Agenda Ransomware Attacking VMWare vCenter & ESXi servers WorldWide
.webp)
Agenda ransomware personnel, moreover identified by its aliases Qilin and Water Galura, has been ramping up its assaults globally.
This noxious personnel has centered on the United States, Argentina, Australia, and Thailand, and it has been focusing on industries serious to the economy, such as finance and legislation.

On the opposite hand, a newest pattern has emerged: Agenda is setting its sights on a brand unique, extremely serious purpose: VMware vCenter and ESXi servers.
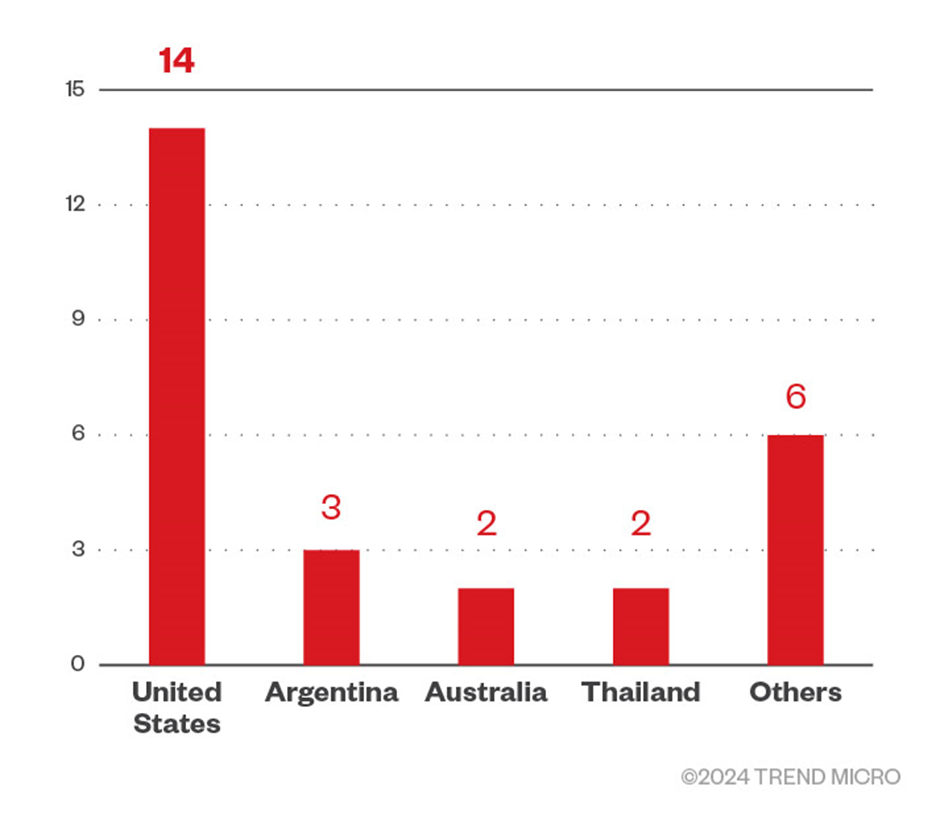
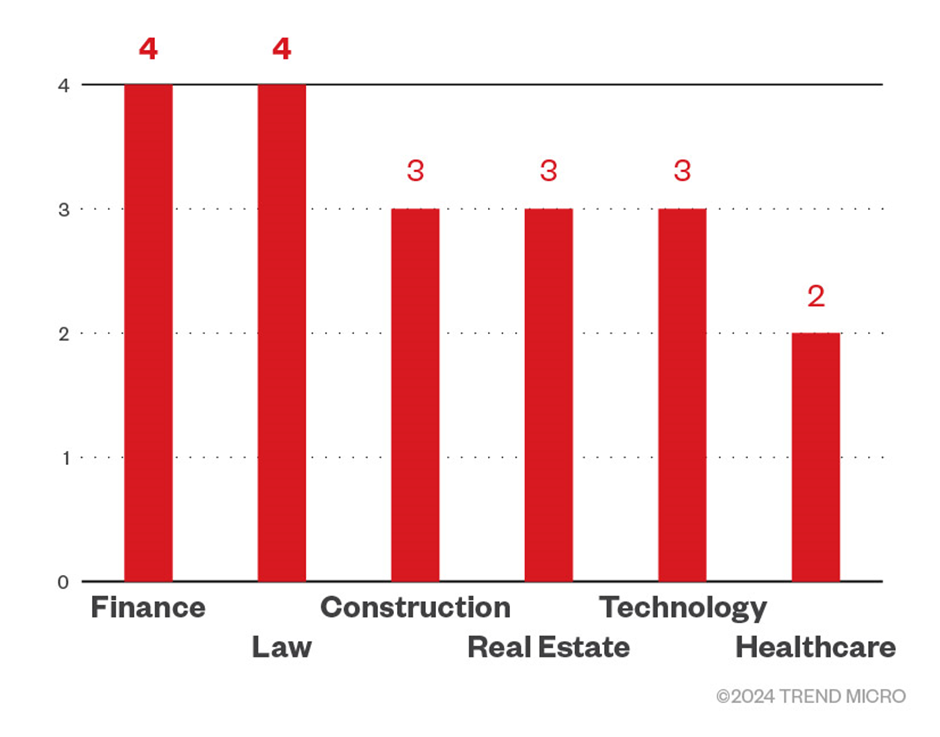
The Rise of Agenda Ransomware
First identified in 2022, Agenda has snappy evolved, demonstrating a fancy thought of cybersecurity vulnerabilities and suggestions on how to milk them.
