ABCs of Information Security – An Employee's Security Awareness Guide – 2023

With ABCs of facts security awareness, we are in a position to diminish the threat of losing non-public knowledge, cash, or recognition from cyberattacks. Here we detail the hazards fervent and prevention.
Knowledge security or InfoSec describes the processes and tools designed and utilized to safeguard confidential firm records against modification, interruption, destruction, and inspection.
Safety awareness working against must abet lift awareness, change habits, and achieve a culture of security in enlighten to diminish threat.
Rising awareness lays the groundwork for behavioral adjustments. A culture of security is fostered by actual behaviors.
The following are the approved key aspects that wants to be included to diminish the threat.
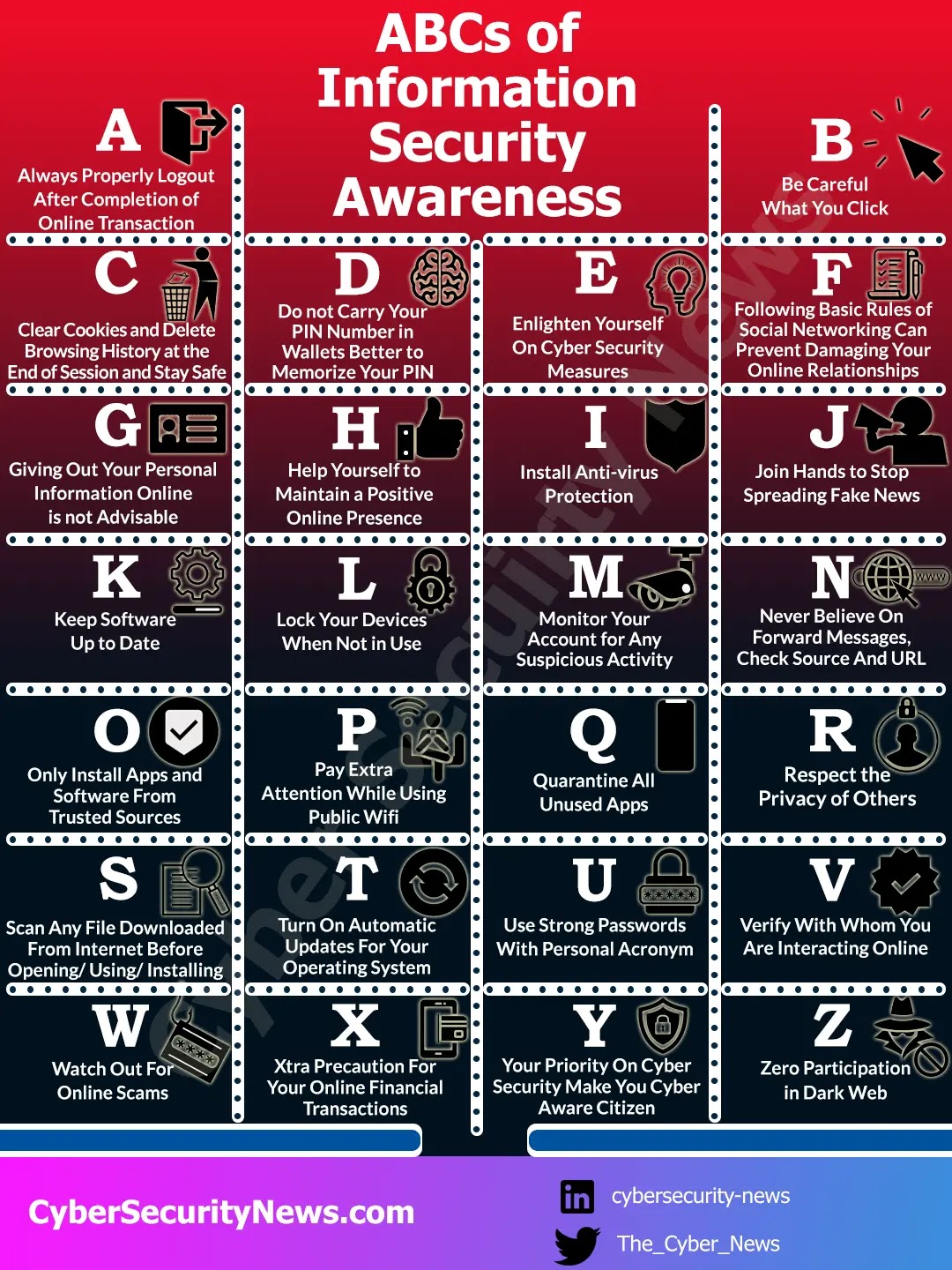
ABCs of Knowledge Safety Awareness
- Constantly Successfully Logout After Completion of Online Transaction
- Be Cautious What You Click on
- Determined Cookies and Delete Making an strive Historical previous on the Halt of the Session and Attach Stable
- Be pleased now not Elevate Your PIN Number in Wallets Greater to Memorize Your PIN
- Narrate Yourself On Cyber Safety Measures
- Following the General Rules of Social Networking Can Prevent Unfavorable Your Online Relationships
- Giving Out Your Personal Knowledge Online is No longer In actual fact helpful
- Attend Yourself to Retain a Sure Online Presence
- Set up Anti-virus Safety
- Join Arms to Halt Spreading Erroneous Knowledge
- Retain Utility As a lot as Date
