APT41 Hackers Using 'Google C2' Red Team Tool as a Payload in Mass Cyber Attacks

A community from China attacked a media organization in Taiwan, which is no longer yet identified, and dilapidated Google’s platform to spread a crimson crew tool known as Google Whine and Adjust (GC2) as a remaining payload.
Whereas it’s segment of their wider efforts to fabricate tainted and malicious actions the utilization of Google’s sources.
The Threat Analysis Neighborhood (TAG) of Google impartial no longer too lengthy within the past diagnosed a campaign that a community of hackers implemented known as HOODOO. At the same time, this community is identified by various names in response to geography and situation, which is being monitored by the TAG.
Right here below, now we own mentioned the total varied names of “HOODOO”:-
- APT41
- Barium
- Bronze Atlas
- Noxious Panda
- Winnti
Strategic Point of view — Executive-Backed Hackers Prone to Investigate cross-test to Criminals for Inspiration Targeting Cloud
Continually, we imagine militia and espionage expertise becoming readily accessible to the public after a whereas in a course of known as “fling-off.”
It entails making futuristic gadgets, admire fighter jets and scrutinize gear, readily accessible for public exercise and commercialization.
In some conditions, it has been noticed that organized crime teams are the first to undertake militia or espionage expertise.
They continually own an advantage over their targets, who easy exercise outdated expertise from previous conflicts. This, as a result, is a mismatch in protection that will well per chance lead to elevated vulnerability for the focused community.
With expertise being a necessary segment of militia conflict and intelligence opponents, dispute-subsidized cyber attackers continually ogle programs to construct their arsenal.
By adapting the tools from threat actors, they attain so the utilization of the next parts:-
- Printed vulnerability review
- Together with exploits dilapidated within the wild
- In-condominium customized-made tools had been developed
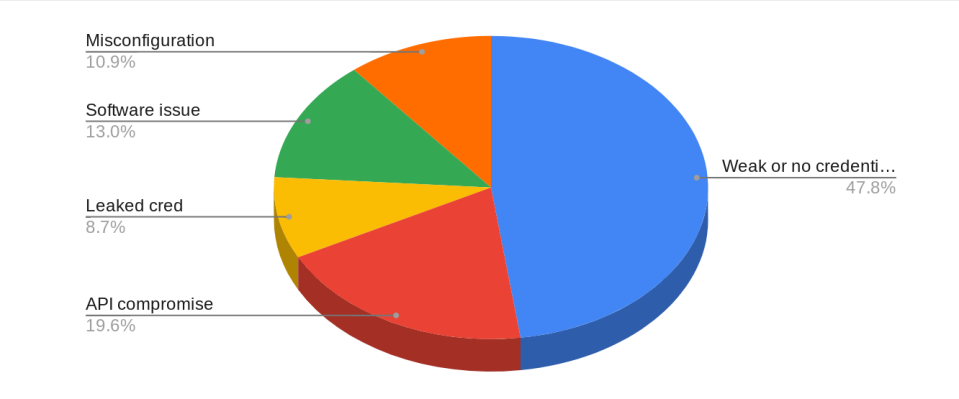
Credentials and API Points Continue to Lead to Compromise Components
Due to the the gentle passwords, it was once noticed all around the fourth quarter of 2022 that nearly half of the safety breaches and incidents had been triggered.
No longer easiest that nonetheless even within the previous three months, this pattern has remained obvious. API compromise remained a important ingredient in nearly 20% of incidents within the third quarter, asserting its pattern.
Nonetheless, there was once some sure files, with a puny lower in misconfiguration and power points. The elevated exercise of leaked credentials partly offset the lower.
Threat actors easy prioritize the utilization of credential-based salvage admission to, a important remark for 2023. Briefly, organizations must compose it their top priority to address this downside on a at once basis to extinguish additional exploitation.
