Endpoint Management And Security : Key To Handling And Securing Future IT Operations
Endpoint Administration And Security : Key To Handling And Securing Future IT Operations
Endpoint administration and security is no longer one among the prime areas of debate relating to IT security, and this doesn’t arrive as a shock.
For the simpler piece of the final decade, most endeavor endpoints have faith been safely barricaded interior the endeavor network that, in flip, became as soon as secured with firewalls, routers, and proxy servers.
When the global labor drive began working from home, endpoint administration and security began to topic.
We witnessed IT admins grappling with securing and updating endeavor endpoints to transition to work environment.
Organizations of all sizes rapidly particular they significant to shift from how IT administration and security have faith been previously perceived.
They realized that security would possibly perchance maybe easy ideally be enforced from primarily the most minor units of their networksâthe endpoints.
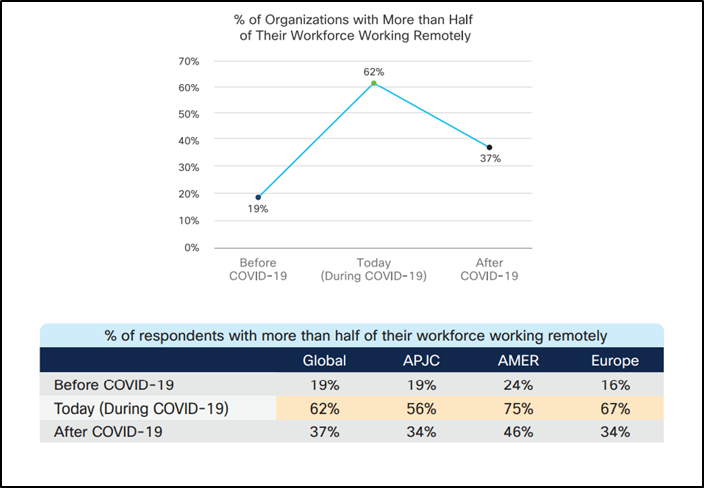
Owing to the work culture adopted at some level of the COVID-19 pandemic, organizations have faith started following a hybrid working model in many parts of the sector.
The labor drive moreover appears to evaluate the identical sentiments as revealed within the USA This day-Harris Pollwitness that stumbled on that 40% of People most well-hottest to work from home fleshy-time, in comparison with 35% who sought a home-scheme of enterprise hybrid.
These numbers characterize a pattern and preference for flexible and hybrid work environments.
Having turn out to be tickled with the rhythm of distant work, the labor drive now expects the identical flexibility and the capacity to work from anyplace, on any machine, at any time, and would possibly perchance maybe in due direction to arrive.
Cisco conducted a global witness at some level of 21 markets in The USA, Europe, Asia Pacific, Japan, and China, surveying over 3,000 IT option-makers from miniature companies to mountainous enterprises.
The witness results in level to identical trends no topic the size of the organization.
Managing devices and implementing cybersecurity in a hybrid work environment comes with its piece of reassessment of existing cybersecurity measures and revamping the protection posture to consist of all user devices.
Inspecting the challenges faced within the transition to distant work and how fleet they’ll also be overcome will make clear aspects to preserve in thoughts whereas designing an unbelievable security machine to effectively cope with a hybrid work environment.
This looks esteem the pattern the sector is marching in opposition to.
Endpoint Administration Solutions Challenges 2023
- Indispensable elevate within the option of cyber threats
- Growing undertaking in onboarding carry your machine (BYOD)/deepest devices.
- Develop in patching complexities
- Irregular work hours
- The steep elevate in serve desk tickets
- Elevated set up of distant collaborative tools
- Specializing in endpoint administration and security for enhancing protection in hybrid work environments
- Coping with insider assaults
- Electronic mail and browser security
- Security training and culture amongst the staff
Indispensable elevate within the option of cyber threats:
With users accessing the organization’s sources remotely or within the cloud, possibility actors fleet exploited the protection gaps triggered by this surprising transition. A cease to-instantaneous result became as soon as the jump in cyber threats and security indicators in most regions worldwide.

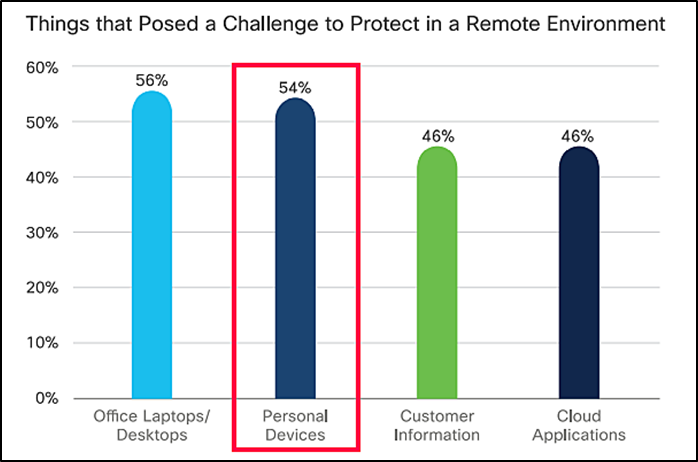
Growing undertaking in onboarding carry your machine (BYOD)/deepest devices:
ManageEngine polled IT and infosec professionals to survey the impact of COVID-19 on IT work.