- Lock Your Gadgets When No longer in Use
- Display screen Your Story for Any Suspicious Job
- Below no circumstances Judge On Forward Messages, Verify Source And URL
- Most piquant Set up Apps and Utility From Depended on Sources
- Pay Additional Attention While The exercise of Public Wifi
- Quarantine All Unused Apps
- Admire the Privateness of Others
- Scan Any File Downloaded From the Web Before Opening/ The exercise of/ Installing
- Flip On Computerized Updates For Your Operating Diagram
- Use Solid Passwords With Personal Acronym
- Verify With Whom You Are Interacting Online
- Explore Out For Online Scams
- Xtra Precaution For Your Online Financial Transactions
- Your Precedence On Cyber Safety Ranking You Cyber Conscious Citizen
- Zero Participation in Gloomy Web
ABCs of Knowledge Safety[[Infographic]
Constantly Successfully Logout After Completion of Online Transaction
Digital funds have evolved as a results of the introduction of abilities.
The nation-wide exercise of rate programs in conjunction with UPI, credit/debit cards, mobile banking, and loads others. have accelerated as a result of the COVID-19 epidemic.
Given the upward thrust in cybersecurity breaches, it’s finest to exercise warning whereas making on-line funds.
In ABCs of Knowledge Safety, The largest thing to be conscious whereas making an on-line rate is that you simply can presumably have to log off after you are completed.
Whether or now not it’s an electronic mail account or another account, you are extra at threat of hacking whereas you don’t properly log off.

