Thousands of Apache Superset Servers Open to RCE Attacks

Cybersecurity analysts at Horizon3 detected that thousands of Apache Superset servers are uncovered to RCE assaults at default configurations.
This would perchance perchance perchance permit the threat actors to do the next illicit actions:-
- Salvage admission to records
- Regulate records
- Harvest credentials
- Make commands
Apache Superset is an delivery-source instrument that is aged for:-
- Records visualization
- Records exploration
At the starting set, this instrument became as soon as developed for Airbnb, nonetheless in 2021, it became a top-level challenge at the Apache Machine Foundation.
Technical Prognosis
Attackers might perchance perchance take revenue of the default Flask Secret Key utilized by Apache Superset for signing authentication session cookies to create unsuitable session cookies.
Consequently, servers that haven’t altered the most main would be inclined to unauthorized derive admission to with elevated privileges.
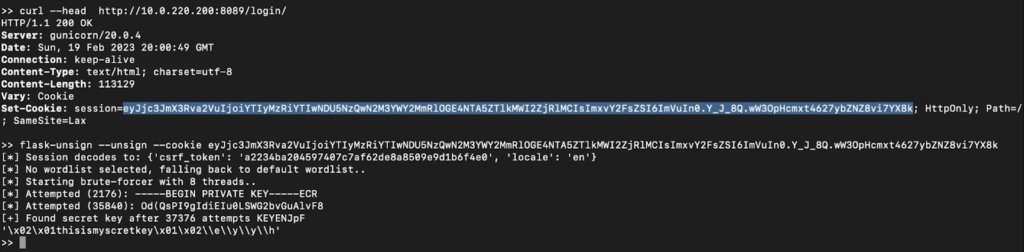
Whereas Horizon3 affirmed that they had identified this susceptible default configuration in 2,000 web-uncovered servers. Some of those uncovered servers belong to plenty of organizations:-
- Universities
- Companies of diversified sizes
- Executive organizations
Superset facilitates the exploration of files and the introduction of visualizations by supporting integrations with plenty of databases.
Attackers can enact arbitrary SQL statements in opposition to linked databases the utilization of the worthy SQL Lab interface.
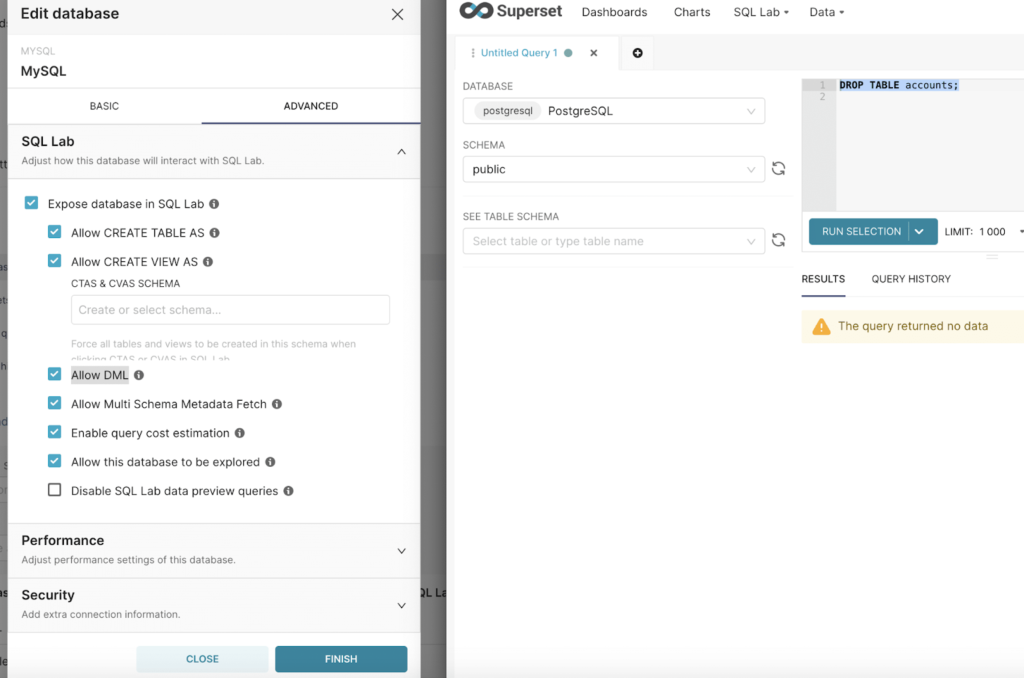
Whereas as a replace of this, directors can steer clear of this attack by altering the default key to an unknown model irregular to the attackers.