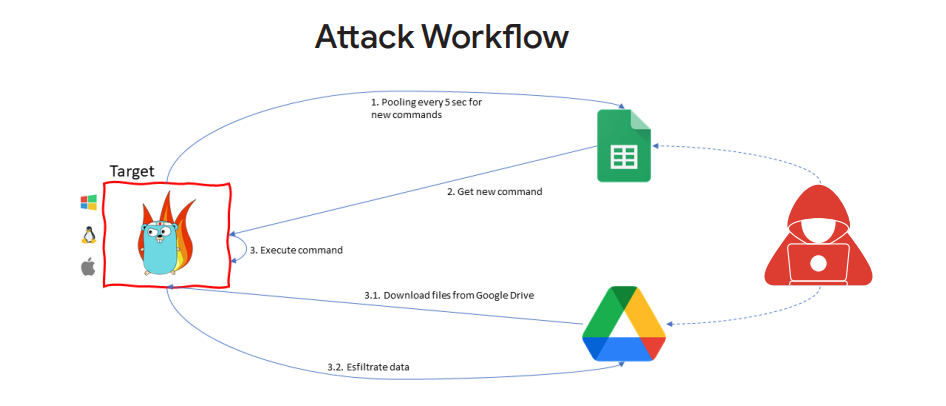
HOODOO Makes exercise of Public Tooling, Google Workspace to Purpose Taiwanese Media
HOODOO (aka APT41), a Chinese language-backed threat community, focused a Taiwanese media organization in October 2022. Whereas focusing on the media company, they sent phishing emails containing links to password-safe files, and the total files sent had been stumbled on to be hosted in Drive.
Nonetheless, on the time, Google’s Threat Analysis Neighborhood (TAG) was once ready to disrupt the campaign.
The payload dilapidated within the HOODOO attack on a Taiwanese media organization was once a Slip-written initiate-provide crimson teaming tool named “Google Whine and Adjust” (GC2).
Right here, the tool makes exercise of the Google Sheets commands after set up on the victim machine to extract files into Google Drive, which is executed to cowl malicious exercise.
Because these incidents, a couple of key traits about the threats posed by cybercriminals affiliated with China had been diagnosed.
Compromised Customer Web pages Hosted on IT Provider Suppliers’ Infrastructure
Google stumbled on 14 customer web sites in Feb 2023 on their cloud web location hosting platform that had been hacked and talking with malware.
Cybersecurity analysts at Google stumbled on this by the utilization of 2022 VirusTotal files. IT Provider Suppliers (ITSP) had been accountable for establishing the total web sites for 14 customers who had bought GC providers from the ITSPs.
There are a couple of things that customers of Google Cloud ITSP and even ITSPs can attain to extinguish such misuse of their environments:-
- Be sure customers are appropriately segregated.
- A particular person administrator’s capability to salvage admission to all customers must be runt.
- Video show and analyze endpoint servers to search out out if they’ve been compromised and take acceptable motion.
- Be sure to patch vulnerabilities stumbled on the utilization of vulnerability scans at once.
- ITSPS must make certain the flexibility to salvage admission to sources in response to their roles.
- In resold resources, ITSPs must provide steering to customers relating to the obtain configuration of web sites, web purposes, and domains.
- Be sure tenants are remoted from one another.
Cloud-Hosted Encrypted ZIP Recordsdata Evading Detection
Google Cybersecurity Action Crew (GCAT) and Mandiant investigated the exercise of Google Drive for malware web location hosting by threat actors.
They stumbled on that in an strive to lead clear of detection, the malware was once being saved in encrypted ZIP files on Google Drive.
In Q4 2022, threat actors utilized DICELOADER malware to amplify on this methodology. DICELOADER is a versatile form of malware that threat actors can exercise for various illicit purposes or malicious activities.
Threat actors the utilization of cloud providers to host malicious deliver pose a likelihood as they proceed to manufacture evasive and stealthy tactics to lead clear of detection.
They own moved from the utilization of encrypted ZIP files containing malware to the utilization of encrypted ZIP files that link to trojanized legitimate installers.
All these stealthy tactics are referring to and emphasize the importance of asserting strong cybersecurity measures.
Customer Challenges and Alternatives When Security Patching Google Kubernetes Engine
The provision, flexibility, and security supplied by Kubernetes clusters own resulted in an increasing selection of cloud customers running their workloads on them.
Kubernetes clusters require ordinary patching to assign their aspects and make certain the set up of security fixes.