If a hacker will get entry to your instrument, now not most productive can they entry your logged-in accounts by your instrument, they’ll hijack/seize your session so they’ll log into your account on other devices with out radiant the password.
Hence, logging out helps prevent other users from having access to the design with out verifying their credentials.
It additionally helps provide protection to the most fresh user’s entry or prevent unauthorized actions on the most fresh login session and is thus a distinguished allotment of security.
Logging out ensures that user entry and user credentials are actual after the login session.
Be Cautious What You Click on
With the ABCs of Knowledge Safety, doubtlessly the most popular system that criminals entry personal knowledge is by tricking other folks into clicking on what appear like harmless links or attachments in emails.
In case, whereas you get any peculiar notifications out of your monetary institution inquiring so that you simply can log into your account.
That you just would possibly presumably maybe also log in by entering the monetary institution’s web location address into the address bar of your browser.

It’s a apt recommendation to repeatedly name your monetary institution to substantiate that a message (electronic mail, SMS) you suspect would possibly maybe presumably maybe be suspicious has certainly come from them.
By clicking the unsuitable link, you are at threat of losing cash, losing personal knowledge, and presumably endangering your loved ones or your business.
In total, there are two forms of URLs:
- A common size, starting with www. Followed by the on-line location name, ending with a .com or another high-stage domain.
- A shortened URL equivalent to bit[.]ly/2qhKcPw
Each URLs can even be perfectly actual to click on, but manufacture sure you function your due diligence before piquant forward.
Subsequently, be very careful before clicking on Web ads, social media posts, and emails. Gaze the URLs.
Cruise your mouse icon over the links. Don’t click on links in emails that you simply didn’t inquire.
Determined Cookies and Delete Making an strive Historical previous on the Halt of the Session and Attach Stable
within the ABCs of Knowledge Safety, C skill Cookies that are “monitoring” files that websites you focus on to set up for your design and are intended to most productive be accessible by the websites that created them.
Cookies are faded by websites to withhold tune of user preferences, login space, and records about plugin exercise. Cookies can even be faded by third parties to procure a model of facts about users all over diversified websites.

Cookies and looking history velocity up sessions in browsers, but they’ll additionally be unsafe. As an illustration, hackers can procedure your individual knowledge within the occasion that they seize cookies.
Thus, it’s seemingly you’ll pause websites and third parties from monitoring your on-line actions whenever you get rid of your cookies and looking history.
You manufacture it exceedingly hard for websites and other entities to stare and video display you by erasing your history.
Be pleased now not Elevate Your PIN Number in Wallets Greater to Memorize Your PIN
PINs are faded for diverse transactions. We require a PIN for monetary transactions like withdrawing cash, swiping the card, and loads others. It’s a long way precious in a replacement of replacement programs to authenticate you.
As an illustration, it’s seemingly you’ll exercise the PIN to pause rate of a cheque, block an account, enlighten a weird chequebook, change your address, change your phone quantity or electronic mail id, and loads others.

It’s needed to withhold the PIN secret in consequence of it affords you (or someone who knows it) entry to confidential records.
Defend it, don’t put it on your pockets, and never write your PIN quantity on an ATM or debit card in consequence of criminals are conscious to survey for four-digit numbers written on the aid of stolen cards.
Essentially the most productive system to soundly abet a PIN is to memorize it. The following are the programs to be conscious your PIN.
- Gather numbers that are meaningful to you
- Use peculiar imagery: uses fascinating or comical visuals that can wait on you be conscious your PIN
- Ranking a mnemonic: As an illustration, 2275 is “two, two, seven, five.” Rob the major letter of every quantity, which is TTSF, and make a sentence, like Two Toads Scent Funky.
- Join numbers to other folks you know
- Ranking a notice or sentence out of your PIN to be conscious.
Narrate Yourself On Cyber Safety Measures
Ransomware assaults were a primary assault vector for both companies and consumers. All companies that exercise networks can even be focused for buyer records, corporate espionage, or buyer assaults.
Corporations would possibly maybe presumably maybe easy exercise diversified ABCs of Knowledge Safety measures to withhold their business records, their cash waft, and their potentialities actual on-line.

Organizations must be certain that their workers individuals are attentive to doable cybersecurity risks and learn the strategy to prevent them.
Every individual wants to became a educated about all cyber security features equivalent to maintaining entry to serious assets, building a sturdy cybersecurity protection and protected network, maintaining entry with efficient identification management, controlling entry to records and programs, placing up a firewall, employing solid passwords, manufacture exercise of security utility, and loads others.
ABCs of Knowledge Safety helps to remark you on cyber security and would possibly maybe presumably maybe easy provide protection to you from viruses, malware, ransomware, records theft or loss as a result of hacking, and so on.
Following the General Rules of Social Networking Can Prevent Unfavorable Your Online Relationships
The foundations of social manners are proper as necessary within the digital world as they are within the correct world—and miserable social networking can stick around to danger you for for loads longer.
As an illustration, strive and exercise respectful language. The exercise of any model of verbal abuse on-line can score you banned out of your social groups. At a minimal, your remarks is mostly removed.

