ANY.RUN Sandbox Now Analyzes Complex Linux Malware For SOC & DFIR Teams
The ANY.RUN sandbox has recently gone thru an update to encompass toughen for Linux, strengthening its ability to supply a real and remoted atmosphere for inspecting malware and conducting menace analysis.
Essentially the most traditional feature launched will facilitate security analysts to be aware and replicate malevolent actions in Linux-oriented systems, providing a more broad and potent menace belief and response.
ANY.RUN is a cloud-based atmosphere for inspecting Windows malware and Linux-based samples. It’s precious for malware analysts, SOC, DFIR teams, and SOC personnel with ANY.RUN, users can safely glimpse threats, simulate a couple of scenarios, and blueprint insights into malware habits to toughen cybersecurity systems.
Linux malware analysis is serious on myth of Linux is a favored purpose for hackers, and Linux malware is refined.
Linux is widely dilapidated in organizational IT infrastructures, ensuing in loads of recordsdata that deserve to be analyzed on these systems.
Researchers at IBM hang noticed an elevate in Linux malware. In 2020, the sequence of malware families connected to Linux elevated by 40%.
Compromising Linux-based cloud computing platforms would possibly enable attackers salvage entry to to big sources, making the OS an enticing purpose.
Try ANY.RUN Your self with a 14-day Free Trial
More than 300,000 analysts use ANY.RUN is a malware analysis sandbox worldwide. Join the neighborhood to conduct in-depth investigations into the tip threats and accumulate detailed experiences on their habits..
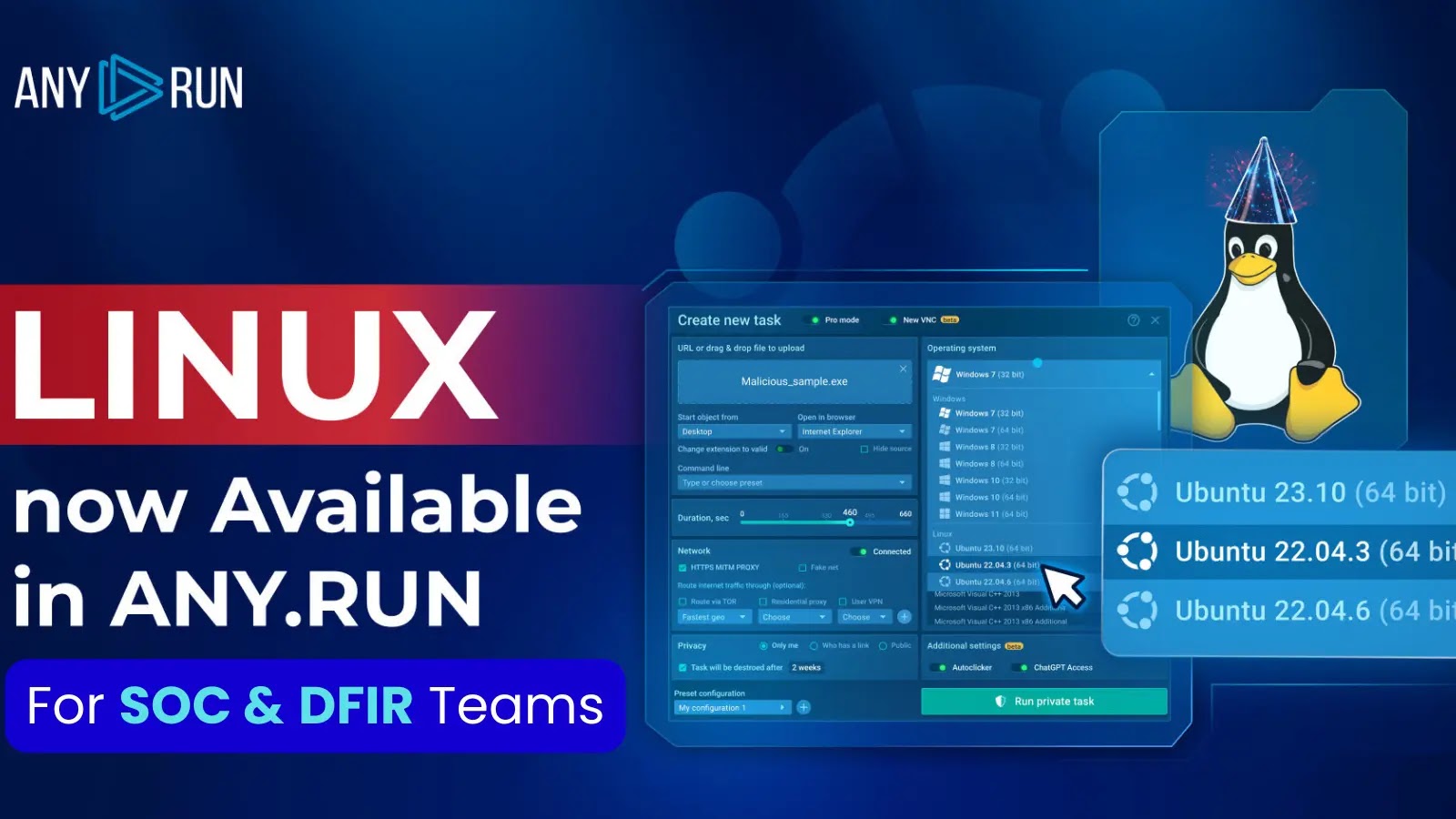
How to Create a Original Job in Linux
You’d make a selection Linux as your working Machine from the drop-down menu when creating a brand current assignment.Â
Per the ANY.RUN listing, Whereas you happen to reach to a name this probability, the sample will flee on Ubuntu. It’s value noting that Ubuntu 22.04.2 will in all probability be supported upon inaugurate and all ANY.RUN users, in spite of their contrivance, would possibly hang salvage entry to to Linux.

The Ubuntu label identifies the Linux samples to serve with navigation. This makes it easy to distinguish between Windows and Linux-based initiatives within the crew’s homepage and sidebar snappily menu.
Enhancing Linux Malware Analysis with ANY.RUN’s
ANY.RUN, a platform for interactive malware analysis, has made its Windows sample analysis capabilities obtainable on Linux for the first time.Â
