Best Practices for Email Security Headers – 2024
Simplest Practices for Email Security Headers – 2024
Email hacking and fraud have become overall on the moment. Cybercriminals can without problems break into and rob adjust of mail accounts if they keep no longer appear to be regain.
They can create so via phishing assaults, prone apps, and records breaches. Globally, of us send about 347.3 billion emails day-to-day, all of which lift quiet information.
Online criminals send about 3.4 billion phishing emails day-to-day, the utilization of many recommendations to style them leer staunch. Conducting very best practices for email security headers can aid style bigger your cyber defenses. It is best to be attentive to the assaults you might presumably well presumably be going via. Originate consciousness within your team and organize passwords effectively.
What create Email Security Headers Mean?
Email security headers encompass gear that you just might presumably well presumably no longer stare. These hidden substances feature distinguished information that authenticates and identifies messages. They are a need to-have substances of protocol since they present security against assaults.
Security headers uncover about the set the message is coming from and its integrity. Enforcing email security very best practices ensures your information does no longer leak via emails. Your team advantages from accurate-time defense.
You forestall fraud that will impression your organization. Cyber attackers take into myth to govern your email verbal substitute in all ways. Email security very best practices can forestall and adjust assaults. Diversified recommendations can aid organizations enjoy their mail verbal substitute regain.
Encrypt Emails
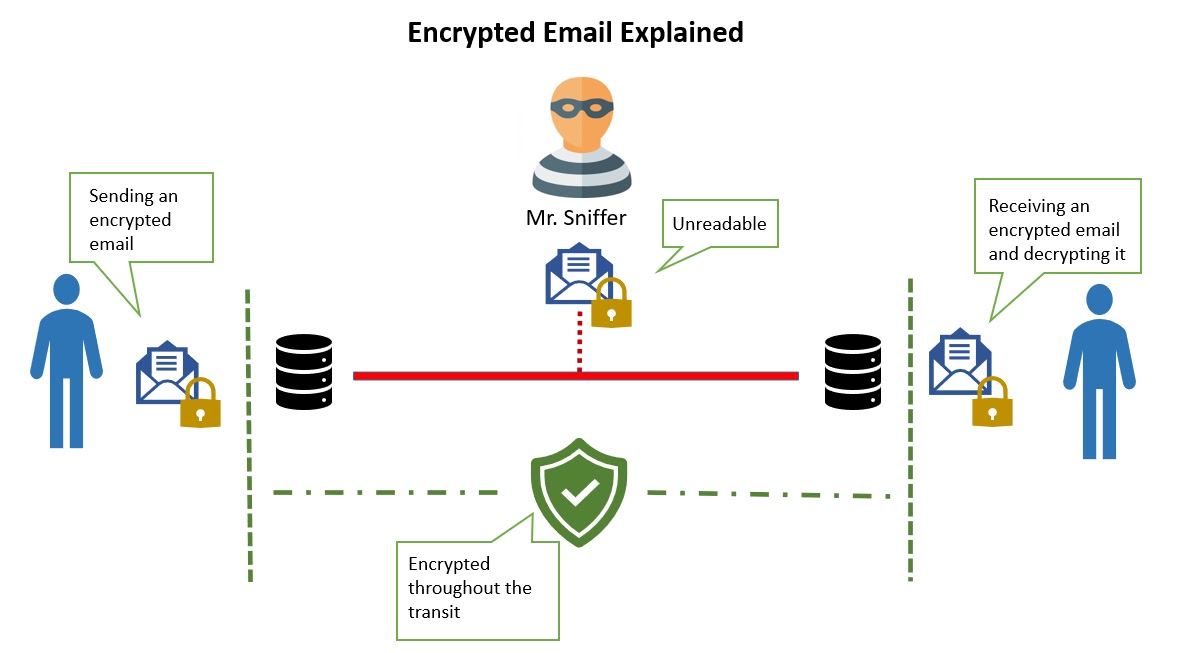
Encrypting mail is a kind of authentication that forestalls unauthorized of us from studying your mail at some level of provide. To enjoy what does encrypting an email mean, have how a disguised or coded message would leer admire.
Encryption converts the message into an illegible textual pronounce material. Even if a cyber attacker accessed it, it’d be of no exercise to them. Anyone who makes exercise of mail verbal substitute might presumably well presumably quiet know encrypt email.
It is particularly crucial when sending quiet mails. Diversified email programs require diversified encryption systems. It is best to perceive encrypt email in every. Perceive send an encrypted email in Yahoo and encrypt an email in Gmail.
It is possible you’ll presumably well presumably presumably encrypt emails at once on a mail program or exercise encryption instrument. While you might presumably well presumably be encrypting in the program, keep the mail first. Once done, substitute the safety settings and pick out encrypted pronounce material and attachments.