Steer particular of sharing irrelevant photos, posting photos of drug or alcohol usage, or sharing any non-public knowledge on-line.
These photos and quotes are without end within the market for the leisure of the area to note after they are posted on-line.
Be cautious when disclosing any small print that would possibly maybe presumably maybe be faded as responses to security questions for your individual accounts.
It’s a long way perfectly acceptable to unfriend anyone if the connection is beyond repair. Ultimate don’t torture them (or yourself) with on-all yet again-off-all yet again connecting.
Admire the privacy of others. Additional, whereas you aren’t sure of the details slack an on-line retailer or social media publish, seek the advice of with anyone who does know or can rep out.
Thus, using Web etiquette can additionally provide protection to your recognition, which is in point of fact helpful on both personal and knowledgeable ranges.
Giving Out Your Personal Knowledge Online is No longer In actual fact helpful
Don’t repeat your individual knowledge (name, age, address, phone quantity, social security quantity) to strangers.
Below no circumstances invite a stranger to come to fulfill you in individual or name you at your home.
Attach in tips your actions before sending emails or making web posts. Somebody can peek what you publish on-line.
Indubitably one of your finest risks whereas using the web is disclosing personal knowledge to other folks you function in a roundabout procedure know.

Sharing non-public knowledge is unsafe and would possibly maybe presumably maybe easy be refrained from. Examples of such knowledge embody your address, phone quantity, family member’s names, vehicle knowledge, passwords, work history, credit space, social security quantity, initiating date, faculty names, passport knowledge, driver’s license knowledge, insurance protection protection numbers, mortgage numbers, credit/debit card numbers, PIN numbers, and monetary institution account knowledge.
Attach in tips deleting your name from websites that distribute personal records gathered from public facts to all people on-line, collectively alongside with your phone quantity, address, social media avatars, and photos.
Attend Yourself to Retain a Sure Online Presence
Online presence refers to a pair key things: Visibility, Credibility, and Reputation. An on-line presence lets in potentialities to now not most productive rep you but to learn extra about your companies and your previous performance.
Your profiles won’t be as efficient as they are progressively within the occasion that they’re incomplete. Every social network affords a special likelihood to spotlight your persona and achievements, both of that are vital for professionals.
Employ the advantages of every social media network you exercise to make an participating presence there.
That you just would possibly presumably maybe also record out your job responsibilities on social media platforms. A extra efficient reach is to enlighten your capabilities and accomplishments by in conjunction with links to work samples.

LinkedIn makes it easy for professionals to showcase their work by offering the answer to glue work samples to their profiles.
Whether or now not you’re sending an electronic mail to practice for a job, verify in with a client, or dispute hello to a fellow employee, your electronic mail signature most steadily is an impressive tool for promoting your social profiles.
Hence, using social media to increase your on-line recognition is an impressive marketing and marketing approach.
Set up Anti-virus Safety
Antivirus merchandise work by detecting, quarantining, and/or deleting malicious code, to prevent malware from inflicting hurt to your instrument. Smooth antivirus merchandise change themselves mechanically, to fabricate security against the most fresh viruses and different kinds of malware.
Within the checklist of ABCs of Knowledge Safety, an antivirus product is a needed one. It’s a long way designed to detect and get rid of viruses and different kinds of malicious utility out of your pc or pc.