The platform can serve analysts rapid establish undetected threats using interactive analysis, even within the case of zero-day vulnerabilities, while using fewer sources. This makes it glorious for coaching entry-level analysts and reverse engineers.
ANY.RUN’s interactive analysis lets in for the snappily identification of suspicious activities, with staunch-time indicators making sure that no serious files is misplaced sight of.Â
Upon assignment completion, concise experiences are generated that supply salvage entry to to all connected records and IOCs, making further investigation or incident response more straightforward.
The platform moreover facets an MITRE Matrix listing that helps establish the more or less menace or family in step with suspicious behaviors recorded within the Linux sandbox assignment. This feature is at hand for rapid aligning suspicious behaviors with TTPs.
For more files on ANY.RUN facets, you would study the platform’s capabilities by visiting 8 ANY.RUN.
Benefits of using ANY.RUN to review Linux malware
Linux-based working systems are inherently more real than Windows. Alternatively, many malware families can quiet exploit vulnerabilities in Linux, that are complicated and refined to establish.
ANY.RUN affords a easy manner to review Linux malware and blueprint staunch-time files from the analysis.
This eliminates the need for security specialists to private reverse engineering skills to establish complicated Linux malware and extract the crucial IOCs rapid. The outcomes are straight understandable, allowing analysts to circulate forward successfully without context switching.Â
ANY.RUN is a cost-efficient resolution that eliminates the need for customized infrastructure requirements. With preconfigured Linux virtual machines (VMs) that accumulate IOCs, customers can withhold away from weeks of infrastructure setup time connected to DevOps.

To boot to being a stand-by myself research platform, ANY.RUN can moreover be dilapidated along with SIEM/SOAR. Upright analysis of Linux malware is crucial for solid security, as Linux is widely dilapidated, in particular in cloud cyber web online page hosting, making it a trim purpose for attackers.
Breaching a Linux-based system can provide salvage entry to to a wealth of sources, so Linux users deserve to be attentive to the growing threats to their gadgets.
ANY.RUN is a cloud-based malware sandbox for SOC and DFIR teams. With improved facets, 300,000 specialists can review incidents and streamline menace analysis. Try all facets of ANY.RUN at zero cost for 14 days with a free trial.
Source credit : cybersecuritynews.com