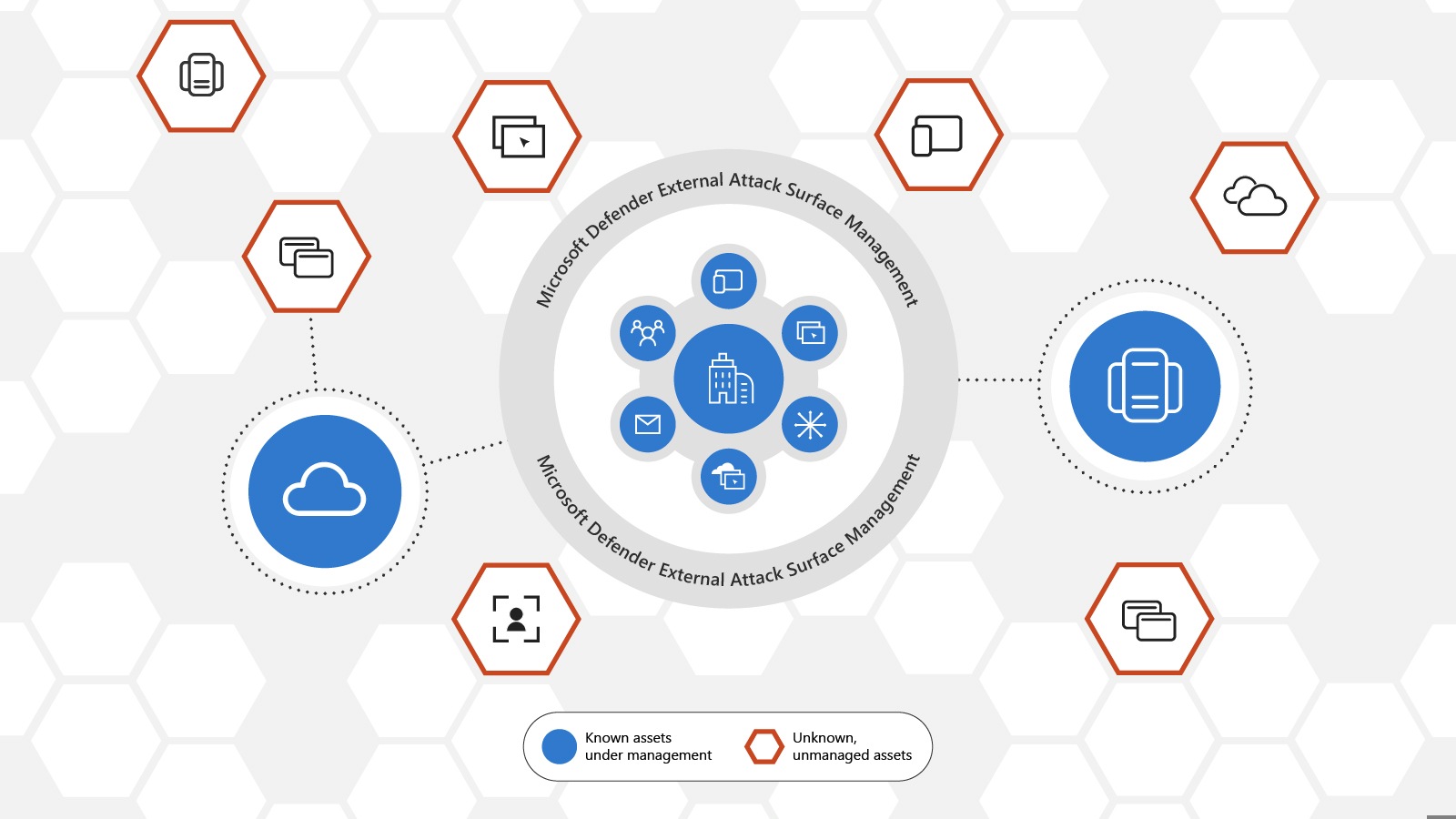
Microsoft point out to mix security information and match management (SIEM) and prolonged detection and response (XDR) to lengthen effectivity and effectiveness whereas securing your digital property.
Microsoft moreover releases Microsoft Defender Threat Intelligence, another security product that will present security operations (SecOps) teams with the threat intelligence wished to fetch out attacker infrastructure and traipse up assault investigations and remediation efforts.“The volume, scale, and depth of intelligence are designed to empower security operations centers (SOCs) to indulge in the say threats their group faces and to harden their security posture accordingly”, saysVasu Jakkal.
You would apply us on Linkedin, Twitter, Fb for day-to-day Cybersecurity updates.
Source credit : cybersecuritynews.com


