Best AWS Network Access Security Solutions – 2024
Most attention-grabbing AWS Network Discover admission to Security Solutions – 2024
AWS (Amazon Web Services) community collect admission to refers back to the systems and products and services that enable users and applications to connect to AWS resources, products and services, and the gain.
AWS provides a whole dispute of networking products and services to present a steal to cloud computing. These products and services enable stable and scalable connectivity in your applications, facilitate the arrival of remoted networks during the cloud, and attach your physical community to your AWS resources.
Bring together AWS community collect admission to security encompasses the systems, instruments, and practices to present protection to knowledge, applications, and resources accessed or hosted during the Amazon Web Services (AWS) cloud atmosphere from unauthorized collect admission to, assaults, or knowledge breaches.
AWS presents so a lot of security facets and products and services that customers can use to stable their community collect admission to. These mechanisms are designed to originate each flexibility and grand AWS security controls to fulfill the necessities of various applications and compliance requirements.
Network security leaders equivalent to Perimeter81 offer AWS Network Discover admission to Security to Bring together your cloud atmosphere and present non-public community collect admission to to AWS resources and applications. Try Free Demo.
What are the AWS Network Discover admission to Parts & Services?
Amazon Digital Personal Cloud (VPC): Gives a logically remoted design of the AWS Cloud where it’s essential to to per chance per chance deploy AWS resources in a digital community you configure. It’s doubtless you’ll per chance per chance settle your IP take care of differ, originate subnets, and configure route tables and community gateways in your digital networking atmosphere.
AWS Sing Join: A dedicated community connection to AWS from your premises. This provider can put community charges, boost bandwidth, and enhance community consistency across web connections.
Amazon Route 53: A scalable and highly accessible Domain Name Draw (DNS) web provider that converts names love www.example.com into numeric IP addresses love 192.0.2.1 for builders and agencies to route dwell users to Web applications.
Elastic Load Balancing (ELB): Distributes application site visitors amongst Amazon EC2 cases, containers, IP addresses, and Lambda capabilities. It’ll kind out fluctuating application site visitors in a single or extra Availability Zones.
Amazon CloudFront: A developer-pleasant CDN that securely distributes knowledge, videos, apps, and APIs to customers worldwide with minimal latency and high transfer rates.
AWS Transit Gateway: Connects Amazon VPCs and on-premises networks to one gateway. AWS Transit Gateway helps you to homicide and arrange a single connection from a central gateway to each Amazon VPC, on-premises knowledge center, or far away place of job in your community.
Bring together your cases and VPC by controlling inbound and outgoing site visitors with Security Teams and Network Discover admission to Retain watch over Lists (NACLs).
How attain you stable the AWS Cloud Atmosphere utilizing a community security provider?
To stable your AWS cloud atmosphere utilizing a community security provider love Perimeter 81, practice these concise steps:
- Combine Perimeter 81 with AWS: Get of living up your Perimeter 81 story and combine it alongside with your AWS atmosphere via VPN or command connectors to your AWS VPCs.
- Elaborate Bring together Networks: Exercise Perimeter 81 to originate stable networks encapsulating your AWS resources, ensuring definite boundaries are dispute.
- Put in force Discover admission to Controls: Configure collect admission to insurance policies in Perimeter 81 to administer who can collect admission to what interior your AWS resources, utilizing blueprint-basically based mostly collect admission to assist an eye on (RBAC) and enabling Two-Part Authentication (2FA).
- Section Networks: Section your community to separate collect admission to between assorted environments (e.g., vogue, staging, manufacturing) interior AWS.
- Video display and Arrange Web page online visitors: Leverage Perimeter 81âs capabilities embody inspecting and monitoring community site visitors and utilizing Bring together Web Gateways to filter depraved site visitors.
- Attach in force Zero Belief Application Discover admission to: Adopt Zero Belief principles for application collect admission to, verifying all users and devices whereas limiting collect admission to strictly to foremost resources.
- Exact Monitoring and Auditing: Exercise Perimeter 81âs monitoring instruments for valid-time signals and habits customary security audits to make sure compliance and alter insurance policies as wanted.
- Educate Your Crew: Originate definite your team is conscious of simplest security practices and the significance of declaring a stable cloud atmosphere.