Pattern Micro, a number one cybersecurity agency, has been closely monitoring the personnel’s activities and has great a main uptick in assaults since December 2023.
Gain Free CISO’s Files to Warding off the Next Breach
Are you from The Group of SOC, Network Security, or Security Supervisor or CSO? Gain Perimeter’s Files to how cloud-based, converged community security improves security and reduces TCO.
- Understand the importance of a zero belief approach
- Full Network security Checklist
- Gaze why relying on a legacy VPN is just not any longer a viable security approach
- Salvage suggestions on suggestions on how to newest the transfer to a cloud-based community security resolution
- Stumble on the advantages of converged community security over legacy approaches
- Gaze the tools and applied sciences that maximize community security
Adapt to the changing probability panorama easily with Perimeter 81’s cloud-based, unified community security platform.
This surge in job suggests that the personnel is either expanding its operations or turning into more functional at reaching its targets.
A newest tweet by Dismal Studying finds that a world ransomware wave has been launched explicitly focusing on VMware ESXi servers.
Technical Breakdown
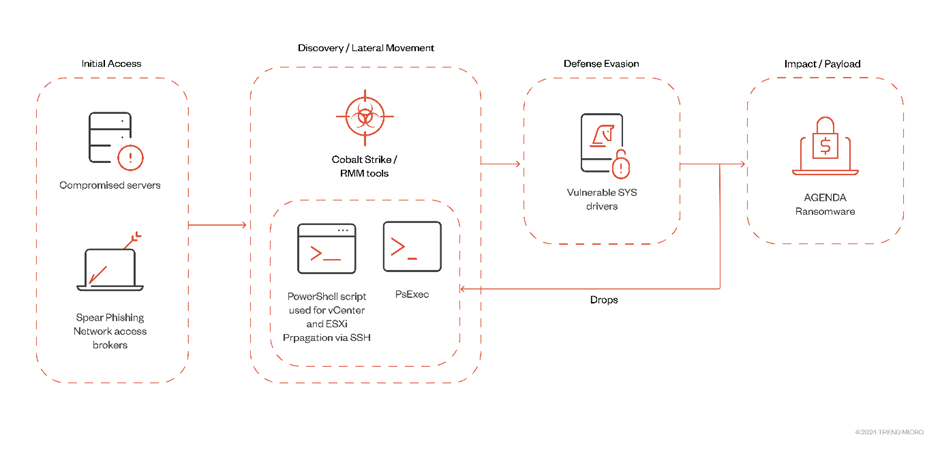
The agenda’s contrivance of attack is especially insidious. The personnel employs Distant Monitoring and Management (RMM) tools and Cobalt Strike to deploy its ransomware binary.
As soon as at some level of the machine, the ransomware can propagate by diversified near, including PsExec and SecureShell, and employs different weak SYS drivers for defense evasion.
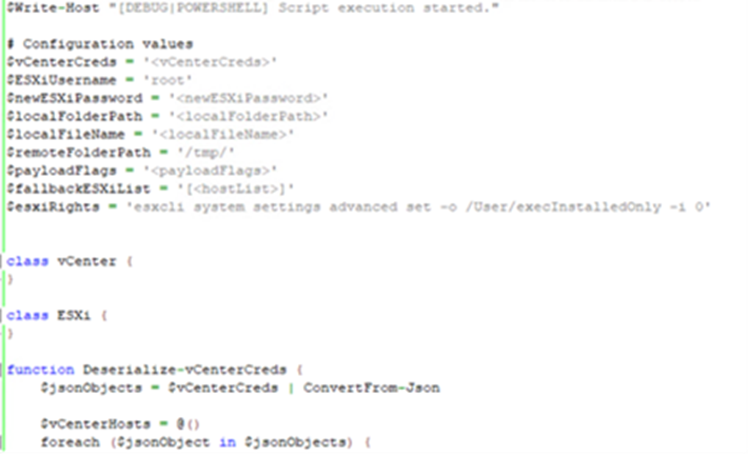
A comparison of the uncover-line arguments aged by Agenda in July 2023 and February 2024 finds main enhancements within the ransomware’s capabilities.