Impact
On October 11, 2021, Horizon3 found and reported the flaw to the Apache Security crew.
The builders launched model 1.4.1 of the tool on January 11, 2022, which changed the default ‘SECRET_KEY’ with a brand new string.
As effectively as, a warning became as soon as included in the logs to tag the detection of the default string one day of startup.
Horizon3 found 2 default keys, aged Shodan to search conditions the utilization of them, and found 67% had been misconfigured which totals round 2,124 total.
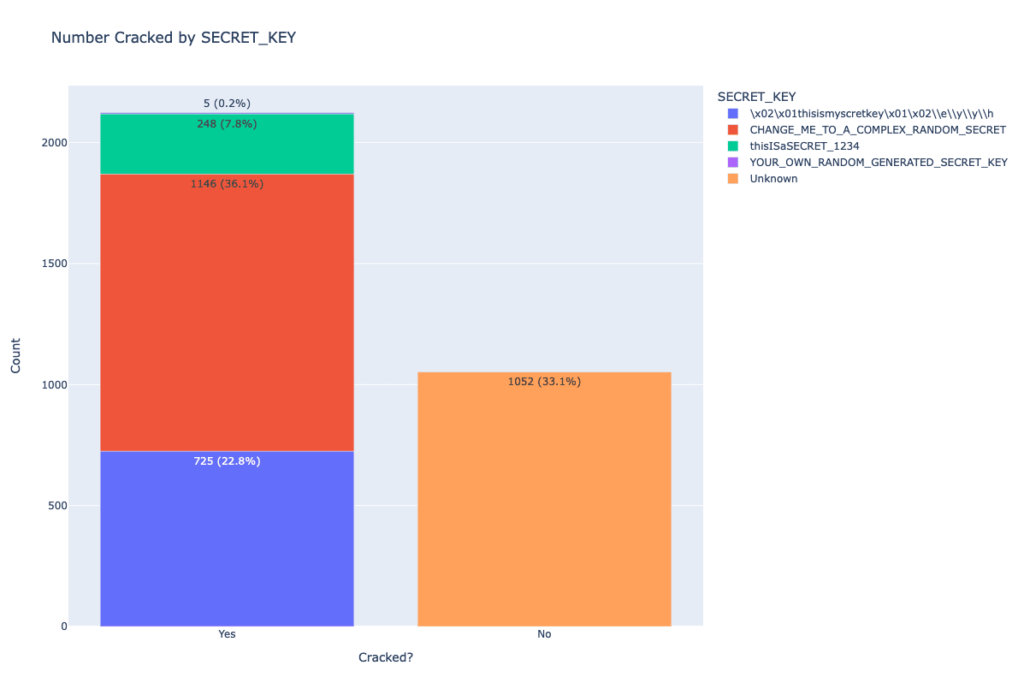
Horizon3 contacted Apache again and warned organizations to alternate their configuration in February 2023.
On April 5, 2023, the Superset crew launched model 2.1 which blocks default ‘SECRET_KEY’ at server startup.
Version 2.1 of Superset prevents new harmful deployments nonetheless doesn’t repair over 2,000 present misconfigurations.
Timeline
Here below, now we like talked about the total timeline:-
- Oct. 11, 2021: Preliminary communication to the Apache Security crew
- Oct. 12, 2021: Superset crew says they are going to learn about into the topic
- Jan. 11, 2022: Superset crew adjustments default SECRET_KEY and provides warning to logs with this Git commit
- Feb. 9, 2023: Email to the Apache Security crew about new records associated to the shrinking default configuration. Started notifying relate organizations.
- Feb. 24, 2023: Superset crew confirms code alternate will most likely be made to handle default SECRET_KEY
- Mar. 1, 2023: Pull ask merged with a code alternate to handle default SECRET_KEY
- Apr. 5, 2023: Superset 2.1 delivery
- Apr. 24, 2023: CVE disclosed
Source credit : cybersecuritynews.com


