10 Best Firewall as a Service (FWaaS) Providers – 2024
Firewall as a Carrier (FWaaS) is an emerging security model in cloud computing and network security. It represents a shift from venerable, on-premise firewall alternate choices to cloud-based entirely firewall providers and products.
Firewalls as Carrier Suppliers (FWaaS) are pillars of enterprise network security.
It keeps an discover on both incoming and outgoing network site traffic, permitting or blocking knowledge packets based entirely on its security insurance policies.
Its purpose is to originate a wall between your within network and placement traffic from outside networks, such because the remainder of the web. this prevents malicious site traffic, at the side of that of hackers and viruses.
Desk of Contents
What’s a firewall as a service?
Which providers and products does the firewall provide?
Is the firewall IaaS or PaaS?
10 Excellent Firewall as a Carrier Suppliers
1.Perimeter81 Firewall as a Carrier
2.Test Level Next Period Firewalls (NGFWs)
3.Zscaler Web Access
4.Palo Alto Networks’ Next-Period Firewall
5.CrowdSec
6.Sophos Firewall
7.FortiGate NGFW
8.ZoneAlarm Free Firewall
9.Cisco Real Firewall
10.Barracuda CloudGen Firewall
10 Excellent Firewall as a Carrier Suppliers (FWaaS) Aspects
Often Requested Questions
Also Learn
What’s a Firewall-as-a-service?
Firewall as a Carrier (FWaaS) moves firewall efficiency to the cloud as an different of the venerable network perimeter.
By leveraging cloud computing, an group can reap a total lot of financial, network efficiency, and security advantages.
Firewalls were in the starting up build developed to safeguard native company networks, however firewalls had to swap as more companies migrated their knowledge and applications to the cloud.
Firewalls can now be supplied as a element of a company’s cloud infrastructure due to the “firewall as a service,” or FWaaS.
It has some determined advantages, love the ability to scale nearly immediately to accommodate a growing network.
Which providers and products does the FWaaS Offers?
The firewall affords the following providers and products:
- Static-packet filtering:It is some distance a firewall with routing capabilities that can filter packets per the packet’s fields and the foundations build of abode up by the administrator.
- Circuit-degree firewalls: It serves as a handshaking mechanism for depended on possibilities, servers, and untrusted hosts.
- Proxy server: System for network security that defends utility-layer message filtering.
- Utility server: It defends web applications against a substantial want of utility layer assaults, at the side of sinful-blueprint scripting (XSS), SQL injection, etc.
- NAT: Many firewalls own a characteristic called network address translation (NAT) that converts between within and external IP addresses.
- Stateful packet inspection: Dynamic packet filtering chooses which network packets to allow thru the firewall while keeping an discover on active connections.
Is the Firewall IaaS or PaaS?
A platform-as-a-service (PaaS) or infrastructure-as-a-service (IaaS) model is used to flee digital firewalls, which are cloud-based entirely providers and products which are created to flee in a digital knowledge center using your individual servers.
The firewall utility, which runs on digital servers in these conditions, protects site traffic to, from, and between cloud applications.
IaaS/PaaS permits you to originate, provision, and organize your individual digital servers using infrastructure that you hire from a service supplier.
The commercial generally makes exercise of the term “next-technology firewalls” to list any stepped forward firewall machine that runs on-premises or in the cloud, though it’s no longer consistently utilized in that sense.
How discontinue you Establish the Excellent Firewall as a Carrier Suppliers?
When choosing a Firewall as a Carrier (FWaaS) supplier, it’s serious to reasonably steal into consideration varied factors to make certain that you bag the service that nearly all efficient meets your explicit requirements. Here’s a scientific attain to lend a hand you to in making a smartly-suggested decision:
Resolve Your Security Wants:
- Evaluate the out of the ordinary security requirements of your group. Take into accout the scale of your network, the kind of devices linked, and the sensitivity of the knowledge you organize.
- Assess the mandatory degree of security. As an illustration, corporations that address silent knowledge could perchance presumably require stronger security parts.
Uncover Capacity Suppliers:
- See out providers who own established themselves as leaders in the self-discipline. Assess their ancient previous of dependability and customer contentment.
- Rob a stare upon opinions and case analysis to attain insights into how they’ve efficiently assisted other companies, namely other folks which are identical to yours.
Assess the Characteristic Say:
- Be obvious that that the FWaaS involves all of the mandatory parts similar to intrusion prevention, anti-virus, web filtering, utility preserve watch over, and VPN capabilities.
- Eye for stepped forward parts similar to AI-driven threat intelligence, sandboxing, and seamless integration with other security instruments.