It’s needed that you simply repeatedly exercise antivirus utility, and follow it to this point to provide protection to your records and devices.
Antivirus utility is commonly included with out cost within the midst of the running programs that high-tail Windows and Apple computers. When you be certain that this built-in antivirus is switched on, you’ll straight away be safer.
In total, unusual computers most steadily comprise a trial version of a separate antivirus product installed (equivalent to McAfee, Norton, and Avast).
When you first set up (or swap on) your antivirus product, high-tail a plump scan to fabricate sure your pc is freed from all known malware and manufacture sure your antivirus utility is location to get updates mechanically.
Join Arms to Halt Spreading Erroneous Knowledge
In informal conversations, on social media, and within the news media, the phrase “faux news” has been faded frequently. Calling anything else “faux news” in a political surroundings is a tactic faded to confuse or undermine officials and distribute faux knowledge.
Halt! Verify your details before sharing, too. Produce a serious mentality and evaluative skills. Be pleased you know why and for what cause this records used to be created?

Don’t proper focal level on what a web location says about itself. As a replacement, notice them up on-line and peek what other folks are announcing about them. This would possibly maybe presumably maybe enable you assess the records’s accuracy.
Explore for authority, accuracy, objectivity, timeliness, and loads others. Thus, verify before you allotment! Rob the further few seconds to note over the source, or shuffle learn the article in plump to fabricate sure the hiss material accurately reflects the topic and that the positioning is knowledgeable.
Retain Utility As a lot as Date
Utility updates will most steadily possess unusual aspects, fixes for bugs, and performance improvements. They’ll most steadily additionally possess security patches and unusual security aspects, both of which it’s necessary to set up.
In ABCs of Knowledge Safety, the Patches topic in consequence of they repair known flaws in merchandise that attackers can exercise to compromise your devices.
All of this utility wants to be kept up to this point to lead clear of known vulnerabilities being faded. Installing fixes made within the market by utility builders to accelerate any security holes detected of their merchandise.

It’s a long way extra hard for attackers to successfully compromise your devices as a result of improved security aspects. Attackers that successfully compromise your devices would possibly maybe presumably maybe seize records, encrypt your files, and even render them ineffective.
While many apps and objects can set up updates mechanically, infrequently the owner of the instrument will need abet, to be capable to presumably easy put a stare on updates in case they pause functioning altogether.
Lock Your Gadgets When No longer in Use
Locking your desktop can have to you aren’t using it’s the finest system to prevent illegal entry.
If your pc, pill, or phone is stolen and there is now not any lock video visual display unit, the thief will straight away have entry to all of the records on the instrument.
Many of your apps, equivalent to your photos and notes, most steadily function now not require passwords or multifactor authentication, but a couple of of your apps would possibly maybe presumably.

The thief can have a discipline day impersonating you whereas you don’t verify out your social media or electronic mail accounts for your devices. That you just would possibly presumably maybe easy therefore location a lock video visual display unit for your instrument.
Most laptops, tablets, and smartphones feature a surroundings that lets in you to velocity up how immediate your instrument locks on its possess.
Attach in tips how frequently and for how prolonged you pause when using your devices. It’s a long way advisable to location the instrument to lock straight away after as dinky time as you are happy with.
Display screen Your Story for Any Suspicious Job
It’s advised to withhold an behold on the exercise on all of your accounts. Review your monetary institution assertion and manufacture sure there hasn’t been any aquire or debits you don’t stare.
ABCs of Knowledge Safety, Verify your trash on your electronic mail accounts, hackers will delete login notifications, but now not all of them deem to empty the trash as properly.
When you can presumably have Amazon or one thing linked, verify your enlighten history and manufacture sure there isn’t anything else there you didn’t enlighten.