GKE customers can make sure their workloads remain readily accessible and up-to-date with security patches by establishing and managing Kubernetes environments. This permits a faster patching course of with out disrupting the ongoing commerce operations.
In 2021-22, GKE teams spoke with customers and stumbled on that most delayed or prolonged security patching to balance security and availability concerns are:-
- It has been a remark for some customers to update their purposes when surprising patches can damage the “dispute” of those purposes.
- For the length of the patching course of, one of the important most crew tremulous that no longer-yet-accomplished workloads would must be restarted all around the set up, which would possibly also disrupt work admire machine learning “practicing”.
- Customers had been exciting that security upgrades can also moreover result in unanticipated changes to APIs, so that they delayed upgrading.
- It is possible that patching will take longer for customers with plentiful node fleets, and a gentle security posture would be maintained longer.
The low-striking fruit: leaked provider yarn keys and the impact in your organization
Without a doubt one of many main causes of abuse on Google Cloud is nonetheless the leakage or inadvertent sharing of provider yarn credentials.
In step with Google’s abuse programs, 42% of leaked important incidents came about on yarn of customers did now not take motion after being contacted by Google, leaving the keys susceptible or uncovered.
The next points must be taken into yarn by organizations seeking to within the bargain of or mitigate the dangers they face:-
- Elegant management.
- Precept of least privilege with scoped IAM policies.
- Be sure the implementation of restricted policies and controls.
- Be sure to proceed scanning and monitoring uncovered keys.
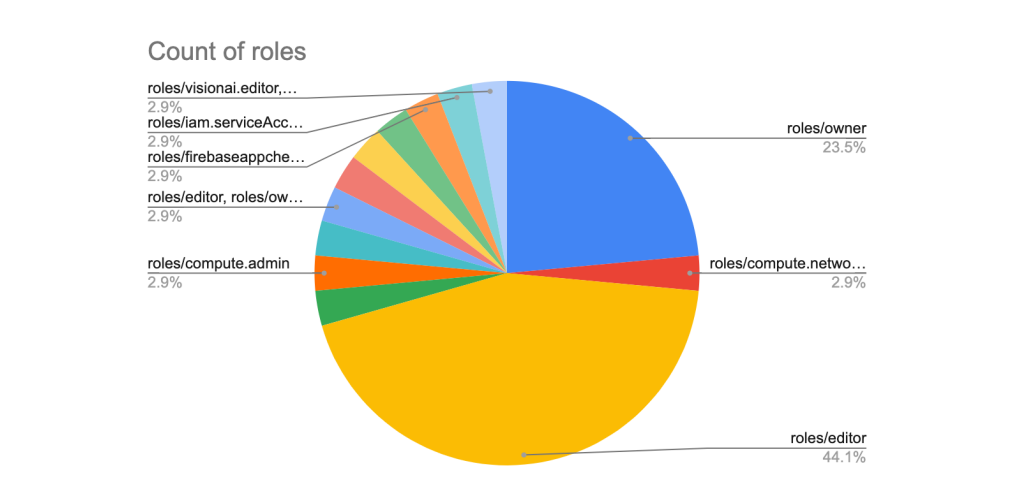
The head 5 most dilapidated policies on AWS and Azure had been AdminstratorAccess and Proprietor, respectively, mirroring what Google Cloud’s Fraud and Abuse teams own stumbled on with IAM feature assignments.
Organizations face important dangers and possible penalties when provider yarn keys and varied persistent credentials are leaked, making it major to acquire such sensitive files.
Mitigations
Right here below, now we own mentioned the total prompt mitigations:-
- Be conscious easiest practices when establishing Provider Accounts and assess their need.
- The stock must be saved, and the customer must be audited continually.
- If keys are uncovered, own a knowing and test your assumptions after discovering them.
- Make the reasonably a range of the IAM recommender, implement organizational policies, and scope IAM permissions.
- Be sure keys are no longer checked in and video show for keys that had been uncovered.
How one can Arrange and Accurate Your Endpoints? – Download Free E-books & Whitepapers
Source credit : cybersecuritynews.com