The outcomes revealed that about 15% of the organizations had an acute scarcity of company laptops prompting them to allow their labor drive to use deepest devices for work.
Cisco moreover confirms this finding by pointing out that 54% of the organizations stumbled on keeping deepest devices the ideal enviornment for their IT security team.
Develop in patching complexities:
With distant work, we seen organizations that hadn’t adopted a cloud-primarily primarily based patch administration machine struggling to be pleased their periodic patching objectives. Most now require devices to connect to VPN for patch scans and deployment.
In step with ManageEngine’s polls, 73% of the organizations polled required users to connect to their company VPN for vulnerability and patch scans, nonetheless since most company VPNs have faith been no longer geared as much as cope with an inflow of devices true away, there have faith been famous bandwidth-connected bottlenecks to patching that resulted in a drop in traditional patching and change deployment.
Irregular work hours:
Throughout the initial days of distant work, the labor pool became as soon as challenged with sticking to a mature 9-5 workday.
This straight impacted the patch schedules as IT admins now needed to allow cease users to skip patch deployment projects to crash disruptions of their productiveness.
ManageEngine’s polls repeat that forty eight% of organizations needed to grant their cease users the flexibleness to assign off patch deployment projects and subsequent reboots.
The steep elevate in serve desk tickets:
With the pandemic, IT admins started receiving moderate 25 serve desk tickets per day, a median of a 43% elevate in tickets since adopting distant work.
IT admins now spend 2.5 hours every workday sorting thru and resolving issues.
Elevated set up of distant collaborative tools:
To retain change continuity and make a seamless work environment, companies worldwide embraced distant collaborative tools, esteem virtual meeting applications, cloud-primarily primarily based file storage and transfer applications, and chat applications.
IT admins, in flip, triggered a 46% elevate in distant troubleshooting applications obtained to make a selection as much as the underside of IT issues effectively.
Specializing in endpoint administration and security for enhancing protection in hybrid work environments
A ways-off work challenges have faith been step by step overcome by adopting countermeasures and the usage of tools that ensured endured protection to company devices no topic the assign they have faith been. Firms started prioritizing cybersecurity measures more, leading to the level of interest shift to endpoint protection.

Selecting the true tools and insurance policies to enable a hybrid work environment:
Because the critical steps to staying afloat, organizations adopted elevated VPN capacity, moved to net-primarily primarily based or cloud alternatives, done multi-component authentication techniques, and commenced specializing in endpoint protection tools.
These changes are slowly becoming lengthy-time frame and they are a proper scheme to birth prepping for hybrid operations.

Responding to zero-day vulnerabilities:
Amongst the patching bottlenecks faced by companies at some level of distant work, we seen many IT admins resort to temporarily blocking off or blacklisting the applications, tool versions, or recordsdata susceptible to the zero-day vulnerabilities on endpoints operating them sooner than patches have faith been available.
This ensures that your machine security techniques to fight zero-day vulnerabilities will also be adopted as a fleshy-time capacity.

Using enviornment name machine (DNS) and network pick up admission to manage (NAC):
Since most assaults target endpoint users, be certain you have faith a DNS as the critical security line. Block suspicious domains that seem malicious.
You would possibly perchance maybe well presumably moreover configure compliance insurance policies under NAC and prohibit or block pick up admission to to net and intranet sources if the machines don’t be conscious your insurance policies.
Boosting productiveness in a hybrid environment:
With no managers around to bodily oversee staff working from home, it is difficult to crash minds from wandering to the gaming consoles and video streaming apps, leading to a decline in productiveness.
That is also solved largely by simply blacklisting social media and gaming applications on the tip-users company devices.
In step with the ManageEngine witness, almost 42% of companies feeble this system to cope with productiveness issues and serve block the unfold of malware thru non-change significant applications.
Coping with insider assaults:
Insider assaults are no longer easy to detect and crash with antivirus protection, patching, or perimeter security.
These assaults can take down an organization from interior, from company recordsdata theft to malware injection.
Organizations can serve crash such assaults by rising a zero-belief environment with privilege administration, in the initiating giving the crew traditional privileges and curbing pick up admission to to soft recordsdata.
Elevated-level pick up admission to will also be extended on an as-significant foundation.
A 0-belief environment in general has machine control insurance policies that detect and crash pick up admission to to recent peripheral devices linked to the network and mark the recordsdata shared to and from company devices.
38% of the organizations, in step with ManageEngine’s witness, adopted a machine control coverage at some level of distant work and are planning to serve it even when they head relief to offices.
Electronic mail and browser security:
With email rating #1 within the checklist of assault vectors, Email security is extremely significant to have faith a security resolution that prevents phishing assaults, ransomware, and change email compromises.
It is moreover significant to crash the tip user from accessing malicious net sites, and downloading add-ons and extensions that would possibly perchance maybe also reason harm to the network.
In accordance with this, 70% of organizations have faith adopted endpoint-level browser security controls to prohibit pick up admission to to malicious net pages with out proxy servers or DNS filtering.
