10 Best Penetration Testing Phases & Lifecycle – A Pentesters Guide 2024

Penetration Testing Phases involves numerous Strategies, phases, lifecycle, and scope to prepare the articulate checklist to originate quality penetration operations.
Here we rating created a total Penetration Testing E book with detailed step-by-step concepts.
Let’s rob a search for on the finest plot to fetch better to your pentesting engagements by breaking your methodology into successfully-defined phases, resulting in efficient workflow.
There is no longer any denying that any penetration testing mission is a lengthy task, inspiring slightly quite a lot of numerous abilities.
Tackling every little thing real away can no longer weigh down pentesters, slightly quite a lot of mishaps can happen: unexplored targets and resources no longer illustrious vulnerabilities and former dusty findings and plenty extra.
So what’s the upper plot on fixing the form of wide number?
When you try and break down your Penetration Testing Phases & lifecycle into smaller steps, with successfully-formed targets and originate them in a sequential manner, this would possibly occasionally flip pentest into an efficient and sincere task.
What steps originate penetration testing Phases, lifecycle, and Strategies encompass?
Penetration Testing phases delivery with timelines and scoping of targets to the discovery of attack ground as much as reporting section, slightly quite a lot of things near in between. Cautious execution of every step will revenue your group with the attend of the finest Pentest suppliers.
| Penetration Testing Phases E book | The vogue to Perfrom? |
| Scoping | Scoping is a prime, it wants slightly quite a lot of consideration and clarified Pentesting documentation before persevering with ahead. |
| Scheduling | Scheduling share of the penetration testing Phases and lifestyles cycle. Potentialities and the group think when to delivery out the mission, when to ask the predominant outcomes, and when to ask the elephantine file. |
| Reconnaissance | Reconnaissance is a task or plot to fetch files in-depth about the purpose. Care for gathering files till penetration testing phases delivery to meander depth to originate in-depth Pentest operation. |
| Exploitation | The exploitation section of the purpose of the pentest engagement is to fetch a reverse shell (or pop a shell as crimson teamers disclose) from the patron’s server to yours. |
| Escalation | Escalation will be horizontal or vertical. Horizontal escalation involves pivoting to 1 other person with an identical privileges whereas vertical escalation is pivoting to a person with elevated privileges. |
| Persistence | The persistence section permits you to continuously fetch entry to to the compromised server to wade via the full exploitation task all any other time is cumbersome. |
| Exfiltration | The exfiltration section is a system to dump as important sensitive files as imaginable after gaining the wonderful imaginable privilege level. Fetch as many password dumps, hashes, PII, and plenty others. |
| Reporting | Reporting section required to write successfully-structured and complete penetration testing studies is a really crucial means. |
| Remediation | This would possibly well additionally simply attend the consumer’s safety group in expediting the process of fixing bugs that rating been pointed out from the penetration testing file and make certain the task continues till the full vulnerabilities acquired mounted. |
| Retesting | Once Crimson Group submits findings via a branded penetration testing file, the Blue group gets on with their process of mitigations: growing Jira duties, checking the patching progress, and stuff. |
Penetration Testing Phases E book – Lifecycle
- The Starting: Scoping
- Closing dates are crucial: Scheduling
- Reconnaissance
- Breaking In: Exploitation
- Root, Admin and Beyond: Escalation
- Leaving Backdoors: Persistence
- Information Gathering: Exfiltration (Put up-exploit)
- Efficient Dialog: Reporting
- Patching, Mitigations and Updates: Remediation
- The Closing Checks: Retesting
Penetration Testing Section 1. The Starting: Scoping

Sooner than the penetration testing task begins, the patron defines the boundaries and boundaries of testing.
- IPs
- Domains
- Subdomains
- Mobile applications (if appropriate)
This step is to elaborate the perimeter where you and your group are free to test. We don’t desire this to happen with our customers.
Scoping is a prime, it wants slightly quite a lot of consideration and clarified Pentesting documentation before persevering with ahead.
Long account short, there rating been incidents with pentest groups that started testing on the unsightly space of IPs and compromised the servers.
It’s crucial to store the scope in primarily the most convenient plot to work with sensitive files properly.
Many customers in most cases provide their scope a traditional text file that will be imported into Hexway Hive to delivery out working with files straight.
Penetration Testing Section 2. Closing dates are crucial: Scheduling