AWS Network Discover admission to Security Companies and its Parts
| AWS Network Discover admission to Security Solutions | Key Parts |
|---|---|
| 1. Perimeter 81 | 1. Scalable cloud-edge infrastructure 2. True-time security monitoring 3. Granular AWS collect admission to monitoring 4. High-notch site visitors encryption 5. Actionable intelligence from analytics |
| 2. Amazon Web Services (AWS) Security | 1. Sexy-grained security protection enforcement 2. Extensive site visitors visibility 3. Active effort security 4. Central administration |
| 3. Palo Alto Networks | 1. Cloud-native NGFW provider 2. App-ID, URL filtering, 3. SSL/TLS decryption 4. Zero maintenance is required for their cloud products and services. 5. Fleet deployment capabilities for instantaneous security. |
| 4. Fortinet | 1. Integrated security suite 2. High-performance VPN collect admission to 3. Cloud-native visibility 4. Evolved possibility security 5. Centralized administration |
| 5. CheckPoint | 1. Evolved possibility prevention against each known and unknown threats. 2. Seamless integration with AWS products and services. 3. Automatic security protection administration. 4. Network and application security |
| 6. Pattern Micro | 1. 15+ AWS competencies 2. Assault floor effort administration 3. Extended detection & response 4. Proactive possibility protection |
| 7. Sophos | 1. Infrastructure Visibility 2. Exact compliance 3. DevSecOps instruments 4. Amazon Linux give a steal to 5. Workload and recordsdata security |
| 8. McAfee | 1. RDP security enhancement recommendationsââ. 2. VPN with grand 256-bit AES encryptionââ. 3. Identification monitoring for non-public informationââ. 4. Compliance assistance, Info Security 5. Threat security and visibility facets. |
| 9. Cisco Methods | 1. Integrated security products and services 2. Cloud workload security 3. Bring together community connectivity 4. firewall security, intrusion prevention systems 5. cloud security solutions |
| 10. F5 Networks | 1. Multi-cloud provider consistency 2. Bring together AWS workloads 3. Simplified application migration 4. Auto Scaling and High Availability 5. Multi-Zone Availability |
Most attention-grabbing AWS Network Discover admission to Security Companies – 2024
- Perimeter 81
- Amazon Web Services (AWS) Security
- Palo Alto Networks
- Fortinet
- CheckPoint
- Pattern Micro
- Sophos
- McAfee
- Cisco Methods
- F5 Networks
1. Perimeter 81
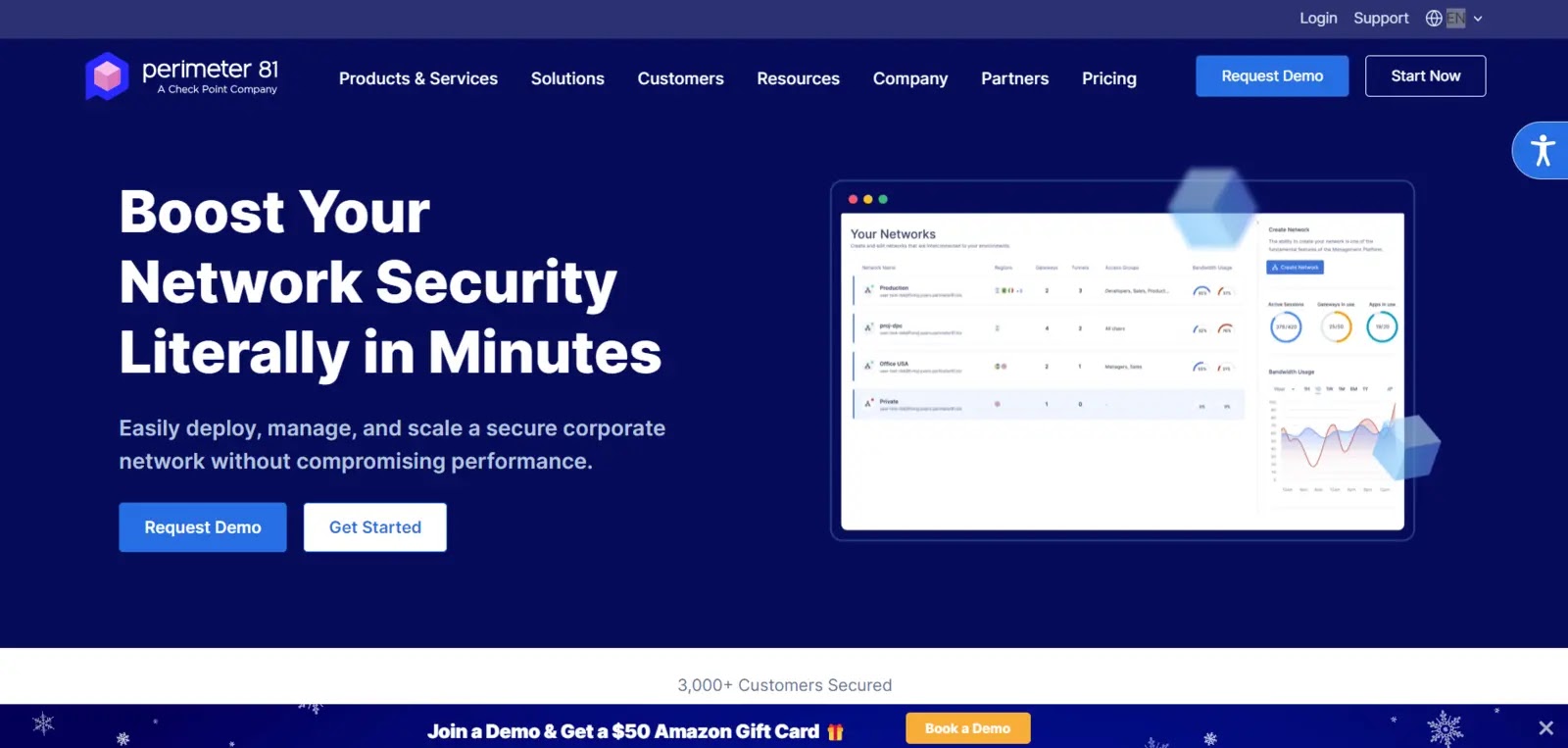
Boosts efficiency with a versatile cloud-edge setup, continuous security surveillance, detailed AWS collect admission to tracking, high quality site visitors encryption, and treasured insights from analytics to detect community risks.
Empower users to send knowledge aloof on their networks to their Amazon S3 bucket and enhance collect admission to controls to enact explicit switch and compliance targets.