In social media, verify your DM’s and manufacture sure there aren’t any messages there you haven’t sent. When you score unsolicited mail emails, flag them so your electronic mail provider can change their knowledge and put your mailbox neat.
When you deem anyone else is signed in to your Google Story, change your password straight away. Subsequently, stare what happens on all of your accounts.
Below no circumstances Judge On Forward Messages, Verify Source And URL
Mighty unverified knowledge is posted on social media and it’s a long way advisable to now not take into consideration in such messages. Folks would possibly maybe presumably maybe easy refrain from forwarding messages with out verifying them first.
Messages with the “Forwarded” imprint wait on you achieve in case your friend or family wrote the message or if it within the origin got right here from anyone else.
When a message is forwarded by a series of five or extra chats, which implies it’s as a minimal five forwards away from its fashioned sender, a double arrow icon and the “Forwarded many cases” imprint will likely be displayed.
When you’re now not sure who wrote the genuine message, double-verify the details.
Verify the URL and source to substantiate that it’s a long way actual. A actual URL repeatedly begins with “HTTPS” within the initiating as one more of “HTTP”.
The further “S” in “HTTPS” stands for “actual”, which implies that the on-line location is using a Stable Sockets Layer (SSL) Certificate.
Shiny that many users function now not listen to small print, some criminals have the profit of this habits when applying scams.
A missing letter, a typo, and, in some instances, serious grammatical errors are particular indicators that the positioning is now not actual — that it’s a long way likely a scam strive.

In some instances, faux addresses change characters, as an instance, by altering the “o” to a nil. For these in a bustle, the g0ogle.com web location will likely be one thing that doesn’t even procedure attention.
Erroneous news most steadily goes viral, and photos, audio recordings, and videos can even be edited to mislead you. Even though a message is shared many cases, this doesn’t manufacture it correct.
When you get knowledge that’s faux, present the sender that they sent you unsuitable knowledge and point out they verify messages before sharing them.
Most piquant Set up Apps and Utility From Depended on Sources
Before downloading an app, habits study to fabricate sure the app is knowledgeable. Checking the legitimacy of an app would possibly maybe presumably maybe embody things like checking opinions, confirming the legitimacy of the app retailer, and comparing the app sponsor’s first rate web location with the app retailer link to confirm consistency.
ABCs of Knowledge Safety, Many apps from untrusted sources possess malware that once installed can seize knowledge, set up viruses, and location off hurt to your phone’s contents.

There are additionally apps that warn you if any security risks exist for your phone. Be cautious of links you get in electronic mail and textual hiss material messages that would possibly maybe presumably trick you into inserting in apps from third-occasion or unknown sources.
Pay Additional Attention While The exercise of Public Wifi
Wi-Fi hotspots in coffee shops, libraries, airports, hotels, universities, and other public places are convenient, but most steadily they’re now not actual.
When you join to a Wi-Fi network and send knowledge by websites or mobile apps, anyone else would possibly maybe presumably maybe be ready to peek it.
When you’re at home, it’s seemingly you’ll seize steps to withhold your home wi-fi network actual — like using a solid router password, limiting what devices can score onto your network, and turning on encryption, and loads others.

However can have to you’re using your coffee store’s Wi-Fi, there’s now not loads it’s seemingly you’ll function to manipulate its network security.
Smooth hacking tools, within the market with out cost on-line, manufacture this uncomplicated, even for users with small technical know-how.
Your personal knowledge, non-public documents, contacts, family photos, and even your login credentials would possibly maybe presumably maybe be up for grabs.
Many public Wi-Fi networks equivalent to in airports and hotels will additionally urged you to set up a “digital certificates” to exercise their web.
They would possibly maybe presumably presumably function this to scan your traffic for malware — but this additionally lets in them to learn your traffic, although it’s to a location using HTTPS (which encrypts knowledge).
Use your mobile records as one more of Wi-Fi whereas you’re on the shuffle, can’t entry a actual web location, and don’t have VPN encryption.
Because it would also be hard to hunt down out whether an app is encrypted, right here is a precious replacement when entering personal knowledge into it.
Quarantine All Unused Apps
Rob away unnecessary (unused) functions from the instrument. This would possibly occasionally enhance overall performance, decreases litter, and would possibly maybe presumably maybe easy focal level on what’s pertinent.
Unwanted apps would possibly maybe presumably maybe now not be as traumatic but they’ll also be extra inappropriate by now not most productive taking over precious storage condominium but by impacting performance, reliability, and – doubtlessly – your phone’s security.