Potentialities wish to in the reduction of the time of penetration testing to delivery out working on vulnerabilities sooner. That also pertains to the scheduling share of the penetration testing cycle.
The pale means can’t provide such an chance, that’s why it change into painful for both facet. Namely difficulties with permitting remediation as soon as bugs meet the pentester.
Hexway Hive has such functionality. Penetration testers fetch vulnerabilities utilizing VAPT Tools and ship them to the consumer portal.
So purchasers can delivery working on fixing them in no time to ship them abet for retesting with out expecting the stop of the pentest.
Potentialities and the group think when to delivery out the mission, when to ask the predominant outcomes and when to ask the elephantine file. Pentests also require purchasers for special arrangements:
- whitelisting testers’ IPs
- non eternal accounts
- staying inner compliance
- and plenty others.
Scheduling closing dates is crucial to preserve every little thing tracked and produce outcomes valid in time. Pentesters ought to space targets in accordance with the discussed length of the mission.
Penetration Testing Section 3. Reconnaissance
That is the lengthiest share of the engagement, however no ought to apprehension. It will in most cases be divided into two normal parts:
1. Mapping The Floor: Discovery
In this Penetration Testing E book Continuously, scope handiest defines the limits, however no longer every little thing one day of the scope is an active server or a reachable domain.
Discovery will be seen as the first share of the reconnaissance section: mapping the attack ground.
This step presents testers with resources to probe further for details.
Tools admire Nmap or Amass play a really crucial position at this point. Subdomain uncovering instruments admire Subfinder, Chaos or others are fundamental to peek much less-feeble subdomains, which is able to have a tendency to be inclined.
Further, to verify that the subdomains are resolving, Massdns is something that will be feeble. There are extra than one instruments feeble in the discovery stage to draw as many resources as imaginable.
In one of our outdated presents, we’ve already mentioned instruments for every pentest section. Below are re-mentioned a few of them that match the Discovery section:
- Nmap: As mentioned earlier, Nmap is with out doubt some of the crucial traditional port scanners and it’s even geared up with scripts to think IPs for vulnerabilities and exploit normal bugs.
- Masscan: Snappy port scanner to scan a natty quantity of IP/CIDR ranges.
- Crt.sh: A favored sequence of SSL certificates to meander attempting via them in exclaim to fetch exposed subdomains.
- Maltego: A relational tool to secure and mine files from numerous online resources and search engines, mainly feeble for OSINT and recon.
- Shodan.io: World search engine to sift via delivery gadgets on the fetch, ranging from server to IOT gadgets.
- SubBrute: A tool to brute force DNS enumeration to fetch uncommon subdomains.
2.Penetration Testing Section 3: Digging Deeper: Enumeration
In this Penetration Testing Phases Once the resources are ready, it’s time to meander on to the next section of recon: enumerating the expert targets. Here is where pentesters fetch the foothold that can lead to the compromise tea of the inclined asset.
Enumeration is widely belief to be some of the duties that want primarily the most thorough execution. Better the enumeration, the elevated the probabilities of gaining entry.
The checklists of enumeration can fetch wide:
- fuzzing for hidden directories
- brute-forcing parameters
- looking to fetch JS secrets
- finding expert CVEs
- and plenty extra and plenty important extra
Ffuf is a wide tool to fuzz directories, virtual hosts, API endpoints, and plenty others. Nuclei by Venture Discovery is terribly valuable in finding servers inclined to CVEs, normal misconfiguration, and numerous exploits via the expend of templates.
Guarantee that that to preserve note of all your finding because it’ll fetch hard to note on larger scopes.
Incidentally, Hexway also has wide functionality to work with Penetration testing checklist and by no methodology misses a component.
It permits customers to implement methodologies and note the full pentest progress properly.
Penetration Testing Section 4. Breaking In: Exploitation