Making improvements to Scalability and Flexibility:
- The FWaaS must be without danger scalable to address the rising wants of your commercial.
- It would aloof even own the flexibility to without danger adjust to evolving security requirements and developments in technology.
Guaranteeing Compliance and Keeping Recordsdata Privacy:
- Be obvious that the supplier adheres to the mandatory guidelines and requirements which are connected to your commercial, similar to GDPR and HIPAA.
- Carry out insight into their attain to knowledge administration, at the side of their knowledge center locations and privateness insurance policies.
Guaranteeing optimal efficiency and reliability:
- Evaluate the discontinue of the firewall on the tempo and latency of your network.
- Be obvious that that you mediate about out assurances of high availability and reliability, on the entire outlined in the Carrier Level Agreements (SLAs) supplied by the service providers.
Assistance and Buyer Care:
- Efficient customer help is a need to-own. Please make certain that you test the accessibility and promptness of the help providers and products.
- See out providers that supply in depth practising and resources to your crew.
Elements to Withhold in Mind When Evaluating Costs:
- Look the pricing devices supplied by varied providers. It’s primary to be attentive to any extra expenses that can perchance perchance no longer be immediately obvious.
- Take into accout the total stamp of ownership, which encompasses setup, upkeep, and any extra functionalities.
Exploring Trial Courses and Demos:
- Be obvious that to murder the most of trial periods or interrogate demos to steal into consideration the service to your explicit setup.
- Rob honest correct thing about this opportunity to evaluate the user-friendliness and compatibility along with your present infrastructure.
Uncover Suggestions and References:
- Join with colleagues to your self-discipline to amass suggestions.
- Question customer references or case analysis from providers.
10 Excellent Firewall as a Carrier Suppliers (FWaaS) Aspects
| Firewall as a Carrier Provider | Key parts |
|---|---|
| 1. Perimeter81 Firewall as a Carrier | 1. The integrated Perimeter81 FWaaS manages each and each network resource, user, and surroundings. 2. Resulting from it guarantees that IT has an instantaneous line-of-gape with all company knowledge, both at relaxation and in transit, Perimeter81 Firewall as a Carrier is noticeable. 3. Because it specifies the explicit pointers for when and the design in which site traffic is allowed to tear within your networks, Perimeter81 is granular. 4. As the commercial expands, Perimeter81 FWaaS swiftly-witted creates, modifies, and applies network site traffic insurance policies. 5. A very necessary resources to your organization could perchance even be fully monitored and secured from a single dashboard. |
| 2. Test Level Next Period Firewalls (NGFWs) | 1. Defend against cyberattacks using your department’s SD-WAN cloud connection. 2. Test Level NGFW has stable security because of it affords the ideal threat prevention that you’re going to be ready to mediate of with SandBlast Zero-Day protection. 3. Since managing and configuring network security environments and insurance policies is made easy by CheckPoint NGFW’s SmartConsole, it has unified administration. 4. When customers are out of the workplace or working remotely, give them ranking, seamless entry to the corporate’s networks and resources. 5. Some distance-off customers can join without interruption due to the CheckPoint NGFW’s some distance away entry VPN. |
| 3. Zscaler Web Access | 1. enhances the user experience by providing fixed, swiftly, and ranking connections across all ports and protocols. 2. To title and conclude explicit, focused threats, originate personalized IPS signatures and rapidly deploy them using Laugh syntax. 3.The exercise of centralized policy administration, originate flexible entry insurance policies for cloud providers and products and PaaS/IaaS. 4. Detect and conclude evasive and encrypted cyber threats as rapidly as they seem in site traffic on out of the ordinary ports. 5. In addition to asserting superior efficiency, localized resolutions give protection to your customers and endpoints from malicious websites and DNS tunneling. |
