Beware of New Android Trojan That Executes Malicious Commands on Your Phone
.webp)
Cybersecurity researchers at XLab hold uncovered a brand original Android malware stress called “Wpeeper.”
This subtle backdoor Trojan has been designed to infiltrate Android systems and develop a mountainous series of malicious instructions, posing a huge threat to unsuspecting users.

Wpeeper’s distribution technique is particularly cunning.
The malware is being distributed thru repackaged functions on the UPtodown app store, a favored third-occasion platform such as Google Play.
By embedding a diminutive code snippet into neatly-liked APKs, the attackers hold managed to avoid antivirus detection.
The modified APKs at exhibit point out zero detections on VirusTotal.
The malware’s network operations are equally subtle, featuring a multi-level divulge-and-control (C2) architecture that depends on compromised WordPress internet sites as relay servers.
This advance effectively conceals the staunch C2 server, making it more no longer easy for security researchers and authorities to examine and disrupt the operation.
In depth Capabilities and Encrypted Commands
Wpeeper is a neatly-liked backdoor Trojan for Android systems, supporting many malicious functions.
These embody gathering gorgeous instrument data, managing files and directories, importing and downloading data, and executing arbitrary instructions on the infected instrument.
The most significant just of Wpeeper is its exercise of encryption and digital signatures to guard its network traffic and instructions.
All communications between the malware and the C2 servers are encrypted utilizing AES, and an elliptic curve signature accompanies the instructions to prevent unauthorized takeover or tampering.
Abrupt Cease and Probably Better Draw
Researchers at XLab hold been intently monitoring Wpeeper’s activities and seen an abrupt cease in the advertising and marketing campaign on April 22.
Combine ANY.RUN in Your Firm for Efficient Malware Prognosis
Are you from SOC, Threat Review, or DFIR departments? If so, you likely can furthermore be part of an internet group of 400,000 autonomous security researchers:
- True-time Detection
- Interactive Malware Prognosis
- Easy to Be taught by Fresh Safety Team contributors
- Net detailed experiences with most data
- Quandary Up Virtual Machine in Linux & all Windows OS Variations
- Occupy interaction with Malware Safely
Must you esteem to must always test all these facets now with for free salvage admission to to the sandbox:
The C2 servers and downloaders stopped providing companies and products, main the researchers to suspect that this shall be section of a greater strategic switch by the attackers.
One most likely explanation is that the attackers will hold deliberately stopped the network activity to enable the repackaged APKs to retain their “innocent” place in the eyes of antivirus application.
This could perhaps enable the malware to amplify its installation numbers and point out its true capabilities later, potentially catching security groups off guard.
While XLab doesn’t hold divulge data on the Wpeeper distribution scale, their evaluation of Google and Passive DNS (PDNS) outcomes means that the an infection is on the thousand level without neatly-liked propagation.
Nonetheless, the researchers emphasize that the threat stays ongoing, because the relevant samples continue to evade detection by security corporations.wpeeper_google.png
Detailed Prognosis of Wpeeper’s Efficiency
The researchers hold completely analyzed Wpeeper’s functionality, shedding light on its interior workings.
Family: Wpeeper
MD5: 8e28f482dab8c52864b0a73c3c5c7337
Magic: ELF 64-bit LSB pie executable, ARM aarch64, version 1 (SYSV), dynamically linked, interpreter /system/bin/linker64, BuildID[sha1]=9fa32612558fab9480496f6b31fa5426ae8885d4, stripped
Packer: None
Obtaining Declare-and-Preserve an eye on Servers
Wpeeper makes exercise of two populate its list of C2 servers.
The principle is by decoding the embedded C2 servers during the malware sample, whereas the 2d is by reading and decrypting the “store.lock” file, which contains extra C2 server data and different configuration data.
Wpeeper employs the libcurl library to originate POST requests for speaking with the C2 servers.
The malware makes exercise of the Cookie and Session fields in the HTTP headers to present apart between different forms of requests, similar to beacons, divulge requests, and result uploads.
struct c2info { uint32 lenOfC2; char[lenOfC2] C2s; uint32 lenOfCookie; char[lenOfCookie] cookie; uint32 flag; uint32 id; uint32 flag; uint32 interval; } The network traffic is further protected by the use of AES encryption and elliptic curve digital signatures, ensuring the integrity and confidentiality of the communications.Declare Execution and Supported Functionalities
Wpeeper supports 13 different instructions, starting from gathering instrument data and kit lists to downloading and executing arbitrary files.
| CMD | FUNCTION |
| 1 | win instrument details |
| 2 | win pkg list |
| 3 | update c2 |
| 4 | plan interval |
| 5 | update pubkey |
| 6 | download |
| 7 | win arbitrary file details |
| 8 | win arbitrary dir details |
| 9 | exec arbitrary cmd by capacity of shell |
| 10 | download from C2 , then exec |
| 11 | update and exec |
| 12 | self-destruction |
| 13 | download from arbitrary URL, then exec |
The researchers hold offered detailed data on the a bunch of instructions and their corresponding functionalities.
Thru their divulge tracking and evaluation, the researchers hold won precious insights into the attackers’ tactics and the total structure of the Wpeeper operation.
The researchers hold known forty five C2 servers outdated by Wpeeper, most of that are compromised WordPress internet sites serving as C2 redirectors.
This multi-layered advance helps protect the staunch C2 server from detection whereas also introducing doable reliability points if the compromised internet sites are stumbled on and taken down.