This stage is self-explanatory: it’s time to expend the vulnerabilities found one day of the recon section.
The exploitation section of pentest engagements purpose is to fetch a reverse shell (or pop a shell as crimson teamers disclose) from the patron’s server to yours.
This indicates a a success compromise of the server (depends on the level of permission the hacked person has).
Now the traipse to getting this shell will be straightforward as uploading a malicious script and executing it or as hard as chaining extra than one vulnerabilities to writing personalized exploits. All the pieces depends on how hardened the purpose is.
The wide majority of the exploitation is a manual process, where evaluation of the vulnerability is required to expend it.
In some conditions, normal exploits can be leveraged. Tools admire Metasploit, and Armitage can originate computerized exploitation.
Ready-to-launch scripts from exploitdb.com and packetstorm.com are also valuable.
Shrimp subsets of vulnerabilities admire SQL injection and SSTI will be exploited via sqlmap and fleshy, respectively.
In moderation ogle the intel gathered in the enumeration section to fetch out what’s going to be done manually and where automation can ease the task.
Right via the exploitation section, it’s excessively crucial to preserve all files about bugs and vulnerabilities tracked.
Namely when any individual from your group wasn’t in a position to expend it, as an illustration.
Hexway Hive is a finest tool for such wants. Any individual can delivery exploring the malicious program and preserve the full actions in a Mask linked to the provider/ host or Resolutions.
Anyone else on the group can continue his actions with out ranging from the foundation, which is fine superior. This protects slightly quite a lot of time for pentesters and their purchasers.
Incidentally, it’s no longer the ending point of the task. The group Lead can also attend his pentester to develop an exploitation belief in checklists with extra instructions on the finest plot to originate exploitation efficiently.
After the a success exploitation, the same plot works for monitoring the put up-exploitation section and monitoring loot.
Penetration Testing Section 5. Root, Admin, and Beyond: Escalation

As a rule reverse shells are got via the exploitation of a provider. This outcomes in having fetch entry to to the server with as important permission as the provider has, in most cases granting pentesters with a low-level person position or a provider myth.
In this Penetration Testing E book, You are restricted by the lesser quantity of privileges feeble by these accounts. That’s where escalating to extra extremely efficient accounts comes into play.
Escalation will be horizontal and vertical. Horizontal escalation involves pivoting to 1 other person with an identical privileges whereas vertical escalation is pivoting to a person with elevated privileges.
In Active Itemizing (AD) environments, Enviornment Controller or Enviornment Admin is the person with the wonderful privileges. In Unix/Linux environments, that person is the foundation.
All any other time a manual task, however you are going to reduction it by utilizing scripts that can file normal misconfigurations.
linPEAS (or winPEAS for Windows) are standard scripts to appear for imaginable escalation paths to privileges.
Bloodhound is a solid tool that can gain files and exclaim paths that can lead to the compromise of the Enviornment Controller.
Penetration Testing Section 6. Leaving Backdoors: Persistence

Within the Penetration Testing lifecycle, It’s a uncommon train to gain every little thing you’ll need in a single meander ought to you fetch a reverse shell.
You’ll want genuine fetch entry to to the compromised server to wade via the full exploitation task all any other time is cumbersome.
That’s where persistence comes into action: leaving a backdoor or an simply accessible script that enables you to meander in repeatedly till it’s required.
Penetration Testing Section 7. Information Gathering: Exfiltration (Put up-exploit)