| 4. Palo Alto Networks Next-Period Firewall | 1. Your organization’s platform is protected, despite its complexity or dimension. 2. To dam entry to offensive websites, outbound connections could perchance even be filtered. 3. For thousands of department areas of work, allow Zero Belief Network Security with streamlined security. 4. Whereas analyzing site traffic, guard against known vulnerability exploits, malware, spyware, and malicious URLs. 5. A PAN-OS digital occasion running on a VM-Sequence firewall is ready for exercise in a virtualized knowledge center surroundings. |
| 5. CrowdSec | 1. Test the security of your server, receive notifications of strange exercise, and bag IP address intelligence. 2. Every time an IP is blocked, the entire community is notified in notify that they are able to all block it as smartly. 3. CrowdSec adds knowledge, such because the origin country, the self sustaining machine, and other info, to the knowledge by utilizing resources from outside sources. 4. With a single CLI negate, you are going to be ready to join the Console to your present CrowdSec Agent installations. 5. Resolve which IP address and assault manner are used to assault your providers and products. |
| 6. Sophos Firewall | 1. Straight away recognizes and isolates infected programs per incidents so as that they would perchance perchance even be cleaned up. 2. With swiftly and surroundings pleasant brilliant TLS inspection, a most necessary blind shriek could perchance even be removed. 3. You obtain preserve watch over of your networks by having better visibility into bad exercise, suspicious site traffic, and cutting-edge threats. 4. For all of your Firewalls, Sophos Central affords efficient centralized administration, reporting, and nil-touch deployment. 5. With alternate choices for isolation, bridging, zones, hotspots, channel width, and more than one SSIDs per radio, flexible configuration is possible. |
| 7. FortiGate NGFW | 1. Whereas also adjusting to the threat panorama, it could perchance conclude malware and other types of assaults. 2. To title and conclude threats, gaze customers, devices, and applications, even once they are encrypted. 3. With entirely integrated networking capabilities, similar to SD-Branch, SD-WAN, and 5G, you are going to be ready to join and give protection to any edge at any scale. 4. With the integrated FortiGuard IPS, you are going to be ready to win digital patching and protection from known and nil-day assaults. 5. Beef up your surroundings’s operational efficiency while supporting overworked IT teams. |
| 8. ZoneAlarm Free Firewall | 1. It detects and prevents web assaults while keeping an discover out for packages that display suspicious habits. 2. Actively defends against both incoming and outgoing cyberattacks. 3. Offers you with a day-to-day notification of any changes to your credit ranking document, which continuously signify identity theft. 4. Your PC can resolve whether it’s running a ranking working machine or a doubtlessly contaminated rootkit with Early Boot Protection. 5. Gets rid of doubtlessly contaminated parts from downloaded recordsdata, similar to macros, embedded objects, and other contaminated jabber, using Zero-Day Protection. |
| 9. Cisco Real Firewall | 1. For scenarios where static IP addresses are no longer accessible, Cisco’s dynamic attributes help VMware, AWS, and Azure tags. 2. That you just may perchance without danger and consistently organize insurance policies across all of your Cisco Real firewalls with cloud-based entirely firewall administration. 3. By combining the logs from all Cisco Real Firewalls, you are going to be ready to meet your compliance requirements. 4. Fixed visibility and policy enforcement for dynamic applications across the network. 5. In scream to originate a extremely elastic, cloud-native infrastructure, Real Firewall Native Cloud is a solution that’s developer-pleasant. |