Particularly, the addition of arguments such as –no-sandbox for disabling sandbox detection, –impersonate for token impersonation, and –unfold-heart for propagation in vCenter and ESXi, amongst others, showcases the personnel’s evolving sophistication.
Lateral Circulate: T1021.004 Distant Companies and products – SSH
Belief to be one of many most alarming dispositions is Agenda’s ability to unfold to VMWare vCenter and ESXi servers.
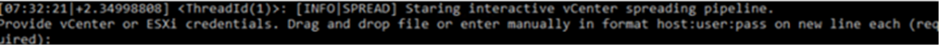
By executing a personalized PowerShell script embedded within the binary, the ransomware can propagate at some level of virtual infrastructure, potentially resulting in main knowledge, financial loss, and disruption of products and services.
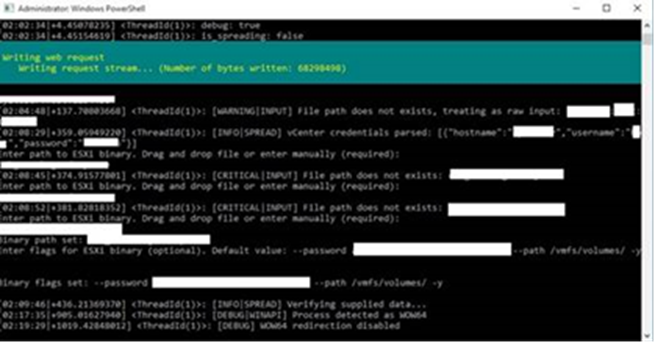
Protection Evasion Ways
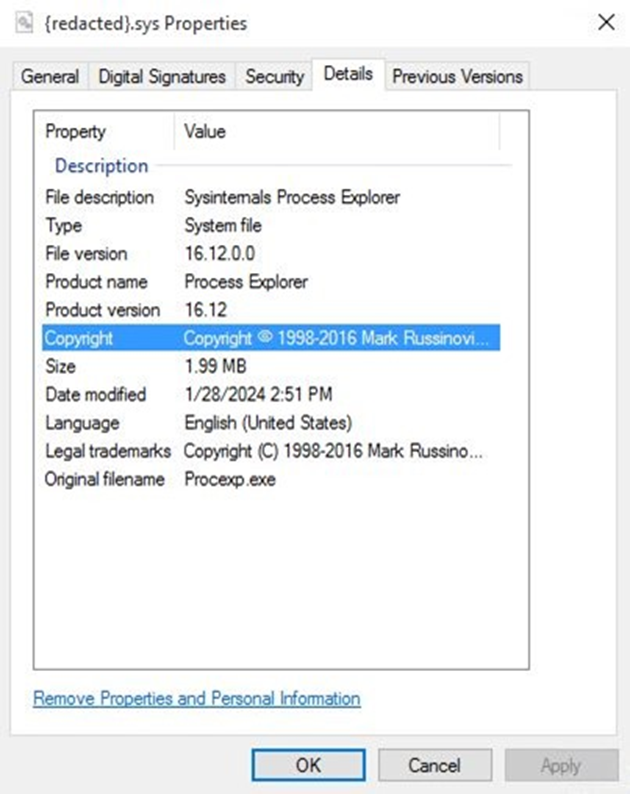
Agenda employs the Carry Your Susceptible Driver (BYOVD) contrivance to evade detection, leveraging different weak drivers to disable security tools.
This near highlights the adaptability of ransomware and the challenges cybersecurity defenses face in stopping these threats.
Organizations are suggested to adopt a multilayered security with regards to wrestle the probability of Agenda and equivalent ransomware.
This involves sparingly granting administrative rights, performing long-established security scans, backing up knowledge, practicing safe electronic mail and net browsing habits, and instructing customers on social engineering risks.
The Agenda ransomware personnel’s address VMWare vCenter and ESXi servers marks a main escalation within the cyber probability panorama.
As these assaults evolve, organizations have to defend vigilant and put in force sturdy cybersecurity measures to present protection to their serious infrastructure from these more and more refined threats.
Preserve updated on Cybersecurity info, Whitepapers, and Infographics. Adjust to us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