Empower organizations to gather admission to cloud resources effectively and securely from any design worldwide.
Get of living up a design-to-design IPSec connection between your AWS resources and the Perimeter 81 community to originate a stable and legit communication hyperlink for the team to work remotely.
Evolved monitoring entails analytics and recordsdata managed by security experts to assist detect anomalies from routine events.
Parts
- Steer clear of wasting time on pointless signals with round the clock AWS cloud security monitoring and knowledgeable administration.
- Perimeter81 monitoring machine entails analytics and recordsdata managed by our security experts to portray you how to pickle any irregularities amongst customary events.
- It’s foremost to comprise correct tournament logs and continuous monitoring to make sure compliance with requirements.
- When accounts are left unsecured, cybercriminals can without complications collect admission to cloud resources and navigate via the company community. One technique to take care of this area is by limiting permissions to the minimum foremost stage.
- Transitioning to AWS could per chance per chance per chance appear overwhelming. We’ll dispute up our security infrastructure rapid to present protection to your company knowledge.
| Pros | Cons |
|---|---|
| Enables least privilege collect admission to | It could well most likely per chance per chance per chance require technical skills to setup |
| Saves money utilizing AWS knowledge centers | Restricted knowledge on give a steal to quality |
| Will increase productivity |
2. Amazon Web Services (AWS) Security
%20Security.webp)
Utilizing Network and Application Protection on AWS permits you to without notify enlarge inspection and security facets to produce definite the continuous availability of workloads without desiring to accommodate infrastructure administration.
Toughen the community and application security on AWS with valid-time site visitors visibility, taking into story intellectual-grained filtering, monitoring, and logging no subject the port or protocol.
Gives assist an eye on over site visitors float to forestall unauthorized collect admission to, capability weaknesses, performance complications, and recordsdata breaches.
This entails safeguarding against approved web assaults, blocking knowledge transfers via depraved DNS queries, and enforcing developed DDoS protections for protecting web applications.
Managing firewall rules and security tournament reporting on AWS is centralized, making it more uncomplicated to make sure protection compliance across the factors of the machine.
Parts
- Supervises encryption keys and user collect admission to.
- Gives possibility detection that constantly keeps an ogle out for suspicious or illegal activities.
- Protects against Disbursed Denial of Carrier (DDoS) assaults with managed products and services.
- Checks programs robotically for security flaws or non-normal habits.