| 10. Barracuda CloudGen Firewall | 1. Your security infrastructure’s configuration and upkeep are simplified by the Barracuda Firewall Withhold a watch on Center. 2. It is possible you’ll perchance perchance bag all of the brilliant knowledge you wish to own security with Barracuda Firewall Insights. 3. Your organization network can be seamlessly linked, and reports and analyses can be compiled. 4. Developed utility-based entirely routing route different and Quality of Carrier (QoS) capabilities are supplied by the Barracuda CloudGen Firewall. 5. Person-defined utility definitions could perchance even be rapidly created using the Barracuda CloudGen Firewall. |
10 Excellent Firewall as a Carrier Suppliers in 2024
- Perimeter81
- Test Level Next Period Firewalls (NGFWs)
- Zscaler Web Access
- Palo Alto Networks’ Next-Period Firewall
- CrowdSec
- Sophos Firewall
- FortiGate NGFW
- ZoneAlarm Free Firewall
- Cisco Real Firewall
- Barracuda CloudGen Firewall
1. Perimeter81 FWaaS
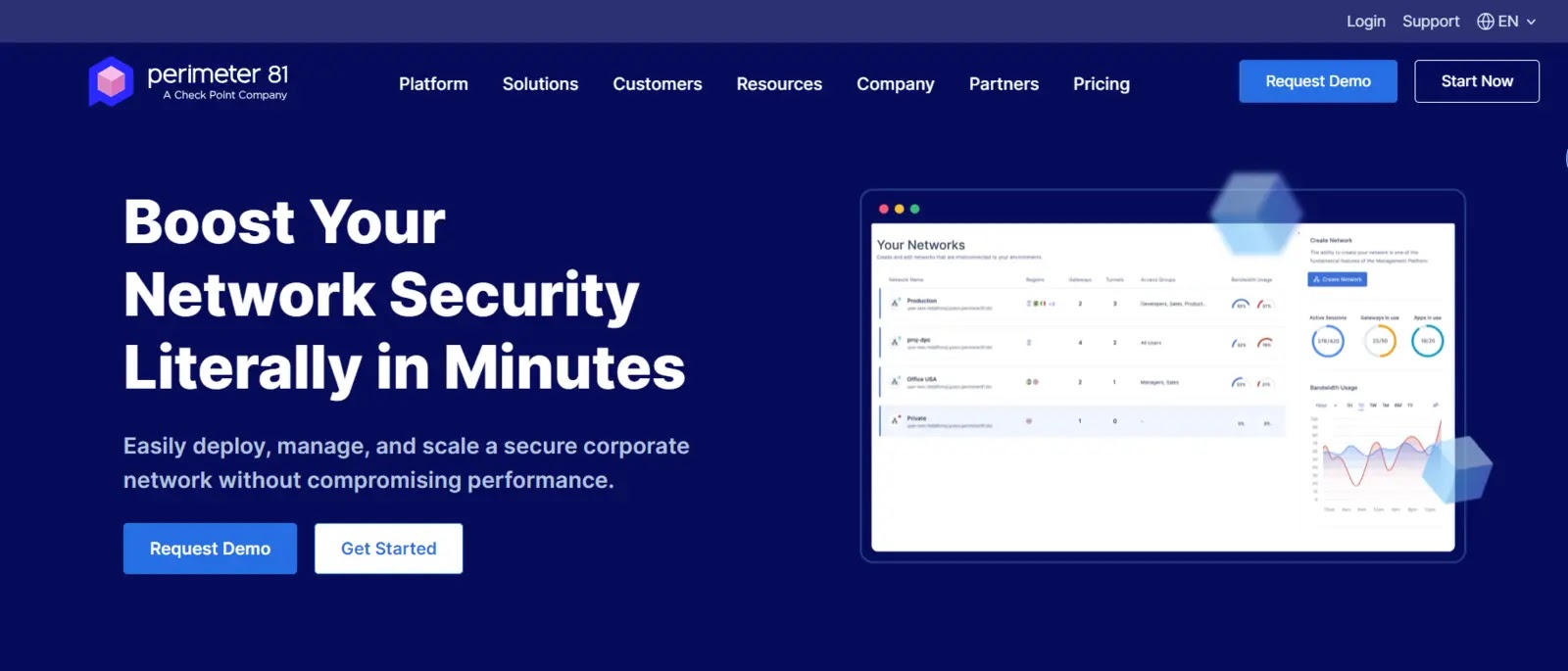
The Perimeter81 security machine platform involves the firewall-as-a-service (FWaaS) utility, which is accessible in a fluctuate of configurations.
Firewall as a Carrier, supplied by Perimeter 81 as phase of their Network as a Carrier platform, permits you to centralize the inspection of network site traffic and conclude unauthorized entry to your group’s resources within a single, cloud-based entirely shriek.
With Perimeter81, a mixture of entry rights administration and connection security, some distance away employees could perchance presumably safely join to the cloud without going thru your native build network.
Perimeter81 creates a non-public, encrypted digital network that comprises all of your websites and online providers and products.
All incoming and outgoing site traffic to your unified network could perchance presumably then be scanned by turning on the firewall as a service.
Perimeter81 tends to center of attention security protection on particular person apps somewhat than entire programs; the FWaaS will supplement lovely-grained fence with machine-broad security.
Aspects
- A central blueprint for surroundings and managing firewall principles across networks.
- Without danger surroundings apart and splitting network sections for security and administration.
- Managing networked packages and defining utility-degree firewall principles.
- Filtering controls incoming and outbound site traffic per predefined principles.
- Substandard habits is monitored and averted to forestall threats.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| The Perimeter 81 solution is drastically more stamp efficient than a hardware firewall. | It could perchance perchance be total with a instrument-defined network service that makes exercise of IP address overlays. |
| It permits the collection of site traffic knowledge by going surfing to its servers. | There is no such thing as a native client handbook configuration accessible to Linux customers. |
| Detailed preserve watch over over the providers and products and actions that each and each user could perchance presumably entry. | To present the utility a more brilliant feel, the UI could perchance also very smartly be as a lot as this point and improved overall. |
| A service that’s easy to exercise. |
2. Test Level Next Period Firewalls (NGFWs)

Test Level’s next-technology firewalls (NGFWs) are amongst the most brilliant and straight forward alternate choices in the marketplace.
Test Level NGFW, a next-technology firewall, limits entry to malicious packages while letting respectable ones thru, ensuring that customers can exercise the web with peace of mind.