Amongst the 9 hardcoded C2 servers, the researchers judge that one, tartarcusp.com, is most likely owned by the attackers themselves, providing a extra layer of control and resilience to the operation.
The researchers at XLab hold offered a total overview of the Wpeeper Android Trojan, highlighting its subtle effect, intensive capabilities, and the aptitude greater draw on the lend a hand of the attackers’ actions.
They emphasize the continuing nature of the threat and invite peers with unfamiliar views and directors of affected internet sites to give extra clues and insights.
As the cybersecurity landscape continues to evolve, users, security mavens, and researchers must always stay vigilant and collaborate in the struggle in opposition to rising threats esteem Wpeeper.
By sharing data and working collectively, the safety group can greater protect Android users from the risks posed by this subtle malware.
IOCs
MD5
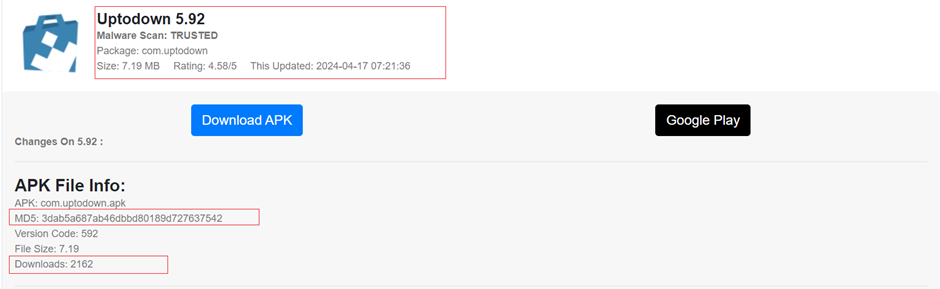
APK 3dab5a687ab46dbbd80189d727637542 ELF 003577a70748ab4ed18af5aecbd0b529 32e92509bc4a5e3eb2146fe119c45f55Reporter
https://eamdomai.com/e?token=Tp5D1nRiu3rFOaCbT4PVcewqIhqbQspd8/3550AI/b1MMJttn+xr4oEFJiGx1bCZztteCi5dG1gYFlNTL0Fp8UaMxROCw4cr225ENjOCmT8oQUyMTjjuTo10fAuFsz9jDownloader
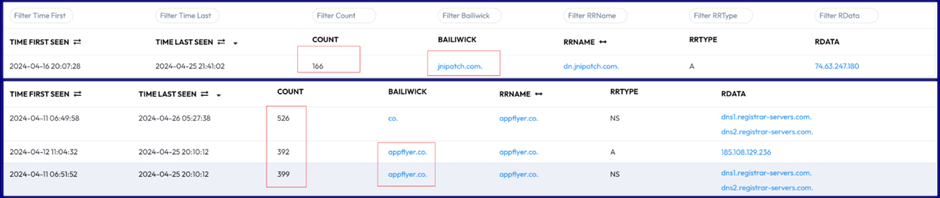
https://appflyer.co/downloads/latest/device/android/ https://dn.jnipatch.com/downloads/latest/device/androidC2 Redirectors
Hardcoded https://tartarcusp.com/BZRAWE/ https://www.chasinglydie.com/7V5QT0/ https://www.civitize.com/0SA67H/ https://wyattotero.com/AQVLLY/ https://web.rtekno.com/5XPOS2/ https://dermocuidado.com/8QSCZP/ https://ocalacommercialconstruction.com/WXFHF6/ https://scatsexo.com/NVZ4L0/ https://snipsnack.com/T8Q2BN/ New https://4devsolutions.com/4NUAK1/ https://atba3li.com/Z99QQ6/ https://avsecretarial.com/PYWDEL/ https://barbeariadomarfim.com/BN2TTO/ https://beanblisscafe.com/MX1OAS/ https://carloadspry.com/SJI4C1/ https://carshringaraligarh.com/TBHH4O/ https://coexisthedge.com/ZF57OA/ https://dibplumber.com/LCN9UJ/ https://dodgeagonize.com/KJSLOT/ https://essentialelearning.com/EVSKOT/ https://focusframephoto.com/1J10V9/ https://fontshown.com/4D69BN/ https://gadeonclub.com/Q9DVGH/ https://hhfus.com/CUGCCO/ https://kiwisnowman.com/DC4O03/ https://masterlogisticsfzco.com/5CBSYC/ https://mrscanology.com/8GVHT3/ https://naroyaldiamonds.com/WZJ236/ https://nt-riccotech.com/Q4LQKN/ https://nutrivital-in.com/7DB9BC/ https://petintrip.com/QPNQSM/ https://qualitygoodsforconfectioners.com/3QLS47/ https://rastellimeeting.com/9Q4GOM/ https://schatzrestaurant.com/J2WMA6/ https://socktopiashop.com/4WYZ7I/ https://speedyrent-sa.com/AIOFB2/ https://stilesmcgraw.com/1WN2BH/ https://toubainfo.com/G1ACF0/ https://trashspringield.com/GYNH3A/ https://vaticanojoyas.com/R5Q7G4/ https://wendyllc.com/QD8490/ https://www.cureoscitystaging.com/YKUCU8/ https://www.elcomparadorseguros.com/A5FDX7/ https://www.francescocutrupi.com/WJYP89/ https://www.yitaichi.com/K7ODU6/Source credit : cybersecuritynews.com