- A web application firewall can assist assist malicious websites and their apps stable from frequent on-line assaults.
| Pros | Cons |
|---|---|
| True-time site visitors monitoring | Capability for prime prices |
| Comprehensive possibility protection | Requires AWS ecosystem integration |
| Unified firewall rule administration |
3. Palo Alto Networks

Palo Alto Networks is explicitly designed for Amazon Web Services (AWS) environments and presents a subsequent-generation firewall provider is called Cloud NGFW for AWS.
For deployment interior AWS Digital Personal Clouds (VPCs), it’s a cloud-native resolution that can additionally be bought via the AWS Marketplace.
Explicitly designed to safeguard AWS cloud infrastructures, this provider provides predominant Subsequent-Generation Firewall (NGFW) performance equivalent to App-ID, URL filtering, SSL/TLS decryption, and extra.
It permits enterprises to withhold a solid security posture extra effectively whereas embracing the benefits of cloud computing by simplifying the maintenance of security rules.
It integrates seamlessly with AWS products and services to originate visibility and assist an eye on over site visitors, ensuring grand security against risks without compromising AWS’s flexibility and scalability.
Parts
- A resolution for community and security products and services that provides stable collect admission to at the provider edge (SASE).
- Protects applications against capability dangers by making them apparent and controllable.
- Items Prisma Cloud, a resolution that provides whole security for cloud workloads.
- It makes use of machine studying to beat back each known and unknown dangers.
- Monitors for and blocks newly figured out malware in valid time.
| Pros | Cons |
|---|---|
| Integrates with AWS VPC | Imprint could per chance per chance per chance be high |
| Scalable security | studying curve for tag new users |
| Simplified deployment |
4. Fortinet

Gives a differ of security solutions that seamlessly combine with AWS to snarl thorough possibility security for networks, applications, and platforms.
The endeavor-grade entirely managed subsequent-generation firewall-as-a-provider that FortiGate CNF on AWS Network Discover admission to Security Operations.
With usage-basically based mostly licensing, FortiFlex permits agencies to settle how a lot to express on AWS and hybrid atmosphere security and what measurement provider to make use of.
The Fortinet Security Cloth without lengthen interfaces with AWS to originate whole and entirely customizable multilayer security and possibility-prevention capabilities.
Organizations could per chance per chance per chance originate consistent security in a shared responsibility model with the assist of Fortinet cloud security solutions for AWS settings.
Parts
- Gives sophisticated security facets, alongside side deep packet inspection.
- Gives cloud-basically based mostly networking and security products and services.
- Keeps apps stable by fixing the OWASP High 10 vulnerabilities and other security flaws.
- A security broker for cloud collect admission to that protects from threats, knowledge security, compliance, and transparency.
- It boosts security and connectivity to the cloud by allowing americans to securely collect admission to the gain without lengthen.
| Pros | Cons |
|---|---|
| Scalable for plenty of sizes | It could well most likely per chance per chance per chance be complicated to configure |
| Sturdy community performance | Fees could per chance per chance per chance be high for little agencies |
| Seamless AWS integration |
5. CheckPoint
To produce the cloud migration assignment stable and straight forward, CheckPoint and AWS eradicated security barriers.
Customers’ workloads are safeguarded utilizing CloudGuard, whether or no longer hosted on-design, in a non-public cloud, or on AWS AWS Network Discover admission to Security.
combating, detecting, and correcting security misconfigurations is foremost for an efficient endeavor cloud security device.
Cloud infrastructure have to follow global, federal, dispute, and native security regulations. Utilize atmosphere pleasant, automated compliance and governance processes across all public cloud environments.
Streamline incident prognosis for configurations, posture, community site visitors, and id express. Automate continuous intrusion detection, monitoring, and possibility intelligence.
Parts
- Gives public and hybrid cloud users grand possibility prevention capabilities with cloud-native security.
- Provide protection to against complicated assaults, zero-day vulnerabilities, and malware that hasn’t yet been figured out.
- Gives first-price security whereas working without problems.
- Contains endpoint security, possibility looking out, and remediation in its whole offering.
- A whole structure for community, cloud, and cell security to forestall cyberattacks from Generation V.
| Pros | Cons |
|---|---|
| Comprehensive security protection. | Imprint is mostly a consideration for smaller organizations. |
| Easy deployment and scalability interior AWS environments. | Complexity in configuration and administration for users uncommon with security or AWS. |
| Sturdy give a steal to for compliance and recordsdata security. |
6. Pattern Micro
Empower the administration of cyber risks by utilizing hybrid cloud security that emphasizes figuring out interior and exterior assault surfaces, evaluating risks, prioritizing them, and enforcing solutions.