Games, namely, most steadily soak up loads of condominium. When you downloaded a refined sport and played it for a whereas, it’s easy sitting there taking over condominium.
That you just would possibly presumably maybe also with out enlighten peek which apps are taking over doubtlessly the most storage condominium correct from the Google Play Store. From there, it’s seemingly you’ll uninstall apps in bulk and seize aid a couple of of your storage condominium for photos, videos, and other stuff.
Admire the Privateness of Others
It’s necessary to admire other folks’s privacy in ABCs of Knowledge Safety. It’s a long way rude to ignore anyone’s needs within the occasion that they’ve a valid location off to withhold one thing non-public except there is a compelling reason to function in any other case.
Keeping privacy is the important thing to making sure human dignity, security, and self-resolution. It lets in folks freely make their possess personalities.

Privateness protects the records we present out now not must be shared publicly (equivalent to health or personal price range). Privateness helps provide protection to our bodily security (if our proper-time location records is non-public).
Respecting privacy is seriously necessary for companies going by sensitive buyer records.
Scan Any File Downloaded From the Web Before Opening/ The exercise of/ Installing
First, it’s seemingly you’ll scan the file with the antivirus utility that’s installed for your PC with out having to scan your total pc.

But any other arresting system to substantiate that that suspicious files are freed from viruses is to match their get link before clicking the get button.
There are diverse on-line malware evaluation tools within the market it’s seemingly you’ll exercise to scan files; VirusTotal is doubtlessly the most advised.
Flip On Computerized Updates For Your Operating Diagram
Utility updates fortify the protection of your devices. They reduction repair security flaws or vulnerabilities that were enlighten on your instrument’s utility.
Cybercriminals and malware can exercise these vulnerabilities to entry your instrument or personal knowledge. Smooth vulnerabilities are stumbled on and stuck the total time, so set up updates progressively to withhold your devices actual.

Turning on computerized updates is absolutely the most effective system to withhold your instrument up-to-date and actual. Computerized updates are a “location and forget” feature that installs updates as soon as they come in.
If your running design or other utility is now not any longer receiving updates, you can presumably easy take into consideration upgrading to a extra fresh version or switching to 1 more product to pause actual.
By default, Windows updates your running design mechanically. On the opposite hand, it’s seemingly you’ll change when Windows installs your updates, allowing you to withhold working with out interruption.
Use Solid Passwords With Personal Acronym
Safety experts enlighten using acronyms to be conscious passwords. They are saying using the major letters of a sentence makes remembering passwords easy whereas additionally improving security.

It’ll be an acronym for a non-public procedure, which would possibly maybe presumably presumably motivate when utilized. Iwl10k—I will lose 10 kgs—would possibly maybe presumably maybe be a password if one’s procedure is to descend a couple of pounds, as an instance.
Indubitably, this approach can even be employed wherever a password is required and location the particular tone for every login.
Verify With Whom You Are Interacting Online
Online communication can even be unsafe can have to you meet unusual folks. Attributable to it’s in point of fact easy to make an on-line profile, another folks have abused this convenience to deceive others by creating faux on-line personas, most steadily on social media or networking websites.
Many of the oldsters with who you interact on-line will likely be actual, but some will exercise faux profiles designed to procedure you in and manipulate you.
That you just would possibly presumably maybe also verify to peek if their profile describe is of an proper individual. If other photos on their account trace the same individual, they’ll be telling the fact.

Verify their space updates and publish, within the occasion that they are largely posting links and ads, it’s a long way likely that they are using a pretend profile to scam other folks or manufacture gross sales.
Hence, be vigilant and double-seek the advice of with whom you are interacting on-line.
Explore Out For Online Scams
Web scams are frequently evolving. Scammers would possibly maybe presumably maybe strive and contact you by social media, textual hiss material, phone, electronic mail, or mail.
Retain your identification and cash actual. Don’t present non-public knowledge like your date of initiating, Social Safety quantity, or monetary institution account quantity.
Know who you’re going by, and function now not originate suspicious texts, pop-up windows, or click on links or attachments in emails – delete them, function now not originate suspicious texts, pop-up windows, or click on links or attachments in emails – delete them.