A this Penetration Testing Phases, One of the principle targets of this section is to dump as important sensitive files as imaginable after gaining the wonderful imaginable privilege level to exhibit the impact of the breach. Fetch as many password dumps, hashes, PII and plenty others.
Dumping hashes in an Active Itemizing atmosphere will be done via many PowerShell scripts or instruments, one of primarily the most expert is Mimikatz, which permits you to dump LSASS conveniently.
To switch files you are going to leverage the HTTP server created on the patron’s machine to extract the concepts.
Chisel is a regular tool to develop fast servers in case python is no longer any longer fresh in the home windows atmosphere.
At this point there’s one painful headache — where to store all this files? Speaking of which.
That’s where Hexway also acquired your abet lined. They developed a numerous section known as Credentials. Here you are going to preserve every little thing you stumbled on one day of the exploitation section.
Penetration Testing Section 8. Efficient Dialog: Reporting
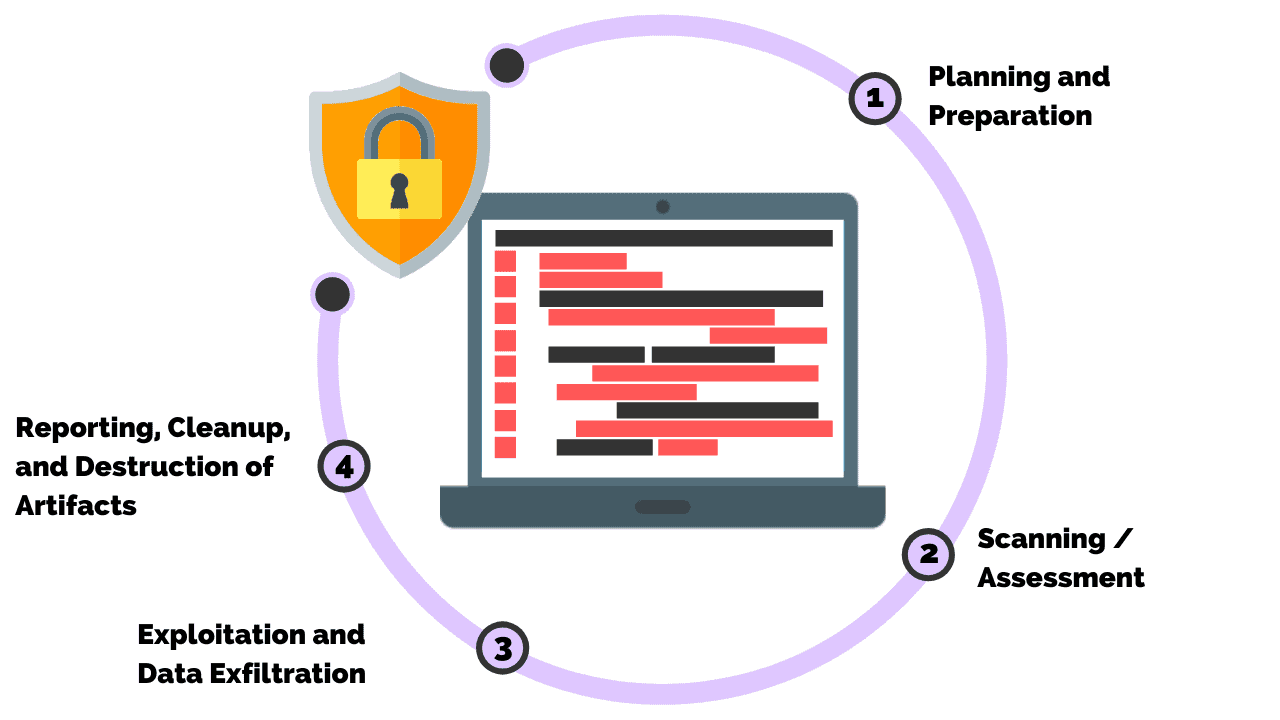
In this Penetration Testing E book, The total group efforts would be wasted if a consumer won’t be in a position to repair exploited findings. Hence, writing successfully-structured and complete studies is a really crucial means.
Starting with an executive summary (which explains every little thing Crimson Group did in a single paragraph), appealing on to describing the vulnerabilities, exploitation, and plenty others.
Merely put every little thing from the above steps that will want an impact on the consumer’s change.
Yet there are slightly quite a lot of numerous file generators to simplify this section. Penetration Testing lifecycle On the different hand quite a lot of them are fine sorrowful to make expend of, especially delivery-source ones.
That’s the valid reason reporting is mammoth painful for pentesters. Hexway Hive developed an interior file generator that collects files from all outdated steps and turns it into human-readable files in a customizable docx file.
Plus Hexway creates personalized file templates free of fee. Welcome to the lengthy fade, and welcome to Penetration Testing as a provider – PTaaS.
Penetration Testing Section 9. Patching, Mitigations and Updates: Remediation

As mentioned in the outdated step, pentest supplier would possibly well additionally simply peaceable counsel remediation for the stumbled on vulnerabilities.
This would possibly well additionally simply attend the consumer’s safety group in expediting the process of fixing bugs from the file.
Steered mitigations vary from normal code practices admire enter sanitization, ready statements and plenty others (to provide protection to in opposition to injection and numerous OWASP Top 10 vulnerabilities to upgrading tool variations (to provide protection to in opposition to plain and identified CVEs).
The purpose of pastime desires to be on keeping programs patched and up-to-date, which eliminates quite a lot of the foothold and entry aspects for attackers (and Crimson teamers alike).
Penetration Testing Section 10. The Closing Checks: Retesting

Once Crimson Group put up findings via a branded file, Blue group gets on with their process of mitigations: growing Jira duties, checking the patching progress and stuff. This would possibly well additionally simply rob a whereas…
But Hexway solutions even develop these sooner with lustrous Jira integration and put change.
When defenders are ecstatic with patches, they’re going to achieve abet to Crimson Group to fetch a retest: it’s fundamental to verify that beforehand inclined providers and products are in truth no longer exploitable.
The conversation and relation between Crimson Groups and Blue Groups are identified as Crimson teaming. It’s crucial that all people appears to be on the same internet page.

