Beware Of New Malware on The Google Play Store Disguising Themselves as Cleaner Apps

Researchers at McAfee’s Mobile Research Personnel chanced on a brand new malware on the Google Play Retailer, known as ‘HiddenAds’, which disguises itself as cleaner apps that delete junk files on devices or one who can help optimize battery existence for instrument administration.
This new malware hides and displays adverts repeatedly to the customers. Consultants say they urge malicious companies mechanically upon set up with out executing the app.
Malware on Google Play
Even supposing they’ve malicious actions, they exist on Google Play, so the victim can seek for the next apps to optimize their instrument.
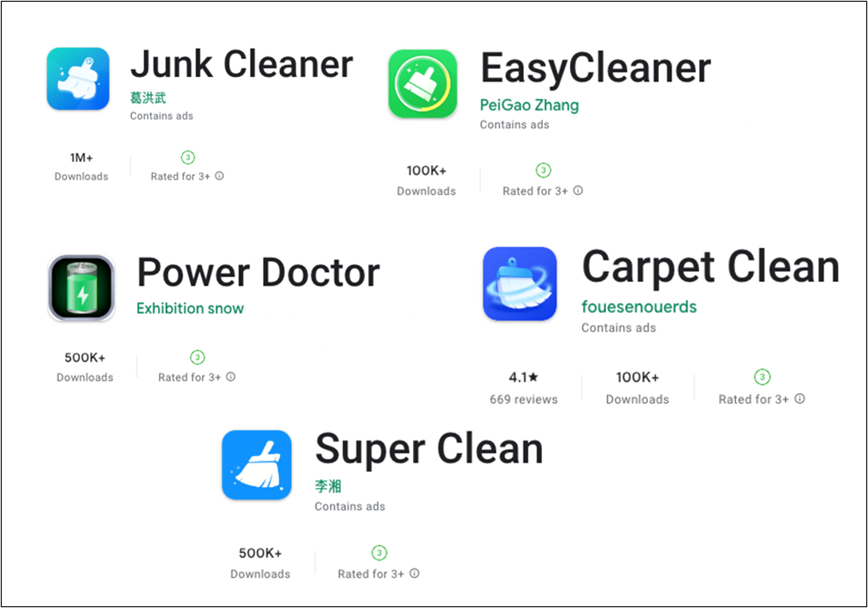
When this malware is installed on the victim’s instrument, they urge malicious companies mechanically upon set up even with out wanting any particular person interaction to launch the apps.
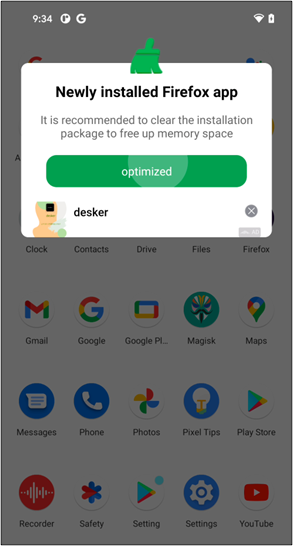
“They try to hide themselves to forestall customers from noticing and deleting apps. Change their icon to a Google Play icon that customers are accustomed to and exchange its title to ‘Google Play or ‘Atmosphere’”, explains McAfee’s Mobile Research Personnel.

Disclose Commercials to Victims

These companies suggest customers urge an app when they install, uninstall, or substitute apps on their devices.
Selling Apps to New Customers
The malware authors created advertising pages on Fb, because it’s miles the link to Google Play distributed through legit social media, leaving miniature margin for doubt for the customers.

The Working of the Malware
The spyware apps abuse the Contact Supplier Android factor, which permits the switch of files between the instrument and on-line companies. For this, Google gives ContactsContract class, which is the contract between the Contacts Supplier and applications.
Consultants say, there is a category known as Directory. A Directory represents a contacts corpus and is implemented as a Disclose material Supplier with its outlandish authority. Therefore, the builders can exhaust it within the occasion that they’re searching for to implement a custom itemizing. The Contact Supplier can look that the app is the exhaust of a custom itemizing by checking special metadata within the manifest file.
“The critical factor is the Contact Supplier mechanically interrogates newly installed or changed programs. Thus, placing in a kit containing special metadata will repeatedly name the Contact Supplier mechanically”, basically based on the sizzling blog post from McAfee.
Also, they exchange their icons and names the exhaust of the
Final Be conscious
In line with McAfee telemetry files, this malware and its variants have an effect on a extensive assortment of worldwide locations, together with South Korea, Japan, and Brazil. Particularly, it’s miles not uncomplicated for customers to ogle this arrangement of malware.
For customers who private installed the above-mentioned apps on their Android smartphone, it’s truly handy to uninstall them manually from the instrument.
It is seemingly you’ll well well explain us on Linkedin, Twitter, Fb for day-to-day Cybersecurity updates.
Source credit : cybersecuritynews.com