Toughen the capability to thwart threats extra effectively by gaining a whole take a look at and deeper insights to title, observe, analyze, and take care of security breaches via personalized hybrid cloud knowledge correlation.
detect, take care of, and arrange security risks within the hybrid cloud setup utilizing valid-time security systems for VMs, containers, storage, VPCs, IACs, repositories, databases, and APIs.
Pattern became chosen because the principle security partner in AWS Managed Services, making improvements to cloud adoption for enterprises and simplifying each day cloud operations, alongside side crucial security responsibilities provided by Pattern.
Parts
- A platform that provides security products and services to cloud builders, alongside side security for workloads and containers.
- Ensures the safety of servers within the cloud, on-premises, and almost.
- This endpoint security resolution presents enhanced automated possibility detection and response capabilities.
- Strengthens the defenses against threats and recordsdata breaches for SaaS applications.
- Gives security and transparency in a hybrid cloud environment.
| Pros | Cons |
|---|---|
| Sizable security protection | Complexity for tag new users |
| Assault floor administration | Capability ticket implications |
| Rapidly possibility response |
7. Sophos
Take a look at the AWS Network Discover admission to Security environments to within the discount of the notify of capability threats, take care of security vulnerabilities, and make sure adherence to regulations.
Provide protection to firm knowledge and infrastructure with adaptable host and container workload security this day and sometime.
Originate definite that the least privilege is utilized during the AWS environments and proactively arrange the AWS identities to forestall exploitation.
Utilize SophosLabs Intelix APIs to originate stable web applications that robotically take a look at for threats and habits anti-malware scans.
Utilizing a single pre-configured Amazon EC2 instance combines several switch-main security solutions to defend the hybrid cloud environments against community assaults.
By utilizing a combination of machine studying, developed analytics, and rule-basically based mostly matching approaches, Sophos NDR constantly analyzes each encrypted and unencrypted community site visitors to title suspicious actions that will per chance per chance per chance be signs of attacker express.
Parts
- Progressive endpoint security utilizing deep studying structure.
- Gives advancements in firewall visibility, security, and response for subsequent-gen security.
- All Sophos merchandise could per chance per chance per chance be managed on a single platform.
- AI powers cloud security and visibility for public cloud platforms, alongside side Google Cloud, Azure, and Amazon Web Services.
- Bring together electronic mail gateway within the cloud that blocks malicious, unsolicited mail, and phishing emails.
| Pros | Cons |
|---|---|
| Extensive AWS integration | Complexity in setup for rookies |
| Single console administration | Capability for better prices with developed facets |
| Exact compliance and guidance |
8. McAfee
Emphasizes offering whole cybersecurity solutions love VPN, antivirus, and id and privacy security products and services.
Providing security against viruses, web fraud, and id theft utilizing AI-powered applied sciences, merchandise are geared in direction of customers and households.
Services equivalent to valid-time machine security, web privacy via VPNs, non-public knowledge cleanup, and id theft protection and restoration meet so a lot of cybersecurity requires.
Parts
- A cloud collect admission to security broker (CASB) presents knowledge security for all cloud products and services.
- It presents Windows and cell users with cutting-edge possibility security.
- Evolved possibility security for hybrid instances with subsequent-gen IPS technology.
- Gives dwell-to-dwell solutions for protecting websites.
- Avoids the loss, misuse, or alteration of confidential knowledge kept within the cloud, on-premises, and in transit.
| Pros | Cons |
|---|---|
| User-pleasant VPN experienceââ. | performance impression on devices |
| Efficient id monitoring alertsââ. | complexities within the user interface |
| Comprehensive customer supportââ. |
9. Cisco Methods

Cisco and AWS comprise joined forces to simplify the cloud scoot for agencies, constructing have confidence, minimizing complexity, and encouraging innovation.
The tool-defined repeatable blueprints, uniform global footprint, and grand framework that AWS and Cisco offer are foremost for connecting hybrid cloud systems, streamlining cloud migration, and enabling staff to work remotely securely.
To safeguard knowledge this day and sometime, enterprises can use Cisco Security on AWS to develop visibility and assist an eye on during their AWS atmosphere.