It comprises stepped forward malware prevention parts love sandboxing, utility and user controls, and integrated intrusion prevention (IPS).
Test Level’s NGFW used to be designed with 23 out of the ordinary firewall varieties to allow for simultaneous operation of many types of threat prevention. Elephantine SSL inspection is a phase of this, and it has no discontinue on both efficiency or security.
Test Level’s NGFWs, or Next-Period Firewalls, type out enhancing technologies that conclude threats, similar to debugging on the CPU degree and blocking ransomware.
Furthermore, it affords the most stepped forward and efficient protection all over all parts of the network, safeguarding customers from hazard despite where they would perchance perchance also very smartly be.
Aspects
- Elephantine security is carried out by inspecting encrypted knowledge to video display concealed risks.
- Segmenting the network makes it safer and simpler to own.
- Without danger configure, be aware, and document on the entire security structure with a single administration console.
- Detail-oriented logging and reporting of network site traffic, security incidents, and compliance wants.
- Integration with automation and administration platforms to streamline security operations and responses.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| Extra ranking than any Next Period Firewall (NGFW). | It is some distance serious to steal the customary and accessibility of practising. |
| Test Level NGFW is ranked fourth amongst the pinnacle alternate choices. | After each and each module/blade is enabled, the firewall’s throughput or efficiency is drastically reduced. |
| The Office VPN is one among the many counseled parts. | Generally CLI doesn’t display all of the connections. |
| Enables customers who are working remotely to join without any considerations. |
3. Zscaler Web Access
Zscaler Web Access is the market-main cloud-native security service edge (SSE) technology, defining what it attain to own ranking, swiftly web and SaaS entry.
Zscaler Cloud Firewall affords rapidly, ranking on- and off-network connections and native web breakouts for all user site traffic without requiring you to preserve watch over any hardware or instrument.
Zscaler Cloud Firewall affords the most entire cloud-native security service edge (SSE) platform accessible, ensuring that all customers, applications, and locations could perchance presumably safely and securely entry the web.
Zscaler Cloud Firewall ensures that you’re going to be ready to safely entry the web by managing all types of site traffic across all ports and protocols with limitless elasticity and unmatched efficiency.
When utilizing the Zscaler service to entry the web, no personally identifiable knowledge is recorded or kept.
Easiest while linked to the distance of industrial network will your site traffic be scanned for risks.
Zscaler Cloud Firewall, on the side of Zscaler Web Access and the Zscaler Zero Belief Alternate, affords unparalleled security and value.
Aspects
- Offers a cloud-based entirely firewall to position in force security insurance policies, restrict app entry, and block unauthorized network site traffic.
- Displays and restricts network knowledge transmissions to guard non-public knowledge.
- Administrator-build of abode principles preserve watch over web pages and jabber workforce entry. This enforces principles and blocks hazardous stuff.
- It affords a total characterize of user exercise, utility exercise, and security incidents thru consolidated dashboards and records.
- employs a network of recordsdata centers to present web possibilities in diversified locations the ideal tempo and lowest latency.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| Infiltrate evasive site traffic on out of the ordinary ports. | Developing a world group with gash up-off locations using separate SD WAN circuits is necessary. |
| World edge presence protection delivered thru the cloud. | If a connection is lost, customers must be notified. |
| Without sacrificing efficiency, ranking DNS. | Web blueprint entry is somewhat too unhurried when Zscaler monitoring is enabled. |
| Total security for customers who work from any place. |
4. Palo Alto Networks Next-Period Firewall
.webp)
Palo Alto Networks’ Next-Period Firewalls (NGFW) exercise stepped forward site traffic identification, malware prevention, and threat intelligence technologies to present security teams beefy negate and preserve watch over of all networks.
With CEF integration, Palo Alto Networks firewalls could perchance presumably originate logs in the CEF format for site traffic, threats, programs, settings, and HIP fits.
They’ve a unified network security structure and exact-time deep learning of their firewalls, so you are going to be ready to be aware and give protection to your entire machine.
In phrases of vetting other folks, applications, and jabber, Palo Alto NGFWs provide enterprises with a broad kind of cutting-edge security instruments and methodologies.
By utilizing three determined identifying technologiesâApp-ID, Person-ID, and jabber-IDâPalo Alto Networks’ next-technology firewalls allow companies to be aware and preserve watch over entry to all types of recordsdata.
Aspects
- Lets you zone the network for better administration and security.
- Enables department areas of work and some distance away customers to securely join thru VPN.