Blue Group in most cases shares a doc with their wants with the pentesters.
They can expend a tool admire Hexway Apiary to log the means of patching and section it with fellow pentesters in valid-time.
These 10 phases of a penetration testing handbook lifecycle are what nearly every safety group goes via.
Some would possibly well additionally simply expend numerous names, however the total concept stays the same. re
Care for them handy and be better than your competition in the case of pentests! Correct luck and delivery offering PTaaS with Hexway.
Continuously Requested Questions
Penetration testing often identified as Pen Take a look at is a simulation of a valid-time cyberattack in opposition to a laptop networks, internet applications and any tool to fetch and exploit the vulnerabilities.
The reason of penetration testing is to evaluate the safety of a machine or network and title any weaknesses that would possibly well additionally very successfully be exploited by cybercriminals.
These are 3 Penetration Testing Phases.
1. Planning and reconnaissance
2. Assault and Gaining Access
3. Exploit and File
1. Community Carrier Penetration Testing.
2. Net Application Penetration Testing.
3. Mobile Application Testing
4. Wi-fi Penetration Testing.
5. Bodily Penetration Testing.
6. Internal/External Infrastructure Penetration Testing
7.Social Engineering Penetration Testing.
1. Metasploit
2. NMAP
3. Wireshark
4. Aircrack
5. Nessus
6. Social Engineering Toolkit
7. W3AF
8. Burp Suite
9. BeEF
10. SQLmap
1. Blackbox Penetration Testing
2. White Field Penetration Testing
3. Gray Field Penetration Testing
1. Hexway
2. Intruder.
3. Acunetix
4. Rapid7
5. Cobalt.io.
6. Invicti
7. Indusface WAS
8. SecureWorks
9. Intruder
10.Coalfire Labs
11.ImmuniWeb®
12.Raxis
13.FireEye
14.Astra
15.Netragard
16.QAlified
17.Cipher Security LLC
18.Machine Secured
19.Offensive Security
20.Securus World
CWPT – Licensed Net Penetration Tester (Ethical Hackers Academy)
CNPT – Licensed Community Penetration Tester (Ethical Hackers Academy)
PenTest+ – CompTIA Pentest+ (CompTIA)
CPENT– Licensed Penetration Testing Educated (EC Council)
OSCP – Offensive Security Licensed Educated (Offensive Security)
GPEN – GIAC Penetration Tester (SANS)
CPTE – Licensed Penetration Testing Engineer (NICCS)
eJPT – eLearn Security Junior Penetration Tester (eLearn Security)
C)PTE– CERTIFIED Penetration Testing Engineer (Mile2)
CPT – Licensed Penetration Tester (Pentester Academy)
Penetration testing as a provider, often identified as PTaaS, is a cloud-based mostly completely mostly penetration testing solution that enables agencies to conduct regular, computerized penetration assessments with ease.
PTaaS platforms provide customers with the full instruments and resources they ought to fade efficient penetration assessments, including a internet based-based mostly completely mostly interface, an intensive files depraved, and 24/365 buyer toughen.
In exclaim so that you just can form a penetration testing quote, there are a few stuff you ought to originate.
1.It be crucial to gain files about your machine or network, including its size and complexity
2 It be crucial to settle whether you’ll desire a complete or normal penetration test
3. You’ll ought to contact a preference of penetration testing corporations and ask for quotations from every person
One of the largest reasons is that it helps to develop definite your programs and networks are gain in opposition to doable threats.
Penetration testing can also will let you to achieve how inclined your programs and networks are to attack, and what steps you rating to rob to beef up their safety.
By figuring out vulnerabilities early on, you are going to keep far from the costly repairs and replacements that would be fundamental in case your machine or network change into to be hacked.
Penetration testing can be serious since it’ll additionally simply will let you boost your sign image and reputation. Potentialities will be extra inclined to belief you with their personal files in case your programs and networks are gain
Precious Linked InfoSec Assets
- Birth Source Intelligence Tools (OSINT Tools) for Penetration Testing
- Developed Endpoint Security Tools
- Unhealthy DNS Assaults Kinds and The Prevention Measures
- Most productive Birth Source Firewall to Protect Your Enterprise Community
- Birth Source Intelligence Tools (OSINT Tools) for Penetration Testing
- Free Net Application Penetration Testing Tools
- Free Penetration Testing Tools
- Most productive UTM Machine
- Free Forensic Investigation Tools
- Free Malware Diagnosis Tools
Source credit : cybersecuritynews.com