Security training and culture amongst the staff:
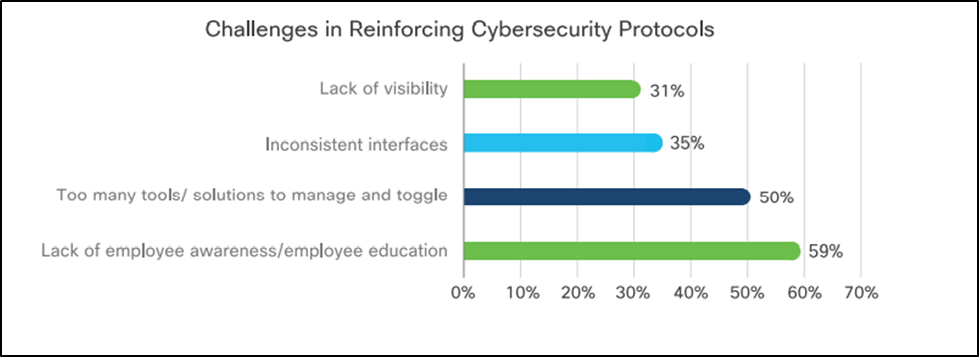
A network is unbiased as solid as its least educated and conscious user.
When asked what machine directors stumbled on a enviornment when implementing cybersecurity protocols, lack of user awareness and training got primarily the most votes within the Cisco witness.
Organizations must have faith traditional security and privateness evaluation classes and checks to change their crew on the protection norms they be conscious or would love to have faith a study.
Endpoint administration and security: Two sides of the identical coin
We have faith now lined intimately the challenges that organizations faced whereas transferring to distant work, and how they excited by and prioritized particular aspects of security to make a selection up over these challenges and pick up sustainable programs that would possibly perchance maybe also cope with future hybrid work necessities.
We didn’t quilt the option of alternatives to put an supreme endpoint administration and security environment.
ManageEngine conducted polls at some level of a recent are living seminar, asking attendees what number of alternatives they idea significant to be certain endpoint administration and security of their endeavor environments.
The majority voted for 3 to 5 alternatives with around 20% announcing they feeble separate alternatives for endpoint administration and security actions.
There became as soon as a famous hole between endpoint administration and security alternatives for a truly lengthy time.
This hole weighs carefully on an organization’s IT budget, with many dispensing ridiculous portions of cash on specialised alternatives that offer restricted capabilities.
One more component to preserve in thoughts whereas investing in more than one alternatives is the administration overhead.
IT admins must test if the alternatives are properly matched with every other fastidiously and if their schedules overlap.
As an instance, installing tool and deploying patches concurrently can delight in a quantity of bandwidth.
The scheduling and compatibility evaluate project is extremely time-ingesting and would possibly perchance maybe well require the organization’s IT setup to be modified to accommodate many applications. That is also every a dear and behind project.
Any proper resolution will win your work less difficult, no longer more clunky and unwieldy.
IT distributors realize machine admins’ frustrations to make a different a proper possibility for their network, and are in point of fact practising integrating endpoint administration and security needs into a single resolution.
Beneath are one of the necessary necessary necessities that a proper endpoint administration and security resolution must meet:
- Easy and unified console: The IT admin would possibly perchance maybe easy be in a scheme to govern and stable more than one devices from a single console.
- Automates work: It is going to also easy allow you to automate your IT operations from deploying tool and updates, asset administration, and OS deployment to troubleshoot your devices.
- Arena up heterogeneous roaming devices and devices on LAN, WAN, and closed networks: One resolution would possibly perchance maybe easy be in a scheme to govern devices of a quantity of flavors unfold at some level of a quantity of mediums.
- Entire vulnerability scanning and remediation: It is going to also easy scan your networks incessantly for vulnerabilities and deploy patches to repair these vulnerabilities if detected.
- Remediate machine misconfigurations: It is going to also easy name machine misconfigurations, equivalent to default settings and terrible passwords, and remediate them.
- Automates OS and third-celebration patch administration: It is going to also easy win your patching routine seamless and grief-free.
- Achieve in drive machine control: It is going to also easy crash unauthorized peripheral devices from connecting to the network.
- Keep utility control and least privilege coverage: The resolution would possibly perchance maybe easy be in a scheme to blacklist/whitelist applications in step with endeavor necessities and assign into designate privilege administration on an utility level.
- Make certain that browser security: It is going to also easy be in a scheme to filter malicious net sites and crash noxious add-ons and extensions from being downloaded.
- BitLocker administration and drive encryption: The resolution would possibly perchance maybe easy crash recordsdata loss in case of theft, and BitLocker encryption needs to be enabled in all endpoints along with drive encryption.
ManageEngine Endpoint Central with its Endpoint Security aspects objectives to bridge the outlet between endpoint administration and security.
Endpoint Central packs aspects significant for the total administration of heterogeneous endpoints along with its security by extending vulnerability administration, machine control, utility control, browser security, and BitLocker administration.
To receive a hands-on skills of the product, test out the inclusive operate thru a 30-day free trial.
Source credit : cybersecuritynews.com