Retain your individual small print actual, put your mobile devices and computers actual, resolve your passwords fastidiously, review your privacy and security settings on social media, be cautious of peculiar rate requests and watch out when looking on-line.
Xtra Precaution For Your Online Financial Transactions
Unfortunately, on-line fraud and identification theft happen proper as frequently. Users would possibly maybe presumably maybe easy seize loads of key steps to be as actual as attainable whereas doing on-line transactions:

- Use a laborious-to-wager password that comprises greater and decrease-case letters, numbers, and symbols.
- Alternate passwords as most steadily as attainable, but as a minimal every three months
- Be pleased now not exercise the same username and password for all on-line accounts.
- Below no circumstances click on any links in an electronic mail inquiring for identification knowledge. Contact the establishment by phone straight away to picture the topic.
- Constantly log off of the monetary institution, bank card, and provider provider websites after you can presumably have accomplished your transaction.
- Be pleased now not enable your pc to retailer user names and passwords for provider provider or banking websites.
- Use a educated third-occasion rate provider equivalent to PayPal for on-line transactions every time attainable. These websites present actual transactions and dispute resolution companies.
- Stable on-line transactions would possibly maybe presumably maybe easy happen most productive on a web location that begins with “HTTPS://.” Be pleased now not have faith a dealer with out the “S” after “http” within the initiating of the on-line address.
Your Precedence On Cyber Safety Ranking You Cyber Conscious Citizen
Awareness of cyber security is serious as it protects an group from cyber assaults on the design ensuing in records breaches.
Utility vulnerabilities are a colossal deal. If cyber security isn’t your high precedence, your business is at high threat. The implications of an records breach can even be large and involve greater than proper fines.

Shiny about diverse cyber threats, the flexibility to detect doable threats, and taking measures to mitigate their manufacture to provide protection to your digital assets manufacture you a cyber-conscious citizen.
Zero Participation in Gloomy Web
The sad web is the hidden collective of web websites most productive accessible by a in point of fact expert web browser. There would possibly be loads of tainted hiss material that you simply can presumably easy steer clear of. It’ll also be offensive at finest and extremely illegal at worst.
It’s a typical gathering web page online for hackers and other cybercriminals, that can manufacture looking the sad web a deadly exercise.

Additional, it’s a long way properly illegal to fabricate illegal acts anonymously, equivalent to having access to dinky one abuse photos, promoting terrorism, or selling illegal objects equivalent to weapons.
Subsequently, all companies, folks, and groups would possibly maybe presumably maybe easy steer clear of using the sad web and pause strict with the ABCs of facts security.
Conclusion
Knowledge security awareness helps to diminish threat, battling the inability of PII, mental property, cash, or trace recognition. An efficient cyber security awareness program addresses the errors all users would possibly maybe presumably maybe commit when utilizing electronic mail, the web, and the correct world.
Taking note of these ABCs of facts security awareness, the development turns into extra life like. It’ll additionally reduction in starting or refining efforts linked to knowledge security.
Also Learn:
10 Easiest IoT Safety Tools – 2023
10 Easiest UTM Utility (Unified Threat Administration Solutions)
Easiest Commence Source Intelligence Tools (OSINT Tools) for Penetration Testing
Easiest Developed Endpoint Safety Tools
Unhealthy DNS Attacks Kinds and The Prevention Measures
Easiest Commence Source Firewall to Defend Your Enterprise Community
Easiest Commence Source Intelligence Tools (OSINT Tools) for Penetration Testing
Free Web Application Penetration Testing Tools
Easiest Free Penetration Testing Tools
Source credit : cybersecuritynews.com