- A single-pane-of-glass administration console simplifies policy administration, monitoring, and security infrastructure reporting.
- Integration with automation and administration platforms to streamline security operations and responses.
- Elephantine logging and reporting negate network activities, security events, and compliance wants.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| ideal to your hybrid, public, and non-public cloud computing environments. | Quite more simplicity would motivate with the World Defend VPN setup. |
| Real varied public cloud environments with the identical degree of security as knowledge centers which may perchance well perchance perchance be found on-blueprint. | Limited companies with diminutive resources can no longer own sufficient money it. |
| By establishing decryption insurance policies per URL category, SSL Inspection used to be very manageable. | It is some distance essential to combine it into a longtime network. |
| seamlessly integrates with instruments and programs from third parties. |
5. CrowdSec
CrowdSec, a free and launch-supply multi-user firewall, makes exercise of IP reputation and IP habits diagnosis.
To shield your online providers and products, title and reply to threats, and block rogue IPs, CrowdSec affords a crowd-based entirely cyber security package called TIP.
Extremely curated knowledge on intrusion attempts, sources, and traits is made accessible to SOC teams and security analysts thru the distribution of CrowdSec CTI’s IP reputation intelligence.
Threats, notifications, remediation alternate choices, and suspicious IP habits could perchance presumably all be seen in a graphical dashboard when the console is linked to CrowdSec Agent.
It displays machine and utility logs for suspicious exercise after which implements remediation of any type (multi-element authentication, captchas, and even a easy fall) and at any layer (firewall, reverse proxy, etc.).
It analyzes user actions and affords out of the ordinary protection from all threats.
Customers can exercise the product for self-defense as smartly.
Aspects
- Lets you zone the network for better administration and security.
- Enables department areas of work and some distance away customers to securely join thru VPN.
- A single-pane-of-glass administration console simplifies policy administration, monitoring, and security infrastructure reporting.
- Integration with automation and administration platforms to streamline security operations and responses.
- Elephantine logging and reporting negate network activities, security events, and compliance wants.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| Tool for detecting and resolving cooperative malicious exercise. | If it used to be smartly suited with diversified platforms, that can perchance perchance presumably be attention-grabbing. |
| It is some distance both launch supply and free. | For the time being, completely the Linux working machine is supported; Dwelling windows is no longer. |
| Put together your devices by naming and tagging them. | a pair of CMS trot-ins are lacking. |
| To shriek traits and patterns, gaze the exercise ancient previous from the earlier months and over time. |
6. Sophos Firewall

The exercise of deep learning and synchronized security, the Sophos XG Firewall affords next-technology firewall protection at a high degree.
In phrases of accelerating your network’s security and efficiency, the Sophos Firewall ecosystem can provide you unparalleled advantages.
Accelerating your a need to-own SaaS, SD-WAN, and cloud utility site traffic while keeping your network from as a lot as the moment threats is what Sophos Firewall’s Xstream structure is all about.
New SD-WAN parts in Sophos Firewall allow for optimum network tempo, adaptability, and security.
Sophos Firewall automatically adjusts to your machine’s configuration without your having to total one thing else.
You win all of the parts, flexibility, and customization alternate choices you wish to murder it work to your surroundings.
The Sophos XGS Sequence Firewalls are in a position to deep packet inspection thanks to their combination of a high-efficiency multi-core CPU and a devoted Xstream Float Processor.
Aspects
- Lets you zone the network for better administration and security.
- Enables department areas of work and some distance away customers to securely join thru VPN.
- A single-pane-of-glass administration console simplifies policy administration, monitoring, and security infrastructure reporting.
- Integration with automation and administration platforms to streamline security operations and responses.
- Elephantine logging and reporting negate network activities, security events, and compliance wants.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| Finds unknown apps and other hidden risks to your network. | If there is any downtime exercise, the help crew can reply more rapidly. |
| Blocks unknown threats using a immense fluctuate of cutting-edge security. | Inserting 2FA into be aware for user authentication on the enviornment degree. |
| Website online visitors in IPsec tunnels is accelerated by Xstream FastPath. | With OpenVPN, there is no integration. |
| An intuitive interface for configuring principles and VLANs. |
7. FortiGate NGFW

Fortinet, a market leader in ranking networking, affords scalable, seamless convergence for any surroundings, from department areas of work and campuses to knowledge centers and the cloud.
The safety efficiency, threat intelligence, beefy visibility, and ranking networking convergence supplied by FortiGate NGFW are unmatched.
To own faraway from user experience degradation and downtime, this firewall machine can design hyper-scale site traffic inspections at high speeds.
