Attackers Uses Weaponized Document to Deliver Jester Stealer Malware using Chemical Attack Themes

The Computer Emergency Response Crew of Ukraine (CERT-UA) has now not too long ago issued a warning in regards to the mass distribution of malicious emails concentrated on Ukrainian voters.
The CERT-UA advisory says, “In the event you launch the document and spark off the macro, the latter will catch and flee the EXE file, that may possibly presumably soon hurt the computer with the bug JesterStealer. It’s far famed that executable data are downloaded from compromised web sources”.
How the Chemical Assault Carried Out
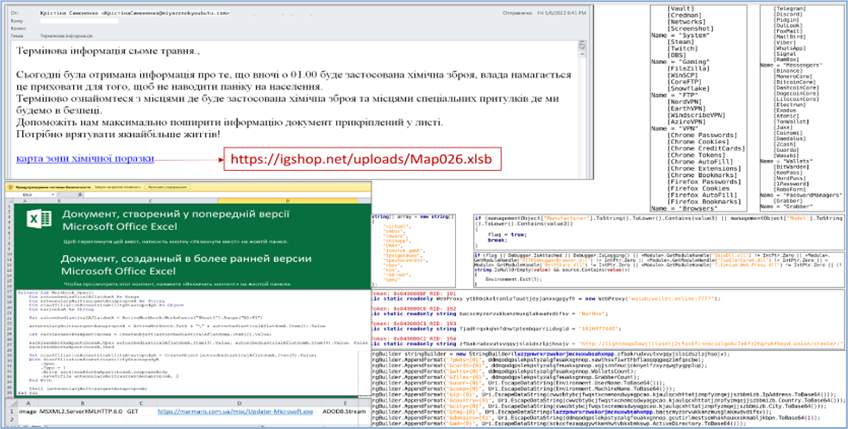
The emails dangle the topic line “chemical attack” and warn Ukrainian that data has been got that signifies chemical weapons shall be used at 01:00, and that the authorities are now not alerting the general public to the threat so as now to not reason fear.
The emails claim to produce data on the place the chemical weapons shall be used and the difficulty of shelters the place individuals shall be stable. That data is supplied in a document, a link to which is incorporated in the e-mail.
Upon clicking the link, the user shall be directed to an XLS spreadsheet hosted on a compromised web problem. The XLS spreadsheet holds a malicious macro that runs if the document is opened and the utter is enabled. The macro delivers an .EXE payload from a far flung server and executes that file, which delivers Jester malware.
Jester Stealer Malware
This malware can clutch and exfiltrate login credentials, cookies, crypto wallets, passwords kept in browsers, messages in email clients, IM chat data, and diversified data.
It furthermore has anti-analysis parts to sense when it is in a sandbox or virtual machine and lacks a mechanism for persistence, so shall be eradicated after its operations had been performed and the program is closed. Consultants yell that there isn’t very any mechanism to make certain resistance – after closing the program is eradicated.
There is a suspicion if this may possibly presumably be an attack from the pro-Russian hacking crew or from a cybercriminal gang. Since Jester malware is broadly accessible and is licensed at $99 per thirty days or $249 for lifetime exercise, the campaign is now not going to had been conducted by a nation-suppose threat actor.
For the rationale that invasion of Ukraine, the voters are highly vigilant and they are residing with the worry of chemical weapon attacks, so there’s a excessive risk that the emails shall be opened. As antagonistic to of the significance of the threat outlined in an email, it is extraordinarily crucial to practice email security most productive practices and now to not practice links or launch email attachments in unsolicited emails.
You can practice us on Linkedin, Twitter, Fb for each day Cybersecurity and hacking news updates.
Source credit : cybersecuritynews.com