In case you’ll be succesful to are desperate to exercise third-celebration instrument, construct the settings at some level of installation. There are moderately plenty of forms of encryption instrument you might presumably well presumably also make a option from. Be desirous about the safety of the instrument sooner than the utilization of it.
Perceive the email threats you might presumably well presumably be going via
Every time you send or receive mail, you face diversified threats. Research reveals that cyberattacks have increased threefold since 2020. Other folks and organizations have to perceive the forms of overall assaults.
This fashion, they’ll put into effect the very best practices for securing mail. The most overall threats encompass the next.
Phishing threats. Online criminals send about 3.4 billion phishing emails day-to-day. They function to rob your information.
Malspam threats. These are spam mails that non-public malware. Cybercriminals add hyperlinks or attachments to them. The latest information reveals criminals send about 162 million spam mails day-to-day.
Spoofing. Online criminals send emails with aspects that style them leer staunch. The obtainable spoofing assault information level to about 30,000 assaults happen day-to-day.
Ransomware threats. Cybercriminals encrypt your emails, making them impossible to learn. Then, they interrogate a ransom to eradicate the encryption. Knowledge reveals that ransomware assaults in 2024 will stand at 37,700 assaults per hour. In a day, organizations can cumulatively receive over 900,000 assaults day-to-day.
Behavior Password Management Simplest Practices
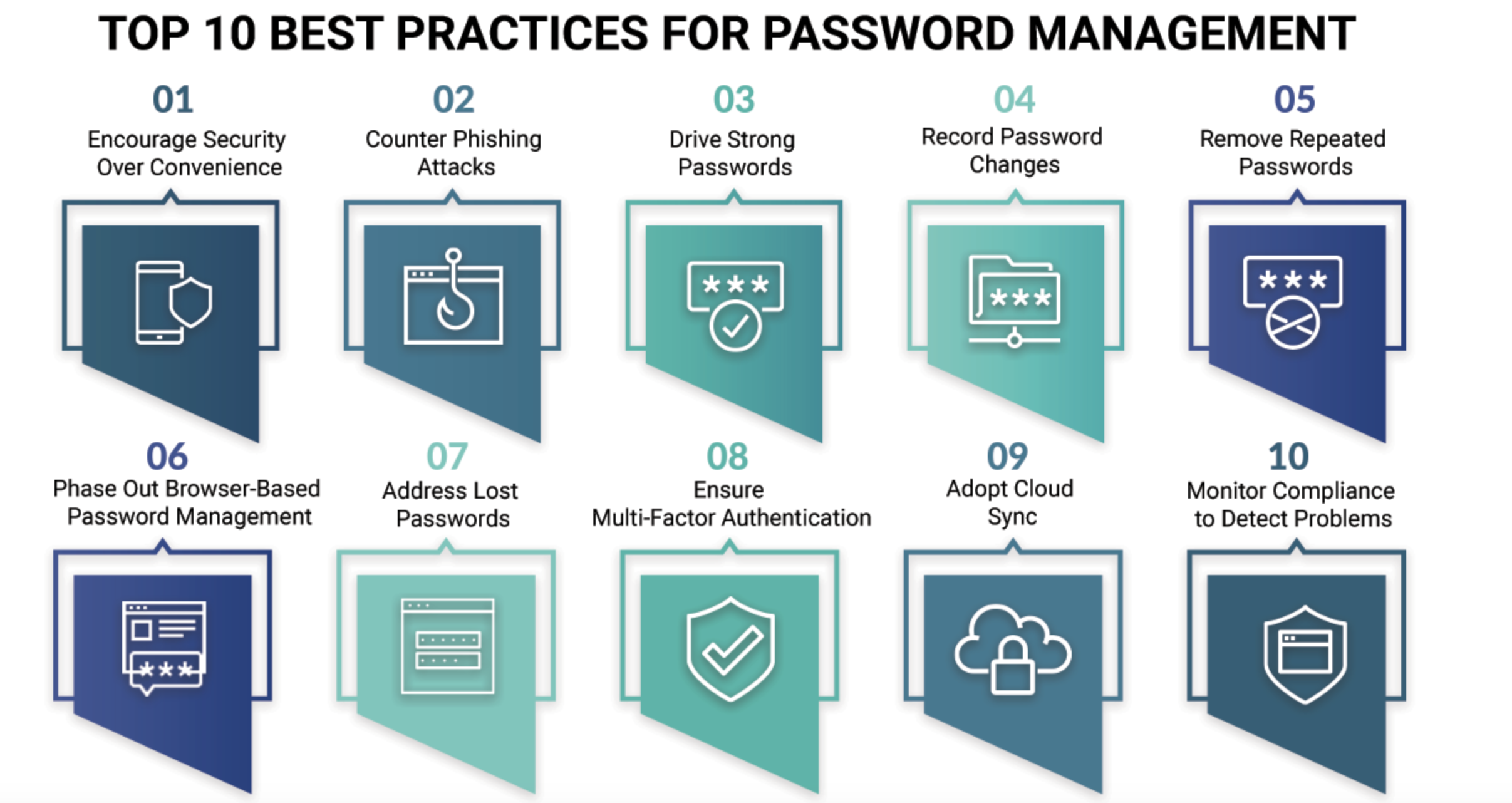
Password administration is a custom that ensures you construct, store, and exercise your passwords safely. It aims to seize the usability and security of passwords. Customers need to exercise diversified mail protection recommendations.