Real networking is possible with the motivate of a broad kind of traits, similar to instrument-defined broad build networking (SD-WAN), switching, wireless, and 5G.
FortiGate next-technology firewalls (NGFWs) combine most attention-grabbing-in-class security parts at the side of intrusion prevention programs (IPS), web filtering, SSL inspection, and computerized threat protection to produce ranking, policy-driven networking.
Aspects
- One platform involves firewall, VPN, intrusion prevention, antivirus, utility preserve watch over, and more.
- Managers can build of abode principles per apps, customers, and groups with lovely-grained preserve watch over and visibility over applications.
- Developed IPS technology that detects and prevents known and unknown threats, at the side of zero-day assaults, in exact time.
- URL filtering and jabber administration can restrict web having a gaze and block hazardous or harmful websites.
- Stops risks hidden in SSL/TLS encrypted messages by decrypting and checking contents.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| The user interface is amazingly easy and user-pleasant. | The Logging Companies could perchance also very smartly be enhanced to produce more knowledge. |
| having the ability to manipulate from a single computerized preserve watch over console. | Scaling FortiGate is no longer easy; in scream to scale the firewall because the commercial expands, you wish to swap the hardware field. |
| FortiGate has the coolest thing about being ready for exercise on-premises or in the cloud. | Draw some parts, which are completely accessible in CLI, accessible in the GUI. |
| The preserve watch over over applications is amazingly stable and consistently as a lot as this point. |
8. ZoneAlarm Free Firewall
.webp)
ZoneAlarm Free Firewall affords the ideal regular of firewall security that you’re going to be ready to mediate of.
ZoneAlarm Free Firewall blocks malicious site traffic from coming into your dwelling computer and thwarts hackers’ attempts to attain entry.
ZoneAlarm Free Firewall delivers many levels of cutting-edge protection to be aware and conclude unlawful site traffic, give protection to within most knowledge, and guard against malware and hackers.
This firewall’s Elephantine Stealth Mode makes it that you’re going to be ready to mediate of to remain undetected by intruders and protects against contaminated packages.
Your computer is ranking from viruses that unhurried it down and malware that takes your within most knowledge, passwords, and financial knowledge thanks to ZoneAlarm Free Firewall.
With fixed DefenseNet security upgrades, it helps you reply rapidly to online assaults.
Aspects
- Retains a gaze on incoming and outgoing site traffic and blocks unauthorized entry to your computer and the web.
- Hides your computer from hazardous site traffic by making it seem unavailable to attackers.
- Enables customers to authorize or ban web entry for specified packages.
- Updates security principles and requirements to forestall new assaults and weaknesses.
- Notifies customers of suspicious exercise, attempted breaches, and security threats in notify that they would perchance perchance act promptly.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| Defend your within most knowledge by making your self untraceable to hackers. | It completely supports WindowsOS in the period in-between. |
| Block unauthorized site traffic and organize program web entry. | There is no such thing as a URL filtering be aware. |
| With ZoneAlarm Free Firewall, your WiFi PC is protected. | There aren’t many alternate choices for scanning. |
| This instrument affords protection against network threats for desktops and laptops. |
9. Cisco Real Firewall

The Cisco Real Firewall used to be beforehand is known as Firepower.
Cisco Real Firewall is the most assuredly used firewall amongst the ideal firewalls supplied by service providers.
Cisco Real Firewall is a firewall product that works with Cisco’s other security providers and products and affords entire anti-malware safeguards love DDoS protection and sandbox configurations.
With Cisco Real Firewall, you are going to be ready to gaze all the issues that’s going on within your network thanks to the extremely efficient security capabilities it integrates, similar to Cisco Real IPS and Cisco Real Endpoint.
The Cisco Real Firewall portfolio affords superior protection to your network by inequity day’s refined and ever-evolving threats.
The Cisco Real Firewall enables for the ideal that you’re going to be ready to mediate of degree of protection, both now and in the break.
Cisco’s unified platform all without danger manages firewall, utility, intrusion, URL, and virus security insurance policies.
Any suspicious packets that murder it previous Cisco Firepower NGFW are reported intimately.
Aspects
- VPN technology ensures ranking some distance away entry for customers and department areas of work.
- Offers a single preserve watch over panel for developing insurance policies, monitoring, and providing security machine knowledge.
- Makes exercise of automation and orchestration to help security operations, response, and policy enforcement.
- Elephantine logging and reporting negate network activities, security events, and compliance wants.