Toughen the on-premises setups by migrating to AWS with high-notch security facets and participating in ticket financial savings via versatile subscription pricing.
Purpose Cisco Cyber Imaginative and prescient from the AWS cloud to enhance visibility into the commercial security posture and OT sources.
Parts:
- Security platform within the cloud that provides DNS-layer security, a firewall, a stable web gateway, and CASB capabilities.
- Entire security against threats at every stage of an assault.
- Blockading malware at its entry point and combating breaches is the blueprint of endpoint security.
- Application security within the cloud with multi-notify authentication (MFA).
- A whole, automated security platform that spans all Cisco security merchandise, taking into story whole visibility.
| Pros | Cons |
|---|---|
| Evolved possibility security | It could well most likely per chance per chance per chance be complicated to configure |
| Extensive community protection | Requires technical skills |
| Legitimate cloud infrastructure |
10. F5 Networks
To bustle up cloud migrations, safeguard cloud apps, and enhance the user ride with AWS cloud products and services, F5 presents a whole portfolio that operates during the hybrid cloud property.
Attach uniformity in provider shipping across all of the applications in a pair of cloud environments. Streamline application shipping utilizing versatile container environments.
Make perception and in-depth knowledge for AWS applications in a single handy location. Shield the applications against customary assaults without requiring updates to the apps.
Originate definite, streamline, and consolidate user collect admission to to apps, APIs, and recordsdata.
Instant deploy, stable, and arrange applications across assorted cloud platforms utilizing a unified tool stack and administration portal.
Provide protection to the apps and community from encrypted threats that can infiltrate via so a lot of assault points across assorted layers.
Parts
- Makes definite apps can kind out fluctuations in quiz by spreading them out over a pair of servers.
- Keeps applications stable against bot assaults and on-line vulnerabilities.
- To enhance application performance, site visitors is dispensed amongst servers.
- It makes it more uncomplicated to deploy F5 solutions in AWS settings robotically and constantly.
- Ensures high availability by allowing deployment across AWS Availability Zones.
| Pros | Cons |
|---|---|
| Automates application shipping | Complexity in deployment |
| Enhances app security | It could well most likely per chance per chance per chance require in actuality good skills. |
| Gives detailed analytics |
Conclusion
Cloud settings could per chance per chance per chance be better stable from the ever-changing cyber possibility landscape with the assist of AWS Network Discover admission to Security Companies’ whole differ of solutions.
Companies in this home offer so a lot of solutions for securing cloud resources and recordsdata, alongside side intrusion prevention systems, developed firewalls, and id and collect admission to administration systems.
The auto-scaling, developed possibility security, and cloud-native security facets they offer are foremost for firms facing cloud security challenges.
Organizations could per chance per chance per chance enhance their cloud infrastructure’s vulnerability to threats and compliance with regulatory requirements through the use of these modern guidelines on how to develop visibility, assist an eye on, and security across all AWS deployments.
FAQ
Retaining knowledge and applications hosted on AWS from cyber assaults is the area of skills of AWS Network Discover admission to Security Companies. Web application firewalls (WAFs), intrusion detection systems (IDPSs), and compliance administration instruments designed for AWS environments are amongst the cloud-native security products and services they offer.
Many services offer free trials or demo variations of their products and services, allowing you to review their facets and usability sooner than making a financial commitment. Take a look at each firm’s web pages for trial alternatives or contact their sales team for extra knowledge.
Finding the upright security provider relies in your requires, funds, and compliance. Rob into story the records you offer protection to, your organization’s measurement, AWS complexity, and regulatory necessities. Overview each firm’s merchandise, customer rankings, and case experiences to assess their performance.
Also Read:
10 Most attention-grabbing Automatic WiFi Security Suppliers â 2024
10 Most attention-grabbing Network Security Suppliers for Govt Sectors â 2024
High 10 Most attention-grabbing Network Security Solutions for IT Managers â 2024
High 10 Most attention-grabbing DDoS Protection Tools & Services â 2024
10 Most attention-grabbing Bring together Network As a Carrier for MSP Suppliers â 2024
10 Most attention-grabbing Network Security Suppliers for Training Sectors â 2024
10 Most attention-grabbing Bring together Network as a Carrier (NaaS) for MSSP Suppliers â 2024
High 10 Security Carrier Edge (SSE) Solutions for Network Security â 2024
Source credit : cybersecuritynews.com