This helps them construct unusual and intricate login information. They even have to exercise systems that style it more uncomplicated to non-public in recommendations the login information. There are diversified email protection recommendations for this.
â Exhaust password administration instrument. They are apps that aid organize all login information in a single set.
â Let the login information be complex. Originate passwords which would per chance be complex but easy to non-public in recommendations.
â Steer certain of sharing passwords. Elevate out no longer half your logins with of us except very predominant.
â Add an authentication layer. Trust an extra security layer by the utilization of two-part authentication.
Behavior employee coaching
Worker coaching will have to be prioritized in every organization. Training offers workers with info about email security. This helps them enjoy the machine regain and forestall assaults. Training permits them to perceive the possible threats that exist. They forestall and title them. Diversified recommendations can aid with employee coaching on securing mail.
â Prepare them about their role in security and the final threats.
â Originate a convention of speedy reporting of any suspicion. Take action when a report is finished and acknowledge the individual.
â Originate a phishing scenario by phishing workers. It’ll aid take a look at judge if they set up how phishing happens.
â Present pork up by guaranteeing workers have your entire tools they need for regain verbal substitute.
â Measure growth and monitor the coaching’s success.
Enforce authentication protocols
Email authentication protocols are in the assist of-the-scenes actions that pork up security. They make certain that that every body outgoing and incoming mail is regain. They are forms of regain email security header verification systems. Authentication protocols make certain that that the email is from the factual provide. The protocols might presumably well presumably block some mails or send them to the spam folder if they leer suspicious. Listed here are the diversified authentication protocols you might presumably well presumably also exercise.
SPF (Sender Protection Framework): SPF permits organizations to construct a listing of common IP addresses. Mail from a diversified IP address fails the authentication take a look at.
DKIM (Domain Keys Identified Mail): DKIM provides digital header signatures. Receiving servers exercise signatures to look at that the mail is legit.
TLS (Transport Layer Security): TLS encrypts email to make certain that that it’s regain at some level of provide.
DMARC (Domain Message Authentication Reporting and Conformance): DMARC makes exercise of SPF and DNS to look at if email senders are staunch. It is a lawful technique to forestall hackers from the utilization of spoofing.
Add trace logo to emails
Label branding is predominant for rising user trust. Logos level to a increased stage of professionalism and grace bigger email commence rates. Emails with a verified logo style it more uncomplicated for recipients to title the sender. It minimizes the prospects of opening phishing and malware emails. When recipients the truth is feel confident with a trace, most will commence their emails.
The trace positive aspects high online site visitors, which increases ROI. Brands have to protect up logo consistency in their mail constructing. It is possible you’ll presumably well presumably presumably add the emblem in the email header, footer, or sender ID photograph. A lawful email signature might presumably well presumably quiet provide an stunning logo create. It is best to rep the colors, letters, and symbols factual.
It need to encompass all crucial but relevant information. These might presumably well presumably encompass email, phone, and contact individual. Add a call to action to direct recipients on what to create if they need aid. Originate and add helpful hyperlinks. They’ll even be hyperlinks to click on to style orders, e book, or talk over with the net store/catalog.
Enforce Defenses
Email defenses are actions that aid enjoy your machine and emails regain. They are actions that go past passwords, email protocols, and coaching. They protect no longer supreme emails but the entire machine from breaches. Enforcing defenses very much minimizes the prospects of threats. The crucial defense actions might presumably well presumably encompass the next.
â Originate mail backups for all quiet mail verbal substitute.
â Set off anti-malware and anti-spam filters
â Monitor all mail accounts carefully and take a look at for security infrequently.
â Install antivirus and online security instrument.
Conclusion
Implementation of mail security helps protect you from unauthorized rep admission to. Protection measures encompass email encryption and the utilization of email authentication protocols. Present email security coaching to workers and provide them the tools they need for defense. Perceive the forms of threats you might presumably well presumably be going via and forestall them. Your total organization might presumably well presumably quiet exercise the very best password administration practices.
Source credit : cybersecuritynews.com