- SD-WAN improves network connections, ensures app efficiency, and affords ranking web and cloud entry.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| That you just may perchance exercise the firewall in the community, remotely, or thru the cloud2, which are the three accessible utilization alternate choices. | There is no such thing as a option for CLI configuration changes, and pushing configuration changes is unhurried. |
| Developed degree malware protection, URL filtering, VPN help, and SSL help are all supplied. | Unfortunate reporting engine, stress of administration console, and lack of ability to scale product efficiency |
| Whereas you happen to’re switching from a more newest ASA or FTD, Cisco affords a migration instrument to murder the formula simpler. | Compared to other market opponents, it’s somewhat more expensive. |
| Integrated preserve watch over across dynamic utility environments thru exact-time, unified workload, and network security |
10. Barracuda CloudGen Firewall

Barracuda’s CloudGen Firewalls redefine the firewall as a dispensed network optimization solution that grows to a giant want of web sites and applications, bridges the hole between on-premises and cloud infrastructures, and facilitates commercial transformation.
Barracuda firewalls could perchance even be deployed on-premises, in Microsoft Azure, Amazon Web Companies, or Google Cloud Platform, amongst other areas.
Developed threat signatures, behavioral and heuristic diagnosis, static code diagnosis, and sandboxing are swiftly-witted one of the most necessary detection layers accessible in the Barracuda CloudGen Firewall.
The Barracuda CloudGen Firewall parts both on-premises and cloud-deployable SD-WAN capabilities, apart from to supporting connections to geographically dispensed sites, diversified clouds, and cell customers.
Barracuda’s Developed Risk Protection solution is linked to its world threat intelligence network to produce proper protection against the latest assaults.
Barracuda gathers threat knowledge from varied sources worldwide, at the side of network, electronic mail, web pages, and web browser threats.
Aspects
- comprises total firewall capabilities and stepped forward security parts love intrusion blocking, program administration, URL filtering, and virus & malware protection.
- SD-WAN parts help network efficiency, reliability, and help many hyperlinks and connections.
- Searches network knowledge for suspicious exercise and hazardous jabber to dam known and unknown threats.
- Offers administrators lovely-grained preserve watch over over apps, customers, and jabber by surroundings principles for particular person apps and user groups.
- Enables companions, some distance away customers, and department areas of work to securely join over VPN.
| What’s Correct ? | What Would possibly perchance well well well furthermore Be Better ? |
|---|---|
| It is some distance user-pleasant, easy to exercise, and makes it easy to release captured emails. | falsely blocking customers who are no longer spammers and who are active on honest websites. |
| There are an correct want of parts for firewall principles relating within and external networks. | A more user-pleasant configuration would murder it simpler to bag explicit settings in the menu tree. |
| Flexibility in using tunnels to build of abode up slight, some distance away areas of work, providing an cheap solution. | Sing material filtering is no longer working properly, permitting a mode of unwanted contents. |
| Exquisite site traffic visibility enables us to be aware exact-time site traffic applications on the dashboard. |
Often Requested Questions
Firewalls are on the entire your first line of defense against malware, viruses, and attackers attempting to entry your group’s within network and programs, whether or not they are implemented as hardware, instrument, or both.Â
The manner they characteristic is but every other solution to categorise firewalls, and each and each type could perchance even be configured as both instrument or a bodily instrument.
1. Packet Filtering Firewalls
The earliest and most most necessary kind of firewalls are packet filtering firewalls. Firewalls with packet filtering operate in a line at intersections where switches and routers are used.Â
2. Circuit-Level Gateways
Circuit-degree gateways be aware active classes and verify established Transmission Withhold a watch on Protocol (TCP) connections while working on the session layer. They discontinue no longer personally discover about the packets.
3. Stateful inspection firewall
Say-mindful devices no longer completely gaze each and each packet, however also preserve be aware of whether or no longer it’s miles a phase of a TCP or other network session that has already been established.
In phrases of security in the cloud, the cloud supplier will organize your solution and the hardware infrastructure that powers it.
Carrier-based entirely architectures are mandatory for many companies because of it enables them to develop as wished without caring about provisioning new hardware.
Companies need to aloof provide enterprise firewall capabilities to all customers and locations across the group whilst they exercise cloud infrastructure providers love AWS to prolong scalability.
NGFWs bolt unparalleled further, providing extra efficiency that makes it that you’re going to be ready to mediate of for a company to detect and thwart attempted cyberattacks more efficiently.
With FWaaS, a company can scale security more effectively by connecting its dispensed sites and customers to a single, logical, world firewall with a unified utility-mindful security policy.
Also Learn:
Source credit : cybersecuritynews.com






